-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Management
p-ISSN: 2162-9374 e-ISSN: 2162-8416
2012; 2(5): 171-179
doi: 10.5923/j.mm.20120205.05
Application of Knowledge Business Framework to Nuclear Decommissioning
Himanshu Upadhyay 1, Leonel Lagos 2, David Roelant 2
1Applied Research Center, Project Management Institute, Florida International University, Miami, 33174, USA
2Applied Research Center, American Nuclear Society, Florida International University, Miami, 33174, USA
Correspondence to: Himanshu Upadhyay , Applied Research Center, Project Management Institute, Florida International University, Miami, 33174, USA.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
This paper discusses the knowledge business framework based on latest information technology patterns and its application to nuclear decommissioning area. Service Oriented Architecture provides a platform for modelling the business processes of any organization or system which allows sharing of the knowledge across the globe. The knowledge business framework is developed by integrating the concepts and features from Knowledge Management and Information Technology area and is applied to nuclear decommissioning with D&D KM-IT (Deactivation and Decommissioning Knowledge Management Information Tool) as a case study. Nuclear decommissioning is high priority area with in the Department of Energy (DOE) complex. The Applied Research Center at Florida International University, working in collaboration with DOE, Energy Facility Contractors Group (EFCOG), and the As Low As is Reasonably Achievable (ALARA) Centres, is developing a web-based knowledge management system to preserve the knowledge that the D&D community has developed and gathered over the years through their experiences on various projects. This system allows the community to share their experiences through various modules that are part of the knowledge business framework.
Keywords: Nuclear, Decommissioning, Deactivation, Knowledge, Framework, Information, Technology, Management
Cite this paper: Himanshu Upadhyay , Leonel Lagos , David Roelant , "Application of Knowledge Business Framework to Nuclear Decommissioning", Management, Vol. 2 No. 5, 2012, pp. 171-179. doi: 10.5923/j.mm.20120205.05.
Article Outline
1. Introduction
- Knowledge management systems are deployed in public and private organizations, with a variety of business models that makes it difficult to design and implement a unified system. Many knowledge management systems are built around independent business units which are not coordinated. Each independent organization has its own processes, business units and delivery channels. An organization has its own approach to control information flow and access to the data. This results in the collection of isolated monolithic systems, using different platforms and standards that make it extremely difficult to access the right information at the right time. Organizations are unable to efficiently and effectively integrate information within their own domain. Legacy systems are restricted by the technological challenges and are not user friendly as they are dependent on rigid old business processes.Knowledge problems in organizations as mentioned by V. Sambamurthy and M. Subramani[26] can be viewed as a combination of the problems of knowledge coordination, knowledge transfer, and knowledge reuse. These knowledge problems reflect difficulties with respect to the access,application, and sharing of knowledge within and across the enterprise. Knowledge coordination problems are linked to the difficulty of locating knowledge sources or identifying knowledgeable individuals or groups for the knowledge required to diagnose or solve specific problems. Knowledge transfer problems are linked to the complexity of transferring or obtaining the knowledge required to solve specific problems. Knowledge reuse problems are linked to the difficulty of ensuring the application of preexisting knowledge to situations when redeployment of prior knowledge stocks rather than a fresh effort to develop novel knowledge is advisable.Knowledge is commonly distinguished from data and information. Data represents observations or facts out of context, and is not directly meaningful. Information results from placing data within some meaningful context, often in the form of a message. Knowledge is what we come to believe and value, based on the meaningfully organized accumulation of information (messages) through experience, communication or inference. Knowledge is viewed both as an object to be stored and manipulated and as a process of simultaneously knowing and acting - that is, applying expertise. As a practical matter, organizations need to manage knowledge both as an object and process.With advancement in information technology to work in integrated seamless ways, modern framework and architectures are used to develop knowledge management systems. Organizations are looking for information technology solutions to manage knowledge stored in various facilities which is not accessible though a common platform. Information technology has to play the most important role of transforming and improving the knowledge processes and systems. An effective information technology knowledge framework helps reduce operational inefficiencies and deliver cost savings.
2. Literature Review
- Study of international best practice on knowledge management (Skyrme and Amidon 1997)[27] has identified two main thrusts. The first is that of making better use of the knowledge that already exists within the firm, for example by sharing best practices. Too frequently people in one part of the organization reinvent the wheel or fail to solve the customer’s problems quickly because the knowledge they need is elsewhere in the company but not known or accessible to them. Hence, the first initiative of many knowledge management programs is that of installing or improving an Intranet, and adding best practice or “expert” databases. The second major thrust of knowledge-focused strategies is of innovation, which is the creation of new knowledge and its conversion into valuable products and services. This is sometimes referred to as knowledge innovation (Amidon 1997)[28]. This requires an environment where creativity and learning flourishes and knowledge is encapsulated in a form where it can be applied. One way is to embed knowledge into products, where it is more easily disseminated.According to Dr. D.Mehta, Dr. N.K.Mehta, and Dr. R.Upadhyay[29], the nature of knowledge management and ways of imparting knowledge management is new wave, which has regained from the birth of its ambitious theme of today. The Knowledge Management systems in the world have the objective of creating intellectual awareness of trends and growth of economic, social, political and cultural activities and their ethos. Knowledge Management is regarded as a corporate cost savings process to enhance performance capabilities with broader availability and utilization of major corporate knowledge assets.According to G.D. Bhatt[24], the Knowledge Management process can be categorized into knowledge creation, knowledge validation, knowledge presentation, knowledge distribution, and knowledge application activities. To capitalize on knowledge, an organization must be swift in balancing its knowledge management activities.N.Levina and E. Vaast[30] provide a practice-based account of the emergence of organizational competencies of boundary spanning that they view as occurring through the emergence of a new joint field that unites agents across boundaries. The study highlights how information systems can be implemented to support knowledge management activities across organizational boundaries by focusing on the emergence of an organizational community spanning organizational units.
3. Knowledge System Overview
- According to Alavi & Leidner[01], information systems designed to support and augment organizational knowledge management need to complement and enhance the knowledge management activities of individuals and the groups. To achieve this, the design of information systems should be rooted in and guided by an understanding of the nature and types of organizational knowledge. Information technology leads to a greater breadth and depth of knowledge creation, storage, transfer, and application in organizations. At any point in time, an organization and its members are involved in multiple knowledge management process chains. As such, knowledge management is not a monolithic process but a dynamic and continuous organizational phenomenon. Furthermore, the complexity, resource requirements, and underlying tools and approaches of knowledge management processes vary based on the type, scope, and characteristics of knowledge management processes. Knowledge management system, by drawing on various information technology tools and capabilities, plays a variety of roles in support of organizational knowledge management processes. According to Ron Sanchez[02], knowledge can be tacit or explicit. The tacit knowledge approach emphasizes understanding the kinds of knowledge that individual in an organization have, moving people to transfer knowledge within an organization, and managing key individuals as knowledge creators and carriers. By contrast, the explicit knowledge approach emphasizes processes for articulating knowledge held by individuals, the design of organizational approaches for creating new knowledge, and the development of systems (including information systems) to disseminate articulated knowledge within an organization. Tacit knowledge is subconsciously understood and applied, difficult to articulate, developed from direct experience and action, and usually shared through highly interactive conversation, story-telling and shared experience. Explicit knowledge, in contrast, can be more precisely and formally articulated. Therefore, although more abstract, it can be more easily codified, documented, transferred or shared. Explicit knowledge is playing an increasingly large role in organizations, and it is considered by some to be the most important factor of production in the knowledge economy. Imagine an organization without procedure manuals, product literature, or computer software. Knowledge also may range from general to specific. General knowledge is broad, often publicly available, and independent of particular events. Specific knowledge, in contrast, is context-specific. General knowledge can be more easily and meaningfully codified and exchanged, especially among different knowledge or practice communities. Codifying specific knowledge so as to be meaningful across an organization requires its context to be described along with the focal knowledge. This, in turn, requires explicitly defining contextual categories and relationships that are meaningful across knowledge communities.According to David J. Skyrme[03], the range of knowledge management activities is broad, and touches many aspects of business operations, such as:01. Creation of knowledge databases - best practices, expert directories, market intelligence etc. 02. Effective information management - gathering, filtering, classifying, storing etc. 03. Incorporation of knowledge into business processes e.g. through the use of help screens in computer procedures or access to experts from icons. 04. Development of knowledge centres - focal points for knowledge skills and facilitating knowledge flow. 05. Reuse of knowledge at customer support centres e.g. via case-based reasoning.06. Introduction of collaborative technologies, especially Intranets or groupware, for rapid information access.07. Knowledge webs - networks of experts who collaborate across and beyond an organization’s functional and geographic boundaries.08. Augmentation of decision support processes, such as through expert systems or group decision support systems.Knowledge management is more fundamental than simply a passing fad because of the following factors:01. The value of an organization’s wealth is increasingly in its intangible assets - its people, know-how, brands, patents, licenses, customer relationships etc. 02. Knowledge can command a premium price in the market - applied know-how can enhance the value (and hence the price) of products and services. Examples are the ‘smart drill’ that learns how to extract more oil from an oil field, and the hotel chain that knows your personal preferences and so can give you a more personalized service.03. As suppliers and consumers get more globally connected (e.g. through the Internet), access to critical knowledge becomes easier and more cost effective. 04. As organizations become more efficient at what they do, they need to apply new learning and talent to help them differentiate themselves in the marketplace. 05. By retaining knowledge as organizations downsize or restructure, organizations can save costly mistakes and prevent “reinventing the wheel”. Existing knowledge systems can be categorized in to three different groups based on their characteristics. Standalone Legacy environment in which systems are standalone old applications and often with paper based inputs and interfaces. These systems perform important functions and are vital for the organization. Very low level of integration or interoperability is possible within these systems which often come from different IT companies like IBM, Oracle, Microsoft, Sun Microsystems, and Hewlett Packard etc. Most important feature of this kind of the system is that business process is limited in scope to one or two applications. The execution process is controlled manually with interpretation of events and situations. Data is usually stored in proprietary formats that are difficult to access and present synchronization problems. Attempts are made to integrate the legacy systems which involve creating a larger all embracing application that addresses a specific functional area and enables interoperability between the different areas. These are Business-to-Business (B2B) applications where one system interacts with another system. Large databases are merged together by removing structural differences and standards based data exchange capabilities are implemented. Current systems are moved from Business-to-Business (B2B) scenario to Business-to-Consumer scenario. End users are connecting through virtual communities and turning to online knowledge resources. This is achieved through knowledge portals, unified communication systems, mobile devices and support centres. It is evident from the current systems that the data and knowledge is fragmented across multiple data centres and are not available to end users in the integrated form.Information can be classified based on scope, content, etc based on the requirements. Current information reflects current state and can be updated. Managing updates to current information is very challenging and must be designed properly to handle loss and conflicts. Ensuring accuracy of current information is critical, considering the cost of communication and latency, which pose major challenges to current knowledge information.Historical information[20] does not change over time. New information is added to previous data set with uniquely identifiable and data time stamped. This information does not conflict or overlap in case they are replicated or come out of sequence. It is possible to maintain information consistency across a distributed system relatively easy.Reference information[20] does not change or changes infrequently. All this information can easily be duplicated through the system based on need with multiple copies existing in parallel and a mechanism for updating them periodically or based on certain events.Internal information[20] defines the information that originates or is used in a particular location like within a department, organization or region. This information does not go beyond the boundary defined by a specific entity. This becomes more important for data collected directly from various devices. This information is transferred to another entity to form a detailed knowledge base. It is important to establish how the ownership of such information is maintained or transferred to other entity. There is also an issue of keeping the information updated and synched with master source.
4. Service Oriented Architecture
- In today’s world, most of the applications are connected. Service oriented architecture[04] is the best development model for building distributed applications in the heterogeneous environment. It depends on passing messages between the services. The best architecture to build connected applications is using service orientation. A service is a program that performs a task and can interact through well-defined messages. A message consists of Extensible Markup Language (XML) and includes a request to perform an action. Response from the service is also a message and consists of XML. Request and response messages conform to Simple Object Access Protocol (SOAP) standards. An application based on service oriented architecture consists of loosely coupled services that communicate through messages and contracts. Contracts[05] define the type of request that can be made to the service and how the service responds to the request message.The proposed SOA based knowledge framework is agile in nature and built on open standards. The services support seamless interoperability between the platforms and vendors. The entire knowledge framework is modular in nature, secure and highly scalable. SOA Based frameworks can act as enabler for broader reach and improved quality and effectiveness of services. With architecture based on SOA Knowledge Framework, systems are in an excellent position to offer easy and convenient access to the information and services. They are also able to reduce cost and resources required by legacy delivery methods. A service is defined as a vehicle by which a consumer’s need is satisfied according to the negotiated contract which includes a service agreement, functions offered etc. Web Service is defined as a software system designed to support interoperable interaction over a network. It has an interface described in a format that applications can process described by WSDL- Web Services Description Language[06]. Different systems interact with the Web Service using SOAP – Simple Object Access Protocol messages over HTTP using XML[07] Serialization[08] with other web related standards (W3C).XML Web Services[09] are fundamental building blocks for distributed computing over the Internet. Open standards and communication/ collaboration among the applications have developed an environment where XML Web Services have become the platform for application integration. Applications are constructed using multiple services from various sources which work together seamlessly regardless of where they reside and how they are implemented. One of the main advantages of these services is that it allows programs developed in different languages and hosted on different platforms to interact with each other using open standards.Boundaries are explicit in the service oriented architecture. Services communicate with each other by sending messages across the boundaries. All the communication between the services happens through messages. Services do not have any information about another service’s internal operations. Each service knows to send and receive the messages. Services are autonomous by nature, which can be developed independently of client or other services. These services can be updated in isolation without affecting other service or client if they maintain the same interface or contract. Each service can be called simultaneously from multiple clients. Services share the contracts and schemas. Contracts are defined by the messages services can send and receive. The schema defines how the client and service build the messages that are exchanged between them. Services define the conditions under which client can interact with them. The service orientation organizes distributed IT resources into an integrated solution that divides the information and maximizes business agility. Service orientation modularizes business process, develops loosely coupled systems that integrates information across the domain. Service Orientation integrates application across diverse systems. Service orientation uses standards protocols and interfaces to facilitate access to business logic data among diverse services.Current applications are built using object oriented methodology. Objects are tightly coupled in object-oriented programming. In service oriented architecture, services are loosely coupled. The client creates an instance of the component and controls its behaviour. Client and services are bound to each other and can exist on different computers or networks or across the globe. Service oriented applications communicate through messages. The client sends a message request to the service and service sends a message response to the client. Applications based on service oriented architecture communicate with each other using SOAP[10] standard established by World Wide Web Consortium (W3C). SOAP provides a stable structure for exchanging data between the applications. It consists of envelop, header and body. The envelope contains the header and the body. The header can contain a request for acknowledge receipt or security information. The body contains data of the message in the normal or encrypted form. Contracts describe the messages services can send and receive. A web service’s contract is an interface expressed in XSD – Extensible Scheme Definition and WSDL- Web Services Discovery Language which is XML based and is derived from W3C standards.
5. Knowledge Business Framework
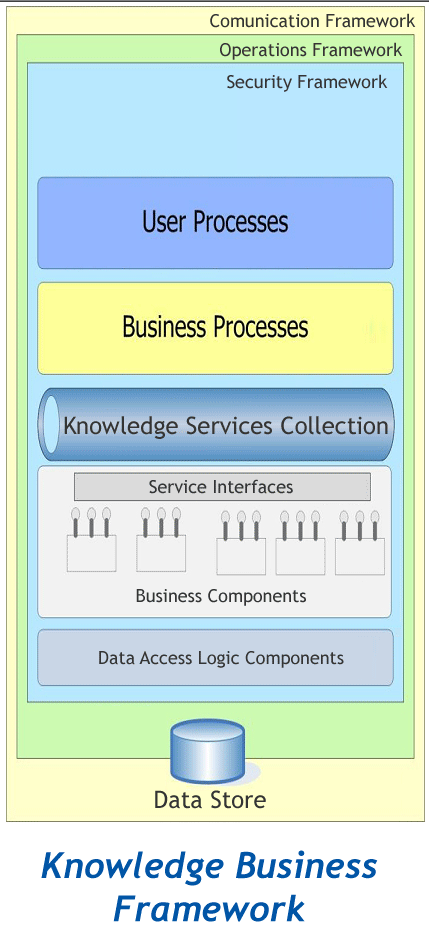
- Modelling any knowledge system is a complex process. Designing and implementing such complex systems are adaptive by nature in which processes followed are constantly changing and output is hard to predict. It is difficult to predict the whole system in its entirety. Requirements are constantly changing with change in new features. One of the goals of the successful Knowledge framework is to develop a user-friendly system, which means that the workflow to be followed must be easy and intuitive. User interface should be nice and clear with important data shown and availability of information with minimum clicks.Business processes in the Knowledge management system should transition seamlessly from one state to another. The user should have seamless experience while interacting with the system. This can be achieved by implementing the logic to control the execution and order of the business process, which can activate multiple applications. There should be dependable mechanisms to move from one application to another. User experience across all the processes should remain uniform with similar look and feel and providing information based on specific functionality or needs. The Knowledge framework provides the foundation to develop systems that are seamless and connected. It results in excellent user experience with executing dynamic and orchestrated business processes under the hood. Connected environment is achieved by developing the applications using open standards, data representation like XML and Web Services.Application Integration in the Knowledge framework can be achieved by implementing Service Oriented Architecture (SOA). Service Oriented Architecture is based on standards such as XML, web services, Simple Object Access Protocol (SOAP) etc. SOA provides the flexibility and agility to manage business processes and changing business goals and objectives. Design and development of the Knowledge framework based on service oriented architecture uses a number of technologies like business process modelling, component based programming, object oriented technologies, enterprise application integration etc. to develop modular and reusable software system to promote knowledge management. A component is defined as an independently deliverable package of software operations that can be used to build software applications or larger components. A component is an encapsulated software module accessible only through its interfaces. Components are defined as at different levels ranging from widgets used in graphical user interface to a major development of business functionality. Components can be embedded within each other. A component has a specification, large number of implementations, and deployment to a specific platform.Component Based Development is a paradigm for software development that focuses on the definition, development, cataloguing and reuse of software components and the assembly of multiple applications from these components. It can be viewed as a systems development approach that addresses the business functionality of the enterprise by providing an interlocking set of applications based on the assembly of predefined building blocks.The Knowledge Business framework is shown in figure 1. The various components of business framework are user process, business process and data access process. They are all based on the service oriented architecture principles. Each of them is discussed below.
5.1. User Process
- User Process controls the interaction of the user with application by using flexible process. It ensures that all the input data is collected and validated. It manages the user transaction, handling cancellation and roll back if the transaction is abandoned. The User process maintains the session state of user connected through certain devices in the event of communication failure and is restored when the connection is established. User Process communicates with Business Process to ensure that the transaction is completed.
 | Figure 1. Knowledge Business Framework |
5.2. Business Process
- The Business layer performs consumption and publishing of business service. Various applications perform business tasks by implementing business logic using business rules, data validation, insert update and deletion of data, execution of various business process, making data and business functionality available to the businesses and consumers. The Business Layer consists of Business Components, Business Process Components, Business Entity Components and Service Interface Components.Business components handle business rules, manage business data, and expose services to be used by business process components. Business process components can handle multiple step business process, initiating applicable functionalities in the right sequence and at the right time. They are also responsible for getting and saving the data at correct stage of processing by communicating with business components, thereby providing the required data processing abilities and functionality. There is a possibility that many business processes may take longer time to run which requires the business process components to be aware of state and should be able to respond, suspend, restart and roll back processes as the execution moves or is abandoned. It may be possible that the component may need to initiate other processes based on the status and condition of the workflow and the whole process is referred to as Orchestration. Business entity components manage the movement of data between different business components. These work with logical level and maintain the data model controlled by the business components. Service interface components expose the functionality of business components (business logic) and owned data of the business components (business entity) as a set of related services. Service Contracts are supported by describing the available data and functionality and the method for calling as well as the message format information, security restriction, access restriction etc.Business Components provide defined businessfunctionality and the maintenance of persistent data. They are large pieces of software and are applicable to a well-defined business domain. Components are self-contained and never overlap or have gaps between them. This means that the business component is not aware of the existence of another business component and can be replaced with equivalent or another greater functional component provided that they share the same interface
5.3. Data Access Process
- The Data access process consists of Data Access Components and Service Agents. Data access components manage the writing and reading of the data to the database that is used to build the application. Data Access Components is responsible for data management and the business layer is unaware physical data storage or any information associated with the storage. Data Access Component is responsible for logical and physical views of data. This process also helps to share data between various applications.
6. D&D KM-IT: Knowledge Business Framework Implementation
- This paper has developed a knowledge businessframework based on information technology services and knowledge management concepts and applies to the engineering field of nuclear decommissioning which is implemented here with D&D KM-IT case study. Deactivation and decommissioning (D&D) work is high priority across the Department of Energy (DOE) complex [11]. Subject matter specialists (SMS) associated with the different ALARA(As-Low-As-Reasonably-Achievable)Centres, DOE sites and the D&D community have gained extensive knowledge and experience over the years. To prevent the D&D knowledge and expertise from being lost over time, DOE and the Applied Research Center (ARC) at Florida International University (FIU) have developed a knowledge management system to capture and maintain this valuable information in a universally available and easily usable system.D&D KM-IT serves as centralized repository and provides a common interface for all D&D related activities. The main purpose of this process is to improve efficiency by reducing the need to rediscover the knowledge and to promote reuse of the existing knowledge. D&D KM-IT is a community driven system. It facilitates the gathering, analysing, storing and sharing of knowledge and information within the D&D community. The D&D Knowledge Management Information Tool (KM-IT) www.dndkm.org[11] is a web-based knowledge platform being developed for the D&D community. This knowledge tool is focused on providing a single-point access into the collective knowledge base of the D&D community within and outside of DOE. Given the dynamic nature and evolution of the D&D knowledge-base due to factors such as changes in the workforce, new technologies and methodologies, economics, regulations, etc., the D&D KM-IT is being developed in a phased and modular fashion. D&D KM-IT Home Page is shown in Figure 2.The following provides a high-level description of the features and functions for the D&D KM-IT system.D&D Hotline: The D&D hotline functionality is supported through a telephone-based hotline and a web-based hotline. The telephone-based hotline is a phone number established for users to call and get immediate verbal guidance from a D&D subject matter specialist. The web-based hotline provides open access to information on previously submitted problems and allows users to ask new questions related to the D&D problem areas: characterization, decontamination, dismantlement, and worker safety.Technology Information Management: The technology information management module provides a comprehensive, easily accessible source of information on D&D technologies, including associated technologydemonstrations and commercial vendors. The objective of this feature is to create, maintain and enhance the technology information repository for D&D applications.Search Engine: The D&D KM-IT search engine has two features. The first search engine feature is the integration of the Google web search process into D&D KM-IT, which allows the user to search through the web similar to the Google search without leaving the D&D KM-IT system. The second search engine feature is a custom D&D web crawler that searches and retrieves information from the web through customized web sites or links specified by the D&D KM-IT system (e.g., Science.gov, NRC, ORAU, ORISE, EPRI, IAEA, etc.). Another part of the D&D web crawler provides search capability through the D&D KM-IT repository.
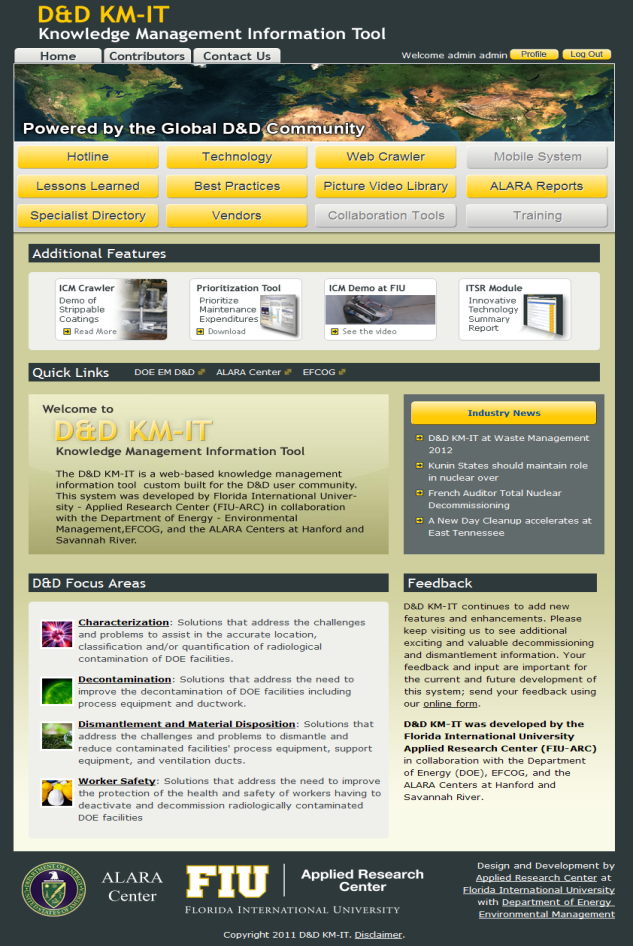 | Figure 2. D&D KM-IT Home Page |
- Collaboration Tools: Collaboration tools provides a platform for conversation and collaboration among the D&D community members and includes features such as news, event calendars, links, message boards, FAQs, etc. The various information tools facilitate the exchange of information within the D&D community.Vendor Management: The vendor module provides a directory of commercial D&D vendors. Vendor management captures all the vendor related information, including vendor name, address, phone, fax, email, website and areas of expertise. The user may search for vendors using a basic text string search. The basic search allows the user to input a simple word or phrase (e.g., full or partial vendor name or area of expertise) to return the applicable vendors.Specialist Directory: The specialist directory module is a directory of D&D experts. The D&D KM-IT specialist directory store the contact information of all the D&D community members who have registered as a D&D expert, along with their areas of expertise.Training: The training module within the D&D KM-IT system allows the ALARA centres to take advantage of the web-based features to reach large numbers in the D&D community with training materials related to dismantlement, decontamination, characterization and other functional areas.Document Library: The document library is a digital archive of D&D related documents created and maintained by the D&D community. Users can contribute to the digital library by uploading documents related to D&D. The documents go through a custom approval process before being made available on the D&D KM-IT system.Video/Picture Library: The video/picture library allows users to upload D&D related videos and pictures to the D&D KM-IT system, including technologies, demonstrations, and past and present D&D projects. These videos and pictures go through a custom approval process before being made available on the D&D KM-IT system.Lessons Learned: The lessons learned module provides a repository of lessons learned documents from the D&D community users. This allows them to share their experiences with the community. The module can also include a series of case studies that took place at various centres to identify the good and bad practices within D&D. The overall objective is to deliver valuable D&D lessons learned to the end user.Best Practices: The best practices module provides the repository of D&D best practices documents that the user community has uploaded to the D&D KM-IT system.Security: The D&D KM-IT system includes a security module that controls user access to the system through the web. The security module consists of the following features: registration, login, role management, authentication and authorization. The D&D community user can get access to published information on D&D KM-IT without registering with the system. However, certain areas of D&D KM-IT require the user to register and login before access is granted. Security is in full compliance to all the DOE requirements and the overall system must be able to pass the DOE Certification and Accreditation (C&A) approval process.
7. Conclusions
- Knowledge systems operate in a heterogeneous environment with different business models that makes design, development and implementation of integrated knowledge systems very difficult and costly. Information technology plays a vital role in managing various knowledge systems within and across the organization. Every organization is trying to improve storage and delivery of knowledge at the right time and right place efficiently and effectively. This can be achieved in today’s world with the help of advances in the technology field by using the Internet, desktop and mobile computing, wired and wireless networks and various high performance computing hardware like tablets, smart phones, laptops, desktops and servers. Each department within an organization tends to implement its own processes, isolated architecture and deployment methodology. They control the flow and access to the information, which results in isolated pockets of knowledge repository within the enterprise across all departments. The advancements in information technology and development of service oriented architecture and associated web standards have lead to a different methodology for developing custom enterprise solutions. The Knowledge Business framework is based on the service oriented architecture, which addresses some of the challenges exposed by old information technology knowledge systems. D&D KM-IT is built using Knowledge Business framework.The Knowledge Business Framework is developed using the service oriented approach to define a core set of business components, each addressing a specialized area and provides services to handle wide range of knowledge business processes. It is developed on the requirements of flexibility and agility. Changes such as addition of authentication providers can be handled as a part of normal usage scenario, supported by the architecture and design of the systems and procedures of the knowledge framework. This knowledge framework supports a range of display options ranging from various clients, depending on the functionality and requirements. The same information is made available to all the connected clients. This provides the support for the separation of the presentation layer of the application from the business logic and data access layer.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML