-
Paper Information
- Next Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Library Science
p-ISSN: 2168-488X e-ISSN: 2168-4901
2012; 1(5): 72-74
doi: 10.5923/j.library.20120105.01
Biometric Recognition: A new Approach for Library Patron Authentication
M. R. Ramesh
Scientific Assistant, Indira Gandhi Centre for Atomic Research, 603102, Kalpakkam
Correspondence to: M. R. Ramesh, Scientific Assistant, Indira Gandhi Centre for Atomic Research, 603102, Kalpakkam.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
This paper discusses a new patron authentication approach in an automated and modern library based on the biometric recognition. The person working at the entrance or at the circulation desk of the library needs to either confirm or determine the identity of an individual requesting service in library. Presently, almost all of the libraries are using identity cards (ID card) for this purpose including photo-based, smart card based or RFID based etc. With the proposed authentication scheme it is possible to confirm or establish an individual’s identity based on “what one is, or how one behaves”, rather than by “what one obsesses” (e.g., an ID card) or “what one remembers” (e.g., a password). The purpose of such authentication system is to ensure that the rendered services are accessed only by a valid user, and not any other else.
Keywords: Patron Authentication, Biometrics, Automated Library
Cite this paper: M. R. Ramesh, "Biometric Recognition: A new Approach for Library Patron Authentication", International Journal of Library Science, Vol. 1 No. 5, 2012, pp. 72-74. doi: 10.5923/j.library.20120105.01.
Article Outline
1. Introduction
- Biometric recognition, or simply biometrics, refers to the automatic recognition of individuals based on their physiological and/or behavioural characteristics. Biometrics can be used to identify the person as person. Tokens, such as smart cards, magnetic stripe cards, photo ID cards, physical keys and so forth, can be lost, stolen, duplicated, or left at home. Passwords can be forgotten, shared, or observed. Moreover, today’s fast-paced electronic world means people are asked to remember a multitude of passwords and personal identification numbers (PINs) for computer accounts, bank ATMs, e-mail accounts, wireless phones, web sites and so forth. Biometrics holds the promise of fast, easy-to-use, accurate, reliable, and less expensive authentication for a variety of applications[1].Any human physiological and/or behavioural characteristic can be used as a biometric characteristic as long as it has the following prerequisites[3].• Universality: each person should have some characteristic;• Distinctiveness: any two persons should sufficiently be differentiable in terms of the characteristic;• Permanence: the characteristic should sufficiently be invariant (with respect to the matching criterion) over a period of time;• Collectability: the characteristic can be measured Quantitatively;• Acceptability: easy to accept the particular biometric identifier (characteristic) as people mostly used it in their daily lives;A biometric system is essentially a pattern recognition system that operates by acquiring biometric data from an individual, extracting a feature set from the acquired data, and comparing this feature set against the template set in the database[4].
1.1. Various Biometrics
- A number of biometric characteristics exist and are in use in various applications. Each biometric has its strengths and weaknesses, and the choice depends on the application. No single biometric is expected to effectively meet the requirements of all the applications. The commonly used biometrics are DNA, Face, Ear, Facial infrared thermo gram, Fingerprint, Gait, Hand and Finger geometry, Iris, Keystroke, Palm prints, Signature, Voice etc.
1.2. Applications of Biometric Systems
- The applications of biometrics can be divided into the following three main groups:• Commercial applications such as computer network login, electronic data security, ecommerce, Internet access, ATM, credit card, physical access control, cellular phone.• Government applications such as national ID card, driver’s license, social security, border control, passport control, etc.• Forensic applications such as corpse identification, criminal investigation, parenthood determination, missing children etc.
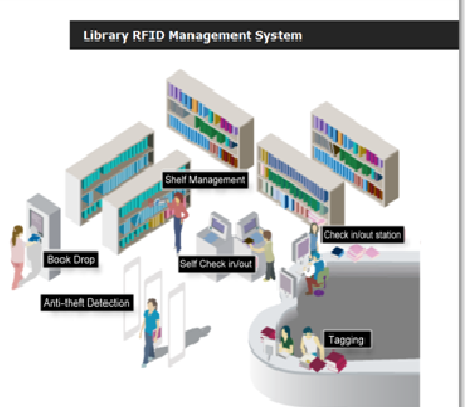 | Figure 1. Library Management System using RFID[2] |
2. Biometric System in Library Perspective
- The Biometric System may easily be applicable to Library System Management in three ways: a) it maintains library patron records very quickly, accurately, orderly; b) it acts as a helpful management Tool for the librarian and other managerial staff of the library; and c) it may continue for years together without any further adding cost after its installation[5]. A schematic diagram of a modern automated RFID Based library system is shown in Figure 1. Biometric based patron authentication system can easily be Introduced in the library management system, which resulting the full proof security cum automated library System. A fingerprint-based door locks & hand geometry verification system. The following can be identified as the major library areas where the biometric system can be used successfully:1. Gate Checking: Each and every library has a manual gate checking system. At least two persons are engaged for doing this job. If biometric system is introduced in the library, it should be fixed with the entrance gate of the library. The authorized library members and library staff members would be able to open the gate by themselves. Non-members should have the assistance to enter the library.2. Circulation Section: In case of daily circulation, there is a chance of misusing library membership cards. One member can use other member’s card, although there are clear indications that Membership Card is not transferable. Biometric based authentication can solve this problem.3. Stack Entry Record: In Open Access Library System readers are always allowed to enter into the library stacks, but there should be a record in detail about readers along with their identity, time in and time-out. From our daily experience it is observed that the readers are not always maintaining manual records properly. They feel this recording is unnecessary and sometime they avoid it. The biometric system can solve these problems of a library easily if it is fixed with the stack entrance gate of the library. It will automatically take care about the most wanted library records. This concept is equally applicable in entry points of different sections of the library for example reading room, rare section, journal section etc.4. Internet Searching, Using Digital Library: Biometric system can identify automatically the library computer users and welcome them for the purpose of Internet searching, using digital library, OPAC, etc. The day-to-day library operation and managements may easily be covered with the application and use of biometric system. Some of the major areas are:1. Surveillance: It is the record keeping of library users, staff, visitors, vendors, suppliers or others who come into the library. Biometric system can successfully manage to record of the library with some days back up and for this purpose one powerful storage server is required.2. Staff Attendance: It is the essential record for the library and this can easily be maintained with the introduction of biometric system, as this system records the persons’ entrance and entry time at the same time of the users. 3. Staff movement record: Biometry system can manage to record of the library staff movement of any particular staff in and out of the library for different purposes with few days back up facilities. This record helps librarian to find out the reasons for non-availability of a person in his / her working point.4. Staff-Computer Automatic Recognition: Staff working with Desktop PCs for essential routine jobs by using the library management software or other works with computers can be authenticated with this biometric system which welcomes the library staffs after recognizing their identity automatically.
2.1. Limitations of (Uni Modal) Biometric Systems
- The successful installation of biometric systems in any applications does not imply that biometrics is a foolproof system. It is clear that there is plenty of scope for improvement in biometrics. Researchers are not only addressing issues related to reducing error rates, but they are also looking at ways to enhance the usability of biometric systems[4]. Uni modal biometrics may face the following limitations: Noise in sensed data, Intra-Class variation means the data for authentication may be different from the stored template due to the varying psychological makeup of an individual might result in vastly different behavioural traits at various time instances, etc.
2.2. Multimodal Biometric Systems
- Some of the limitations of uni-modal biometric systems can be overcome by using multiple biometric modalities (such as face and fingerprint of a person or multiple fingers of a person). Such systems, known as multimodal biometric systems[5] are expected to be more reliable due to the presence of multiple, independent pieces of evidence. These systems are also able to meet the better performance requirements imposed by various applications[6].
3. Conclusions
- Reliable personal recognition is a critical task in many cases. Biometrics refers to automatic recognition of an individual based on his behavioural and/or physiological characteristics. The conventional password-based and ID card-based methods do not really provide positive personal recognition because they rely on surrogate representations of the person’s identity. It is, thus, obvious that any system assuring reliable personal recognition must necessarily involve a biometric component. Biometric-based systems also have some limitations that can be overcome with the evolution of biometric technology and a careful system design, it is important to understand that foolproof personal recognition systems simply do not exist and perhaps, never will. Security is a risk management strategy that identifies controls, eliminates, or minimizes uncertain events that may adversely affect system resources and information assets. The security level of a system depends on the requirements of an application and cost-benefit analysis. It is certain that biometric-based recognition will have a profound influence on the way we conduct our daily business. And thus, a modern automated library can also use these biometric based patron authentication systems.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML