-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Journal of Wireless Networking and Communications
p-ISSN: 2167-7328 e-ISSN: 2167-7336
2013; 3(3): 29-38
doi:10.5923/j.jwnc.20130303.02
Vehicular Ad-Hoc Networks (VANETs) - An Overview and Challenges
Sabih ur Rehman , M. Arif Khan , Tanveer A. Zia , Lihong Zheng
School of Computing and Mathematics, Charles Sturt University, Australia
Correspondence to: Sabih ur Rehman , School of Computing and Mathematics, Charles Sturt University, Australia.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Vehicular ad-hoc networks (VANETs) technology has emerged as an important research area over the last few years. Being ad-hoc in nature, VANET is a type of networks that is created from the concept of establishing a network of cars for a specific need or situation. VANETs have now been established as reliable networks that vehicles use for communication purpose on highways or urban environments. Along with the benefits, there arise a large number of challenges in VANET such as provisioning of QoS, high connectivity and bandwidth and security to vehicle and individual privacy. This article presents state-of-the-art of VANET and discusses the related issues. Network architecture, signal modeling and propagation mechanism, mobility modeling, routing protocols and network security are discussed in detail. Main findings of this paper are that an efficient and robust VANET is one which satisfies all design parameters such as QoS, minimum latency, low BER and high PDR. Some key research areas and challenges in VANET are presented at the end of the paper.
Keywords: VANET, Modeling, Mobility, Routing, Security
Cite this paper: Sabih ur Rehman , M. Arif Khan , Tanveer A. Zia , Lihong Zheng , Vehicular Ad-Hoc Networks (VANETs) - An Overview and Challenges, Journal of Wireless Networking and Communications, Vol. 3 No. 3, 2013, pp. 29-38. doi: 10.5923/j.jwnc.20130303.02.
Article Outline
1. Introduction
- Although Vehicular Ad-hoc Network (VANET) is not a new topic, it continues to provide new research challenges and problems. The main objective of VANET is to help a group of vehicles to set up and maintain a communication network among them without using any central base station or any controller. One of the major applications of VANET is in the critical medical emergency situations where there is no infrastructure while it is critical to pass on the information for saving human lives. However, along with these useful applications of VANET, emerge new challenges and problems. Lack of infrastructure in VANET puts additional responsibilities on vehicles. Every vehicle becomes part of the network and also manages and controls the communication on this network along with its own communication requirements. Vehicular ad-hoc networks are responsible for the communication between moving vehicles in a certain environment. A vehicle can communicate with another vehicle directly which is called Vehicle to Vehicle (V2V) communication, or a vehicle can communicate to an infrastructure such as a Road Side Unit (RSU), known as Vehicle-to-Infrastructure (V2I). Figure 1 shows a typical VANET scenario. The main contributions of this paper are to present state – of – the - art in VANET technology. A detailed study of network architecture with different topologies and network modeling is presented in this paper. A key design area in VANET in order to properly form a communication network is routing the packets in effective manner. The paper discusses different routing algorithms for VANET and presents limitations of those algorithms. Security issues in VANET environment are also addressed in the paper so that trustworthy network architecture can be modelled. The paper also discusses some of the key research areas and challenges in this field.
1.1. Background Research
- A very important design aspect of VANET is to develop an efficient, reliable and secure routing protocol. Vast research has been conducted in thisarea[1],[2],[3],[4],[5], [6],[7],[8],[9],[10],[11],[12],[13],[14],[15],[16]. The main objective of any routing protocol is to find an optimal way of communication between nodes (vehicles). One popular VANET routing protocol is Ad-hoc On Demand Vector Routing (AODV) presented in[17, 18] which uses a demand-driven route establishment procedure. A limitation of this approach is that it creates flooding type of situation within the entire network. Many researchers have presented the remedies for flooding in AODV[19, 20]. Another routing approach is presented in Dynamic Source Routing[21] which is also classified as reactive in nature. Routes are stored in cache and it is expected that source will have complete knowledge of hop-by-hop route to the destination. In[22], authors have presented another routing approach using border node concept. This protocol was based on stop and carry mechanism. There are many important applications of VANET in today’s world. These applications range from critical medical services to comfort and leisure activities. A VANET must be able to fulfil all requirement of ever changing user needs and should also comply with the standard and architectures of the available technology. Some of the key applications[9] of VANET can be summarised as follows:
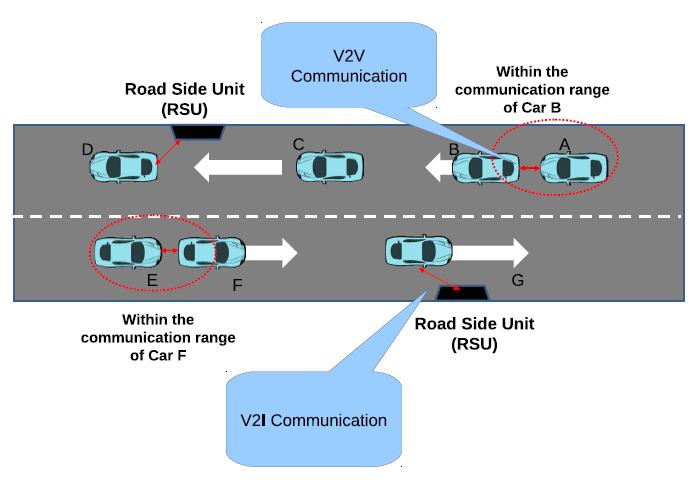 | Figure 1. Creating an Ad-hoc Network using Vehicles (VANETs) |
2. Architecture and Network Modeling
- In principal, there is no fixed architecture or topology that a VANET must follow. However, a general VANET consists of moving vehicles communicating with each other as well as with some nearby RSU. A VANET is different than a MANET in the sense that vehicles do not move randomly as nodes do in MANETs, rather moving vehicles follow some fixed paths such as urban roads and highways. While it is easy to consider VANETs as a part of MANETs, it is also important to think of VANETs as an individual research field, especially when it comes to designing of network architecture. In VANET architecture, an on board unit (OBU) in a vehicle consists of wireless transmitter and receiver.
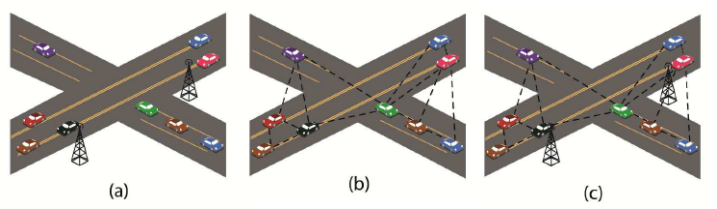 | Figure 2. Network Architecture in VANET |
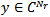 is the complex Gaussian received signal with zero mean and unit variance at one of the nodes and is given by the following equation
is the complex Gaussian received signal with zero mean and unit variance at one of the nodes and is given by the following equation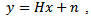 | (1) |
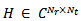 is the complex channel gain matrix,
is the complex channel gain matrix, 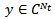 is the complex transmitted signal and
is the complex transmitted signal and 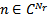 is additive white Gaussian noise. In order to minimise the bit error rate and provide the promised QoS, one has to reduce the effect of wireless channel on the received signal. For this purpose a number of wireless channel models such as Free Space Model[59], Nakagami Model[58] and Log Normal Shadowing Model have been considered. These models also play an important role in creating the simulation environment for different VANET scenarios. For example, NS-2 uses Nakagami model whereas OMNET++ by default uses Free Space Model. In any VANET environment, calculating the transmission range and then finding the probability of packet delivery ratio (PDR) is important. Transmission range for a Free Space wireless channel model can be calculated using Friis Transmission equation[60] given as
is additive white Gaussian noise. In order to minimise the bit error rate and provide the promised QoS, one has to reduce the effect of wireless channel on the received signal. For this purpose a number of wireless channel models such as Free Space Model[59], Nakagami Model[58] and Log Normal Shadowing Model have been considered. These models also play an important role in creating the simulation environment for different VANET scenarios. For example, NS-2 uses Nakagami model whereas OMNET++ by default uses Free Space Model. In any VANET environment, calculating the transmission range and then finding the probability of packet delivery ratio (PDR) is important. Transmission range for a Free Space wireless channel model can be calculated using Friis Transmission equation[60] given as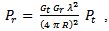 | (2) |
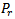 and
and 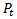 are receive and transmit powers respectively,
are receive and transmit powers respectively, 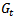 and
and 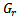 are gains of transmit and receive antennas respectively,
are gains of transmit and receive antennas respectively, 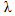 is the wavelength and
is the wavelength and 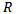 is the distance between transmitting and receiving nodes. Considering proper propagation scheme, wireless channel model and combining schemes at the receiver improves the QoS in VANET.
is the distance between transmitting and receiving nodes. Considering proper propagation scheme, wireless channel model and combining schemes at the receiver improves the QoS in VANET.3. Routing in VANET
- One of the major challenges in the design of vehicular ad-hoc network is the development of a dynamic routing protocol that can help disseminate the information from one node (vehicle) to another. Routing in VANET is different to the traditional MANET routing because of highly dynamic and ever changing topologies in the former. Few protocols that were earlier designed for MANET environment have been tested on VANET. The challenge however remains as how to reduce delay associated with passing the information from one node to another. Overcoming these hurdles in MANET protocols, can help implement real time applications for VANET environment. Other implications such as reducing control overheads also need to be looked into carefully. Keeping an eye on the dynamic characteristics of VANET (as highlighted previously), the routing protocol should be able to withstand the unpredicted and dynamic nature of vehicular network topology. Perhaps the most difficult task in VANET routing is finding and maintaining the optimal paths of communication in desired environments[6].Most of the routing protocols in VANET are closely linked with the topology being used in the network architecture and the performance deviates whenever there is a change in network topology.As highlighted in Figure 3, routing in VANET can be classified into five major categories namely as: • Ad-hoc or Topology Driven Protocols • Location Based Routing Protocols • Cluster Based Protocols • Broadcast Protocols • Geocast Protocols
3.1. Ad-hoc or Topology Driven Routing
- In general, VANETs are infrastructure-less networks and many routing protocols devised for prior ad-hoc network such as MANET based on different network topologies may be applied to VANETs with certain modifications. Topology driven protocols are sub-classified into three categories such as proactive, reactive and hybrid. A number of such protocols were designed to cater the needs of VANET environment[17],[21],[22],[33],[34]. In a proactive protocol, nodes continuously update their routing table with information regarding new routes within the network. This information is passed around to all nodes by sending periodic HELLO packets. This approach, however, creates substantial control overheads. This restricts the use of limited wireless resource such as available bandwidth. On the other hand, in reactive approaches, for example AODV[17], DSR[21], BRP[22] nodes will only send the control data when there is a need. This reduces overheads associated with establishing the link, and helps distribute the actual information faster. This approach however still puts undue resource overheads like maintenance of used/unused routes. These unused paths are created and broken, due to stringent network topology of VANET. Overheads created in reactive protocols are associated with discovering the path to send the information. The path finding process is initiated by sending certain type of message called Route Request Message (RREQ). In Figure 4, node (S) wants to send information to node (D). This process will be initiated first by discovering of route to the destination. When node S needs to find a route to node D, it broadcasts an RREQ message to all its neighbours. When intermediate nodes, say node 1 receive a RREQ message, they compare the desired destination with their own identifiers. If there is a match, it means that the request is destined for node 1, otherwise, node 1 will rebroadcast the RREQ to its neighbours and so do all the other nodes. This approach can create a flooding in the network. Once the request reaches the destination (node D in this case), Route Reply Message (RREP) is initiated back to the source using Backward learning method. Besides studying basic reactive and proactive type of protocols, researchers have found tremendous liking to discover hybrid protocols as well. An example of such a protocol is discussed in detail in[33]. In this approach, the authors have focused more on the design architecture of whole network rather than the performance analysis.
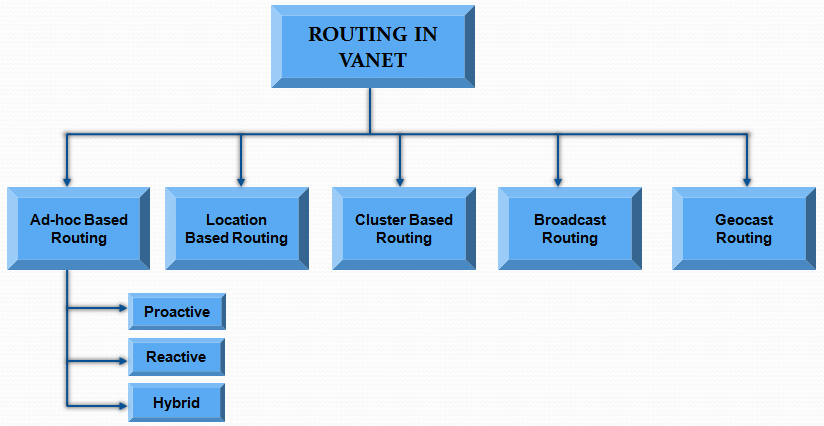 | Figure 3. Routing Types in VANET |
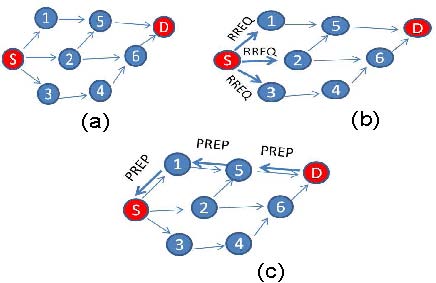 | Figure 4. Traditional Routing -Route Discovery using Flooding |
3.2. Location Based Routing
- Another category of protocols that have shown interest among the researchers are Location or Position Based Routing protocols. In this scheme of protocols information regarding geographic location of vehicles is obtained from different sources like maps, Global Positioning System (GPRS) or even traces of traffic models to help disseminate the information. Quite a few researches like[36] and[37] have presented a thorough comparison of well known topology based protocols like AODV and DSR in conjunction with Position Based algorithm and the results have shown better and improved performance as compared to using plain topological approach. Unlike topology based protocols, position based protocols do not need any route maintenance and the route can get established when there is a need for it. This reduces undue constraint on the bandwidth that is already inadequate in VANET environment. Greedy Perimeter Stateless Routing (GPSR)[38] is one of the examples of a location based protocols where search for nearest neighbour is performed. Each node is aware with its position as well as the position of its closest neighbours. Having the main node this specific information makes GPSR highly suitable for dynamic topological networks. In scenario where no nearest neighbour exists, GPSR utilises perimeter mode with face routing to maximise the search for destination. A performance comparison of GPSR and DSR in a highway environment has been presented in[37]. It has been shown that an improvement in route delay is achieved while using GPSR. In applications where delay and Packet Delivery Ratio (PDR) have stringent requirements mostly in urban environment, GPSR in its original form cannot be used. To cater this problem,[39] presented a modified version of GPSR called Advanced Greedy Forwarding (GPSR-AGF). In this version, information about speed and direction of the destination node are included within the HELLO packets. This showed an improvement in relation to the above mentioned performance metrics. To overcome the deficiencies of GPSR, another approach was presented by the introduction of Geographic Source Routing (GSR)[40]. In GSR, road layouts are used to discover the destination route. It mostly relies on availability of road maps which are used in conjunction with the shortest path finding algorithms.Another important location based routing approach was presented in[12],[13] namely Location Assisted Routing (LAR). LAR is classified as a reactive protocol which uses location information of nodes to decrease the routing overheads that were underlined by other reactive protocols such as AODV and DSR. LAR mainly employs two methods to determine the next hop, one based on window size and other with distance variation. In[13], authors have presented a study of LAR scheme for VANET in Highway scenario using the performance metrics such as Packet Delivery Ratio (PDR), System Throughput, Average Delay and Routing Overheads. It is shown that the PDR increases for moderate number of nodes but decreases at a higher network density. The reason being that at higher network density, the connectivity between nodes is high resulting in less loss of packets. The system throughput of LAR increases from low to moderate network density but it decreases when the number of nodes is higher than 50 in the network. The reason for decrease in system throughput could be the high interference among the transmitted signals. Routing overheads and average delay decrease with the large number of nodes because of many routing paths and larger number of hops. A different methodology not relying on external resources like maps or infrastructure is presented in Greedy Perimeter Coordinator Routing (GPCR)[41]. GPCR is based on the uderstanding that street paths in urban environment create a planner graph. Packets are always forwarded to a node (coordinator) that is on the junction edge. The routing decisions are only made by the coordinator. In another routing scheme where routing decisions are made based on the connected paths between source and destination pair is Connectivity Aware Routing (CAR)[42]. Anchor-Based and Traffic Aware Routing (A-STAR)[36] is another position based protocol used for urban environments. It exploits the usage information for a particular route, to determine the anchor path (number of junctions) to establish maximum connectivity. This usage can be determined using statistical data gathered for particular surroundings. If packet (information) is needed to be sent to any node in between anchors, the usual greedy approach is used. Studies have shown a much improved performance by using A-STAR as compared to GSR and GPSR[43].
3.3. Cluster Based Routing
- In order to reduce the network traffic and routing overheads in VANET, a routing paradigm namely Cluster Based Routing (CBR) is introduced in[44],[45],[46],[47]. The main idea behind CBR is to create a network architecture based on small groups of vehicles called as clusters. In a cluster, one of the vehicles plays the role of a cluster-head as shown in Figure 5. The size of the cluster depends on the design of the routing algorithm which may be based on the number of vehicles in a cluster or the geographical position of the vehicles.
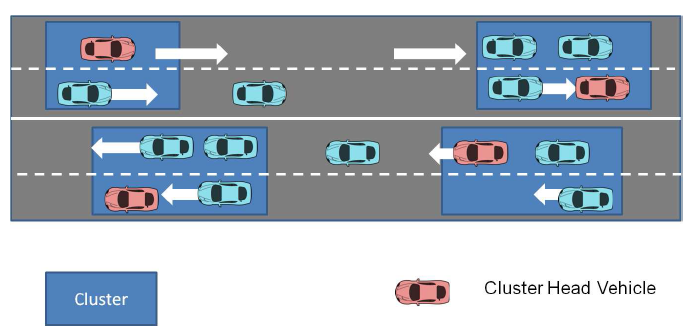 | Figure 5. Cluster Based Routing |
3.4. Broadcast Routing
- Broadcast Routing was one of the traditional routing techniques used in VANET. Primarily broadcast approach is used when the message is needed to be sent to the vehicle that is outside the range. Packets are transmitted using flooding techniques. This ensures delivery of information, but uses extensive resources of bandwidth. As briefed previously, this sort of technique is utilised in many well established routing protocols, especially in the stage of discovering of route to the destination. BROADCOMM[48] and the Nth-Powered P-persistent Broadcast protocol (NPPB)[49] are such well known protocols designed using the broadcasting concept. In BROADCOMM, a hierarchical structure of highway is simulated and the whole region is divided into virtual cells. Cell members establish a hierarchy of Cell Reflector (CR), which acts like a base station to gather messages for particular call as well as from neighbouring cells. CR helps in making judgements in relation to forwarding the messages to individual vehicles. This protocol has shown an improved performance in message broadcasting, delay and routing overheads when compared with other broadcasting protocols. In NPPB[49] a probabilistic broadcasting approach is designed to mitigate broadcasting storms in dense VANET in order to transmit emergency messages effectively. The authors studied a weighted p-persistent routing scheme which shows better accessibility of the farthest node. The performance of this protocol depends on a reasonable choice of the number of nodes in the environment.
3.5. Geocast Routing
- Geocast routing is the classification of routing that deals with dissemination of information in specific area of relevance. Since the early induction of VANET, quite a few approaches of Geocast routing werepresented[10],[11],[12],[13],[14],[15],[16]. Many VANET applications require position dependent multi casting e.g. disseminatinghazardous traffic information to vehicles approaching in the same direction. The key idea behind the Geocast routing is to narrow down the search for next hop to a specific Zone Of Relevance (ZOR). Imagine the possibility of having a mechanism in which if a car gets involved in an accident, it will automatically report the accident to the approaching vehicles within that zone. In[10], authors have presented a Geocast routing protocol by submitting design architecture of RObust VEhicular Routing (ROVER). In ROVER, only control packets are flooded in the network and the data is disseminated using unicast approach that in turn increases the efficiency and reliability of the routing scheme. In ROVER, a ZOR is created as a rectangular window at the back of the source node. The dimensions of the window created are defined as length (L) and width (W) respectively. The size of the window is decided such that all of the lanes on the current road are covered. The node (vehicle) will accept the message if it receives it while it was in ZOR and reject it if it is not within that zone. It was shown in[10] that ROVER presents better results for low density environments. In[14], authors have presented a geographic routing scheme, GROOV, for both city and highway scenarios based on the geographical routing strategy presented in[15]. GROOV is based on the idea of finding the most suitable relay node rather than on the greedy selection criteria. Most of the greedy selection schemes are based on improving the average end-to-end delay while compromising on PDR. It is shown that GROOV achieves higher PDR compared to the routing algorithm presented in[15] for city environment. In order to localize the search space by using node positions and map information, there are few techniques which are based on this idea. In[16], authors have presented a context based routing protocol, VCARP, which uses vehicles information such as destination, location and packet cache state to make optimal routing decision. The packet retransmissions are avoided by storing them temporarily in a cache. Simulations studies have shown that VCARP achieves better PDR and reduces the routing overheads in VANET scenarios. Another vehicle assisted routing protocol for VANET is presented in[50] and is called Vehicle Assisted Data Delivery in Vehicular Ad-hoc Network (VADD). In this protocol authors adopted the concept of carry and forward. Four different variants of VADD are presented and their performance is compared with each other. It is shown that the proposed VADD protocols have better performance in terms of PDR, Average End to End delay and routing overheads compared to other existing protocols. Among the different variants of VADD, the H-VADD out performs the other three.
4. Security in VANET
- Security in VANET should be considered as important as securing other networks in computing. Due to the highly sensitive nature of information being broadcasted via VANET, all applications designed for vehicular network need to be protected from malicious manipulation. Imagine the possibility of a critical message been manipulated and the harm it will cause if not detected. In addition to that, comfort and quality applications in VANET need to be protected to prevent loss of revenue. Various consortiums like Network on Wheels (NOW)[51] and Secure VehicularCommunications (SEVECOM)[52] are running with prime focus of addressing security issues within the vehicular networks. As per basic computer and network security definitions[53], attacks on a computer network can be classified in three main groups of threats; threats associated with Authenticity, Confidentiality and Availability of the resource. If one applies this model of security on vehicular network, the one threat that really stands out is the Confidentiality of the source. For example, an attacker who is busy in analysing which certificates are attached to each message distributed in the system, might also be able to track the exact location of the vehicle (compromise of privacy). Currently a broadcast authentication scheme is utilised in current standards of security for VANET such as IEEE 1609.2. This scheme is based on the use of a public key signature. Broadcast authentication enables the receivers to verify that received information was really sent by the claimed sender. In order to protect the privacy of the node, few approaches have been adopted[54],[55]. In[54], authors presented an approach of loading each vehicle with multiple certified public keys instead of only using one default key. In another approach[55], authors have presented a scheme of using pseudonym pools of identifiers in which vehicles are allowed to switch between different identities. One limitation of these approaches is that they put undue processing constraints on the network that is already being pushed to the limit due to the lack of bandwidth. In order to understand how to develop a secure vehicular network, one has to really consider the ‘Attacker Model’ and the types of attacks which are encountered in VANET. Usually attackers are led by their own motives like curiosity, malignity or just a competitive spirit. An attacker might have access to inside knowledge and can be classified as an inside attacker which poses same level of threat as an outside attacker. A better approach in VANET security could be to provide an authentication mechanism to each node. In[56], authors have presented such a security method which encourages the nodes to provide a secure sender authentication. Due to the large number of independent network members (vehicles) and the existence of human factor, misbehaviour can take place. So an authentication trust needs to be established. In VANET security, the attack threats can be classified into different categories. In[57], authors have described three key types of attacks: Bogus Information:- An inside attacker can make bogus safety messages to be distributed in the entire network. This can cause disastrous situations (a threat to Authenticity). ID Disclosure:- Location information in relation to vehicle’s exact position (privacy) needs to be protected (a threat to Confidentiality). Denial of Service:- Attackers can potentially flood the entire network so that no one will be able to use the applications/services. Such circumstances can create catastrophic situations if triggered instantaneously (a threat to Availability). The two key challenges in relation to providing a secure communication in VANET can be briefly classified as establishing a robust system of sender authentication and providing a mechanism to keep the user location undisclosed. Since vehicles are boosted with sufficient processing power, the computational resources needed for applying cryptographic techniques in real-test bed should not be a concern. On the other hand, if needed to be implemented in virtual (simulated) environment, computational resources required such as speed of processor and desired memory will need to be looked into.
5. Key Research Areas and Challenges
- Although there has been an ample amount of research in VANET, still there are many areas which need to be looked into. Due to the different nature of VANET form many other wireless communication networks and hard design requirements, there are many interesting research problems in this field. The paper summarizes some of the key research areas and challenges as under. However, it must be noted that the research challenges in VANET are not limited to only these areas. (a) Quality of Service (QoS): Provision of certain quality of service levels in VANET is an important task. A network with minimum delay for data delivery, less retransmissions, and high connectivity time can provide certain QoS guaranteed to the users. Promising this kind of QoS with different user applications and dynamic network environment is an interesting and challenging task in VANET design. (b) Efficient Routing Algorithms Design: In order to timely and properly sending data packets from one node to another node an efficient routing algorithm is required. In VANET, efficient routing algorithm means a routing scheme with minimum delay, maximum system capacity and less computational complexity. Design such an algorithm which can be implemented in multiple topologies of the network and satisfies all of the above mentioned properties is an active area of research in VANET. (c) Scalability and Robustness: Designing a scalable and robust network remains an open area of research in VANET because of its challenging characteristics. Many design approaches fall short when VANETs transform from sparse to high dense mode, or from high mobility to slow traffic scenarios. A complete VANET framework that is scalable to different network scales and robust to the topological changes is required. This is an emerging area of research for VANET environment. (d) Co-operative Communication: A key challenge in VANET is establishing the communication among different nodes. Different concepts of co-operative communication from wireless network theory may not be directly applied to VANET. This co-operative communication, such as up to which extent nodes should exchange information among themselves, is one of the key research areas in the VANET design. (e) Network Security: As the nodes in VANET environment seek exchange of information among each other all the time, making sure that certain critical privacy information remains within the concerned node is an important design aspect. Designing a proper authentication mechanism and a trust based security protocol is an interesting and open research area in VANET.
6. Conclusions
- This paper presented an overview and tutorial of various issues in VANET. Various types of research challenges are highlighted in context of vehicular communication. In particular, this paper presented a review of VANET architecture, transmission modelling, mathematical aspects of signal modelling, routing protocols and security. A comparative analysis of different routing algorithms in the field of VANET has been presented. It also highlighted the main issues in routing algorithms. The performance metrics for routing algorithms, discussed in this paper, were PDR with respect to average velocity of vehicles, node density and system throughput. The other parameters of interest discussed widely in the paper were average end-to-end delay and routing overheads. The paper concluded that some algorithm perform well in urban environment while others are suitable for highway environment. It was also concluded that proper modeling techniques are necessary for designing a seamless communication in VANET for a particular environment. Finally, main research challenges and areas of interest in vehicular communication were discussed.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML