-
Paper Information
- Next Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Journal of Wireless Networking and Communications
p-ISSN: 2167-7328 e-ISSN: 2167-7336
2012; 2(3): 11-13
doi: 10.5923/j.jwnc.20120203.01
A Method in Computing Successive Interference Canceller
Hoa Tran
Computer Information Sciences Department, Fordham University, Bronx, 10458, USA
Correspondence to: Hoa Tran, Computer Information Sciences Department, Fordham University, Bronx, 10458, USA.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Successive Interference Canceller is a multistage approach that sequentially recovers each user from the received signal. Each stage provides an estimate using the MF detector. The re-modulated signal is subtracted from the original signal and the difference signal becomes the input. Bit Error Rate expressions are derived to evaluate performance of the SIC and its algorithm.
Keywords: DS/CDMA, SIC, BER, PIC, Error probability, MAI, Optimum Detector
Article Outline
1. Introduction
- Multiuser Detection is developed for CDMA uplink systems and other environments in which the receiver has knowledge of the signature waveforms for K users. Subspace techniques are used to estimate the interference from the unknown users and the interference estimate is subtracted from the received signal. It can be difficult to recover CDMA signals, primary because the received power levels may be spread over a wide range among the users. We focus on a multistage algorithm called the successive interference canceller (SIC) which uses a single antenna element to sequentially recover CDMA signals according to their power levels[2]. Bit error rate (BER) expressions are derived to evaluate the performance of the SIC for near-far scenarios[5]. We also examine a parallel interference canceller (PIC) which is similar to the SIC except that all users are estimated simultaneously in each stage.
2. Multiuser Detection
- Consider a DS/CDMA system where K active users transmit their information asynchronously over a common additive white Gaussian noise (AWGN) channel[4]. The received signal impinging on a single antenna element at the base station can be modeled as
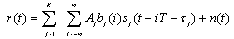 | (2.1) |
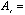 recived apmplitude of the jth user,
recived apmplitude of the jth user, 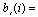 transmitted symbol ( ± 1) of the jth user,
transmitted symbol ( ± 1) of the jth user, 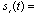 signature waveform of the jth user,
signature waveform of the jth user, 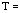 symbol interval,
symbol interval, 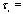 time delay of the jth user, and
time delay of the jth user, and 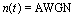 with zero mean and a two-sided power spectral density.A signature waveform can be represented by
with zero mean and a two-sided power spectral density.A signature waveform can be represented by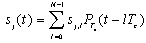 | (2.2) |
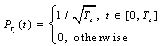 Multiple access interference (MAI) is caused by nonzero cross-correlations between the signature waveforms; it is the limiting factor in a DS/CDMA system[13]. The (k, j)th component of the cross-correlation matrix R(l) for time- shifted versions of the signature waveforms of the kth and jth users is given by
Multiple access interference (MAI) is caused by nonzero cross-correlations between the signature waveforms; it is the limiting factor in a DS/CDMA system[13]. The (k, j)th component of the cross-correlation matrix R(l) for time- shifted versions of the signature waveforms of the kth and jth users is given by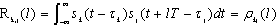 | (2.3) |
3. Conventional and Optimum Detector
- The sampled output of the matched filter of the jth user in the mth symbol interval is
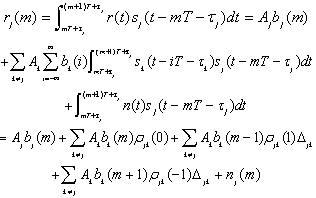 | (3.1) |
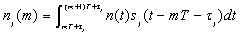 | (3.2) |
4. Successive Interference Canceller (SIC)
- Successive interference cancellation is a multistage approach that sequentially recovers each user from the received signal[15]. Each stage provides an estimate of one source by using the conventional MF detector[14]. The transmitted symbol of the jth user in the mth symbol interval can be determined by
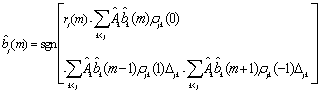 Where
Where 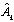 is the estimated amplitude of the kth user.For the case of synchronous channels,
is the estimated amplitude of the kth user.For the case of synchronous channels,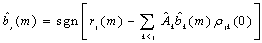 | (4.1) |
5. Parallel Interference Canceller (PIC)
- The PIC is another multistage nonlinear receiver that can be used to separate and demodulate co-channel signals in a DS/CDMA system[11,12]. The decision variables in the mth stage can be written as:
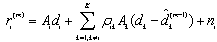 Consider the estimate in the first stage:
Consider the estimate in the first stage: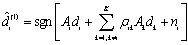 | (5.1) |
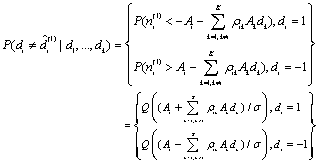 | (5.2) |
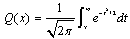 | (5.3) |
6. Group-Blind Detector for Asynchronous CDMA
- The received signal due to user k (1< k < K) is given by
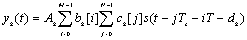 | (6.1) |
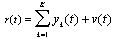 | (6.2) |
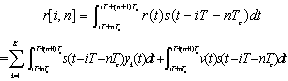 | (6.3) |
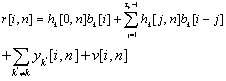 | (6.4) |
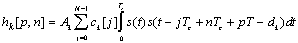 Denote
Denote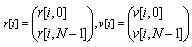
7. Numerical Results
- We consider a DS/CDMA system with ten users and spreading codes of length N=64. Ten million events were generated using Monte-Carlo simulations to estimate the error probabilities.The below table shows the Correlation Values
 of the spreading codes for a Ten- User DS / CDMA system.
of the spreading codes for a Ten- User DS / CDMA system.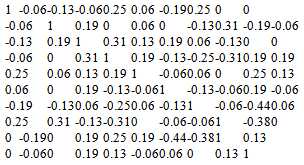 As a result, estimates of the error probabilities on the order of 10As a result, estimates of the error probabilities on the order of 10-5 (or higher) are quite reliable. Note that most of the cross-correlation coefficients are in the range (-0.2, 0.2); the noise variables are approximately uncorrelated.
As a result, estimates of the error probabilities on the order of 10As a result, estimates of the error probabilities on the order of 10-5 (or higher) are quite reliable. Note that most of the cross-correlation coefficients are in the range (-0.2, 0.2); the noise variables are approximately uncorrelated.8. Conclusions
- In this paper, we described SIC and PIC algorithms for DS/CDMA signals, and analyzed their BER performance using conditional probability methods. An analysis of the BER performance of the SIC for a two-user DS/CDMA system illustrated the effects of erroneous cancellation and amplitude mismatch. With reference to single path, a robust multiuser detector for non-coherent detection signals has been implemented. A novel blind multiuser detector is derived for joint multiuser detection and differential decoding, which can be efficiently implemented using Monte Carlo procedure.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML