-
Paper Information
- Next Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Journal of Wireless Networking and Communications
p-ISSN: 2167-7328 e-ISSN: 2167-7336
2012; 2(1): 1-4
doi:10.5923/j.jwnc.20120201.01
Wireless Audio/Videoless Communication Between Miners Working Underground and Control Station at Surface
Jagdish Lal Raheja
DSG Group, CEERI Pilani
Correspondence to: Jagdish Lal Raheja, DSG Group, CEERI Pilani.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Disasters in coal mines are very common and keep appearing frequently in our country as well as in the other countries in different parts of the world. Analysis on these accidents shows that most of the accidents are related to human factors. It affects the efficiency of the miners and that in turn affects the productivity of the mines. Several technologies are emerging to prevent and mitigate the disasters. The systems based on these technologies employ some software or other, for communicating the occurrence of disaster and persons trapped in it. A large number of communication software are developed and installed in coal mines all over the world. However, in most of the case, the mode of communication between the miners and the control station is either audio or video. These kinds of communications include the personal involvement of the miner as he has to convey his state of health visually/orally to the control station. This involvement not only hampers the working of the miner but also slows down the communication speed as well. In view of this it is proposed to develop data communication system through software and hardware (MineCom), which is going to inform the central control room about the disaster having occurred and its location.
Keywords: Mine Communication, OOAD, Animation, GSM, Physiological Details
Cite this paper: Jagdish Lal Raheja, Wireless Audio/Videoless Communication Between Miners Working Underground and Control Station at Surface, Journal of Wireless Networking and Communications, Vol. 2 No. 1, 2012, pp. 1-4. doi: 10.5923/j.jwnc.20120201.01.
Article Outline
1. Introduction
- Disasters in coal mines are very common and keep appearing frequently in our country as well as in the other countries in different parts of the world. Analysis on these accidents shows that most of the accidents are related to human factors. It affects the efficiency of the miners and that in turn affects the productivity of the mines. Several technologies are emerging to prevent and mitigate the disasters. The systems based on these technologies employ some software or other, for communicating the occurrence of disaster and persons trapped in it. A large number of communication software are developed and installed in coal mines all over the world. However, in most of the case, the mode of communication between the miners and the control station is either audio or video. These kinds of communications include the personal involvement of the miner as he has to convey his state of health visually/orally to the control station. This involvement not only hampers the working of the miner but also slows down the communication speed as well. In view of this it is proposed to develop data communication system through software and hardware (MineCom),which is going to inform the central control room about the disaster having occurred and its location. Therefore, it improves the safety by enabling real-time access to critical information about the miners.Communicating within an underground coal mine environment is quite challenging [3,4]. Various technologies have been applied in the past. One of the well known communications is leaky feeder where normal coaxial cable is designed to pass radio frequency (RF) signals from one end of the cable to the other with varying degrees of loss, dependant on the quality. The purpose of the cable’s outer copper shield is to keep as much signal as possible inside the cable and prevent external RF signals and/or interference from entering the cable. However the external copper shield on a Leaky Feeder cable has ‘holes’ or ‘gaps’, allowing the RF signals to leak out evenly along its length, so that it can be picked easily[1,2]. However, The optimum efficiency of a leaky cable as a support for radio communications in tunnels involves a compromise between high leakage fields and a low increase of the coaxial mode attenuation. The latter is an important disadvantage of continuous leaky feeders. Another approach is to use wireless technology such as mobile based on GSM technology. However, it is not possible for the signal to reach out to the miners working underground as there is lot of turns and bends in the galleries. Therefore we have applied a combination of wire and wireless technologies to develop the signal. Data communication from the surface to the mine galleries is through wire and from there on it is wireless up to the miners working there.
2. Overview of the System
- The MineCom software works as a standalone. It consists of PC, its serial port, Base stations and miner’s kit hardware. The system is depicted using a block diagram in figure 1. PC is connected to base stations through RS232/RS485. These base stations are in turn connected wirelessly through miner’s kit. The location of the base station is fixed and is know at priory while miner having a miner kit may move from one place to another. However it is assumed that a miner is moving in a predefined path and is always in the communication network. In case he moves out of the network coverage, it is missing/out of range status is passed to the control software at the surface.
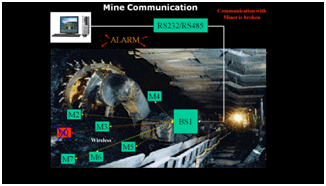 | Figure 1. System overview |
3. Algorithm
4. Features of MineCom
- MineCom is a low cost PC based system. One of its components, the serial communication using RS232/RS485 connects the PC to the Base stations (Base station is a hardware, which receive the data from the PC and then send back its response) lying underground in the mine. Once this software is started, it initializes the communication with the base station by sending few bytes of information. It then waits for the input from the base stations and processes it, once received.The major features of it are discussed below:
4.1. Initialization
- Once the program has started as shown in figure 3, it asks the user to choose the baud rate from the possible four options. These options are 300,600, 1200 and 2400. By default the selected baud rate is 1200. The next option is the selection of serial com port from the two ports: COM1 & COM2. With these parameters set, communication gets started.
4.2. Communication
- The communication starts by sending a block of four bytes to each base station(s) located underground in the mine. Each byte of this block of four bytes has the following interpretation. First byte is the ID of the source i.e. the PC ID. Second byte is the ID of the base station. Third byte is the ID of the miner attached to the base station and fourth byte is the byte containing the additional information.
| |||||||||||||||
4.3. Search of a Miner
- Miners working underground are free to move in the galleries. Sometimes, it may be needed to search a given miner to know his location. It can be done by entering his identification number. It then searches the location of the miner and if succeeded, displays it textually on the screen.
4.4. Emergency warning
- It may happen that during emergency, there is need to inform all the miners working in the underground mine to come out or to take shelter in the non-hazard places. So a user, sitting at the surface, can warn them by sending emergency alarm. By pressing this button, a typical beep coming out of the miner kit will alarm the miner.
4.5. Miner’s physiological details
- All the relevant physiological details of the miners are stored in the Data bases. They are also displayed on the screen. User can select a miner ID to see his details.
4.6. Data base support
- All the information regarding the active base stations and miners physiological and other details is stored in the data base. It is read automatically within the software and only those base stations and miner’s kit are activated which are stored in the data base. Therefore there is no need to enter these details online every day.
4.7. Graphic animation
- Apart from the information about the base station and miners in text format, there is an option to switch to animation also. It animates a miner’s status (i.e. working, missing or buried under debris). It also displays base station in two situations i.e. working normally or disconnected.
4.8. Other information
- User can also see how many base stations are there in the mine along with their locations and number of miners attached to each base station. This information is only for the active base stations. i.e. base stations which are part of the active communications.
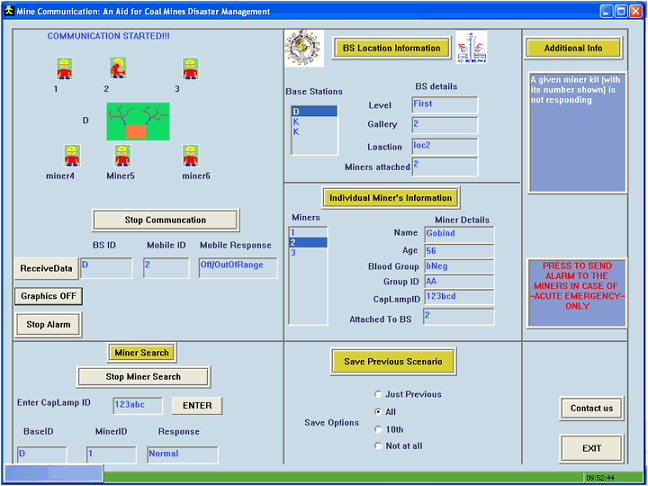 | Figure 3. Object Oriented Analysis and Design (OOAD) |
5. Methodology
- In the recent past, software was designed around functions or blocks of statements which manipulate data. This is called the procedure-oriented way of programming and has the disadvantage of the difficulties of reasoning about programs and to some degree difficulty of parallelization. However MineCom has been developed using the concept called the object oriented analysis and design (OOAD) [5-7]. It started with the understating of the problem and thorough interaction with the users. It resulted in identifying various objects, these objects were then defined as logical software objects that were ultimately implemented in a programming language i.e. C++. Using C++, the whole program is divided into various classes. The use of a class of programming languages and techniques based on the concept of an "object” which is a data structure (abstract data type) encapsulated with a set of routines, called "methods”, which operate on the data. Operations on the data can only be performed via these methods, which are common to all objects that are instances of a particular "class”. Each class combines data and functionality and wrap it inside what is called an object. Some of the advantages of OOP are1. Makes development faster, you don't need to write code again and again.2. Generic classes can be created that can be used in different projects.3. One can change logic by writing minimum code.4. It is best programming practice to use OOPs in software development field Using the OOAD.Using the OOAD methodology based CASE TOOL, the various classes were generated [8,9]. Individual classes and their relations to other classes are shown in figure 4.Some of the classes identified are :●. StartUp: It deals with the setting up of communication parameters. E.g. baud rate, serial communication port etc.●. CMineComDlg: It is the major class which interact with other classes to start communication and displays the online status of the miners●. Miner: It consists of miner’s details.●. MinersData: For miners’ data base management.●. SnPorts: A class for serial communication.●. CColorCtrl: For graphical display●. CColorCtrEx :For graphical display●. CBlinkCtrEx : For graphical display●. DispMiners: For animation of miners.
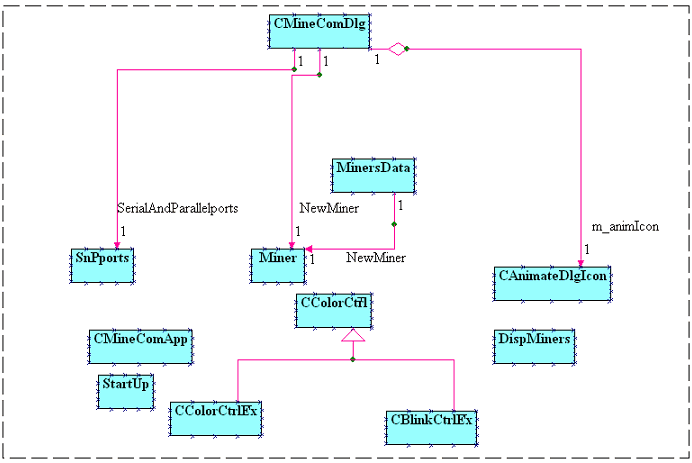 | Figure 4. IVarious classes and their relationships |
6. Multithreading
- Another characteristic of the software is that it is based on multi threading concepts. It means being multithreaded software has many independent parts. Each part of such a program is called a thread, and each thread defines a separate path of execution. Therefore it is capable of running two or more of its parts concurrently. The main advantage of multithreading is that it helps us to write very efficient programs because it lets you utilize the idle time that is present in most programs. Any of the thread can be ready to run as soon as it gets CPU time and can be suspended, which is a temporary halt to its execution. It can then later be resumed. Further a thread can be blocked when waiting for a resource or a thread can be terminated, in which case its execution ends and cannot be resumed
7. Conclusions
- In this paper we discussed the audio & video less communication between the miners working under ground and supervisor sitting in the control room at the surface. It works without much interaction from the supervisor and without interrupting the miners. It also store the history of the miners movements.
ACKNOWLEDGMENTS
- This research work was carried under the network project Development of an Electronic System for Location of Trapped Miners in Coal Mines for Jharia Coal Field between CEERI PILANI and CIMFR, Dhanbad. My thanks to Director, CEERI, Pilani for supporting this research work and Director, CIMFR, Dhanbad for field trial under the coal mines.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML