-
Paper Information
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Networks and Communications
p-ISSN: 2168-4936 e-ISSN: 2168-4944
2020; 10(1): 10-19
doi:10.5923/j.ijnc.20201001.02

Optimized Trust-Based DSR Protocol to Curb Cooperative Blackhole Attacks in MANETs Using NS-3
Ephantus Gichuki Mwangi, Geoffrey Muchiri Muketha, Gabriel Ndung’u Kamau
School of Computing and Information Technology, Murang’a University of Technology, Murang’a, Murang'a, Kenya
Correspondence to: Ephantus Gichuki Mwangi, School of Computing and Information Technology, Murang’a University of Technology, Murang’a, Murang'a, Kenya.
| Email: |  |
Copyright © 2020 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

MANETs Communication relies on special routing protocols that make security a challenging endeavor. MANETs are open to a range of active and passive attacks; black hole attack is an active attack affects the network layer. Cooperative black hole attack is a form of denial of service attack comprised of more than one black hole nodes that collaborate in order to drop data packets during communication process. In our study, we used the concept of trust to extend the DSR protocol in order to mitigate cooperative black hole attacks that leads to loss of data packets. The paper proposes an Optimized Trust-Based Dynamic Source Routing protocol. The proposed protocol integrates dynamic trust and friendship functions in the standard DSR protocol. The proposed protocol was designed, implemented and simulated in Network Simulator version 3 (NS-3). Simulation results indicate that the proposed protocol is superior to standard Dynamic Source Routing (DSR) protocol and Ad hoc On Demand Vector (AODV) protocols used as the benchmark protocols; in terms of packet delivery ratio, routing overhead and end-to-end delays and throughput used as performance metrics. The Optimized Trust-Based DSR protocol had a packet delivery ratio of above 95%, routing overhead of about 4.75% and an end-to-end delay of between 0.9 seconds and 1.65 seconds and a throughput of 95.6 Kbps.
Keywords: Routing protocol,Trust-Based Routing, OTB-DSR Protocol, Cooperative Blackhole and Composite Trust Values
Cite this paper: Ephantus Gichuki Mwangi, Geoffrey Muchiri Muketha, Gabriel Ndung’u Kamau, Optimized Trust-Based DSR Protocol to Curb Cooperative Blackhole Attacks in MANETs Using NS-3, International Journal of Networks and Communications, Vol. 10 No. 1, 2020, pp. 10-19. doi: 10.5923/j.ijnc.20201001.02.
Article Outline
1. Introduction
- The advent of mobile devices brought a paradigm shift in network communication. Mobile technology has led to the emergence of Mobile ad hoc networks (MANETs). MANETs are special types of wireless networks comprised of mobile nodes [1]. The network is infrastructureless and has no centralized management. Nodes in MANETs freely join and leave the network at their own will, hence making the network topology highly dynamic. The nodes cooperate in forwarding data packets from source to destination using special routing protocols. The protocols used in wired networks are not applicable to wireless networks [2]. Each node in a MANET has a transceiver gadget which makes it to acts as both a router and a host. A node intending to communicate with other nodes in MANET establishes a route using the special routing protocols [1].Several routing protocols have been designed to optimize MANETs routing security [2], [6]. The design of secure routing protocols has been surrounded by design issues such as dynamic network topology, constrained bandwidth, limited battery power, error prone wireless channel, and unpredictable node mobility. The unique features of MANETs make most of the security solutions designed for wired networks inappropriate for mobile ad hoc networks. Further, the dynamic nature of MANETs makes it difficult to develop secure ad hoc routing protocols [3].The aim of our study was to develop an Optimized Trust-Based DSR protocols by extending the standard DSR protocol using dynamic trust and friendship functions. The purpose of dynamic trust function was to calculate trust values for the individual nodes in MANETs based on how successful or unsuccessful they forward data packets to their immediate neighbours. Further, friendship function was used to classify nodes in various levels of friendship based on composite trust values (CTVs) generated from the dynamic trust function. MANETs routing protocols are categorized as: reactive routing protocols (on demand), proactive routing protocols (table driven) and hybrid protocols. In reactive routing protocols routes are created on-demand whenever a source node intends to send data packets to a destination node. This means that only nodes which participate in active routes maintain the routing information. Ad hoc On-demand Distance Vector (AODV), Dynamic Source Routing (DSR) and Link Aware Routing (LAR) are some of the examples of reactive routing protocols [6]. In proactive protocols, each node maintains complete routing information of the network in a routing table. Change in the network topology due to nodes mobility leads to automatic updating of routing tables in all the nodes. Examples of proactive routing protocols are Destination Sequenced Distance Vector (DSDV), Global State Routing (GSR) and HSR. Hybrid protocols are as a result of blended features of both proactive and reactive routing protocols [4].MANETs Routing protocols govern how data packets flow from source to destination nodes [1]. The uniqueness of MANETs has exposed these protocols to a variety of attacks. The attacks can either be from within or outside the network. Studies conducted in this domain indicate that there is need to enhance existing MANETs routing protocols so that they can effectively mitigate network attacks as they transmit data with higher efficiency [6]. DSR is a reactive routing (on-demand) protocol that relies on the concept of source routes in order to transmit data packets. It uses two primary mechanisms; route discovery and route maintenance. When a source node wants to transmit some data packets, it initiates a route discovery mechanism by first searching for a source route from the routes saved in its routes’ cache. The source routes are maintained by every node in the network. If no source route is found in the sending node’s cache, it initializes route request process by sending a RREQ packet to its immediate neighbours. The nodes using DSR protocol carries complete routing information from source to destination node in its packet header. However, the routes in the cache may be stale or broken. The DSR protocol uses route maintenance mechanism to validate all its source routes. The mechanism is managed using route error messages or acknowledgements. Previous studies show that the DSR protocol suffers some transmission inefficiencies attributed to broken links, invalid routes and inability to effectively identify malevolent nodes in the network during source routes establishment [6]. The concept of trust among nodes in MANETs can be used to identify and eliminate malicious nodes in a network [7], [8]. Further, trust can be used to determine the degree of reliance among interacting nodes. Additionally, trust can be used to determine which entities belong to which circle of friendship. Trust is dynamic; a member of a certain circle of friendship can be promoted to a higher circle or demoted to a lower one depending on the variance of trust. Furthermore, every circle of friendship can be assigned a level of trust.The rest of the paper is organized as follows; section one introduces the paper, section 2 discusses the related works, while section 3 presents a trust model, section 4 presents trust based routing, section 5 presents protocol’s algorithms, section 6 describes simulation environment, section 7 presents results and discussion, and section 8 presents conclusions and future work.
2. Related Work
- El-Haleem and Ali [10] proposed a two node-disjoint routes protocol for Isolating Dropper (TRIDNT) in MANETs. TRIDNT permits some degree of selfishness to a selfish node. This gives it a chance to declare itself to its neighbors as selfish, hence reducing the misbehaving nodes searching time. When a malicious behaviour is detected within the paths, then the path searching tool automatically starts to detect and isolates them. TRIDNT protocol was not simulated; its performance analysis relied on mathematical model which is not sufficient to validate this protocol.In [11], Airehrour, Gutierrez and Ray proposed GradeTrust, a Secure Trust Based Routing protocol for MANETs. GradeTrust is based on trust levels of network nodes. In this protocol, all nodes are categorized into three sets namely: trusted friends (TF), friends (F) and possible friends (PF). During the routing process GradeTrust uses the three trust metrics to compute secure routes. These trust metrics help in isolating routes with black hole nodes. In terms of performance metrics, that is packet delivery ratio, end to end delay and trust compromise; GradeTrust protocol performed much better than AODV and DSR used as the benchmark schemes. However, on average the packet delivery ratio of GradeTrust was below 80% and decreased with increase in speed of node mobility. Further, trust compromise increased with increase in the number of nodes in the presence of black hole nodes.Sultana and Ahmed [12] implemented a secure AOMDV protocol using Elliptic Curve Cryptography (ECC) to prevent loss of data packets from malicious attacks in the network. AOMDV a reactive routing protocol is an extension of AODV routing protocol. ECC is an encryption technique which provides security with smaller key size compared to other public key encryption. Simulation experiment was configured in three different kinds of environments: secure environment without malicious nodes, hostile environment with black hole attacks and an environment with ECC implementation by the agent. Simulation results showed that AOMDV is more superior to standard AODV protocol, although not completely restraint from all types of attacks. The study did not indicate whether AOMDV protocol is sufficient enough to mitigate collaborative attacks.In [13] Sreenath at al. proposed an algorithm using Secure Enhanced-On Demand Multicast Routing Protocol (EODMRP). The algorithm focused on improving the security of MANETs against multicast attacks. The proposed algorithm was implemented and tested using GloMoSim (2.03). Further, after simulation, performance analysis showed improvement in packet delivery ratio in presence of black hole attack, with marginal rise in average end to end delay and normalized routing overhead. Additionally, simulation showed that this technique worked well for flooding attacks even when the identity of the malicious nodes was unknown. This mechanism did not use any additional network bandwidth during data transmission. However, the mechanism was only intended for multicast routing protocols. There is a need to extend this study by developing a solution for proactive protocols through the change of implementation techniques.Jhaveri [14] proposed a modified RAODV (MR-AODV) protocol, an enhancement of R-AODV protocol. This protocol was subjected to varying network size, mobility, traffic load and malicious attacks through a simulation process. Simulation results showed that MR-AODV isolates black hole nodes during route discovery phase just as R-AODV and sets up a secure route for data transmission. The study showed that MR-AODV protocol was superior to R-AODV protocol used as benchmark; hence a better solution for MANETs against black hole attacks. However, MR-AODV protocol needs further enhancement to improve network efficiency in terms of packet delivery ratio as the number of malicious nodes increases. Further, the MR-AODV protocol needs to be enhanced in order to mitigate cooperative black hole attacks.Gupta and Woungang [15] proposed a trust-based security protocol (TSP) against PRoPHET (PBH scheme) routing protocol for opportunistic networks (Oppnets). The aim of the study was to compare the effectiveness of the two protocols. Simulation results showed that the PBH scheme led to higher wastage of network resources while the TSP contributed in reduction of network bandwidth usage by avoiding the additional message replicas that would have been transmitted to the black hole nodes. These findings indicated that TSP is a better routing protocol to curb black hole attacks than PBH scheme. However, TSP needs to be enhanced in order to provide the following functions: calculation of the SGV values in case of randomized behavior of malicious nodes, calculation of credits for evaluation of the trust values of nodes and capturing node’s relative delivery probability for higher trusted. Further, TSP needs to be enhanced to be able to detect and prevent cooperative black hole attacks.In [16], Arya et al. recommended a trusted AODV routing algorithm for detecting and mitigating collaborative black hole attacks in MANET. Simulation experiment indicated that in the presence of collaborative black hole attack AODV protocol used more energy than trusted AODV algorithm. Further, it was noted that throughput and packet delivery ratio of trusted AODV algorithm was better compared to AODV protocol. This was an indication that trusted AODV routing algorithm is a superior compared to AODV protocol and can do better in protecting MANETs against collaborative black hole attacks.Woungang et al. [17] introduced DBA-DSR a novel scheme for detecting blackhole attacks in MANETs. Simulation results showed that the proposed scheme performed better than DSR scheme in terms of network throughput and packet delivery ratio. However, this scheme needs to be extended in order to detect and prevent cooperative blackhole attacks in MANETs. Further, the throughput of proposed scheme needs to be enhanced as it was below 80%; while its end to end delay needs to be maintained to acceptable levels.The reviewed literature indicates some underlying gaps in existing protocols that led to the development of the proposed OTB-DSR protocol. The gaps are as follows; 1) most of the existing protocols do not have the capacity to mitigate cooperative blackhole attacks with a higher efficiency. This leads to compromised data transmission in MANETs. 2) Most of the existing protocols have not embraced the concept of trust based routing which can help in mitigating collaborative attacks.
3. The Proposed Trust Based Routing Management Model
- Trust based routing is a technique where nodes establish routes based on the level of trust amongst other nodes in a network. In this technique past experience, interactions and recommendations from other nodes forms the basis of trust. The technique establishes a mechanism of awarding trust values to a node which are finally used to promote it to different levels of trust based on aggregate successive transmissions. The trust values and trust levels help the source node to identify the most trusted nodes during route discovery. Nodes that successfully route data packets amongst their peers are considered more trusted than others and are awarded higher trust levels [20]. The study adopted the concept of Trust Based Routing in extending DSR protocol. The formula 1 below is a derivation of a trust management model based on human interaction concept. According to the formula, human trust is a fraction derived from the difference between successful and failed interactions attempts between any two persons divided by summation of successful and failed interactions attempts; multiplied by a time growth factor (TGF). The TGF is a variable that represents the growth or decay of trust with time.
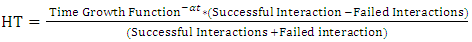 | (1) |
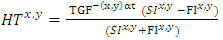 | (2) |
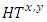 is the trust between any two interacting parties. The variable
is the trust between any two interacting parties. The variable 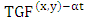 is a factor of growth or decay of trust over time. The expression
is a factor of growth or decay of trust over time. The expression 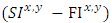 represents the difference between successful and failed interaction attempts between any two interacting parties. Further, expression
represents the difference between successful and failed interaction attempts between any two interacting parties. Further, expression 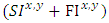 represents the summation of both successful and failed attempts between any two parties.In networking environs, the interactions of nodes can be equated to the behaviour of human beings in social networks as indicated in formula 2. Further, trust among nodes in a MANET can be quantified through a model. In our study, we derived a trust management model based on how nodes build trust based on the interactions amongst themselves overtime. The basis of this trust is anchored on both positive and negative interactions among interacting the nodes. To demonstrate how this trust relationship can be modeled and quantified among neighbouring nodes in a MANET, equation 3 was adopted as the basis of our model.
represents the summation of both successful and failed attempts between any two parties.In networking environs, the interactions of nodes can be equated to the behaviour of human beings in social networks as indicated in formula 2. Further, trust among nodes in a MANET can be quantified through a model. In our study, we derived a trust management model based on how nodes build trust based on the interactions amongst themselves overtime. The basis of this trust is anchored on both positive and negative interactions among interacting the nodes. To demonstrate how this trust relationship can be modeled and quantified among neighbouring nodes in a MANET, equation 3 was adopted as the basis of our model.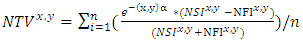 | (3) |
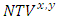 is the composite node’s trust value,
is the composite node’s trust value, 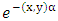 is an expression that shows the growth on nodes trust with time. Further, expression
is an expression that shows the growth on nodes trust with time. Further, expression 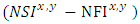 shows the difference between successful and failed interactions attempts between two nodes. Additionally, expression
shows the difference between successful and failed interactions attempts between two nodes. Additionally, expression 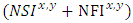 is the summation of both successful and failed interactions. Finally, n is an integer value that represents the total number of nodes that recommend trust to a certain node.
is the summation of both successful and failed interactions. Finally, n is an integer value that represents the total number of nodes that recommend trust to a certain node.4. Design of the Proposed OTB-DSR Protocol
- This study has extended standard DSR protocol using Dynamic Trust and Friendship functions which were informed based on the concept of trust values and levels discussed above. The two parameters formed the basis of classification of nodes in our proposed OTB-DSR protocol.
4.1. Architecture of OTB-DSR Protocol
- The proposed protocol is made up of two key segments: Optimized Trust Manager and the Standard DSR protocol. Figure 1 shows the interrelationship of the various components in the architecture of the proposed Optimized Trust-Based DSR protocol. The DSR protocol forms the core segment and directly interacts with the Optimized Trust Manager. The Optimized Trust Manager is made up of three components: Dynamic Trust Function, Friendship Function and Route Selector. The three components are interrelated and directly interact with each other during route discovery in order to establish the optimal route from the node’s cache.
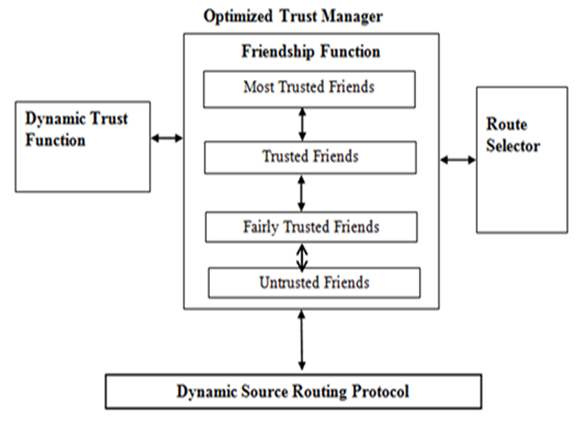 | Figure 1. OTB-DSR Protocol Architecture |
4.2. Design of the Dynamic Trust Function
- The purpose of this function is to calculate Composite Trust Values (CTV) of every node in the network using a trust model. The principle behind Composite Trust Value calculation is earning or losing points bases on successful/unsuccessful packet transmissions to its immediate neighbours. In this technique, the next hope neighbours of every node has the responsibility of continuously recommending Trust Values (TVs) by sending acknowledgement packets (ACK) when they receive data packets successfully. A node which successfully transmits a packet to its next hop neighbour is appraised by one point which is automatically incremented in CTV and stored in the Trust Wallet (TW) of a node. In case a node fails to forward a data packet to its immediate neighbour either due to selfishness or malicious intentions, a negative acknowledgement (NACK) is sent. A NACK makes a node lose a point which is automatically decremented from CTV of a node. Nodes joining the network for the first time are automatically assigned CTV of zero (0) points. The TVs from all immediate neighbouring nodes are then forwarded to the node’s routing table in order to compute CTV; which is finally stored in the TW. Equation 4 shows how CTV are computed for an individual node in a given route.
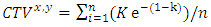 | (4) |
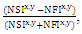 i represent the number of neighbouring nodes recommending Trust Values and n represents the total nodes that participated in trust recommendation (whether positive or negative recommendation).The CTVs for nodes in a certain route are used to calculate Route Trust Value (RTV) for that route. Equation 5 shows how Route Trust Value (RTV) for a given route is computed.
i represent the number of neighbouring nodes recommending Trust Values and n represents the total nodes that participated in trust recommendation (whether positive or negative recommendation).The CTVs for nodes in a certain route are used to calculate Route Trust Value (RTV) for that route. Equation 5 shows how Route Trust Value (RTV) for a given route is computed.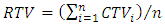 | (5) |
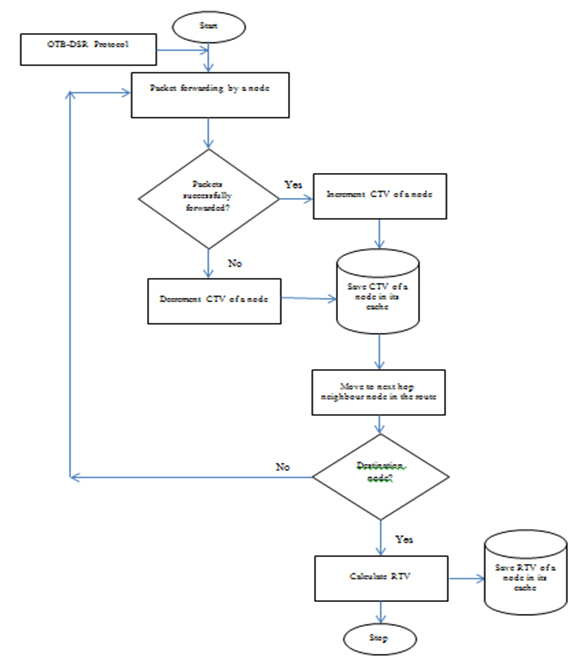 | Figure 2. Operation flowchart of the OTB-DSR Protocol |
4.3. Design of the Friendship Function
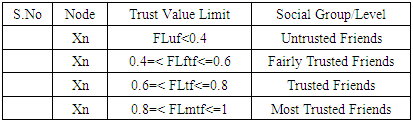
- This function uses threshold trust values to classify nodes into social friendship groups based on successful interaction experiences during data packet transmission. A node can be classified in any of the four friendship levels: Untrusted Friends, Fairly Trusted Friends, Trusted Friends and Most Trusted Friends. A node that joins the network for the first time is automatically assigned a Trust Value (TV) of zero points. Nodes cumulatively build their TVs based on successfully packet transmission to their immediate neighbours. Any node with TVs less than four points is marked as malicious node. The malicious nodes are not considered during routes formation unless they are the only existing nodes along that route. Nodes under Untrusted Friends level are the nodes that have met trust threshold value of four points by successfully forwarding data packets to their immediate neighbours’ atleast four times consecutively since they joined the network. A node under Fairly Trusted Friends level must first meet the trust threshold value of four points in order to be allowed to participate in data packet transmission. Further, the node must have successfully passed data packets to its one hop neighbours atleast two times consecutively since it was enrolled under Untrusted Friends level. Routes with nodes under this level have the least chances of being selected to participate in any packets transmission responsibility. Nodes that are promoted to Trusted Friends level are the nodes that have successfully passed data packets atleast more than two times since they joined Fairly Trusted Friends level. Route with nodes under this category have fair chances of being selected to participate in packet transmission. The Most Trusted Friends level belongs to nodes that have successfully passed data packets to their one hop neighbours atleast two times consecutively since they joined the Trusted Friends level and have never dropped any data packets since they joined the network. A source route with most of these nodes in the route cache has the highest chance of being selected for participation in packet routing. The equations 6 to 9 shows how nodes trust levels are classified into social friendship groups based on the successful interactions with immediate neighbours during data packet transmission.
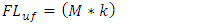 | (6) |
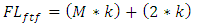 | (7) |
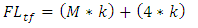 | (8) |
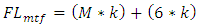 | (9) |
|
5. Algorithm
- This is a logical flow of steps that define a solution to an underlying problem. The study designed two algorithms for the dynamic trust and friendship functions. These algorithms give a detailed procedure of how the two functions were integrated in the DSR protocol.
5.1. Algorithm of Dynamic Trust Function
- The dynamic trust function algorithm awards individual nodes in a MANET trust points based on how successful or unsuccessful they interact with their neigbours. A node that successful passes a data packet to its neighbour is awarded trust value of one point. Further, any node that does not pass a data packet to its neigbour either due to selfish or malicious intentions is denied trust value of one point. The trust values are saved in Composite Trust Value field of a node’s data structure. The value in this field is updated every time a node participates in a data transmission process. The algorithm of Dynamic Trust Function is represented in figure 3. The algorithm is a sub module of the OTB-DSR protocol.
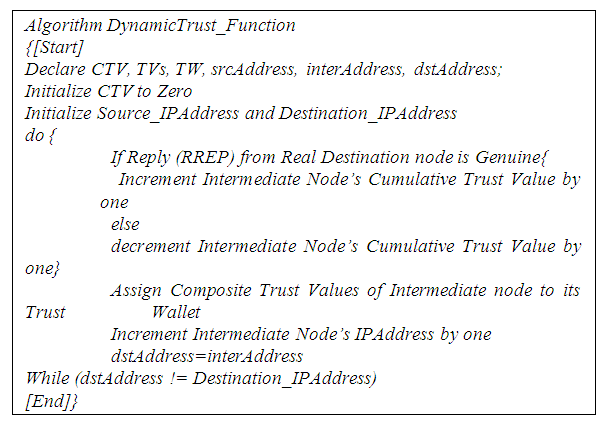 | Figure 3. Dynamic Trust Function Algorithm |
5.2. Algorithm of Friendship Function
- The friendship function is a sub module of the OTB-DSR protocol. The purpose of this algorithm is to classify nodes in different levels of trust based on composite trust values (CTV) awarded by their neighbours. In this algorithm, there are four levels of friendship; untrusted friends, fairly trusted friends, trusted friends and most trusted friends. Nodes whose CTV points fall between 4 and 5 since they joined MANET are classified as ‘UntrustedFriend’. Additionally, nodes whose CTV points fall between 6 and 7 since their promotion to the previous friendship level are classified as ‘FairlyTrustedFriends’. Further, nodes whose CTV points fall between 8 and 9 since their promotion to the previous friendship level are classified as ‘TrustedFriends’. Finally, nodes whose CTV points are greater than 10 since their promotion to the previous friendship level are classified as ‘MostTrustedFriends’. Figure 4 shows the implementation of friendship function algorithm.
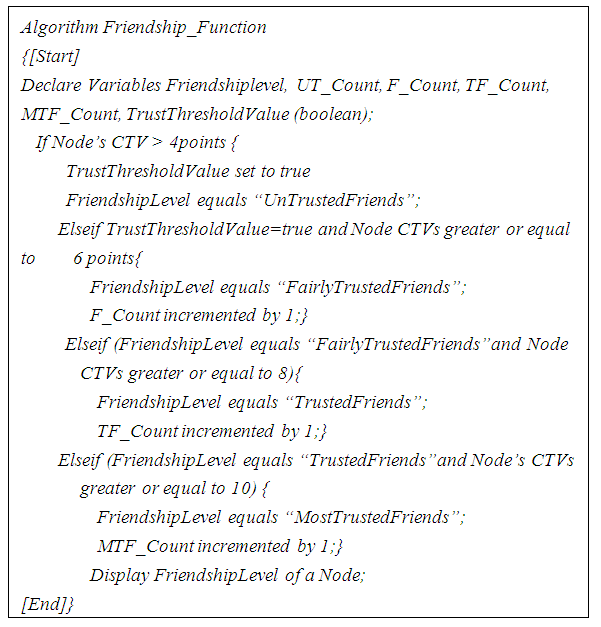 | Figure 4. Friendship Function Algorithm |
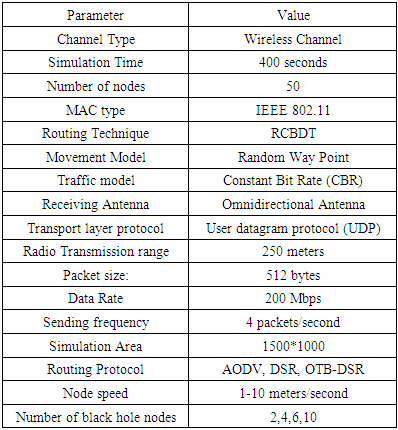
6. Simulation Environment
- The platform for simulation of OTB-DSR protocol was Ubuntu linux Operating System version 18.03. Ubuntu Operating System is open source; which means it can be freely downloaded from the Internet. Recent upgrades of the Ubuntu operating system are also found inform of patches downloadable from the Internet. The minimum hardware requirements for Ubuntu Operating system are; core 2 Duo processor or higher, memory of 2 GHz or higher and hard disk capacity of 500 GB or higher. Ubuntu operating system is compatible with NS-3 simulator. In our simulation experiment, two assumptions were made, that is; data packets can only be lost as a result of them being dropped by malicious nodes and nodes that participate in packet transmission have enough battery power to sustain the transmission process.a) NS-3 SimulatorNS-3 is a discrete-event network simulation tool developed by Tom Henderson, et al. [18], [19] in the year 2006 for Internet systems and was mainly targeted for educational use and research purposes. NS-3 was built as a replacement for NS-2. The new simulator completely abandons backward-compatibility with NS-2. NS-3 is written from scratch, using C++ programming language and Python with scripting capability. The simulator has a set of network simulation models implemented as C++ objects and wrapped in Python [18]. In NS-3 users write Python or C++ application that starts a set of simulation models that defines their simulation scenario. Building and compilation of NS-3 applications is done in Python [19].NS-3 software mainly target the system needs by first building the libraries of software development environment, and then build the user application program. The Network Simulator tool is built on the concepts of independent tracing of sources and sinks, and a uniform mechanism for connecting sources to sinks [18], [19]. NS-3 design simulations are built using Use Case models to allow the simulator to interact with real world. Figure 5 show the internal architecture of NS-3 simulator.
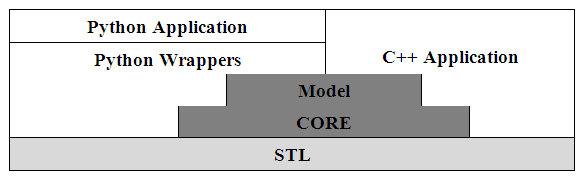 | Figure 5. NS-3 Architecture |
|
7. Results and Discussions
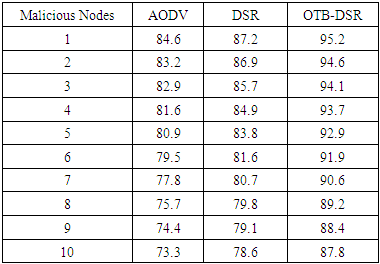
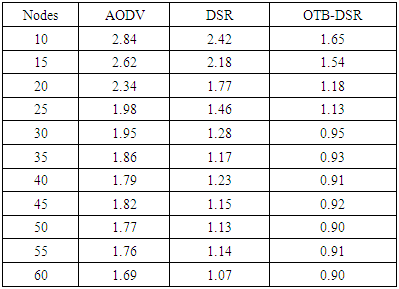
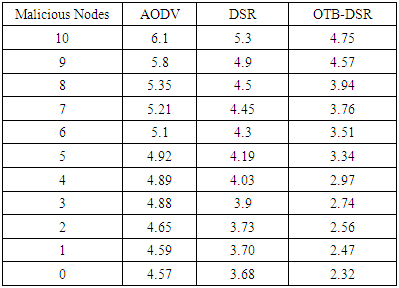
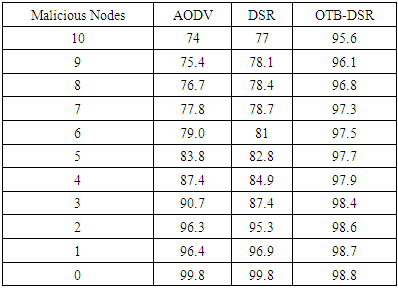
- a) Packet Delivery Ratio Table 3 shows the sample data extracted of packet delivery ratio of the three protocols. The data was extracted after the simulation process. This data was used to plot the graphs in figure 6 that depict PDR of the proposed OTB-DSR protocol compared to AODV and DSR used as benchmark protocols.
|
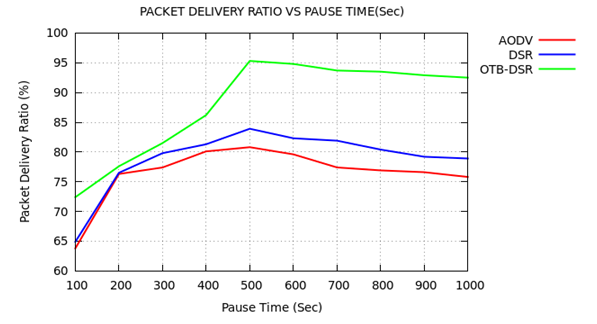 | Figure 6. Packet Delivery Ratio versus Pause Time |
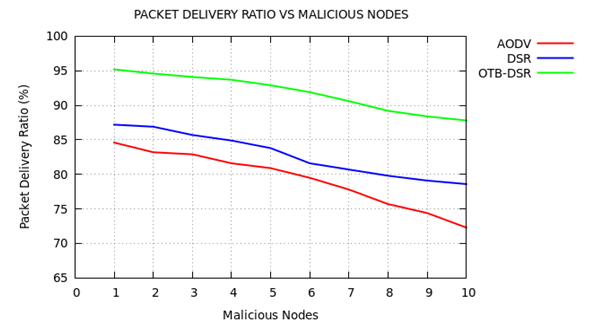 | Figure 7. Packet Delivery Ratio versus Malicious Nodes |
|
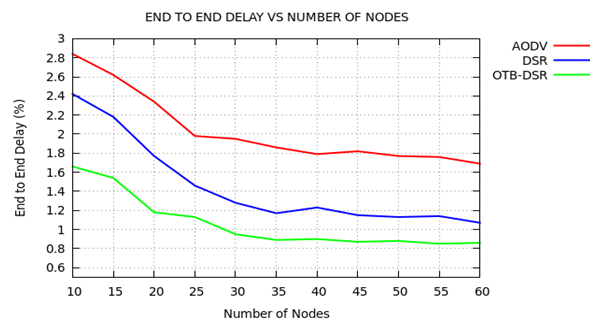 | Figure 8. End-to-End Delay versus Number of Nodes |
|
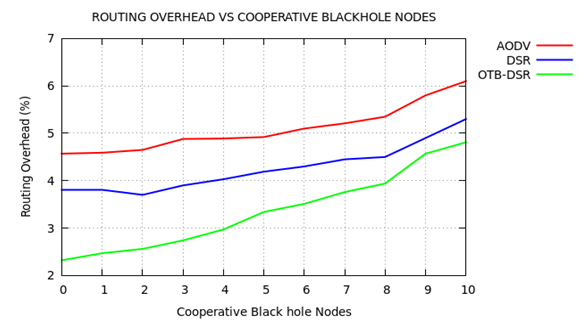 | Figure 9. Routing Overhead Versus Cooperative Blackhole Nodes |
|
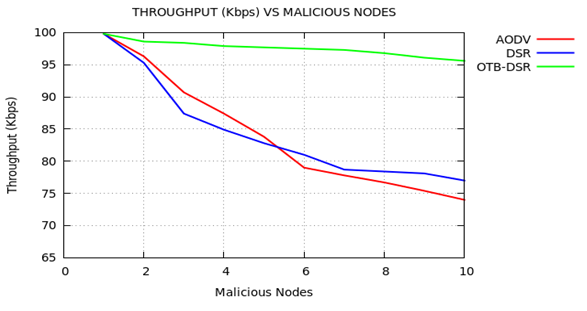 | Figure 10. Throughput Versus Cooperative Black hole Nodes |
8. Conclusions and Future Work
- In this paper, we developed an OTB-DSR protocol by integrating dynamic trust and friendship functions in the architecture of the standard DSR protocol. The proposed protocol was simulated in NS-3 simulator. To compare the performance of OTB-DSR protocol with the benchmark protocols; Packet Delivery Ratio, Routing Overhead, End-to-End Delay and throughput were used as our performance metrics. Simulation results indicated that in terms of the four performance metrics, the proposed protocol is superior to AODV and standard DSR used as benchmark protocols. The Optimized Trust-Based DSR protocol had a packet delivery ratio of above 95%, routing overhead of about 4.75%, end-to-end delay of between 0.9 seconds and 1.65 seconds and a throughput of 95.6 Kbps, while the performance of the benchmark protocols was slightly lower.As part of our future work, we intend to improve the proposed OTB-DSR protocol so that it can mitigate a range of active attacks such as Sybil, jelly fish, worm hole and grey hole attacks that compromise communication in MANETs.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML