-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Networks and Communications
p-ISSN: 2168-4936 e-ISSN: 2168-4944
2019; 9(2): 82-88
doi:10.5923/j.ijnc.20190902.03

Integration of SDN and 5G and Its Related Challenges and Security Issues
Nilofer Fatma, Jihad Qaddour
School of Information Technology, Illinois State University, Normal, IL USA
Correspondence to: Jihad Qaddour, School of Information Technology, Illinois State University, Normal, IL USA.
| Email: |  |
Copyright © 2019 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

The 5G technology is presently in its early research stages, so researches are currently underway exploring different architectural paths to address their key drivers. SDN techniques have been seen as promising enablers for the future networking, is likely to play a crucial role in the design of 5G wireless networks. A critical understanding of this emerging paradigm is important to understand that address multiple challenges and security issues of the future SDN-enabled 5G technology. This paper discusses the challenges and security issues that comes up by integrating SDN and 5G technology and proposed some solutions to overcome it.
Keywords: SDN, 5G, Security, QoS
Cite this paper: Nilofer Fatma, Jihad Qaddour, Integration of SDN and 5G and Its Related Challenges and Security Issues, International Journal of Networks and Communications, Vol. 9 No. 2, 2019, pp. 82-88. doi: 10.5923/j.ijnc.20190902.03.
Article Outline
1. Introduction
- The 5G technology is presently in its early research stages, so research is currently underway exploring different architectural paths to address their key drivers. Whereas, SDN technology have been seen as promising enablers for this vision of carrier networks, which will likely play a crucial role in the design of 5G wireless networks. A critical understanding of this emerging paradigm is necessary to address the multiple challenges and security issues in the future SDN-enabled 5G technology. With the integration of SDN and 5G technology, the complexity has been increased due to the hybrid infrastructure which may to leads to various challenges and security requirements that must be satisfied. Even as a leading SDN technology, the application of OpenFlow in the next generation of mobile network is still a challenging problem [2]. The advantage of SDN in 5G networks lies in its ability to provide new capabilities like automation and creating new services on top of the virtualized resources, in secure and trusted networks. SDN enables the separation of the control logic from vendor-specific hardware to open and vendor-neutral software controllers. Thus, it enables implementing routing and data processing functions of wireless infrastructure into software packages in general purpose computer or even in the cloud [2].This paper is organized in four sections: Section I gives the general introduction of the SDN architecture framework, Section II gives the description of 5G architecture, Section III discusses how SDN can be used in 5G architecture, Section IV describe the security challenges and proposed solutions for 5G leveraging SDN, Section V gives the conclusion, Section VI presents future intended research.
2. SDN Architecture
- The SDN architecture consists of the following key planes as shown in Figure 1.• Data plane/infrastructure layer:The Data Plane layer is also known as a Resource layer or Infrastructure layer, it is the bottom layer in the SDN architecture as shown in Figure 1. It primarily consists of a data forwarding unit including physical switches and virtual switches for exchanging and forwarding data packets to the SDN controller. We also categorize the physical mobile terminal as belonging in the data plane. The networking devices in the data plane layer perform simple forwarding functions, without embedded software to make autonomous decisions.
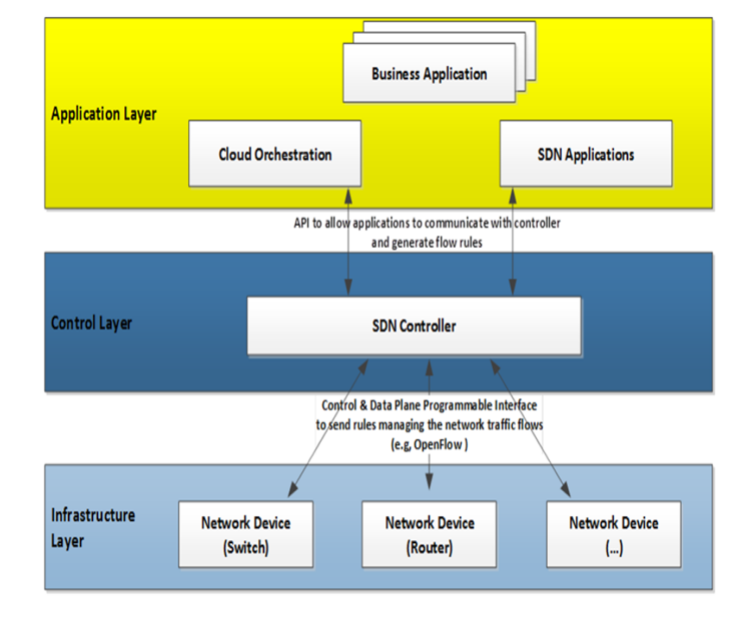 | Figure 1. SDN architecture |
3. 5g Architecture
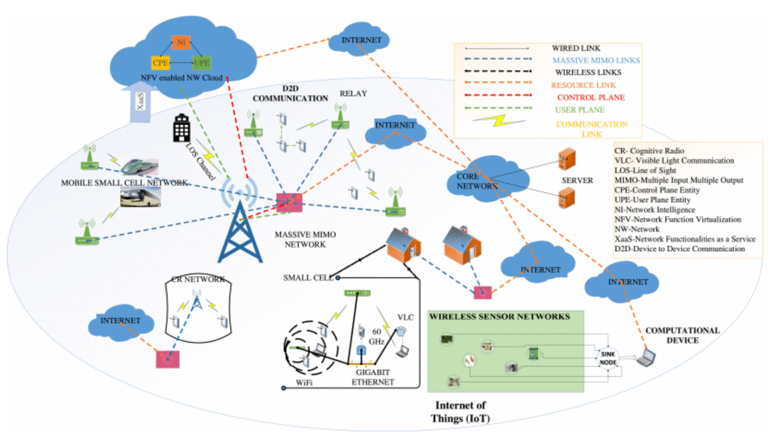 | Figure 2. 5G Architecture [5] |
4. 5G Leveraging SDN
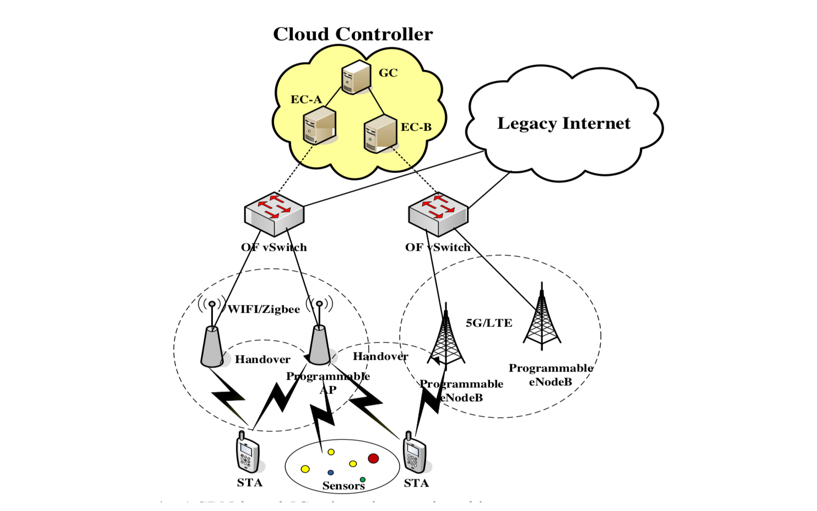 | Figure 3. Architecture of 5G leveraging SDN [1] |
5. Security Challenges
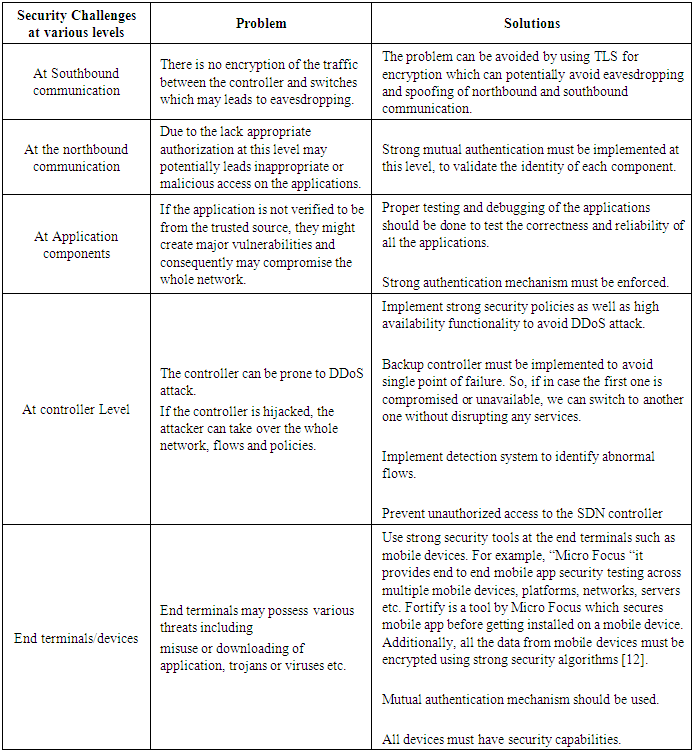
- The basic properties of a secure communications in a network includes: confidentiality, integrity, availability of information/data or resources, authentication and non-repudiation. In order to provide a secure network, security professionals must secure the data, the network assets (e.g. devices) and the communication transactions across the network at all times. The alterations to the network architecture introduced by SDN along with 5G or other technologies must be assessed to ensure that network security is sustained. One of the network features of 5G technologies is heterogenous access, which only allow use of different access technologies such as Wi-Fi or LTE, but also support multi-network environment. That means that the access network architecture of different networks are different, so security designers of 5G technology must ensure that they are building the suitable security architecture for different access technologies.Though SDNs provide us with the ability to easily program the network and to allow for the creation of dynamic flow policies in the network. It is, in fact, this advantage that may also lead to some potential security vulnerabilities. In [3] Kreutz et al. present a high-level analysis of the overall security of SDN. They conclude that due to the nature of the centralized controller and the programmability of the network, new threats are introduced requiring new responses. They propose a number of techniques in order to address the various threats, including replication, diversity and secure components [4]. The results of these analyses indicate that the control and data layers in SDN are still clear targets of attack.The QoS provisioning in the advanced SDN-enabled 5G networks are more complex and poses a real problem that need to be addressed [1]. QoS automation should be supported at every wired and wireless technology that may share the same the network slice. Although SDN allows creating different network slices in the same network infrastructure to provide a strict QoS as well as performance and isolation required by across applications without interfering with traffics in other slices, however, SDN does not provide the ways for automating QoS provisioning per-application/per-service [1].A DDoS attack refers to an attack that attempt to make a machine or network resource unavailable to its intended users. In the case of SDN, the network devices require access to the control plane to receive traffic management instructions and traffic across the network requires access to the network device flow tables to dictate traffic management policies. The data-control plane interface and the network device flow table are therefore points of vulnerability to DoS attack. Most of the current research done in SDN security focused more on the OpenFlow protocol, but the vulnerabilities that exist in OpenFlow are likely to be generalizable to any SDN system that uses a centralized controller. As per the study done in the research paper [9-11], the most common vulnerability that is noted is the communication bottleneck that is between the data-plane and the controller in an OpenFlow network.a. Risk at Southbound API’s:Due to the lack of intelligence at the southbound APIs, they are susceptible to attack via false and forged flow table entries. The attacker may send false data stream with slightly different header information to overflow the flow table, as a result the legitimate flows cannot be updated on time. The security of the whole network could be compromised by unsecure implementation of the southbound protocols.Suggested Solutions - The problem can be avoided by using TLS for encryption which can potentially avoid eavesdropping and spoofing of northbound and southbound communication, message integrity ensuring that the message is not altered, authentication by validating one or both partners to exchange using public-key certificates. The security function provided by TLS is transparent to the application and also to TCP, thus neither TCP nor application needs to be modified to invoke the security features of TLS.b. Risk due to End Terminals/Devices:End terminals may possess various threats including misuse or downloading of application, trojans or viruses etc. These mobile devices should also the area of focus, as any vulnerable devices may lead to vulnerability in the entire infrastructure. The terminals usually lack an effective security tools such as intrusion detection system, antivirus software, endpoint firewalls, spam blocking and so on. These end terminals/devices possess huge security risk, if not properly secured.Suggested Solution -Make end device secure by default. When the control is unable to meet the security requirements, it should take actions such as deny by default, etc., Different security level must be implemented in order to meet the security requirement. All the end devices must have required security capabilities in place, the security application used within the network must push rules to all network devices. The devices must be check for required security compliance before giving access to them.c. Risk at Communication layerThe protocols used in communications between base stations and controller, controller and application services are also vulnerable to attacks due to lack of the underlying IP layer security and authentication. Some of the attacks that could be possible at this layer are SYN DoS and TCP reset attack [7].Suggested Solution: The communication channel between the controller and data plane must use IP-Sec tunneling to secure the communication between them. Intrusion Detection Mechanism should be implemented to detect the inappropriate or incorrect behavior of protocols used in this layer. Researcher in [8] also proposed a solution by using HIP and IPSec tunneling to provide secure channel between the controller and data plane layer.d. Risk at Application layerThe 5G network support wide variety of mobile devices that might host vulnerable applications which can also be the source of attack. Hence, the application layer hosting various applications might be vulnerable, as it can cause fault information flow to the controller or inject deceptive rules into the network. A successful attack at this risk layer could gain control of the networking infrastructure. To provide security at this layer, we must focus on preventing unauthorized applications and users from exploiting the controller.Suggested Solution: The application layer must host application management and strong authentication mechanism. It must also ensure periodic debugging and testing of all the applications for correctness and reliability. Proper constraint must be defined for APPs, so unauthorized access by these APP can be easily detected and proper actions can be taken on time.e. Risk at Controller layerSDN controller when implemented in 5G provides management and router selection for all radio access network (RAN) to core network connection. But it also provides single point of failure, and if it is compromised the whole network can be under the controller of the attackers. SDN-controller is the high-value target that needs a high level of protection. The controller can also be prone to DDoS attack, if the controller is hijacked, the attacker can take over the whole network, flows and policies. Hence, SDN controller must have strong security policy so as to avoid it from any vulnerability.Suggested Solutions: Strong security policies must be implemented to avoid DDoS attack on the controller. It is also advisable to use high availability functionality in the controller to guard against DoS attacks. We can also employ a detection system such as IDS/IPS to help identify any abnormal flows within the controller. Unauthorized access to SDN controller must be prevented and logging as well as trails must be used.Table 1 summarizes some of the security challenges at each level that still remain possible sources of attack and proposed solutions. Research still needed to be carried out to overcome these challenges and make it stronger. The table focuses on major area of focus that need more attention implementing SDN for 5G network.
|
6. Muthual Authentication between the Controller and Base Station
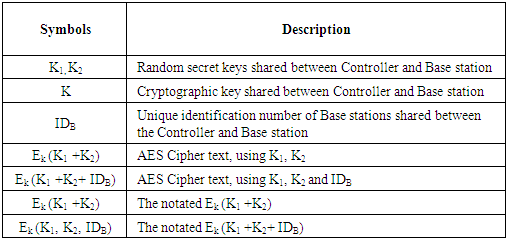
- If the controller is implemented in the edge network connecting different base stations, in that case all the processing is being performed at the controller. As controller is the core of the network, it is highly important to secure the controller from any kind of attack. So, this paper also focuses on strong mutual authentication between the controller and the base stations before any exchange of messages. The authentication must be performed before every session and new keys must be used for each session between them, to avoid any kind of replay attack, man-in-the middle attack as well as controller hijacking.Mutual authentication between controller and base station could be achieved by using AES as shown in figure 4. It is assumed that the random secret keys and cipher key is shared between the controller and the base station only. The controller also keeps a copy of the identity IDB of the base-station. The notations can be summarized in Table 2 to describe the algorithm.
|
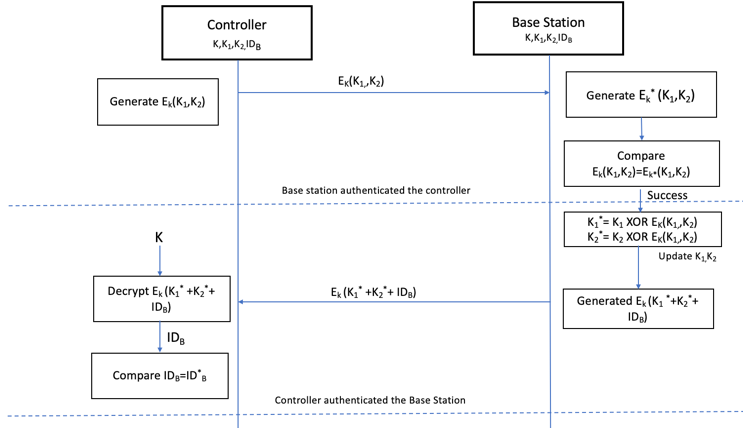 | Figure 4. Mutual Authentication between the Controller and the Base Station |
7. Conclusions
- This paper focuses mainly on security issues and challenges with the integration of SDN and 5G. Although some advances are being made by combining SDN and 5G, there are many challenging problems that need to be addresses with the integration of heterogenous technologies. Security is one of the issues that needs the significant research efforts. As these technologies are still new, many challenges and security issues still need to be solved. This paper highlights the major area that needs more attention during the implementation of SDN and 5G. It also discusses some of the problems that that exist at various levels and suggest proposed solutions for them.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML