Shereen Omar, Osama El Ghandour, Ahmed M. Abd El-Haleem
Department of Communication, Electronics and Computers Engineering, Helwan University, Cairo, Egypt
Correspondence to: Shereen Omar, Department of Communication, Electronics and Computers Engineering, Helwan University, Cairo, Egypt.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Abstract
Cognitive Radio technology provides a promising solution for the spectrum scarcity issues in wireless networks. It allows the efficient use of radio frequency spectrum. In cognitive radio terminology, the Primary Users are defined as users who have high priority to use the spectrum band, whereas Cognitive Users are defined as users who can use the spectrum which is temporarily not used by PUs activity, without causing interference to them. In this paper, we discuss the implementation of MACNRP protocol based on the Ad hoc on demand Multipath Distance Vector (AOMDV) routing protocol. The performance of MACNRP protocol compares with the D2CARP and FTCRP are conducted through OPNET simulation. Results show that the performance of the proposed protocol achieves an increase in network throughput, besides it decreases the probability of route failure due to node mobility and primary user activity. We have found that, the MACNRP result is reduction in blocking probability, and improvement in network throughput due to the successful reduction of collision between Primary Users and Cognitive Users. Moreover, the MACNRP scheme results obviously in decreasing the path failure rate.
Keywords:
Cognitive Radio Networks, Ad Hoc Network, Multi-path Node-disjoint, Activity based routing, Routing Performance evaluation, OPNET, Blocking probability
Cite this paper: Shereen Omar, Osama El Ghandour, Ahmed M. Abd El-Haleem, MACNRP Implementation Based AOMDV and Performance Evaluation, International Journal of Networks and Communications, Vol. 7 No. 1, 2017, pp. 17-23. doi: 10.5923/j.ijnc.20170701.02.
1. Introduction
Cognitive radio is an intelligent wireless communication system that is aware of its environment. Also it uses the methodology of understanding by building to learn from the environment and adapt its internal states, to statistical variations in the incoming radio frequency stimuli by making corresponding changes in certain operating parameters in real time. With achieving two main objectives: highly reliable communications needed and efficient utilization of radio spectrum [1]. Under usage of the spectrum and need to expand the spectrum efficiency is motivating researchers to take advantage of the wireless medium. In this direction, the Federal Communications Commission (FCC) Spectrum Policy Task Force has published in 2002, in which it investigates the underutilization of the radio spectrum [2]. While the FCC is responsible of determining the spectrum usage and its policies [3]. The key technology of dynamic spectrum access approaches is the cognitive radio (CR) technology, which afford the capability to share the wireless channels with the licensed users in an opportunistic way. CR networks are assumed to provide high bandwidth to mobile users via dynamic spectrum access techniques. It allows the efficient use of radio frequency spectrum [4]. Cognitive radio networks are envisioned to be able to opportunistically exploit those “spectrum holes”, by awareness of the environment and cognition capability, in order to adapt their radio parameters accordingly. Spectrum sensing is the main step that will enable cognitive radio networks to achieve this goal. In cognitive radio terminology, Licensed users or Primary users (PUs) are defined as users who have right to use the spectrum band, whereas unlicensed users or Cognitive users (CUs) are defined as users who can use the spectrum which is temporarily not used by PUs, without causing interference to them [5]. In [6], a protocol called joint path and spectrum diversity in cognitive radio Ad Hoc networks (D2CARP) it is adopted in a routing protocol, in which jointly exploiting both diversities, CUs can move dynamically to different paths and spectrum bands for communicating with each other in the presence of PU activity. In [7], authors are introduced a fast and efficient route to recovery in presence of path failures during data delivery in CRAHNs. In FTCARP, a backup path is immediately utilized in case a path failure occurs over a primary transmission route in order to transfer the next coming data packets without causing a severe service disruption, which uses a different route recovery mechanism to handle different cause of a path failure.In this paper, we proposed two different versions of cognitive radio networks routing protocols. Both the versions are able to take advantage of the spectrum diversity and path diversity, but they exploit two different techniques. The first version, referred to as a multi-path activity based routing protocol for cognitive radio network (MACNRP) [8], it is able to utilizes channel availability and creates multiple node-disjoint routes, at least two node disjoint routes, and reserves at least two different frequency chan. The second one, referred to as Frequency Locked Mechanism (MACNRP+F), the same techniques but it's different in reservation of matching process in route discovery process. Also, the performance evaluation compares with the D2CARP and FTCRP protocols based on OPNET simulation are presented.The rest of the paper is organized as follows. In section II, described briefly the AOMDV and MACNRP protocols. The implementation of MACNRP based on AOMDV is presented in Section III. The simulation results and performance evaluation are presented in Section IV. Finally, concluding remarks are drawn in Section V.
2. Background
The implementation of the MACNRP protocol should be considered as based on the AOMDV multipath routing protocol [9]. For a more detailed description, we shortly address both protocols in the rest of this section.
2.1. AD HOC on Demand Multipath Distance Vector Routing (AOMDV)
The AOMDV protocol uses the basic AODV route process, with extensions to discover multiple loop-free and link-disjoint paths from the source node to the destination.AOMDV mainly computes the multiple paths during the route discovery process, and it consists of two main components:1. Alternate loop-free reverse paths for route updates to find multiple paths at each node and Title of the paper.2. Calculate the link-disjoint paths by using distributed protocol. In this protocol, when the source node transmits packet to destination by using a different route for each route request and route reply. AOMDV route update rules, which applied locally at every node, this is the key role in keeping up loop-freedom and node-disjoints properties. AOMDV is the same basic of AODV route discovery procedure in two ways. First, have loop-free reverse paths formed at intermediate nodes and the destination by using the routing information acquired by duplicating route request. Second, the destination node generates multiple route replies, which these replies travel along multiple loop-free reverse paths to the source established during the route request propagation phase to create multiple forward paths to the destination.The algorithm is used “advertised hop count” as metric in such a scenario. The advertised hop count for a particular node is the maximum acceptable hop count for any path recorded at that node. A path for the destination, it was set to the hop count of the longest path available at the time, when a node first advertises. The advertised hop count set stays check once fixed until the sequence number changes. Moreover, AOMDV also finds routes on demand using a route discovery procedure. The main difference of this protocol is the number of routes found in each route discovery [9]. In AOMDV, the source node broadcast RREQ towards the destination node, and then establishes multiple paths. Multiple RREPs traverse these reverse paths back to form multiple forward paths to the destination node at the source and intermediate nodes. AOMDV relies possible on the routing information already available in the underlying AODV protocol, thereby limiting the overhead incurred in discovering multiple paths. Specifically, it doesn't utilize any special control packets. In fact, extra RREPs and RERRs for multipath discovery and maintenance along with a few extra fields in routing control packets constitute the main extra overhead in AOMDV relative to AODV.
2.2. MACNRP Protocol Overview
In this section describes the MACNRP protocol. The main idea of this algorithm is to efficiently utilize channel availability depending on CUs sensing history and the current sensing decision of mobile PUs activity. Therefore, we can share the lowest activity channels among different CUs by using different frequency channel per single route, it will increase the frequency reuses and minimize the interference with PUs which increases the network capacity and maximize the spectrum utilization. In additional, we divided spectrum band into two separate types of channels. A common control channel (CCC) is used by all CUs for synchronization purposes. And a data channel (DC) which used for data communication, and it is assumed to be divided into a number of time slots. Finally by increasing the number of cognitive users and the spectrum utilization, the overall network throughput will increase.The MACNRP achieves some goals by using a number of mechanisms, stated as follows: • Creating a stable and reliable route: one of the significantly important problems in the CRAHN routing protocol is to cope with the route failure due to Pus activity and node mobility. In the proposed MACNRP protocol the low activity node-disjoint routes are selected as follows: For each connection request MACNRP protocol discovers several node disjoint routes (at least two node disjoint routes), and reserve at least two different frequency channels; with the lowest probability of PUs activity; per route. So, there are four different paths per connection. This mechanism will decrease the probability of route failure due to node mobility (construct a node disjoint routes) or primary user activity (select the most probable idle frequency channels).• Developing an efficient spectrum sharing techniques: MACNRP protocol divided each frequency channel into a number of time slots shared among different CUs; and each CUs reserve one time slot per frequency channel per path per neighbour; which increase the number of cognitive users using the available spectrum. • Developing an efficient technique for minimizing the interference between PUs and CUs: MACNRP protocol depends on a Local route-decision, where each node determines the most probable idle channel based on its own information about the PUs activity (node local spectrum knowledge). So, according to the PU location and its transmission range, the most probable idle frequency channel is different among different SUs nodes (depending on the relative location of CU to the active PU). So, there is no requirement of frequency channel availability in the whole region traversed by the route. Here each intermediate neighbour node will use its local most probable idle frequency channel to form the route. The use of different frequency channel per single path, and sharing the lowest activity channels between different CUs users will increase the channel frequency reuse and minimize the interference to PU, which increase the spectrum utilization and the network capacity.
3. MACNRP Implementation
The main operation of the MACNRP protocol in MANETs is based on AOMDV multipath routing to select two node-disjoint routes between the source and destination nodes. The protocol works in three phases: Route Discovery Phase, data forwarding Phase and Route Maintenance Phase are described in the following.
3.1. Route Discovery
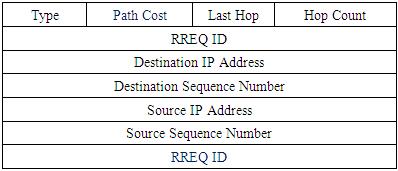
The source node initiates a route discovery process by broadcasting a Route Request RREQ packet to each neighbour CUs, through the common control channel data if there are common routes between the source node and its neighbours. The RREQ packet contains the channel activity table of the source node, and a path cost field with value equal zero as shown in table 1.Each intermediate node receives the first copy of a RREQ, compares its channel activity table with the received upstream neighbour channel activity table and search for a match as shown in table 2. When it finds a matched frequency channel with matching free time slots (fi, Tfi), it reserves at least two time slots, one per each matched frequency channel, which has the lowest channel cost.If a multiple frequency channels have the same cost, it selects the channels having the highest Idlelity factor. If the RREQ packet is received over the control channel the intermediate nodes will reserve the channels (fi, Tfi) from the matching process to form a route between these two CUs. Otherwise, if the RREQ is received piggybacked with a data packet, the intermediate node updates the existing route between itself and its upstream neighbour according to the result of the matching process. In additional if no match found by the node receiving the RREQ it will be rejected.Table 1. Format of RREQ
 |
| |
|
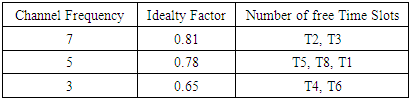
We include an additional extra field that works as flag known as seen-flag. At begin, this flag is set to FALSE, when the seen flag is set to TRUE simply the RREP packet discard. Otherwise, after a node gets its RREQ packet, the RREP packet checked the seen flag value in their seen table. If the seen flag is set to FALSE, this indicates that is the first RREP then check for lowest cost in seen table and sends a unicast RREP packet on the reverse path towards the source node with matching process, then rest value of seen flag [11].Table 2. Channel Activity Table
 |
| |
|
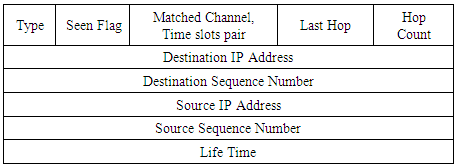
If the intermediate CU node has a valid route to the desired destination, it then sends a unicast RREP packet back to the source node containing the result of the matching process (fi, Tfi), to establish a forward path as shown in table 3. This will reduce the overhead in routing caused by the route discovery processes. Otherwise, the intermediate node replaces the channel activity table in the RREQ packets by its channel activity table, updates the path costs and re-broadcast the RREQ.Table 3. Format of RREP
 |
| |
|
Copy duplicates of the RREQ are immediately discarded upon reception at every node.When the destination node receives the RREQ packet from multiple nodes, it searches for a match and updates the path costs. Then it forms the forward paths by unicasting two RREP containing the result of the matching process (fi, Tfi) back to the source along the selected least cost (lowest PU activity) node-disjoint routing paths.Any intermediate node receiving the RREP packet sets up a forward route through the matched (fi, Tfi) toward the destination, inserts the result of the matching process in the RREP, and forwards a copy of the RREP packet to upstream neighbour nodes form a forward path from the source to the destination.
3.2. Data Forwarding Phase
The source node partitions to send the data flow packets over the primary path after receiving the RREP packet is shown in table 4, and send it on the available paths by hopping on the different frequency channels using generated during the matching process, to selecting the two node-disjoint paths.Table 4. Data Packet Format
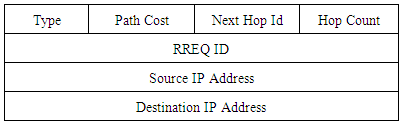 |
| |
|
3.3. Frequency Locked Mechanism (MACNRP+F)
During the route discovery phase of the MACNRP protocol and after the matching process at the intermediate nodes, each node will reserve the matched channels (fi, Tfi).…..(fj, Tfj) without informing the upstream neighbour node about this reservation. So, during the RREP packet traveling up from the destination node to the source node, intermediate node nk+1 will request from the upstream neighbour node nk to reserve the time slots it reserved to form the forwarding. Due to the time delay between the RREQ and its corresponding RREP packets traveling through this node, the requested resources by node nk+1 may be used by node nk for another connection, so the route discovery process will fail, which increase the blocking probability.Table 5. IR packet format
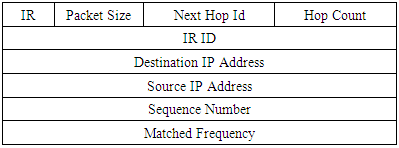 |
| |
|
To cope with this issue, we modify the route discovery phase. During the route discovery phase, when any intermediate node “F” receives a RREQ and performs matching, it sends an Immediately Response (IR) packet to the upstream neighbour node “C” that sent the RREQ. This IR packet contains the results of the v-matching process (fi, Tfi). The number of matched frequencies is variable, it will be added “packet size" field into IR packet, to identify the size of the IR packet as shown in table 5.When node “C” receives the IR packet, it temporarily reserved the requested resource with time out until a RREP packet is received. Then, node “C” sends an ACK packet to node “F” if the selected channels (fi, Tfi) are still proper as shown in table 6.Table 6. Acknowledge format
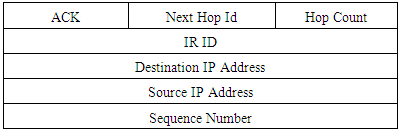 |
| |
|
But if the (fi, Tfi) found in the IR packet are busy (selected for other connections), node “C” will send a NACK packet containing its channel activity table to node “F” to search for another match. This process is repeated until the two-node lock on minimally two time slots at two different frequency channels can be seen in table 7.Table 7. Negative Acknowledge format
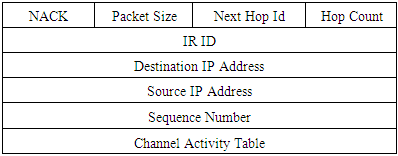 |
| |
|
3.4. Blocking Probability Analysis
In this section, we develop a simple model to calculate the connection blocking probability based on the probability of not finding a two node disjoint routes with minimum two frequency channels on each to carry out the data packets.The probability of neighbour node has at least two free time slots on two different frequency channels [12] can be modified and written as: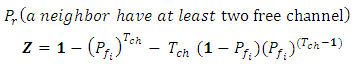 | (1) |
Where 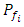 the probability of a given channel is busy
the probability of a given channel is busy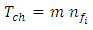 Is the total number of available channelsThen the connection blocking probability is:
Is the total number of available channelsThen the connection blocking probability is: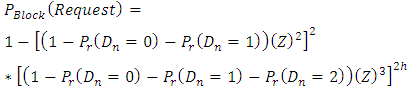 | (2) |
Finally we have,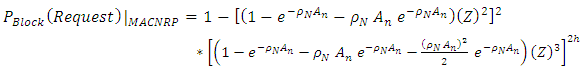 | (3) |
Also, the connection request blocking probability for a D2CARP and FTCARP routing protocols can be written as: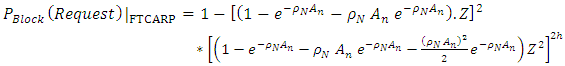 | (4) |
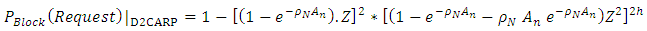 | (5) |
Here 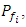 is the probability of channel fi to be busy
is the probability of channel fi to be busy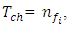 is the total number of available channels.Through this performance evaluation it is assumed that the number of network nodes N = 60, the number of channels
is the total number of available channels.Through this performance evaluation it is assumed that the number of network nodes N = 60, the number of channels 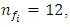 the average path length h = 6 nodes, and m = 12 time slots per channel, the node transmission range = 25m, the network area size
the average path length h = 6 nodes, and m = 12 time slots per channel, the node transmission range = 25m, the network area size 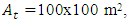 and the probability of a given channel
and the probability of a given channel 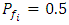 .Figure 1 shows the relation between the number of network node density and the connection blocking probability. The figure shows that at a lower node density the rate of blocking probability is high. However, when the number of network node density increases the blocking probability of our MACNRP protocol decreases exponentially, which is a higher rate than the other two protocols. This means that the MACNRP protocol performs better in case of increase number of network node density, the probability of finding routes is high, and the sharing of the lowest activity channels increases, which decrease the connection blocking probability.
.Figure 1 shows the relation between the number of network node density and the connection blocking probability. The figure shows that at a lower node density the rate of blocking probability is high. However, when the number of network node density increases the blocking probability of our MACNRP protocol decreases exponentially, which is a higher rate than the other two protocols. This means that the MACNRP protocol performs better in case of increase number of network node density, the probability of finding routes is high, and the sharing of the lowest activity channels increases, which decrease the connection blocking probability.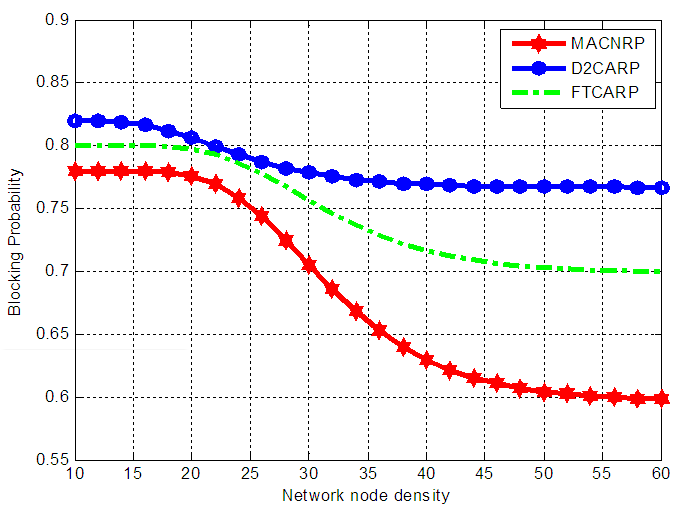 | Figure 1. Blocking probability versus network node density |
4. Simulation Result
In this section, the performance of the MACNRP protocol is simulated by OPNET to evaluate the network performance. During simulation, during simulation, PUs and SUs are distributed uniformly across an area size of 100x100 m2 with 60 moveable CUs and [5, 10, 15, 20] PUs nodes. The transmission range of each node is 25m with random way point mobility. The nodes are able to communicate with each other’s using the IEEE 802.11 MAC layer protocol. In the application layer, the nodes communicate using constant Bit Rate generators (CBR). Each generator produces data packet 512 bytes at the rate of 10 packets per second. The simulation time is set to 300 seconds. Each simulation is repeated five times and then average values of their results are taken to ensure integrity. The performance metrics used for evaluation include: throughput, path failure, and compared with other two algorithms D2CARP and FTCRP protocols.In figure 2, the relation between the network throughput and the number of network node density is shown. The results show a clear relation between network node density and increased throughput. At low densities, we see lower increases as both the MACNRP and MACNRP+F protocols nearly the same single path. Moreover, when the density of the network is low, the topology becomes less connected.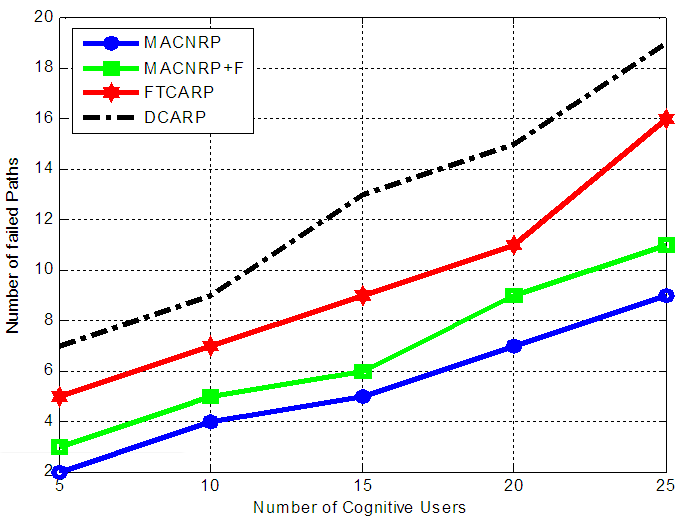 | Figure 2. Throughput versus network node density |
Figure 3, shows the performance results of MACNRP protocols in terms of path failure versus the number of CUs without mobility. From the graph, it is observed that the number of failed paths increases as the number of CUs increases. This is due to increase the probability of collision between the PUs and CUs connections and the number of failed paths.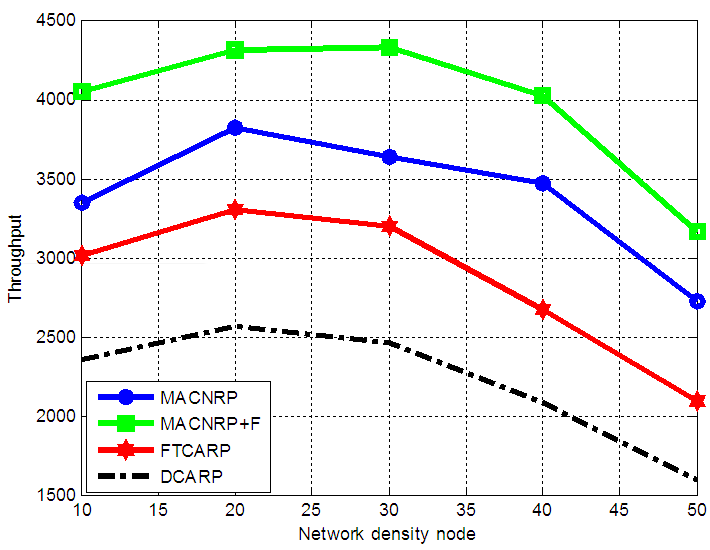 | Figure 3. Path Fail failures versus no of CU nodes without Mobility |
5. Conclusion and Future Work
This paper described the details operation of the MACNRP routing protocol, and the performance of protocol compares with the D2CARP and FTCRP protocol based on simulation.MACNRP protocol success to established multi paths node-disjoint routes between the source and destination nodes, with lowest PUs activity value and utilizes channel availability.Through simulations, we showed that, the MACNRP protocols increase the network throughput. Also, the proposed protocol succeeded in reducing the blocking probability. However, the protocols reduced the number of failed paths in case of CUs activity compared to D2CARP and FTCARP protocols. The results confirm the suitability of the protocol for cognitive radio ad hoc networks.
References
| [1] | FCC, ET Docket No 03-322 Notice of Proposed Rule Making and Order, Dec 2003. |
| [2] | S. Haykin, “Cognitive radio: brain-empowered wireless communications,” Selected Areas in Communications, IEEE Journal on, vol. 23, no. 2, pp. 201–220, 2005. |
| [3] | Federal Communications Commission, “Unlicensed operation in the TV broadcast bands and additional spectrum for unlicensed devices below 900 MHz in the 3GHz band,” ET Docket No. 04-186, May 2004. |
| [4] | I. F. Akyildiz et al., “NeXt Generation/Dynamic Spectrum Access/Cognitive Radio Wireless Networks: A Survey,” Comp. Networks J., vol. 50, Sept. 2006, pp. 2127–59. AbdEl-Haleem, A.M., Ali, I.A., & Ibrahim, I.I. (2011). Analytical Model and Performance Evaluation for the TRIDNT protocol. IJCSI. |
| [5] | S. Haykin, “Cognitive Radio: Brain-Empowered Wireless Communications,” IEEE JSAC, vol. 23, no. 2, Feb. 2005, pp. 201–20. |
| [6] | Rahman, M., Caleffi, M., & Paura, L. (2012). Joint path and spectrum diversity in cognitive radio ad-hoc networks. EU Journal on Wireless Communications and Networking, 2012(1), 1-9. |
| [7] | Che-aron, Z., Abdalla, A. H., Abdullah, K., Hassan, W. H., & Rahman, M.A. (2015). A Fault-Tolerant Multi-Path Multi-Channel Routing Protocol for Cognitive Radio Ad Hoc Networks. Information Science and Applications, 339, 43-50. |
| [8] | Omar Shereen, Osama El Ghandour, and Ahmed M. Abd El-Haleem. "Multipath Activity Based Routing Protocol for Mobile Cognitive Radio Ad Hoc Networks." Wireless Communications and Mobile Computing 2017 (2017). |
| [9] | M. K. Marina, and S. Das. “On-demand multi path distance vector routing in ad hoc networks”. In Proceedings of the IEEE ICNP, 2001, pp. 14–23. |
| [10] | YuHua Yuan, and Min Jia. An optimized ad-hoc on demand multipath distance vector (AOMDV) routing protocol. In Communications, Asia -Pacific Conference on, pages 569 –573, oct. 2005. |
| [11] | Singla, Er Rubia, and Er Jasvir Singh. "Node-disjoint multipath routing based on AOMDV protocol for MANETS." Int J Comput Sci Inf Technol 5.4 (2014). |
| [12] | Abd El-Haleem, A.M., Ali, I.A., & Ibrahim, I.I. (2011). Analytical Model and Performance Evaluation for the TRIDNT protocol. IJCSI. |


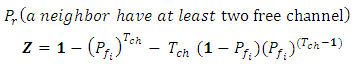
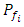 the probability of a given channel is busy
the probability of a given channel is busy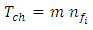 Is the total number of available channelsThen the connection blocking probability is:
Is the total number of available channelsThen the connection blocking probability is: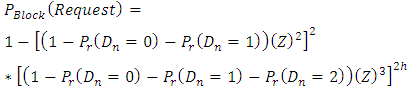
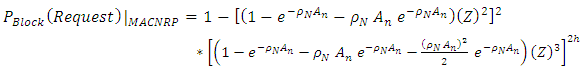
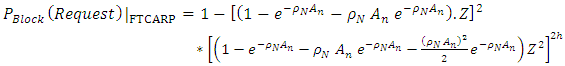
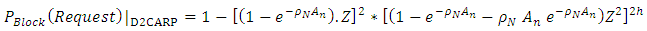
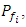 is the probability of channel fi to be busy
is the probability of channel fi to be busy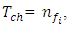 is the total number of available channels.Through this performance evaluation it is assumed that the number of network nodes N = 60, the number of channels
is the total number of available channels.Through this performance evaluation it is assumed that the number of network nodes N = 60, the number of channels 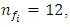 the average path length h = 6 nodes, and m = 12 time slots per channel, the node transmission range = 25m, the network area size
the average path length h = 6 nodes, and m = 12 time slots per channel, the node transmission range = 25m, the network area size 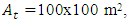 and the probability of a given channel
and the probability of a given channel 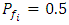 .Figure 1 shows the relation between the number of network node density and the connection blocking probability. The figure shows that at a lower node density the rate of blocking probability is high. However, when the number of network node density increases the blocking probability of our MACNRP protocol decreases exponentially, which is a higher rate than the other two protocols. This means that the MACNRP protocol performs better in case of increase number of network node density, the probability of finding routes is high, and the sharing of the lowest activity channels increases, which decrease the connection blocking probability.
.Figure 1 shows the relation between the number of network node density and the connection blocking probability. The figure shows that at a lower node density the rate of blocking probability is high. However, when the number of network node density increases the blocking probability of our MACNRP protocol decreases exponentially, which is a higher rate than the other two protocols. This means that the MACNRP protocol performs better in case of increase number of network node density, the probability of finding routes is high, and the sharing of the lowest activity channels increases, which decrease the connection blocking probability.


 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML





