-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Networks and Communications
p-ISSN: 2168-4936 e-ISSN: 2168-4944
2016; 6(2): 19-23
doi:10.5923/j.ijnc.20160602.01

A Study on Memory Management in Wireless Sensor Nodes during Key Agreement Generation
Lunda Machaya , Simon Tembo
School of Engineering, University of Zambia, Lusaka, Zambia
Correspondence to: Lunda Machaya , School of Engineering, University of Zambia, Lusaka, Zambia.
| Email: |  |
Copyright © 2016 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

The objective of the research was to efficiently manage memory in wireless sensor nodes during key agreement generation using minimax sampling. The wireless sensor nodes are faced with scarce memory resources, which limits their computing power and communication capabilities in highly dynamic environments. Wireless sensor networks represents a new generation of distributed embedded systems with a wide range of real-time applications. The applications of such nodes include process control, fire monitoring, cross border surveillance, health care, fixed and mobile asset tracking, agriculture, highway surveillance. In our research, we have proposed minimax sampling during key agreement generation to efficiently manage memory usage in wireless sensor nodes. The adopted experimental approach involved the use of Matlab. The signal was analysed at various frequencies using uniform sampling to determine memory variations with changes in the number of samples considered for key agreement generation. The results showed that as the number of samples increases, the memory usage in the wireless sensor node increases and vice versa. Our proposed minimax sampling method reduces the number of samples, thereby efficiently managing the memory. This results in memory availability for other tasks in the wireless sensor node.
Keywords: Wireless Sensor Node, Network, Key Agreement Generation, Memory Management, Minimax Sampling
Cite this paper: Lunda Machaya , Simon Tembo , A Study on Memory Management in Wireless Sensor Nodes during Key Agreement Generation, International Journal of Networks and Communications, Vol. 6 No. 2, 2016, pp. 19-23. doi: 10.5923/j.ijnc.20160602.01.
Article Outline
1. Introduction
- A Wireless Sensor Network (WSN) is a network of wearable and implantable computing devices [1]. The computing devices are either medical, weather or environmental sensing devices. With the growing demand and implementation of WSNs, there is need to optimize the resources of sensor nodes to ensure reliable and accurate collection and communication of data by the nodes. The WSNs represent a new generation of distributed embedded systems with a wide-range of real-time applications including process control, fire monitoring, cross border surveillance, health care, fixed and mobile asset tracking, agriculture, highway surveillance [2]. A WSN system can be integrated with existing communication systems infrastructure to reach longer distances. This allows for connection to remote servers via internet or mobile communication technologies (GSM/GPRS/3G). This way, the collected data can be accessed online using the fixed or mobile communication technologies independent of the sensor location. The rapid development of sensor technology, low-power integrated circuits, and wireless communication has enabled a new generation of wireless sensor networks such as Mobile Adhoc Networks (MANETS), Vehicular Adhoc Networks (VANETs), Military MANETs, Internet based MANETs (iMANETs) and Smart Phone Adhoc Networks (SPANs) [3]. This research proposes minimax sampling during key agreement generation to efficiently manage memory resources in the sensor nodes during agreement key generation. Minimax Sampling is the method where the analog signal is sampled at its local maximum and minimum points [4]. The key generated ensures confidentiality and authenticity of the data collected by the sensor nodes.
2. Related Work
- In [5], the authors propose the introduction of a third party node for key generation purposes. This is to relieve the memory stress of the WSN. The other reasons for the introduction of the third parties include relieved computational burden and reduced communication overhead. The highlighted reasons are mostly due to resource constraints of WSN nodes. This method tends to be expensive because of extra hardware.In [6], key generation was performed by the two communicating sensors, by performing uniform sampling on the ECG signal at 125Hz for a duration of 5 seconds. The uniform sampling produced 625 samples which were further divided into 5 parts of 125 sample values. The 128 point Fast Fourier Transform (FFT) was performed on the 125 sample values to obtain 128 FFT coefficients the first 64 of each where used for feature vector generation, which was quantized to obtain the binary key. This method equally requires more memory to handle the computations and the samples.In [7], the authors propose a new approach to symmetric cryptographic key establishment, based on biometrics physiology with careful consideration on Body Sensor nodes performance constraints such as limitation in energy resources, data-processing and topology. In this paper, the authors used changeable topology to improve network performance and increase level of security. The hybrid topology, Star and Mesh topology, was deployed in this setup to ensure efficient usage of Body Sensor Node resources.In [8], the authors discuss how different WSNs operating systems (OS) manage memory. They discuss OSs such as MANTIS, LiteOS, TinyOS, Nano-RK, LIMOS, SOS, Contiki, Enix and µC/OS-II. Among the methods used by the different OS to manage memory include pre-emptive scheduling, module level programming, dynamic memory management, hybrid operating system, and support of virtual memory. They also discuss the research gaps and OS design with respect to memory management in WSNs. The research proposes inclusion of secondary memory management in future OS design and fair scheduling to ensure support for concurrent tasks. However, the research does not look at memory management during key agreement generation, which is the objective of this research. In [9], the authors proposed the use of Attribute-Based Encryption (ABE) for security and privacy implementation in Wireless Body Sensor Networks. The authors described the ABE as a fined-grained access control, which is a one-to-many encryption method, where the cipher-text is meant to be recognizable only by a group of users that satisfy a certain Access Policy (AP). The paper highlights the constraints of the Sensor nodes resources and the negative effects these resources have on the implementation of the security and privacy method to be deployed in WBSN. The need for high efficiency and strong demand for data security in WBANs, not only because of the resource constraints, but also for the applications.
3. Findings and Discussions
- The signal as illustrated in equation 1 [10] was used in the
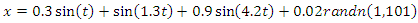 | (1) |
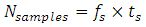 | (2) |
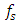 is the sampling frequency and
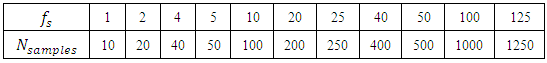
is the sampling frequency and 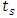 is the signal duration for which the sampling instant is considered. From Equation 2, we obtain table 1 has shown.
is the signal duration for which the sampling instant is considered. From Equation 2, we obtain table 1 has shown.
|
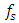 and number of samples
and number of samples 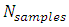 obtained after sampling at different frequencies.Figure 1 shows the MATLAB simulation of the signal before sampling for a duration of 10 seconds.
obtained after sampling at different frequencies.Figure 1 shows the MATLAB simulation of the signal before sampling for a duration of 10 seconds. 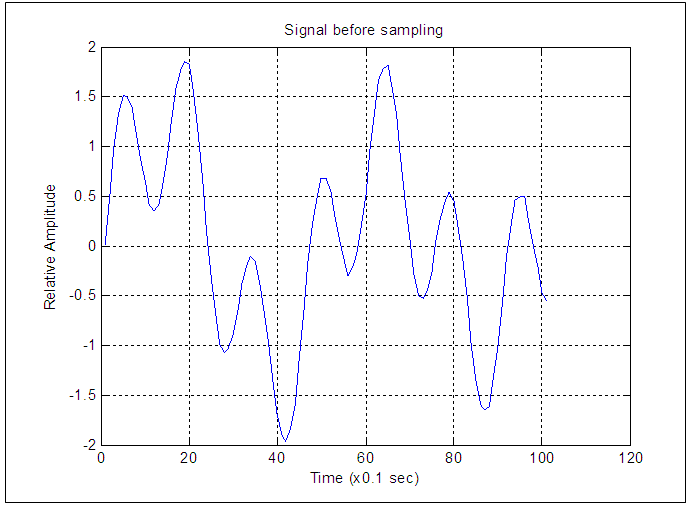 | Figure 1. Signal before Sampling |
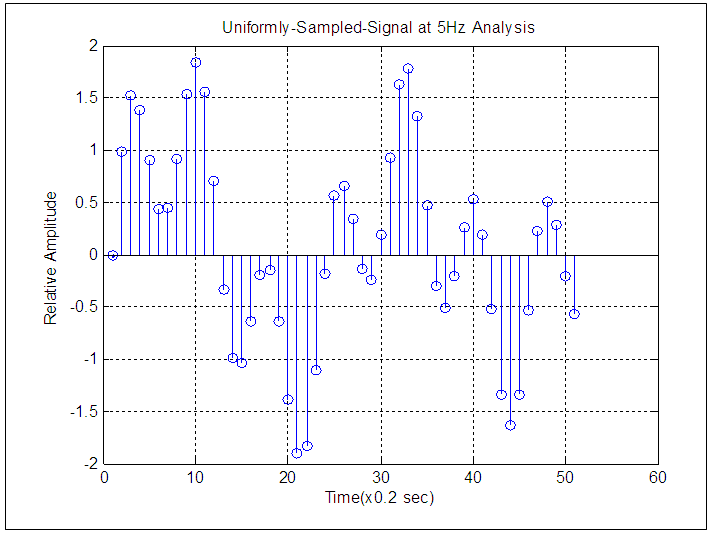 | Figure 2. Signal Uniformly Sampled at 5Hz |
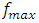 for a duration of 1s. The number of samples will be;
for a duration of 1s. The number of samples will be;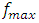 The same signal is subjected to minimax sampling through a minimax sampler
The same signal is subjected to minimax sampling through a minimax sampler 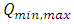 shown in figure 3 for a duration of 1s.
shown in figure 3 for a duration of 1s.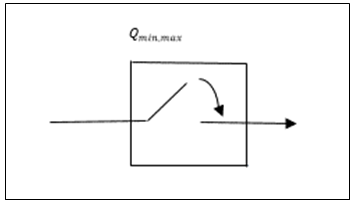 | Figure 3. Minimax Sampler |
 The capacity loss or excess capacity,
The capacity loss or excess capacity,  after minimax sampling will be given by
after minimax sampling will be given by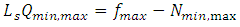 | (3) |
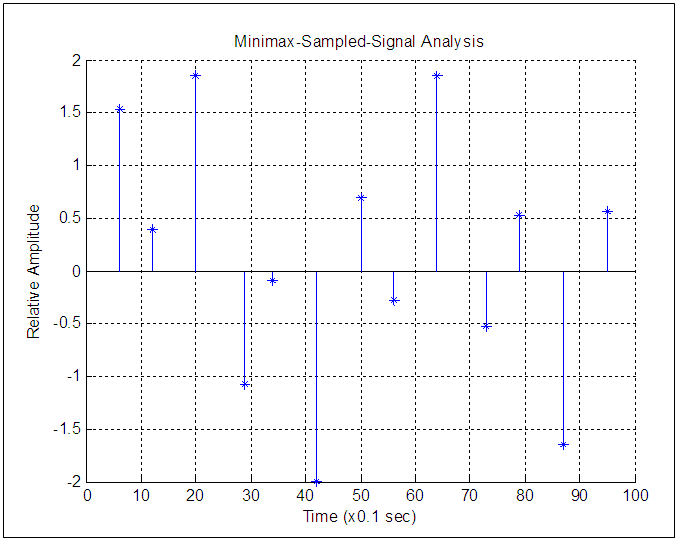 | Figure 4. Signal after Minimax Sampling |
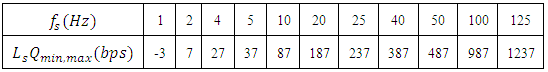
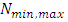 we can calculate Excess capacity at different frequencies to obtain table 2. Assuming 1 sample needs 1 bit per second of memory. From table 2 we obtain a plot of sampling frequency verses capacity loss or Excess capacity as shown in figure 5.
we can calculate Excess capacity at different frequencies to obtain table 2. Assuming 1 sample needs 1 bit per second of memory. From table 2 we obtain a plot of sampling frequency verses capacity loss or Excess capacity as shown in figure 5.
|
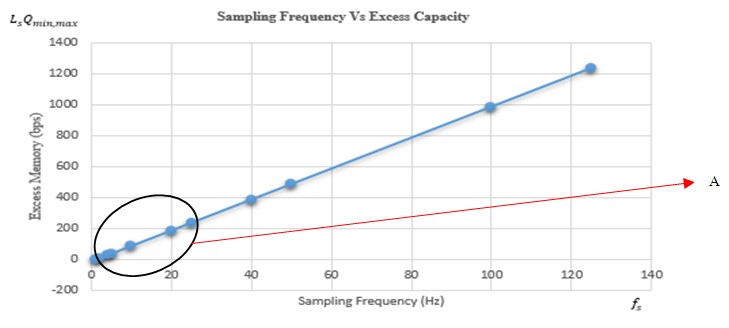 | Figure 5. Plot of Sampling Frequency Vs Excess Capacity4. Implementation Model |
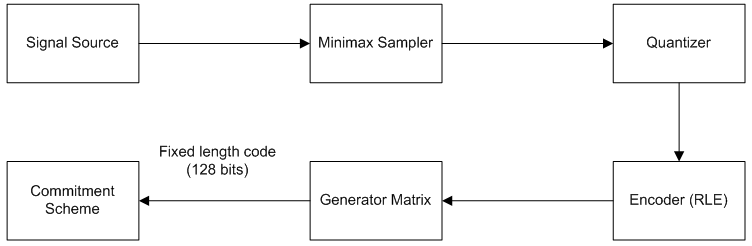 | Figure 6. Implementation model |
4. Conclusions and Future Work
- The research objectives are achieved using minimax sampling. The proposed minimax sampling results in higher signal compression as demonstrated from graphical interpretation of the results obtained when the signal was sampled at different frequencies. The minimax sampling uses very few samples for key generation because only the samples occurring at minimum and maximum points are considered. Future research should concentrate on the practical implementation of minimax sampling in WSNs during key agreement generation.Special thanks go to my supervisor Dr. Simon Tembo for his support and encouragement during the research. I wish to thank my wife and children for the support during this period. And most of all God almighty for the strength and good health during the course of study.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML