-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Networks and Communications
p-ISSN: 2168-4936 e-ISSN: 2168-4944
2014; 4(1): 1-11
doi:10.5923/j.ijnc.20140401.01
An Efficient Pre-computed Backup Path on the IGP Network Communication
Radwan S. Abujassar1, Ma’moun Khalid1, Mohammed Ghanbari2, 3
1School of Information Technology, MEU University, Jordan
2School of Electrical and Computer Engineering, University of Tehran, Iran, Tehran
3School of Computer Science and Electronic Engineering, University of Essex
Correspondence to: Radwan S. Abujassar, School of Information Technology, MEU University, Jordan.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Currently, data communication during heavy traffic transmission on the network suffers from node failures. A failure in the network is required to be restored by the routing protocols in the networks. Traditional routing protocols schemes normally compute a routing table which contains all paths between all nodes on the network. Hence, the data packets will be passed via the single shortest path which is the best path between each source and destination. In this paper, a pre-computed alternate path is introduced to assist the congested networks to continue passing the data packets from its source to the final destination once failure occurs. The proposed alternative routing table (ART) algorithm aims to re-route the traffic through a backup route when the primary path has failed. We have evaluated the performance of the proposed scheme with OSPF routing protocol through NS2 simulator. The results show that packet losses, rerouting and end to end delay times of the proposed methods are substantially improved.
Keywords: Component, Link state, ART (Alternative Routing Table.)
Cite this paper: Radwan S. Abujassar, Ma’moun Khalid, Mohammed Ghanbari, An Efficient Pre-computed Backup Path on the IGP Network Communication, International Journal of Networks and Communications, Vol. 4 No. 1, 2014, pp. 1-11. doi: 10.5923/j.ijnc.20140401.01.
Article Outline
1. Introduction
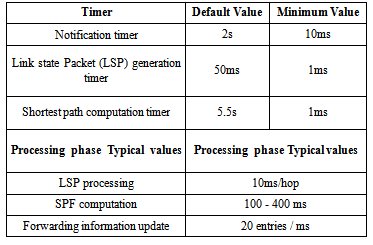
- Network communication continues to increase and thus the system is required to tolerate large volumes of traffic with respect to huge capacity of links. Network communication is affected by frequent failures and this leads to find an efficient recovery mechanism. In current networks, failures occur frequently, which will affect the stability of the network. When there is a link or a node failure, the node that is connected to that failure needs to re-compute its routing table and propagate the updates to all nodes concerned with this failure. Recovery mechanism has a motivation that concerns two cases. First, the time required to detect failure.Second, the time to compute a new shortest path that takes roughly 70ms. However, the slow convergence time of the routing protocol for the network when failure occurs has inducted to find an optimal solution to carry all traffic to route from an alternative path until the routing protocol updates the routing table and re-computes a new shortest path. Alternative Routing Table (ART) algorithm aims to recover the network from failure during a short period of time. Precisely, when link or node goes down, it aims to reduce delays and improve throughput in the network. Hence, the pre-computed alternative path can be used when link or node fails on the primary path without waiting for the routing protocol to re-compute a new shortest path [12].The Open Shortest Path First (OSPF) routing protocol is used as a dynamic link state protocol for TCP/IP or UDP traffic and is designed to update the information for topology by sending a Link State Advertisement (LSA) based on the presence of a failure. The convergence time of the recovery mechanism is still too large for the real time applications. The convergence time can be of the order of 100’s of millisecond or even 10’s of seconds in the Border Gateway Protocol (BGP) networks. Table 1 lists the default and minimum times for the routing protocol to re-compute a new shortest path. Hence, during the process, while the routing protocol is converging micro-loops may be created. The affection of this can lead to increase loss of packets and end to end delay in the applications such as video or VOIP traffic; because the source will keep sending packets until it receives a notification that a failure has occurred. In this paper, we concentrate on the original routing table, which is computed by the Link State Protocol. We propose a new algorithm to create a new backup routing table with excluding all primary paths in the original routing table. The main contribution of this paper is an alternative and a fully disjoint path computed by using the original routing table, which guarantees that the backup path does not join with any node or link on the primary path between source and destination to avoid a loop in the network.
|
2. Related Work
- An efficient routing protocol algorithm has been built for achieving robustness and fast convergence within a short time in case of failure. In [7] authers address classifications of failure. The result shows that 80% of all failures are unplanned. According to this finding, the 70% of failure is due to the effect of a single link failure at a time, and the remaining is due to the effect of a shared link risk groups. The protection schema is a proactive mechanism, which calculates backup routes in advance while the restoration schema is reactive by calculating the backup routes when failure has been detected [2, 10]. The restoration schema considers more flexibility with regard to the location of failures. The disjoint path between source and destination considers the best solution to recover the network from failure, which is guaranteed to pass the traffic through it to the destination with reduced loss of packets [15]. In [5, 4] the authors discuss the cost of the links in the network, which is considered to be an important parameter in determining the best path through the routing protocol algorithm. The minimum path cost will be determined by comparing it with other candidate paths. There are two kinds of the Dijkstra algorithms. Firstly, there is a Dijkstra algorithm to compute the best path by removing the links with bandwidths less than a threshold. Secondly, there is an on demand Dijkstra algorithm, which generates the shortest path tree to a precomputed node [3]. The node will be added to the tree depending on the requested bandwidth [16]. In [11, 14] the authors proposed a new mechanism, termed Failure Insensitive Technique (FIR). FIR uses the specific forwarding interface to provide a backup next hop with loop free. The FIR mechanism makes the node, which is connected to the failure to add a new header by re-encapsulating the packets and then re-sending them to the adjacent nodes to inform them about the fault through the interface packets that arrive. Hence, based on the interface packets when failure occurred, the adjacent node will reroute the affected packets and the other nodes which will not know about the failure by sending packets according to pre-computed routing tables. FIR has many drawbacks as follows: the encapsulation of packets is not desirable because that will reduce the throughput and make the end-to-end delay longer. In addition, FIR cannot provide protection against node failure. The Internet Protocol Fast Re-Route (IPFRR) is an applicable technique. It includes the LFA, U-turn and not-via address [9, 13]. The drawback to the IPFRR technique is that loop free is not guaranteed because the packet can be returned to the source with regard to a specific forwarding pre-computed routing table for each node on the network. In addition, not-via address needs to encapsulate/ de-capsulate packet, which affects network performance [8].
3. ART Technique
- While most proposed solutions intend to reduce recovery time through many technique. The efficient routing protocol algorithms have been built for achieving robustness and fast convergence within a short time in case of link or node failure [7, 10, 2, 15]. The results show that 80% of all failures are unplanned, as shown in table 1. According to that, 70% of failures affect a single link at a time, and the remaining percentage is affected by shared link risk groups. The work in this paper provides a new technique based on ART algorithm. In ART algorithm, the computed disjoint path between source and destination considers the best solution to recover the network from node or link failure, regardless of the location of the failure, and also disjoint path is guaranteed to be local loop free in the network. A node in the network may have many interfaces, therefore when a node fails, all its interfaces will fail simultaneously, and loss of signals will occur. Hence, the disjoint path can protect data packets from dropping and deliver them safely to the destination, improving end-to-end delay. This is because disjoint path excludes all links or nodes in the primary path. The main goal of ART algorithm is to reduce recovery convergence time. This section illustrates that the core principle of ART algorithm is that once network routers receive notification of an incident of failure, the ART algorithm in turn reroutes the traffic via pre-computed backup disjoint path until the routing protocol computes the new primary path. Additionally, ART algorithm approach avoids local loops in the computed backup path. ART is invoked by the source node, which reroutes the traffic after experiencing a link failure or receiving an LSA/LSP (if the source node has already computed a backup path in advance). The node must calculate and update a set of parameters regularly, and based on these parameters the source node must decide whether to invoke backup path. All these calculations performed by the nodes are based upon the table 1.The mechanism of ART algorithm has been illustrated in the flowchart as shown in fig. 1 to show the mechanism of computing disjoint path. The algorithm computes disjoint backup path in the five following cases:– First: Routing protocol computing the routing table for the topology.– Second: Source node identifies its adjacent node through the routing table and then broadcasts a small packet to all adjacent nodes, excluding the adja- cent node (first primary hop) on the primary path.– Third: Each adjacent node starts checking if it has a disjoint path to the destination not containing any node from the primary path. Thereafter, the adjacent node will send an acknowledgement to the source of whether or not it has a disjoint path.– Fourth: The source node receives all acknowledgements from adjacent nodes.If there is any positive answer, then the source node will add this adjacent node as a first hop, and its neighbours as the second hop in the new routing table.– Fifth: If all answers are negative, the nodes will keep searching until the backup routing table is completed.

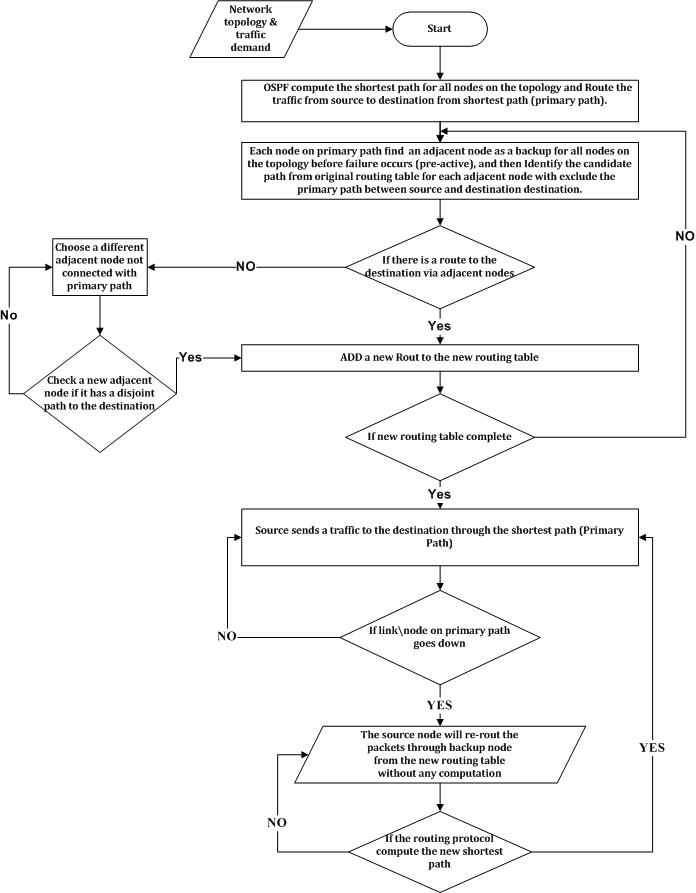 | Figure 1. Algorithm Flowchart |
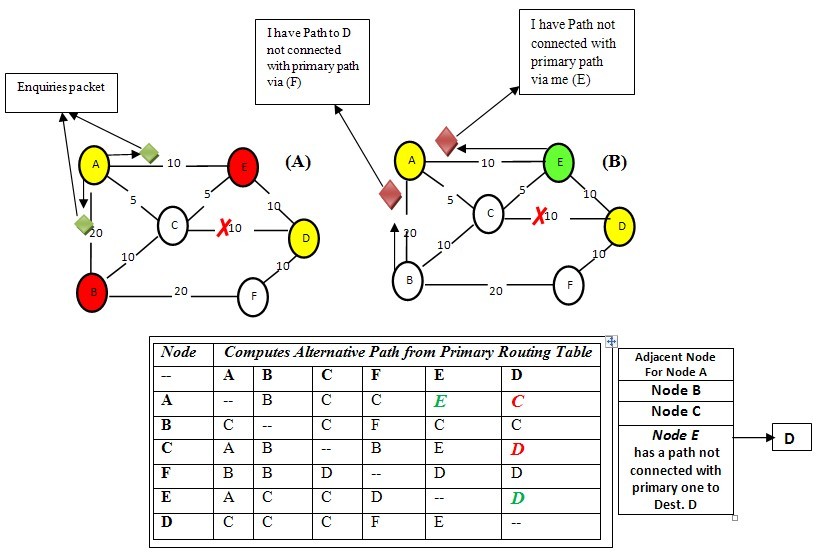 | Figure 2. Example illustrating the ART mechanism |
3.1. The ART Algorithm’s Operation
- Before describing the details of the algorithm, the following delay timer and parameters are clarified:– Link Failure Detection: the time between detecting the link failure and hardware level.– SPF Delay: A default delay between receiving an LSA/LSP and starting the shortest path calculation.– Neighbour SPT Calculation: Delay due the SPT calculations and routing table update performed at the neighbour node.– FIB delay: The time required by any node to upload the original routing table.– Adjacent Total Convergence Delay:
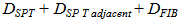 | (1) |
4. Related Research with Comparative Study of Convergence Time
- While ART algorithm computes a disjoint backup path to reduce recovery time in the network, we can compare the recovery time of traditional link state protocol with the convergence time of a link state protocol combined with a state of the art ART algorithm. In order to compare the convergence time of a link state protocol with that of link state protocol combined with ART algorithm, the duration of each operation carried out by a regular link state routing protocol must be known; the relevant operations are link failure detection, LSP origination, flooding SPT com- putation and FIB updates. In a normal link state operation, all nodes (predecessor) can start forwarding traffic once they receive the link failure message, compute a new SFP and update the FIB. The Open Shortest Path First (OSPF) routing protocol is used as a dynamic link state protocol for TCP/IP or UDP traffic, and is designed to update the information for topology by sending an LSA based on the presence of a failure. The convergence time of the recovery mechanism is still too large for the real application. The convergence time can be of the order of tens of milliseconds or even tens of seconds in Border Gateway Protocol (BGP) [3]. Hence, during the process, while the routing protocol is converging, micro-loops may be created. This can lead to increased loss of packets and end-to-end delay in most applications such as video and VoIP traffics, because the source keeps sending packets to its destination until it receives a notification that a failure has occurred.
5. Results
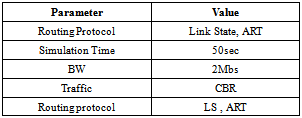
- Part of a Mesh Network was replicated by using a NS-2 simulator as a single area OSPF network. The links represented the OSPF routing metrics. UDP traffic is sent from source to destination. Every simulation involved one or two link failures on the primary path. The link failure could occur along the primary path at any time without notification and instantaneously at different hop count distances between source and destination nodes. When the simulation was run for 50 seconds, all the links can potentially fail and a loop could occur after 10 seconds [6]. This is because the routing protocol takes approximately 6.6 seconds to compute the primary path and construct the routing table for the network’s topology [7]. Therefore, one needs to give the routing protocol enough time to guarantee that the routing table for each node has been constructed, and in turn, each node has received identical copy information about the network topology. This enables data packets to be transmitted successfully to their final destination and then they can begin to compute the backup route from the original routing table. In this experiment, we ran the simulator 50 times with randomly configured failures between source and destination. In addition, the source and destination were randomly configured. This caused failure to occur arbitrarily and haphazardly. The LS protocol started to construct a routing table for the network’s topology once the network started working. The UDP traffic for all the source nodes was configured to start sending from 1.0s to 50.0s. If the LS protocol is not combined with the ART algorithm, failure can lead to increased loops in the network. This phenomenon will be harmful if it causes link utilisation to reach 100%, which will increase loss of packets.This experiment was implemented using the parameters stated in table 2. At first, we ran the simulator with only LS protocol. After analysing the results, we again ran the simulator for the same network topology with both LS protocol with ART algorithm in order to evaluate the impacts of the computed disjoint backup path by ART algorithm.
|
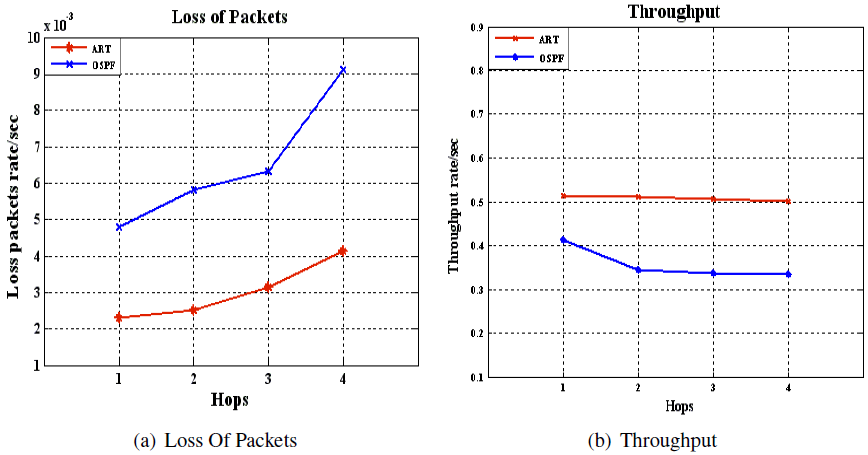 | Figure 3. Loss Packets and Throughput |
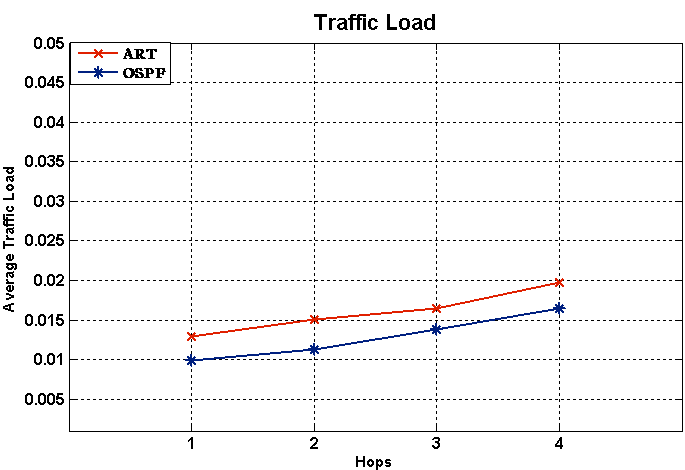 | Figure 4. Load |
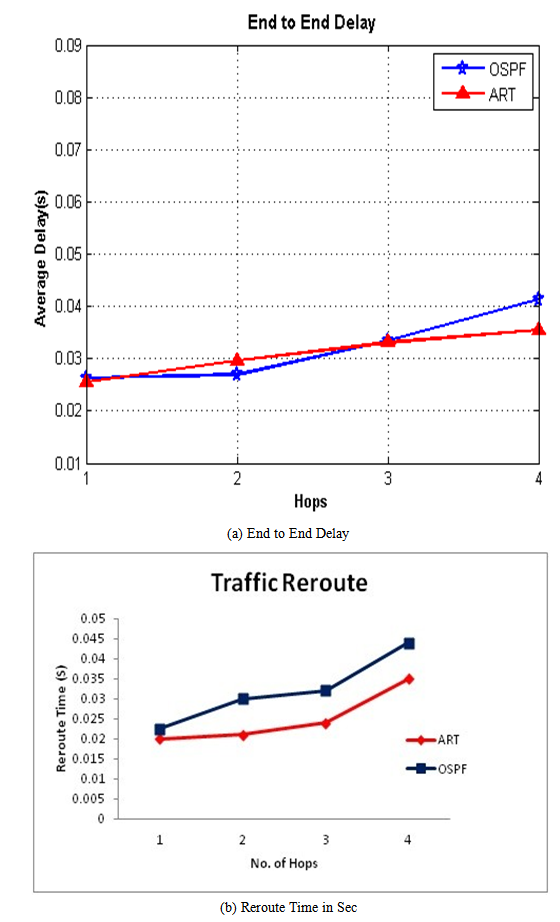 | Figure 5. End to End delay and Reroute Time in Sec |
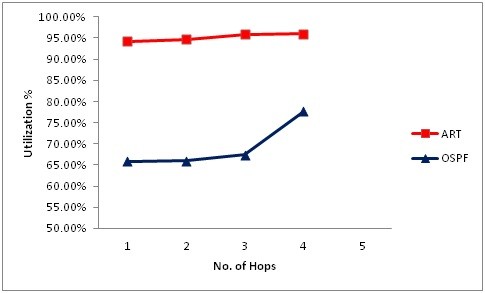 | Figure 6. The effective backup path during the frequently of failure |
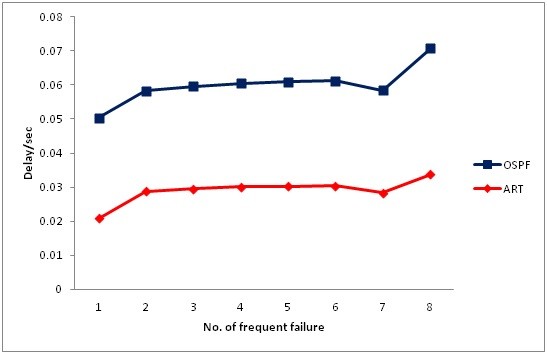 | Figure 7. The effective backup path during the frequently of failure |
6. Conclusions
- This paper introduced a new algorithm called ART mechanism. When the failure occurred in an IGP network that will lead to degrade from network performance, and lead to producing such problems as local loops in the network. When local loops occur, many problems can arise, such as wasting network resources and delaying sensitive traffic passing through this network. The ART mechanism reduces recovery time by computing a disjoint path between the source and the destination in advance. In case of link state protocol only, the convergence delay will be higher, and links can form loops and holding time for the packets in the nodes buffer will increase and then lead to increase delay in the network. Hence, LS combined with ART algorithm not only reduces recovery time; it also improves the quality of service for sensitive traffic and reduces packet loss and delay times in the network. However, the ART algorithm creating a new backup routing table has a disjoint backup path for all nodes on the network. The new backup routing table is based on the original routing table, which is computed by a link state. For real time traffic, the results show that LS with ART algorithm reduces the loss of packets and delay between source and destination. Additionally, we have proved that the ART algorithm can avoid the occurrence of loops in the network by keeping the utilisation stable compared to link state protocol. The ART algorithm has its own messages that are sent between nodes to create the new shortest path, and these packets do not affect the performance of the network.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML