-
Paper Information
- Next Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Internet of Things
2019; 8(1): 10-16
doi:10.5923/j.ijit.20190801.02

Threat Detection Model in Edge for the Internet of Things - A Comprehensive Multi-Layer Solution to Detect Threats in Edge and Cluster Large Networks of IoT
Karthika Venkatraman, Jihad Qaddour
Department of Information Technology, Illinois State University, Normal, United States of America
Correspondence to: Jihad Qaddour, Department of Information Technology, Illinois State University, Normal, United States of America.
| Email: |  |
Copyright © 2019 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

The Internet of Things (IoT) is emerging rapidly, with a huge impact on consumer products, resulting in the emergence of AI-based products such as Google Home and Amazon Echo. As the scale of IoT products gets larger, the more they would have to process personal information of users on a daily basis and as a result, the enterprises will have to enhance the security features to protect the devices from attacks. The addition of security features might effectively mean an increase in processing capability, increase in cost and storage, while the device-makers look to keep the prices low. This paper attempts to analyze security risks surrounding the Internet of Things and offer intrusion detection solution at the edge by a detection mechanism in the router.
Keywords: Internet of things, Security, Intrusion detection, Edge, Router
Cite this paper: Karthika Venkatraman, Jihad Qaddour, Threat Detection Model in Edge for the Internet of Things - A Comprehensive Multi-Layer Solution to Detect Threats in Edge and Cluster Large Networks of IoT, International Journal of Internet of Things, Vol. 8 No. 1, 2019, pp. 10-16. doi: 10.5923/j.ijit.20190801.02.
Article Outline
1. Introduction
- In today’s IoT landscape, with the technology still being nascent, it is greatly vulnerable to a myriad of attacks such as Distributed Denial of Service (DDoS), eavesdropping and data leaks as detailed in [3]. However, due to its limited processing capacity and limited storage, implementing traditional solutions such as periodic rotation of passwords, multifactor authentication, AES-128 encryption, host-based Intrusion Detection Systems/Intrusion Prevention systems, anti-virus software, malware detection, Distributed Denial of Service protection, bot protection remain a challenge.As a result, solutions surrounding intrusion detection or intrusion prevention need to account for the limitations in IoT devices and work around it. The challenges that stem from limitations in IoT could be potentially circumvented through a distributed processing approach that does the processing across devices in the network. However, this will require manufacturers to scale up the processing, memory and storage capacity of devices in the future. Alternatively, the IoT devices could be clustered and a centralized processing manager could be deployed for each IoT cluster. While this approach could bring in the benefits of distributed control and inter-manager communication for alerts and coordination, this will also add to the hardware overhead in the IoT network causing a significant increase in the overall cost of implementation.In this paper, a solution that effectively utilizes the untapped processing capacity of routers is presented in the form of a software application that could be installed in a router and serve as a threat detection mechanism in an on-going basis. This paper is organized into six sections. The second section provides a literature review of existing work discussing existing solutions. The third section discusses challenges in existing work which this paper attempts to solve. The fourth section illustrates the proposed new architecture of threat detection in edge, along with a cluster management method and automation technique to update benchmark values.
2. Literature Review
- As businesses increasingly get electronic devices into the market that can interact with each other, regulatory measures are necessary to ensure security in them. However, in the case of IoT, the regulatory efforts are not consistent with the unpreceded growth of devices [2]. As per the report demonstrated in [4], DBS Asian Insights has predicted that the IoT installed base will grow from 6.3M units in 2016 to 1.25B in 2030. This could potentially offset the security mechanisms that protect technology preceding IoT leaving networks open for attacks and loss of data. Recognizing that the risks outweigh opportunities in IoT, the Internet of Things Cybersecurity Improvement Act was passed in 2017, which seeks to enforce security in devices procured by the government. However, a broader regulation as of today is not a reality [5].One of the major deterrents of IoT security is the economic value it brings. The return on investment for the funds dispatched in enhanced security does not make economic sense for companies to actively pursue security. As a result, the possibility of improved security might not materialize in the foreseeable future. This calls for cost-effective, readily- available solutions that could be incorporated without a significant demand for infrastructure on the part of device-makers or end-users.This warrants an immediate security solution that addresses the most crucial among problems facing IoT. As discussed in [6], there are three ways to go about implementing security in IoT viz at a centralized location, on-the-edge and on the gateway. The benefits of implementation include the ability to have an overall view, reduced cost, energy efficiency, and ease-of-sharing. However, it comes with the cost of single point failure and slow feedback. Implementing security in gateway equipment such as cellphones allows instant feedback from users, privacy, the ubiquity of equipment and the possibility of data aggregation however at the cost of complexity, software management, and reduced security. The third method is security in the edge which brings instant feedback, reduces data transfer and improves security. The disadvantages of security in edge according to [6] is the cost, energy consumption and lack of overview.These disadvantages can be addressed by effective use of equipment that is already available in the market. [7] demonstrates a load-balancing solution by tapping on to underutilized line cards to share the router’s processing power with supporting algorithms. This brings us to the potential of routers which could be used for edge security and address its inherent disadvantages cost, energy consumption and lack of overview.[8] is another instance of the router’s potential to support resource-intense activities. [8] is an adaptive edge-computing solution based on regressive admission control and fuzzy queuing to react to quality-of-service changes within heterogeneous networks. This supports the security solution described in the rest of the paper.
3. Challenges in Current Work
- A. Distributed Security Mechanism for resource-Constrained IoT devices[9] offers a distributed mechanism to secure IoT network in multiple layers. The approach here is to secure the entire network by processing lighter operations in the end-point, heavier operations in a gateway while using symmetric encryption for data objects combined with native wireless security. In this case, the gateway provides additional protection by securing data using TLS. The proposed solution in the paper has been demonstrated through real-time evaluations for targeted Class-0 IoT devices. While this offers layers of security, this does not address the need for intrusion detection in IoT.B. Analysis of Security Mechanisms Based on Clusters IoT Environments[10] begins with a systematic analysis of existing research in IoT at the privacy level and control access in this type of environment. Then presents the issues that need to be immediately addressed, from different clusters and identified areas of application. This paper does not offer a solution to the issues identified.C. Flow-sensitive and Context-sensitive mechanisms[11] attempts to capture the baseline behavior of IoT devices to use them for anomaly detection. While noting that the existing methods are either flow-sensitive or context-sensitive information to capture system call context which limits the scope and accuracy. The paper proposes using context-sensitive features based on control-flow and details the process to detect anomalies using the same.
4. Proposed Solution
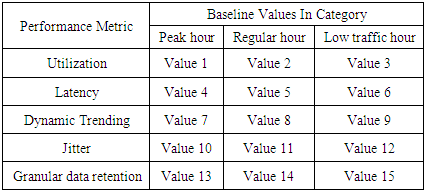
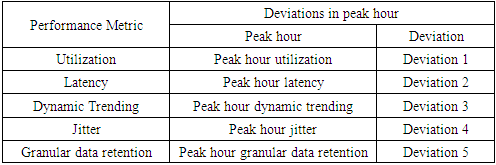
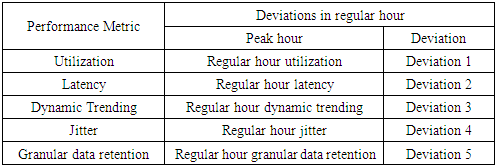
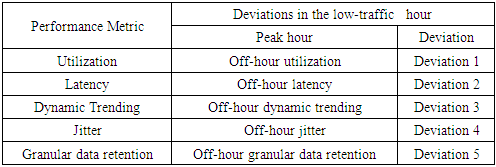
- This paper proposes a solution in two-layers. The first layer utilizes the processing capacity of routers to detect threats in IoT edge. The focus areas of this paper are Distributed Denial of Service (DDoS), password attacks and code injection which can further be extended to detect all other types of threats in the future. Threat detection in the edge is implemented as a software application that can be installed in the router to monitor incoming and outgoing traffic pertaining to IoT. The second layer organizes the IoT network into clusters with a fixed size, each with a manager to facilitate intra-cluster inter-cluster communication.A. IoT security through a router applicationA router application monitors all incoming and outgoing traffic to and from IoT devices to detect Distributed Denial of Service, password attacks and code injection in three software modules. Intelligence about Denial of Service can be obtained by observing the following factors measured against baseline values expected for both peak and regular hours of IoT traffic.• The volume of ingress traffic in terms of packets per second and high level of deviation from baseline• Percentage of CPU utilization and high level of deviation from baseline• Throughput and high level of deviation from baseline• Bandwidth and high level of deviation from baseline• More than one parameter demonstrating moderate to high deviation from baseline• One or more parameters demonstrating moderate to high deviation from baseline over a period of time• All of the aforementioned deviations occur at a time frame that is not peak hour activity• Possible attack packets from one more sourceDenial of Service (DoS) and its variants can be measured with a high degree of accuracy using any of the following algorithms PART, BayesNet, IBK, Logistic, J48, Random Committee, and InputMapped. However, research in [13] along with [14] shows PART as the top choice for DoS with an accuracy of 98.5539% which is what will be used in the proposed solution. PART is a Partial Decision Tree algorithm and is an advanced version of C4.5 and RIPPER algorithms. The most notable aspect of this algorithm is it doesn’t need global optimization to generate reliable rules. PART decision trees will be used on IoT dataset in edge to classify attacks from possible false alarms.Authentication in home appliances is usually carried out through mobile phones using an authentication application. The solution proposed in this paper relies on correctly identifying legitimate devices and blocking all other unknown devices out of the network. The attack detection, in this case, is distributed among router and mobile device.Password attack detection can happen by tracking authentication requests coming from known sources and identifying legitimate devices through multi-factor behavior-based fingerprinting techniques involving factors beyond IP, mac address, OS and RFID.In the event that a node in the IoT network is compromised, code injection is a likely next step on the part of attackers. Code or malware injection can be detected using proprietary software such as Avast, Bitdefender, BullGuard, Panda or McAfee. Alternatively, open-source equivalents can be used to achieve the same results. However, the biggest disadvantage here is the resources it consumes. Malware detection is to be performed in a distributed fashion between edge, gateway and remote processing by accessing a cloud-based application.In order to optimize resource utilization in the router or other edge devices, malware detection and code injection should between on-device computation and cloud-based malware signature detection. The module in IDS software at the edge should be built to detect common signatures and if the code needs to be checked for advanced threats or analyzed further, it should be sent to a cloud-based solution that detects malware/malicious code and alerts administrators about it. However, the cloud-based solution could potentially increase the turnaround time.While advanced routers such as CISCO 7600 come with DDOS protection and have an intrusion capability, they are not designed to handle IoT traffic nor are the performance metrics benchmarked and optimized for IoT. The benefit of the proposed solution is, it is designed specifically for a particular IoT network whose traffic is observed and analyzed over time in an automated manner. This level of granularity greatly helps minimize false positives and false negatives which are crucial success factors for IoT.B. Clustered approach with managers to facilitate efficient communication and securityWhile the intrusion detection mechanism in the edge might suffice for small networks, additional controls would prove useful in case of large enterprise-grade IoT networks.The second step in ensuring security in IoT is to organize the entire IoT network in the form of clusters for ease of management and communication. The devices in the IoT network could be grouped based on the content and be assigned a manager which serves as the single point of communication for the cluster and has maximum processing capacity in the cluster. This manager will handle authentication for the cluster, facilitate updates and perform security functions in a distributed security solution for IoT network. The biggest benefit of this approach is that it renders the capability to perform resource-intense functions for the entire clusters comprising or heterogeneous devices that may or may not have the capacity to support security functions themselves.C. Authenticating cluster managers and IoT intrusion detection applicationAn important success factor is to enforce mutual authentication between IoT cluster managers and IoT intrusion detection application. This step will help eliminate the possibility of rouge edge devices and rogue endpoints in the network. Furthermore, authentication should also be enforced when IoT cluster managers interact with each other.This can be accomplished through an authentication mechanism involving PUF algorithm. The Physical Unclonable Function (PUF) described in [20] is an entity embodied in a physical structure such as microchips and is often used in applications with high-security requirements. This will be used along with a fuzzy extractor or key extractor to uniquely identify IoT devices, device managers and router.[21] shows a mechanism of DDoS protection implemented in routers through packet classification and traffic control. While the mechanism proposed in [12] differs from the model discussed in this paper, it demonstrates the feasibility of innovative applications in router devices.
5. Architecture
- A. Intrusion DetectionThe proposed solution for intrusion detection has a traffic handler that parses incoming and outgoing traffic for IoT devices in the network and then analyzes the parsed traffic to identify possible Distributed Denial of Service, password attacks and code injection attacks through three separate modules in this application.In addition, this application maintains a cloud repository to persist logs that have saves only events of interest over time, allowing complex AI based analytics using cloud resources, while saving storage from logging all events.Finally, the architecture encloses a module to alert system administrators about an ongoing attack that requires immediate action. In a home network, the owner plays the role of an administrator and receives email alerts.The intrusion detection solution is to be implemented as an application in the router. In a home network, this eliminates the need for additional hardware and costs associated with it, while utilizing the untapped potential of router.
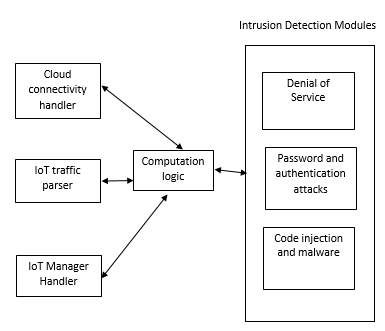 | Figure 1. Architecture for Intrusion Detection |
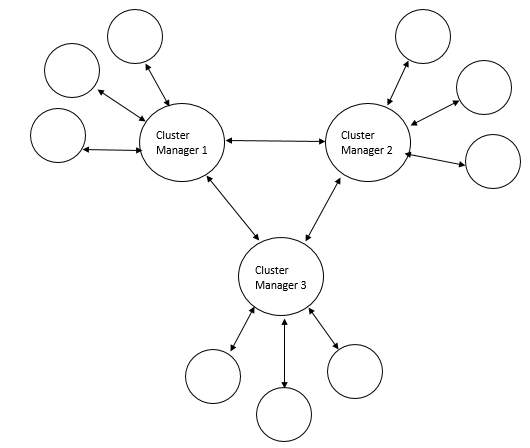 | Figure 2. Cluster management in IoT through managers |
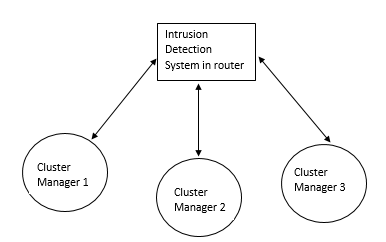 | Figure 3. Cluster managers and their interaction with the intrusion detection system |
|
|
|
|
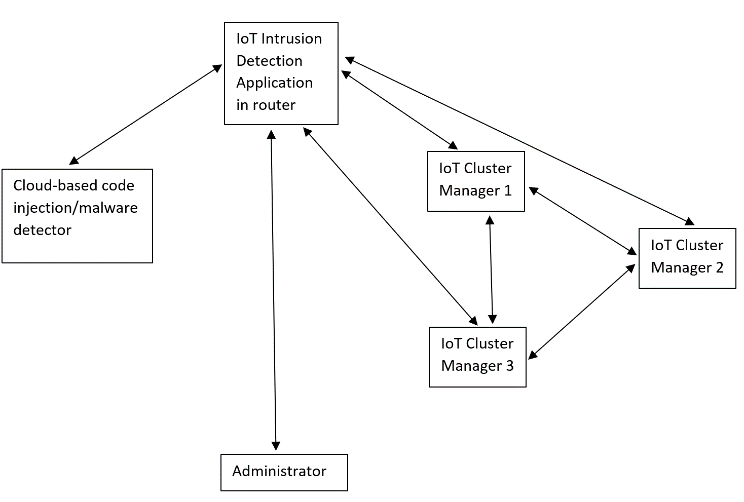 | Figure 4. Interaction between IoT Intrusion Detection application, Cluster managers, Cloud-based Malware detection system and the administrator |
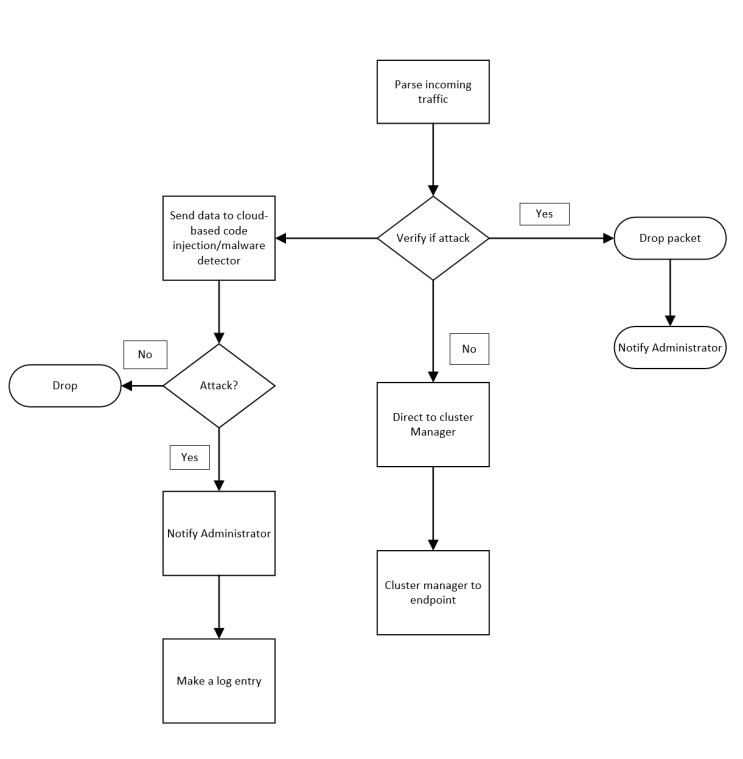 | Figure 5. The workflow of IoT Intrusion Detection Application |
6. Conclusions
- Thus the solution discussed so far, utilizes the unused processing capacity of routers to host an IDS/IPS application, while eliminating additional hardware needs. Furthermore, it offers cluster management and performance benchmarking approaches that could be applied to existing IoT networks while keeping the costs low [28].
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML