-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Internet of Things
2017; 6(2): 67-70
doi:10.5923/j.ijit.20170602.12

Smart Key: Secure Door Lock System using NFC Enabled Smartphone
Menezes Allwyn Bonaventure, Priyadarshini S., Priyanka, Sindhu Nayak, Ushadevi A.
Department of Computer Science, St Joseph Engineering College, Mangalore, India
Correspondence to: Priyanka, Department of Computer Science, St Joseph Engineering College, Mangalore, India.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Smartphones have become very popular and versatile devices. An emerging trend is the integration of smart phones into security systems and applications, particularly access control systems to unlock doors. Smartphone based security solutions promise to greatly enhance the user’s experience by providing advanced features far beyond the conventional dedicated tokens/transponders. The generic security architecture protects the electronic access tokens on the smartphone and provides advanced features such as context-aware access policies, remote issuing, and revocation of access rights and their delegation to other users. Various approaches to instantiating the security architecture based on different hardware-based trusted execution environments and elaborate on their security properties are discussed here. The door lock system is implemented based on the latest Android-based NFC-enabled smartphone.
Keywords: Nearfield Communication, Mobile Security, Access Control
Cite this paper: Menezes Allwyn Bonaventure, Priyadarshini S., Priyanka, Sindhu Nayak, Ushadevi A., Smart Key: Secure Door Lock System using NFC Enabled Smartphone, International Journal of Internet of Things, Vol. 6 No. 2, 2017, pp. 67-70. doi: 10.5923/j.ijit.20170602.12.
Article Outline
1. Introduction
- Today, smartphones are high-performance platforms providing a wide range of features and have become an integral part of daily life. The increasing computing and storage capabilities, the vast number and variety of apps available on app stores and new communication interfaces, such as Near Field Communication (NFC), provide many deployment possibilities for smartphones, including electronic ticketing, payment and access control. In this context, an emerging trend is the integration of smartphones into modern automotive systems and applications such as access control to lock and unlock and also configure the system. In particular, the NFC interface is well-suited for such applications due to its short nominal communication range (of a few centimeters) providing basic assurance of the user’s physical proximity. In this paper, the focus is on smartphone-based NFC-enabled door lock systems. An electronic door lock is an anti-theft device that prevents an unknown person from entering the house unless the corresponding access token is (physically) present and authenticated. Currently, this access token is a transponder (i.e., an NFC chip) embedded into the NFC smartphone. They do not require users to obtain a physical transponder but allow them to use their smartphone to remotely obtain electronic door lock access. Moreover, access rights can be delegated to other users, revoked or bound to specific policies. Despite the mentioned advantages for users, the core challenge concerns the security aspects of smartphone based door lock systems. Smartphones are complex devices and appealing targets of attacks (e.g., by malware), especially when they are used in security-critical applications. The traditional locks used in practice are closed and proprietary systems and suffer from various security vulnerabilities. The reasons are conceptual protocol design flaws as well as the deployment of insecure or weak cryptographic schemes. On the other hand, a commercial smartphone-based NFC enabled door lock systems have been introduced recently, but without providing technical details or information on their security properties. Goal and contribution: An open smartphone-based lock system architecture and the underlying security framework, which provides enhanced functional and security features and overcomes the security issues of the conventional door lock systems. In particular, the contribution is as follows: Framework for smartphone-based door lock systems: Framework considers the functional and security requirements on the protocols and the system architecture of a smartphone based solution under realistic adversary models. Evaluation of existing security hardware: This paper evaluates and discuss various instantiations of security architecture using different approaches to establishing trusted execution environments on smartphones. It discusses which security guarantees can be provided by these instantiations, under which assumptions, and how some of these assumptions can be fulfilled by leveraging the features of security hardware currently available on recent smartphones. Implementation: It shows show that it is feasible to implement a secure NFC-enabled and smartphone based door lock system. In particular, the paper discusses the conditions for the secure integration of enhanced features such as delegation under a strong but realistic adversary model, where the adversary has full control over the software on the smartphone platform. Hereby, it takes the technical limitations of currently available security hardware for smartphones into account. Outline: The paper presents the framework for smartphone based door lock system systems, an overview of related work in Section 2 and the proposed system in Section 3. The security requirements are defined in section 4 and the implementation and evaluation of solution in Section 5. Finally, conclude in Section 6. References are presented in Section 7.
2. Related Work
- In this section, existing door lock system systems in practice and in literature are discussed. Further, it gives an overview of related work regarding access control with smartphones. NFC-based Door lock system: NXP Semiconductors presented the prototype of an NFC-based door lock system. The security of this approach relies on the secure element of the smartphone. However, it is unclear how this secure element is instantiated and whether this approach requires new phones with special security hardware. Transponder-based Door lock system: Lemke et al present a system model and requirement analysis for electronic door lock system systems that use dedicated hardware tokens. The proposed model does not capture advanced use cases such as delegation and thus cannot be applied to the system. Delegable Access Control with Smartphones: The work is along the lines of the Smart Token system by Dmitrienko et al. which enables NFC-enabled smartphones to maintain electronic access control tokens that can be delegated to other users. Specifically, the project adapt the protocols of the Smart Token scheme to the door lock system use case and provide a tool-based security verification of these protocols.
3. Proposed System
- A. System Model The system model is depicted in Figure 1 and involves a Security Technician, a Home, an owner, and a user.
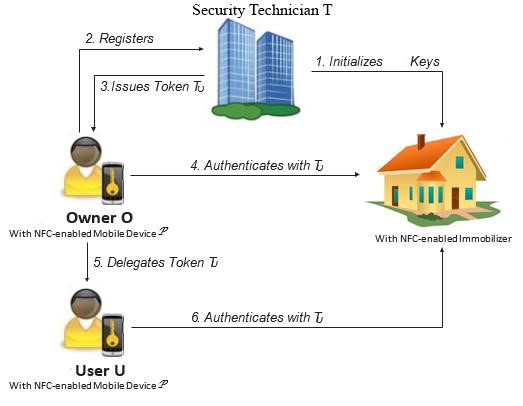 | Figure 1. System Model |
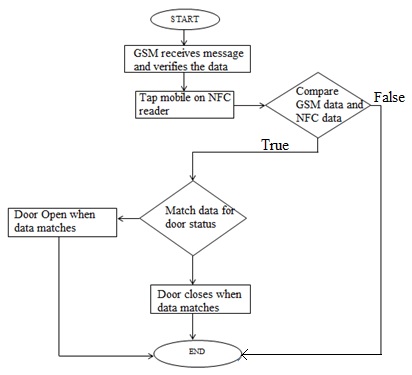 | Figure 2. Operational Flowchart |
4. Security Requirements
- Protocol-specific requirements:The main security objective of a door lock system is the secure authentication of the owner (or the delegated user) to the door lock system. Platform-specific requirements:Mobile platforms typically host a mobile operating system that can potentially be compromised and expose all secrets stored on the platform. Hence, to achieve the objective, the security-sensitive data used in the underlying protocols must be protected against untrusted code. Therefore, it defines the following security requirements on the underlying mobile platform: Secure storage: Security-sensitive data should not be accessible by untrusted software components while stored on the platform. Isolation: The system components operating on security- sensitive data must be trusted and isolated from the untrusted components. Further, it has to be ensured that the security sensitive operations, such as authentication and delegation, are triggered by the user rather than by malware. Moreover, advanced use cases, such as delegation and policy-based access control, rely on security-critical user inputs, such as passwords and user-defined access-control policies. Hence, for these use cases it needs an additional security requirement: Secure user interface: The user (the owner or the user) should be able to securely communicate with the trusted components.
5. Implementation
- An NFC reader/writer is connected to an Arduino which reads the details of the user from the NFC smartphone. The Arduino then checks if the d is an owner d or a guest d. If it is a guest d, it verifies it with the code provided to the GSM module. For this and the previous condition, if the NFC smart d code matches with the required data. It will send a signal to the servo motor to rotate to either locked or unlocked state. When the servo motor is in the locked state, a red LED will be on and the LCD screen will display that the door is locked, and when the servo motor is in the unlocked state the green LED will be on and the LCD screen will show that the door is unlocked. Android provides an adaptive app framework that allows you to provide unique resources for different device configurations. For example, you can create different XML layout files for different screen sizes and the system determines which layout to apply based on the current device's screen size. You can query the availability of device features at runtime. Owner sends a message to a person having NFC mobile, Message is received by the person. The message will have the key and person need to take his mobile to NFC reader which is on the door. A person needs to enter the key in the android application and tap on the NFC reader. Based on the key door can be opened or closed. Performance Evaluation: The performance of the implementation of the authentication protocol running between the smartphone and the door lock system is evaluated. For this purpose, we made the following measurements: the time required to start the authentication mechanism and to get the challenge from the door lock system after the NFC connection has been established, the time required by the phone to send the response to the door lock system. The time required by the door lock system to verify the phone’s response, and the time required for the complete authentication protocol.
6. Conclusions
- Unlike the conventional, closed and proprietary door lock systems that suffer from various vulnerabilities, this open approach allows the independent evaluation of the solution by the research community. The framework consists of a set of secure protocols and a security architecture for the mobile platform. The security of the underlying protocols using automated formal verification tools is analyzed. Moreover, the paper analyses the security of the architecture and discuss which objectives can be achieved using off-the shelf secure hardware for mobile platforms. The paper shows that available hardware allows remote issuing and remote revocation of electronic tokens, which cannot be achieved with classical (transponder-based) door lock system systems. Further, the project outline approaches to achieve more advanced security features, such as secure delegation and context-aware access control.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML