-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Internet of Things
2017; 6(2): 34-39
doi:10.5923/j.ijit.20170602.05

Advanced PCA for Enhanced Illumination in Face Recognition to Control Smart Door Lock System
Nishmitha R. Shetty, Prathviraj N.
Department of Computer Science and Engineering, St. Joseph Engineering College, Mangaluru, India
Correspondence to: Nishmitha R. Shetty, Department of Computer Science and Engineering, St. Joseph Engineering College, Mangaluru, India.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Face recognition is a commonly used biometric strategy in various field because of its accuracy and security. However, any feasible system will have its drawbacks. Some of the drawbacks of the face recognition system include, pose change, aging, light variation and many more. By focusing on these, illumination effect is taken into account and an advanced face recognition technique is developed. The technique that is used here is Principle Component Analysis (PCA) and Fast Fourier Transform (FFT-2). This solution is applied to a smart door lock system which allows the authorized people to access the door of the house by using face recognition technique.
Keywords: PCA, Face Recognition, Illumination Effect, Smart Door Lock
Cite this paper: Nishmitha R. Shetty, Prathviraj N., Advanced PCA for Enhanced Illumination in Face Recognition to Control Smart Door Lock System, International Journal of Internet of Things, Vol. 6 No. 2, 2017, pp. 34-39. doi: 10.5923/j.ijit.20170602.05.
Article Outline
1. Introduction
- Biometric strategies are very important in recognizing humans because it has the capacity to uniquely identify a person based on his body parts. It can be face, fingerprint, iris, retina, voice etc. Among these techniques, face recognition method is commonly used for identification of the human because, it has the ability to recognize a person without his participation in the recognition technique. This has a prominent role to play in security purposes. Face recognition is used to criminal identification and many more because of its feasible characteristic. Studying the essence of high dimension training data in a low dimension form has become very common in the recent years. The study of reducing the dimension of the training data is known to Dimensionality Reduction.One of the important concepts in Dimensionality reduction is the subspace method. There are 2 types of subspace methods. The first one is a Linear Subspace method. The other one is a Nonlinear Subspace method. The method that is ued in the proposed system is based on Linear subspace method. Principal component analysis (PCA) is one of the basic linear subspace method used for recognition of face. It is a mathematical procedure which makes use of orthogonal conversion for changing the data to a set of linearly uncorrelated data called as principal components.PCA is one of the common techniques which finds the application in the fields like face recognition, image compression and is commonly used for determining the patterns in data of high dimension. Figure 1 shows the image for PCA in 2D. This image is reduced to one dimensional subspace and the orthogonal diagonal element is obtained. This transformation is shown in the Figure 2.
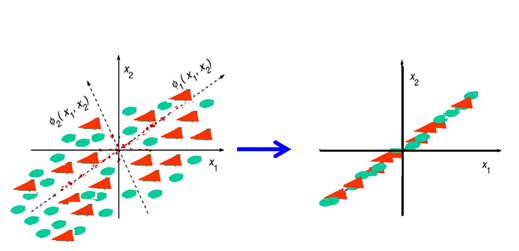 | Figure 1. PCA basis (2D); Figure 2. PCA reduced to 1D subspace |
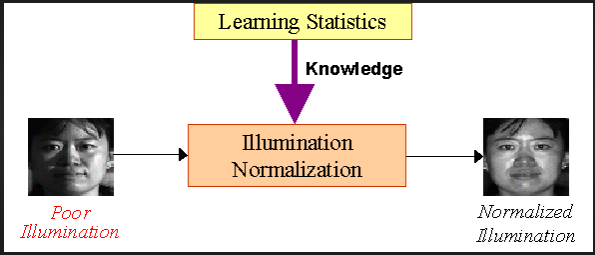 | Figure 3. Image Normalization using FFT2 |
2. Related Work
- Paul Viola, Michael J. Jones, n et all [1] says recognition of face is a method for face detection in an image. There are several methods for face detection and one of the commonly used method is viola jones. Once the detection of the face is done, the author explains the process for face recognition. This is accomplished using the Principal Component Analysis (PCA) algorithm. In PCA, the recognition is based on the Euclidean Distance and hence the face can be recognized.PCA is one of the common and basic method employed for face recognition. Even after commonly using this technique, there are several drawbacks associated with it J.Y. Yang, Kilic N, n et al [2, 3] speaks about the disadvantages associated with the traditional PCA. PCA extracts the feature of the face in an input image and converts it into a one dimensional matrix of vectors. Once the feature extraction process is done, then K-L transformation is applied to this one dimensional vector which yields in the image vector that is enormous and computationally complex. This will be a problem to compute the covariance matrix.Zhao and Yang [4] speaks about the illumination effect on PCA. They generated a formula for the covariance matric for the environment with the various light condition and then speculated an equation for approximate illumination. But, Wiskott et al. [5] mentioned that PCA cannot be used to identify the simple inference until this data is mentioned in the training data. This lead to presenting a technique called as Elastic bunch graph matching to overthrow the drawback of light variation on PCA.With the improvement in internet and technology, several door locks have been proposed. Several methods were presented to develop the door lock system for the physically disabled. The physically disabled people have limited capacity to access the electronic devices such as turning on/ off fan, light etc. because to control these devices, either the person has to move to the switch board or ask someone to do for them. However, with the help of internet, technologies can be developed to operate the electrical devices remotely. Kuang-Yow Lian, Sung-Jung Hsiao and Wen-Tsai Sunghave, n et al [6] mentioned ways to operate the devices through technologies such as hand writing recognition and blue tooth using smart phones. When the disabled person using mobile phone captures the handwriting in his phone, the control will be passed to the door lock system to validate the user. If the user’s hand writing is recognized, the door will be automatically locked or unlocked by the access system within the small specified range.Other door lock system was presented by Ushie et al. [7], GSM enabled phone is used to control the door lock system for enhancing the security of the house. This setup requires 2 mobile devices with GSM enabled in it. This operation can be done through a distant area in which the phone with GSM acts as a transmitter. The receiver part for the system is setup using another mobile device. This phone is connected to the door through tone multi frequency (DTMF), a controller. As an addition, SMS along with GSM/GPRS was used to access the door where the locking and unlocking mechanism for the door is done based on the SMS from a particular user. When the device receives a particular message, the control passes to the door lock system and the locking and unlocking mechanism takes place. Using this concept, a PIC system was proposed which provide security with the password. This system makes use of GSM for alerting on the intervention.Wi-Fi is another technique through which the door lock can be accessed. When the controller is operated by the Wi-Fi by the user who has smart phone results in a secure system. The user will have a mobile phone in which the application for managing the door lock will be installed. The door locks can also be accessed by the user through the application with the automated key. Chih-Chung Lu and Shau-Yin Tseng SLS, et al in [8] says people lose their keys easily than the phones. Therefore, the security concern for the door locks of the house can be improved. The authors also speak of encrypting the automated keys using various encryption algorithm for providing additional security. The standard AES encryption algorithm is the one used by the author to encrypt the automated key or the password.Authors Wan Mohd Nor Izudeen bin Wan Ahmad, n et all [9] present a technique for door lock using face recognition. The authors say that providing security to building, homes and other places have become very concerning in recent years. There are many methods of identification have been continuously used to provide security for the system. Some of the identical methods that are used include fingerprint recognition, face recognition, iris and retina identification etc. Among these, face recognition is proven to be the prominent one and it is least intrusive. Therefore, for this reason, the authors propose the door lock system using the face recognition. This approach works by attaching a web camera near the door. Whenever the authorized person arrive, the web camera captures the image and control is passed to the door lock system for controlling the door. The system works by creating the templates of the user’s face and storing the information in the database. This template is verified with the templates captured through the web camera. Access will be provided to the user only if there is a match between the two templates.Internet of things is a popular technique which is used in most of the system in the recent decade. It is commonly employed in home automation for automatically controlling the devices of the home such as fan, TV, light, door and many more. Nagender Kumar Suryadevara, and Subhas Chandra Mukhopadhyay, n et al [10] say that the IoT-based system is very secure and robust for communication. Using IoT, controlling the appliances is done using smartphone. The user with the smart phone will be able to control the appliances through the applications installed in the mobile. The user interface can be accessed using the login details like user name and the password or any other recognition technique.
3. Methodology
- In the proposed system, the drawbacks of Face recognition system was identified and focus was provided in overcoming illumination effect. When there is change in the light condition, the face recognition system fails to identify the user even though the user is a valid one. Therefore, the proposed system normalises the images before recognition so that the validation takes place accurately without failure. Also, the propose system compares the traditional PCA with the advanced PCA to verify the changes. This solution is applied to a real time problem of providing security to the house. The door lock will be attached to the controller which controls the access to the door if the face is recognized. Initially, the database will be containing the details and images of privileged users that are being updated by the owner of the house. When any of the members of the house wants to lock/unlock the door, he/she needs to use the front camera of their smartphone which captures an image. The captured image is then compared with the images stored in the database. If the face is recognized and matched, then the access to that person is granted. The implementation of the smart door lock system is as follows:
3.1. Implementation of the Algorithm for Face Recognition
- The technique for face recognition has the following steps. Initially the feature extraction of the face takes place using PCA. It is one of the common linear subspace methods which converts the 2 dimensional input data into 1 dimension, thus employing dimensionality reduction. Therefore, the second step of face recognition after extracting the features will be the feature reduction.The final step of face recognition is the validation or classification. This method is implemented using Euclidean distance. This method classifies the attributes of the face within the images which is stored in the database with the Test image. The advances PCA overcomes the problem of illumination by implementing FFT2 along with PCA. FFT2 is a normalizing technique which is usually implemented to process signals and data such as images. This normalizes the image to a certain level and helps the recognition algorithm to recognize the images accurately.The flowchart showing the implementation of the algorithm is shown in the Figure 4.
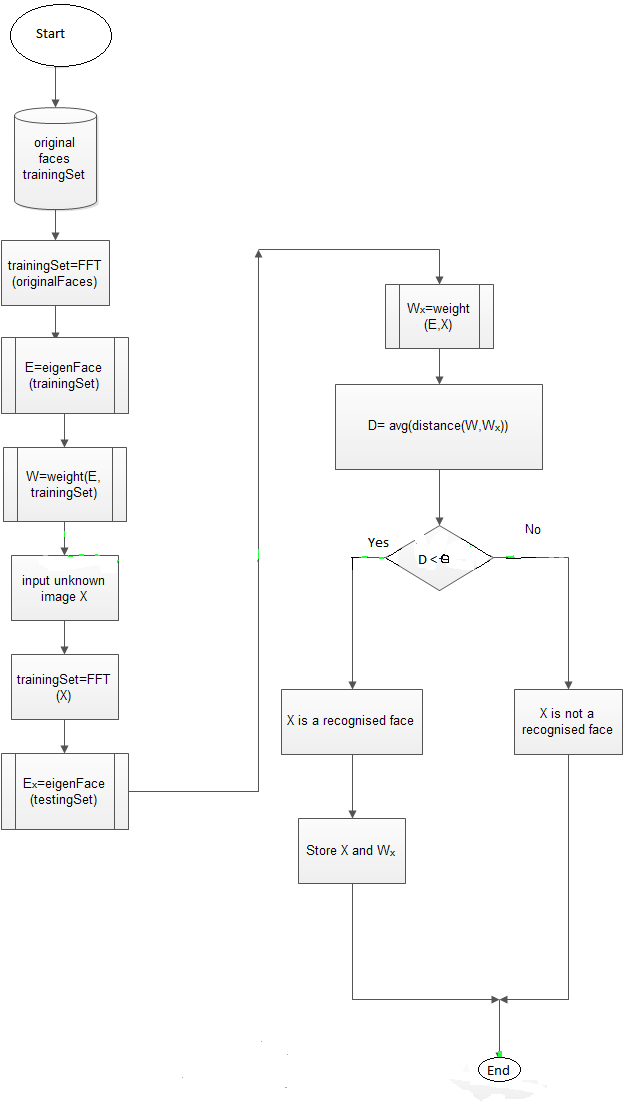 | Figure 4. Flowchart showing the implementation of PCA with FFT-2 |
3.2. User Interface
- The android application is installed in the user’s phone which acts as an interface between the user and the door. The android application allows the admin to add and manage the user profiles and receive notification about the user whenever he/ she enters or leaves the house along with the time. The application allows the user to capture the image and authorize notifications. This function of the android application is depicted in the Figure 5.
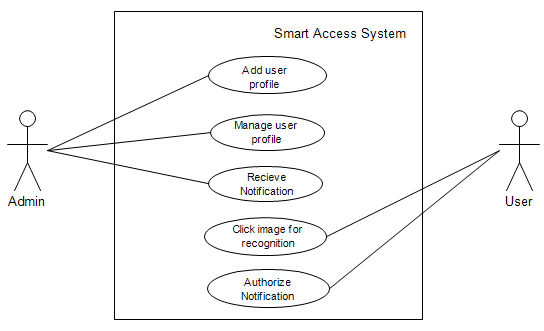 | Figure 5. Use Case Diagram |
 | Figure 6. User Interface of the Android Application |
3.3. Communication of the Client and the Server
- The image clicked by the user from the smartphone is sent to the server. Since the door can be remotely controlled by the user, the image has to be stored in the server. Once the recognition is done, the control is passed to the smart access system which is controlled by the microcontroller. The controller used in the proposed system is the Aurdino microcontroller. When the microcontroller receives the command from the local system, locking/ unlocking mechanism takes place. Figure 7 shows the Aurdino Microcontroller board to which the door lock will be attached.
 | Figure 7. Aurdino-Uno Microcontroller with LED |
4. Evaluation
- The smart access system with enhanced face recognition is compared with the traditional PCA. The system is tested with 2 users and changed light condition. Among the 2 users, the illumination enhanced PCA was able to recognize the users without any issue thus proving to be accurate. However, the traditional PCA failed to recognize the users. Based on this evaluation, a graph was plotted for Accuracy vs. Algorithm and it is shown in the Figure 8.
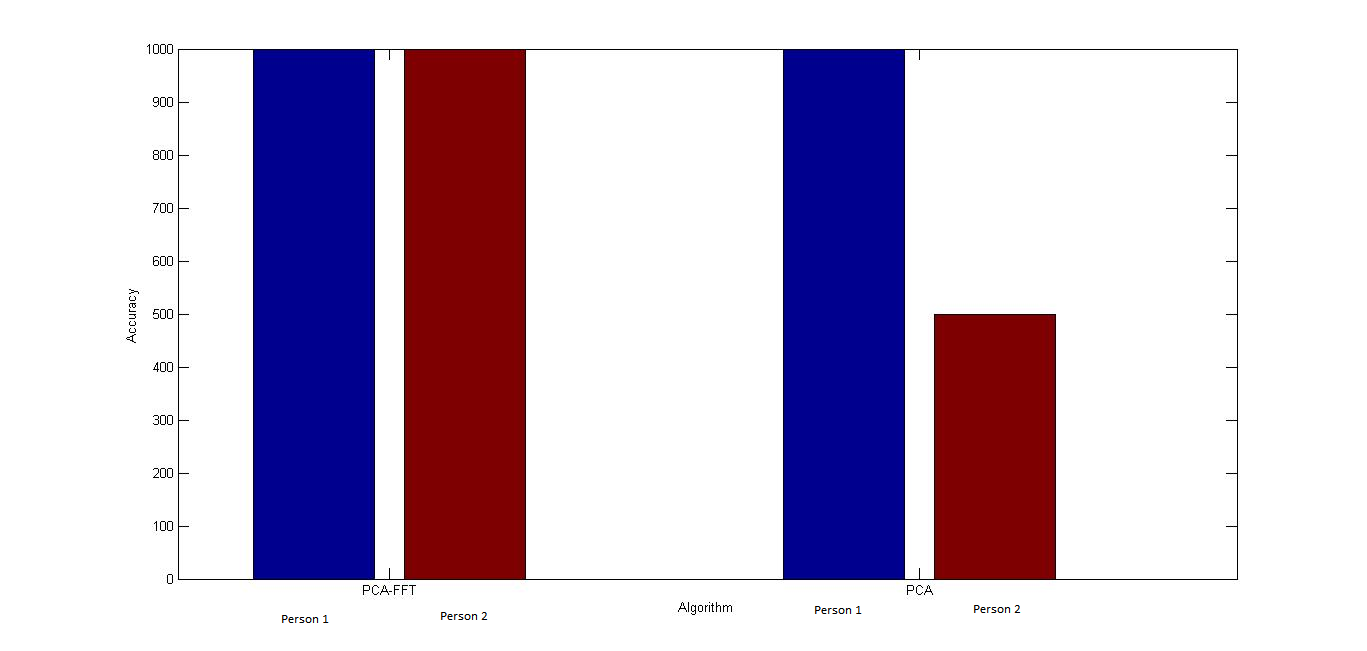 | Figure 8. Graph- Accuracy vs. Algorithm |
5. Conclusions
- There are several drawbacks in a face recognition system such as pose change, aging, light variation and many more. By considering the drawback of the illumination effect, an advanced PCA is proposed by combining the PCA algorithm with FFT2. The advanced algorithm recognizes the human under different light condition with a greater accuracy when compared to the traditional PCA. Since security is a main concern in our daily life, the proposed algorithm is applied to a smart access system. This provides security because of using human face for recognition. The solution is cost effective since the camera of smart phone is used to capture the human face instead of a separate web camera. The system can be generalised to offices, buildings, cars etc.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML