-
Paper Information
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Internet of Things
2012; 1(1): 9-15
doi:10.5923/j.ijit.20120101.02
Impact of Cyber Crimes on Social Networking Pattern of Girls
M. Neela Malar
Dept of Media Sciences, Anna University, Chennai
Correspondence to: M. Neela Malar, Dept of Media Sciences, Anna University, Chennai.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
AbatractSocial networking sites have become an integral part of the lives of most of the youth today. It has encouraged new ways to communicate and share information. The relative freedom afforded by social networking sites has caused concern regarding the potential of its misuse by individual patrons. This questions the safety and security of the users, especially girls who are more preyed upon particularly in relation to online sexual predators. These sorts of cyber crimes leave an everlasting scar in the minds of the users and change the way in which they communicate in the social networking sites and sometimes even force them to completely opt out of the social networking sites. This study deals with how girls are affected by cyber crimes in social networking sites and how those crimes impact their social networking pattern.
Keywords: Cyber Crimes, Social Networking, Users, Safety, Online Communities
Cite this paper: M. Neela Malar, Impact of Cyber Crimes on Social Networking Pattern of Girls, International Journal of Internet of Things, Vol. 1 No. 1, 2012, pp. 9-15. doi: 10.5923/j.ijit.20120101.02.
Article Outline
1. Introduction
- A social networking site focuses on building online communities of people who share interests and/or activities, or who are interested in exploring the interests and activities of others. Most social network services are web based and provide a variety of ways for users to interact, such as e-mail and instant messaging services.Social networking has encouraged new ways to communicate and share information. Social networking websites are being used regularly by millions of people. Although the features of social networking sites differ, they all allow users to provide information about themselves and offer some type of communication mechanism (forums, chat rooms, email, instant messenger) that enables them to connect with other users. On some sites, we can browse for people based on certain criteria, while other sites require that we be "introduced" to new people through a connection we share. Many of the sites have communities or subgroups that may be based on a particular interest.Cyber CrimesCyber or Electronic Crime is where a computer is the target of a crime or is the means adopted to commit a crime. Most of these crimes are not new. Criminals simply devise different ways to undertake standard criminal activities such as fraud, theft, blackmail, forgery, and embezzlement using the new medium, often involving the Internet (Seth, 2007).Cyber Crimes in IndiaIndia is one of the very few countries to enact IT Act 2000 to combat cyber crimes. The Act has termed certain offences as hacking, publishing of obscene materials in the net, tampering the data etc as punishable offences (Halder, 2006). However, there is lack of clarity and jurisdiction to keep pace with new forms of cyber crimes and lack of international treaties on cyber crimes to track the sources of crime originating in other countries. There is also lack of cyber army and cyber savvy policy makers including judges and finally there is lack of awareness among the net users.As per the National Crime Records Bureau statistics, 217 cases were registered under IT Act during the year 2007 as compared to 142 cases during the previous year (2006) thereby reporting an increase of 52.8% in 2007 over 2006. 22.3% cases (49 out of 217 cases) were reported from Maharastra followed by Karnataka (40), Kerala (38) and Andhra Pradesh and Rajasthan (16 each). 45.6% (99 cases) of the total 217 cases registered under IT Act 2000 were related to obscene publication / transmission in electronic form, normally known as cyber pornography. The age-wise profile of persons arrested in cyber crimes cases under IT Act, 2000 showed that 63.0% of the offenders were in the age group 18 – 30 year (97 out of 154) and 29.9% of the offenders were in the age group 30 – 45 years (46 out of 154). Crime-wise and age group wise profile of the offenders arrested under IT Act, 2000 revealed that 55.8% (86 out of 154) of the offenders were arrested under ‘Obscene publication / transmission in electronic form’ of which 70.9% (61 out of 86) were in the age-group 18 – 30 years. 50% (24 out of 48) of the total persons arrested for ‘Hacking with Computer System’ were in the age-group of 18 – 30 years.Most victims, especially women hesitate to report the crime for fear of personal and social backlash. According to one of the cyber law experts in India Na. Vijayashankar (popularly known as Naavi), it is difficult to measure the growth of Cyber crimes in India by any statistics, the reason being that a majority of cyber crimes go unreported. Cyber lawyers Pavan Duggal, advocate with the Supreme Court of India, points out to the result of a survey he conducted in early 2006 on the extent of under-reporting. For every 500 instances of cyber crimes that take place in India, only fifty are reported and out of that fifty, only one is registered as an FIR or criminal case. So, the ratio effectively is 1:500 and this, he points out, are conservative estimates. Giving an insight into the reasons for low reporting, Nandkumar Sarvade, Director, Cyber Security and Compliance at Nasscom, points out that very often, people are not aware whether an incident is a cyber crime; there is also lack of awareness on where to lodge a complaint or whether the police will be able to understand.
2. Review of Literature
- The distribution of malware on social networking sites first occurred in small amounts towards the end of 2007, but that trend appears to be on the rise.According to a report from MessageLabs Intelligence, which specializes in the analysis of messaging security issues and threats, a popular tactic in 2008 among cyber criminals involved the creation of fictitious accounts on social networking sites. These fake accounts were then used to post malicious links, which usually led to a phishing site, to legitimate users (www.messagelabs.com)Scammers would then make use of the phished personal information, such as usernames and passwords, to gain access to legitimate accounts. This access would be used to post blog comments on their pages of their friends, and send messages from the phished accounts to other contacts. These messages usually contained spam, including links to spam sites such as online pharmacies."Web 2.0 offers endless opportunities to scammers for distributing their malware--from creating bogus social networking accounts to spoofed videos--and in 2008, the threats targeting social networking environments became very real," said Richard Bowman, regional manager, MessageLabs South Asia.Another report from security expert Symantec, which owns MessageLabs, showed this trend does not look to be slowing down.The report, which analyzed Web threats for the month of January 2009, said social networking sites continue to be popular premises for cyber criminals seeking potential victims.According to the Symantec report, January saw the emergence of e-mail spam which closely mimicked legitimate notification e-mails of two major social networking sites. These spam messages, which invited users to join a group on the social networking site, contained a link to a virtual group created on the site by the spammers.
3. Social Networking Sites and Indian Youth
- The Indian youth have immediately taken to social networking sites, much in the same way they took up internet as a technology. Some of them have gone to the extent of getting addicted to the social networking sites. And some others have met up with serious psychological implications, due to their utmost concentration in the interactions through social networking sites. Above all, there definitely is an increase in the percentage of cyber crimes in after the invent of social networking sites. As has happened in so many other crimes, girls and young women happen to be the target of attack for cyber criminals too. The details of girls and women displayed in Orkut are (mis)used by the miscreants, raising serious security problems for the youing women aspiring to find friends through Orkut.Orkut – one of the most famous social networking sites in IndiaOrkut is a free-access social networking service owned and operated by Google. The service is designed to help users meet new friends and maintain existing relationships. The website is named after its creator, Google employee Orkut Büyükkökten.Although Orkut is less popular in the United States than competitors Facebook and MySpace, it is one of the most visited websites in India and Brazil. In fact, as of May 2009, 49.83% of Orkut's users are from Brazil, followed by India with 17.51% .
4. History
- Orkut was launched on January 22, 2004 by Google as an independent project of Orkut Büyükkökten, a Turkish software engineer. The community membership was originally by invitation only. At first year, had the largest user base. By word of mouth, various Brazilians began adopting and inviting more friends, in a viral driven by the blogosphere. Soon after, surpassed in number of users and Orkut started becoming heavily popular in . Americans then started leaving the service and switching to other similar sites such as MySpace and Friendster. This phenomenon was covered by the English blogosphere with some criticism towards Brazilians because they communicate among themselves using their native language Portuguese and not English.From that time, orkut growth was driven by Brazilian users, first being opened to everyone by registration and becoming one of the most popular websites in Brazil. The creator Orkut Büyükkökten visited Brazil in 2007, in an attempt to understand the success in that country. In 2007 Orkut began attracting large amount of Indians who were not intimidated by the number of Brazilians on the site. As for now, orkut also has a simplified site for mobile users.
5. Case Studies
- Case studies were conducted with girls belonging to Chennai. Chennai is one of the metros of and hence possess people belonging to various backgrounds and people all over could be spotted in Chennai and hence has been taken as the place for study. Girls belonging to the age group of 16-22 share their experiences in Orkut and tell how the cyber crimes have made them more cautious in net and also how it changed their social networking.Priya *22 years, final year, MA travel and tourismPriya had nearly 500 friends in her orkut profile, many of them she already knew and some of them she came to know through orkut, and one such guy who called himself Shiva sent her a friend request, he was one of the members in her cute community'(She owns the community). He sent her a request saying that he would like to be her good friend and hence she accepted his request. He gradually started scrapping her everyday, he started to ask her very personal questions-which she did not like and so she took him out of her friends’ list to avoid any further mishaps. In return he started posting bad and illicit comments about her in her own community, at first she did not notice it but later one of the members in her community, who is also her friend scrapped her about it. She was shocked to hear it first, she went to the community and deleted all his posts and banned him from the community.
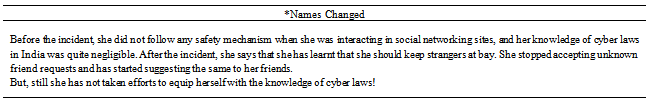 Koushika (20 years, final year, B.Com)She calls herself an Orkut fan, she logs into Orkut at least 3-4 times per day. Once she had to scrap all people in her friends’ list and invited them for some programme. To do the 'scrap all' thing, one has to join one of the many 'scrap all' communities out there and copy paste the code they give. Once it is done, it is possible to scrap all friends in the list in one go. One such of those communities asked her email id and password of her orkut account and she typed it down. The next time when she logged into the Orkut, to her shock she found out that her entire profile has been changed and illicit website URLs were posted in her profile page! For a minute she did not know what to do, later she changed her password and deleted all that was posted in her profile.She did not take any special action, she just handled it herself, but she made all her friends aware of it. She says that she knows cyber laws are existent but she feels that they are not stringent enough in India as in other countries.After the incident she learnt that she should not give her email id or password to anyone on the net, no matter how confidential they claim themselves to be and she started suggesting the same to her friends.Tina: (22 years, currently undergoing air hostess training)She has her orkut account for more than 4 years now and she used to post pictures in her profile. One day when she was browsing the net, she got a call from one of her friends saying that she had seen Tina’s picture in a man’s profile and asked her to view it immediately. She was stunned and immediately went to that profile. There in his album he had posted her picture stating that she is his girlfriend. She was shocked for a moment because she did not even know who this guy was. She did not know what to do and so she called one of her friends and asked her what could be done. Then, many of which specializes in the her friends scrapped him asking him to remove the picture immediately and cautioned that otherwise they would go to the police. That guy next day apologized to her through scrap and removed her picture.Since she did not want to make a big issue out of it, she preferred not going to the police. Instead, she took the aid of her friends to resolve the issue! She knows about cyber laws but her scant knowledge made her thik it was only for very severe cases like hacking, phishing etc.After the incident, her parents had insisted that she should not post her pictures and she also follows that safety mechanism in Orkut.Rashmi: 22 years, final year, mass communicationAbout a year ago, her orkut profile was hacked by somebody and that person started sending obscene scraps to all her friends in the list. She did not know about it first and later one of her friends told her that she was receiving obscene scraps from her profile. She was shocked and immediately after going home she tried logging into her profile and was unable to do so. She then realized that her profile has been hacked and she immediately created a new account and scrapped all her friends about the incident and asked them to report abuse. After many abuse reports were filed, the profile was removed by Orkut.She did not know about the cyber laws when the incident happened but now she says she is well aware of it. As a result, she stopped joining too many communities and stopped posting any personal information in her profile. She suggests the same to the girls who want to safeguard themselves on Orkut.Gowri: (19 years, 2nd year, BE, ECE) About 6 months ago when she was in college, her friend received a SMS in her mobile saying that she had received a scrap from Gayathri from orkut mobile services. At that time, she was sitting just beside that friend. Gayathri was shocked and did not know what to do. She went home and immediately checked her account and her whole profile was changed. It was alarming to her and she did not know what to do, so she deleted her account in Orkut. Later after a week she reopened a new account in Orkut.She did not take any steps; the only thing she did was informing all her friends and asking them to be careful! She came to know about cyber laws only very recently.She says that she really did not have any reason to get her account hacked because she did not post personal information or photos or videos but still got her account hacked. Hence she says the same can happen to anyone else. Now A days she is always on the alert and also suggests to others to be alert and monitor their profiles regularly! And she believes that a sound knowledge of cyber laws is needed to safeguard oneself on net!Roshini: (22 years, completed B. Sc., Visual Communi- cation )Her scrapbook was available to public until that particular incident happened. Some two guys in Orkut suddenly one day started scrapping her obscene messages. She did not even know who they are. More over their scraps were in Tamil and she does not know Tamil. She got it translated from one of her friends. It was scandalizing to hear them and she felt bad of herself. She immediately put her scrap book to private, and deleted those obscene scraps. She sought her friend's help to track down who those people were; the friend lodged a complaint with the cyber crime officials. The officials tracked down the people who were doing this. They got to know that these people were doing this as a hobby with many girls’ profile. They had them arrested and they were made to pay some amount of fine.After the incident, she locked her scrap book, photos, videos and testimonials only allowing her name to be displayed. She also learnt that her safety is in her hands and she needs to monitor and control it herself without allowing anybody to disturb her!
Koushika (20 years, final year, B.Com)She calls herself an Orkut fan, she logs into Orkut at least 3-4 times per day. Once she had to scrap all people in her friends’ list and invited them for some programme. To do the 'scrap all' thing, one has to join one of the many 'scrap all' communities out there and copy paste the code they give. Once it is done, it is possible to scrap all friends in the list in one go. One such of those communities asked her email id and password of her orkut account and she typed it down. The next time when she logged into the Orkut, to her shock she found out that her entire profile has been changed and illicit website URLs were posted in her profile page! For a minute she did not know what to do, later she changed her password and deleted all that was posted in her profile.She did not take any special action, she just handled it herself, but she made all her friends aware of it. She says that she knows cyber laws are existent but she feels that they are not stringent enough in India as in other countries.After the incident she learnt that she should not give her email id or password to anyone on the net, no matter how confidential they claim themselves to be and she started suggesting the same to her friends.Tina: (22 years, currently undergoing air hostess training)She has her orkut account for more than 4 years now and she used to post pictures in her profile. One day when she was browsing the net, she got a call from one of her friends saying that she had seen Tina’s picture in a man’s profile and asked her to view it immediately. She was stunned and immediately went to that profile. There in his album he had posted her picture stating that she is his girlfriend. She was shocked for a moment because she did not even know who this guy was. She did not know what to do and so she called one of her friends and asked her what could be done. Then, many of which specializes in the her friends scrapped him asking him to remove the picture immediately and cautioned that otherwise they would go to the police. That guy next day apologized to her through scrap and removed her picture.Since she did not want to make a big issue out of it, she preferred not going to the police. Instead, she took the aid of her friends to resolve the issue! She knows about cyber laws but her scant knowledge made her thik it was only for very severe cases like hacking, phishing etc.After the incident, her parents had insisted that she should not post her pictures and she also follows that safety mechanism in Orkut.Rashmi: 22 years, final year, mass communicationAbout a year ago, her orkut profile was hacked by somebody and that person started sending obscene scraps to all her friends in the list. She did not know about it first and later one of her friends told her that she was receiving obscene scraps from her profile. She was shocked and immediately after going home she tried logging into her profile and was unable to do so. She then realized that her profile has been hacked and she immediately created a new account and scrapped all her friends about the incident and asked them to report abuse. After many abuse reports were filed, the profile was removed by Orkut.She did not know about the cyber laws when the incident happened but now she says she is well aware of it. As a result, she stopped joining too many communities and stopped posting any personal information in her profile. She suggests the same to the girls who want to safeguard themselves on Orkut.Gowri: (19 years, 2nd year, BE, ECE) About 6 months ago when she was in college, her friend received a SMS in her mobile saying that she had received a scrap from Gayathri from orkut mobile services. At that time, she was sitting just beside that friend. Gayathri was shocked and did not know what to do. She went home and immediately checked her account and her whole profile was changed. It was alarming to her and she did not know what to do, so she deleted her account in Orkut. Later after a week she reopened a new account in Orkut.She did not take any steps; the only thing she did was informing all her friends and asking them to be careful! She came to know about cyber laws only very recently.She says that she really did not have any reason to get her account hacked because she did not post personal information or photos or videos but still got her account hacked. Hence she says the same can happen to anyone else. Now A days she is always on the alert and also suggests to others to be alert and monitor their profiles regularly! And she believes that a sound knowledge of cyber laws is needed to safeguard oneself on net!Roshini: (22 years, completed B. Sc., Visual Communi- cation )Her scrapbook was available to public until that particular incident happened. Some two guys in Orkut suddenly one day started scrapping her obscene messages. She did not even know who they are. More over their scraps were in Tamil and she does not know Tamil. She got it translated from one of her friends. It was scandalizing to hear them and she felt bad of herself. She immediately put her scrap book to private, and deleted those obscene scraps. She sought her friend's help to track down who those people were; the friend lodged a complaint with the cyber crime officials. The officials tracked down the people who were doing this. They got to know that these people were doing this as a hobby with many girls’ profile. They had them arrested and they were made to pay some amount of fine.After the incident, she locked her scrap book, photos, videos and testimonials only allowing her name to be displayed. She also learnt that her safety is in her hands and she needs to monitor and control it herself without allowing anybody to disturb her!6. Conclusions
- The case studies reveal that the cyber crimes those girls have encountered in their interaction through social networking websites have made them more cautious and alert on net. But it is really saddening to know that only their own bitter experiences in Orkut have made them alert. They have not learnt from others’ experiences or from whatever is portrayed in the media. Also, it is evident that Orkut has immediately come to their rescue whenever security problems were taken to their notice.There exist so many other girls who were more affected by cyber criminals and who have undergone severe mental agony. They are not even in a position to share their cyber problems with others! Hence, the need of the hour is proper propagation of awareness to all the youth who interact through social networking sites, especially to the girls who are the most affected in Indian context. And this could be achieved only through a perfect co-ordination between the parents, teachers (who essentially need to guide the teen-agers on safety-related issues) and law-enforcement agencies. Both the cyber laws and cyber crime cells in India need to be scrutinized and strengthened further. The knowledge of cyber crimes and the means to escape from them should be strongly imparted to girls. Successful implementation of all these would definitely enable safeguarding girls in social networking sites such as Orkut.
References
| [1] | Bagyavati (2009) ‘Social Engineering’ in Lech J.Janczewski and Andrew M.Colarik Cyber warefare and cyber terrorism pg: 182 |
| [2] | Bargavi and Sheeba (2009 November) ‘Safety Issues in Orkut for Girls’, Unpublished. |
| [3] | Bradley (2009) ‘Predators on Social Networks' http://netsecurity.about.com/od/newsandeditoria2/a/socialpredators.htm |
| [4] | Brenner (2009), ‘Social networking dangers exposed’ http://www.networkworld.com/news/2009/020909-slapped-in-the-facebook-social.html |
| [5] | Collier and Magid (2009), ‘Social networking dangers in perspective’, http://www.connectsafely.org/Commentaries-Staff/social-networking-dangers-in-perspective.html |
| [6] | Everett (2009), ‘Social networking - a risk to information security?’ http://www.infosecurity-magazine.com/view/2503/social-networking-a-risk-to-information-security/ |
| [7] | Gonsalves (2009), ‘Social Networkers Risk More Than Privacy’ http://www.informationweek.com/news/internet/social_network/showArticle.jhtml?articleID=219500360 |
| [8] | Joseph A L (2009, April 23) ‘Man arrested for posting obscene profile of ex-boss on Orkut’, The Indian express |
| [9] | Krishnan. S (2009, March 21) ‘Mumbai Police tie up with Orkut to nail offenders’. The Indian Express |
| [10] | Kumar A (2008, May 19) ‘Orkut used in credit card scam to buy airline tickets’, The Deccan Chronicle |
| [11] | Leyden (2006), ‘Social networkers risk losing their identities’ http://www.theregister.co.uk/2006/10/04/social_networking_security_survey/ |
| [12] | Muthalaly, (2007, June 12) Orkut users livid over demands for ban, The Hindu |
| [13] | Nappinai (2010), ‘Cyber Crime Law in India: Has Law Kept Pace with Emerging Trends? An Empirical Study in Journal of International Commercial Law and Technology Vol. 5, Issue 1 (2010) |
| [14] | San Diego News (2007), ‘Social Networking Sites Could Open Doors to Danger’ http://www.10news.com/news/ 14557347/detail.html |
| [15] | Satyanarayana (2009), ‘Security Risks of Social Networking websites’ http://www.brighthub.com/computing/enterprise-security/articles/9732.aspx |
| [16] | Tan N (2008), ‘Social networking: Danger - Warning for Teens’ |
| [17] | http://www.articlesbase.com/internet-articles/social-networking-danger-warning-for-teens-654816.html |
| [18] | The Hindu Business Line (2007, Dec 19) Google in India’s fast lane; Orkut fast rising search query |
| [19] | Willard N E (2007) ‘Social networking: are cyber teens in danger?’ http://www.ivillage.co.uk/parenting/teens/teencon/articles/0,,186632_712646,00.html |
| [20] | Zechariah, (2009, June 27), ‘Man held for defaming woman on Orkut’, The Indian Express |
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML