-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Information Science
p-ISSN: 2163-1921 e-ISSN: 2163-193X
2014; 4(1): 13-20
doi:10.5923/j.ijis.20140401.03
Assessment of E-Government Weak Points to Enhance Computer Network Security
Yas A. Alsultanny
College of Graduate Studies, Arabian Gulf University, Manama-Kingdom of Bahrain
Correspondence to: Yas A. Alsultanny, College of Graduate Studies, Arabian Gulf University, Manama-Kingdom of Bahrain.
| Email: |  |
Copyright © 2014 Scientific & Academic Publishing. All Rights Reserved.
This paper determines the e-government weak points to enhance the computer network security and to protect the computer network. A questionnaire of two parts was designed for assessment of e-government; the first part was for demographic information and the second part was consists of 30 statements, these statements distributed into five dimensions, the 5-points Likert scale was used to measure the degree of agreement. The data collected from 356 IT developers. The results conclude that there are some procedures from e-government’s managers to secure users’ data, there is an evaluation to the information technology used in the e-government network, there is an evaluation to the security level of e-government network, and there are monitoring and improvement to the vulnerability issues in the e-government networks. More attention recommended to overcoming of any possible weak points within the network.
Keywords: Weak Point, Vulnerabilities, Computer Network, E-Government Security, Information Technology
Cite this paper: Yas A. Alsultanny, Assessment of E-Government Weak Points to Enhance Computer Network Security, International Journal of Information Science, Vol. 4 No. 1, 2014, pp. 13-20. doi: 10.5923/j.ijis.20140401.03.
Article Outline
1. Introduction
- E-government has concentrate on the security factor in order to keep the databases of users’ from any unauthorized people or users who misuse these personal information or databases. Because of the importance of the security in the e-government, there are several solutions to avoid any vulnerable issues. That can lead the unauthorized person to access the personal information of the users or the personal information of the government itself (Moen et al., 2007; Karokola and Yngström (2009). However, Saha et al. (2010) defined vulnerability issues as the capability of the system to change the impacts of the events. This means that vulnerability relates to the ability of the system to expose the risks and then change their consequences. Policy makers in the e-governments pay a lot of attention on providing the required security to their files and folders in order to avoid any vulnerability or threats on the data or information in the e-government networks, which then plays a major role in the trust that are provided from the citizens towards e-governmental applications (Syamsuddin and Hwang, 2010).The significance of security in the e-governments applications relates to the vision of e-governments to provide citizens with applications of high level of security. Therefore, e-governments have provided several techniques to keep security at a highest level (Elssied et al., 2011). Personal information accessing in the e-governmental applications sometimes requires the fingerprint, iris, or voice recognition. The humans can form some vulnerable issues to the e-governmental system either intentionally or by mistakes. Therefore, e-governments mangers must train the computer network security employees before recruiting them in real jobs (United Nations Department of Economics and Social Affairs, 2007; Zhao et al., 2008). E-governmental protected clients’ personal information, updating the system regularly to limit the malicious entity, like hackers or attackers, viruses, and unauthorized employees from reaching the sensitive data (Upadhyaya et al, 2012).Security assessment of e-government computer network is the most important object that all the IT employees responsible for developing e-government applications with the highest level of security. The security must be the first priority for each application before publishing it to users’, because the security will increase the users’ trust in using applications and reducing the fraud, especially in the applications have money transfer and have the users’ information. From these two points the importance of this paper was raised to assess security level from the perspective view of the IT developers who responsible for developing Kuwaiti e-government computer network and its applications to enhance computer network security. The structure of the paper is as follows, we will try to link the objective with the hypotheses that was designed to answer the questions of this paper, and then presenting the results analysis from IT developers’ perspective followed by conclusion.
2. Motivations for This Study
- The development in ICT tools has identified the concept of e-government as the government applications that are used for different transactions through Internet (Wong et al., 2011). Alfawaz et al (2008) argued that e-government concentrated on the security factor in order to keep the databases of users’ from any unauthorized people or users who misuse these personal information or databases. Vulnerability and weak points of e-government networks are very important. Thus, it is certainly worthwhile to evaluating the vulnerability and weak points of e-government from the perspective of view of IT developers.
3. Research Objective
- The major objectives of this research are concerned with answering the following questions:• Is there measurement to the web effectiveness? • Is there measurement to the services security?• Is there evaluation to the information technology use?• Is there evaluating to the information technology security?• Is there improvement for the vulnerability issue?• Is there effect of demographic information on e-government weak points?
4. Literature of E-Government Security
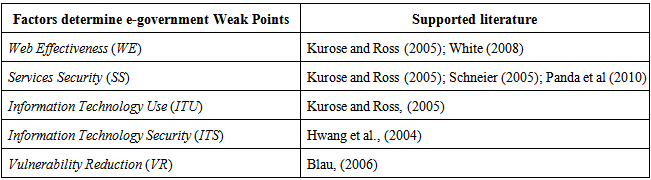
- E-governments are established for the benefits of citizens; they can access their needed governmental services anytime and anywhere and perform their transactions easily and rapidly. But these services facing the problems of security issue in the applications of e-governments, Therefore, E-governments must provide a security system in order to avoid any unauthorized people from accessing the E-governments applications (Elssied et al, 2011). E-governments take different procedures to avoid various vulnerabilities; For example, e-governments provide user name and password in order to log in a certain file or folder. Also, E-governments provide antivirus programs to protect the computers while downloading files or folders as well as they provide encryption and decryption tools to protect the computers from any vulnerability issues (United Nations Department of Economics and Social Affairs, 2007). Security issues are considered as the main framework to ensure the successfulness of any e-governmental; if there is any security vulnerability, the whole system will be at risk. So, these e-governments are seeking more and more to protect and isolate their systems from any sudden danger. E-government must take into consideration the personal information have to be kept secure and private (Schwester, 2009; Upadhyaya et al. 2012). E-government in Kuwait has offered for their citizens flexible applications where they have the ability to do their different transactions 24 hours/365 days (Kostopoulos, 2003). These applications needs security to avoid any problem faces the users (Boujarwah, 2006). AL-Shehry et al (2006), indicated in their study that the security is an important factor in the e-government applications, because it can provide the required trust to users, and this will increasing the effectiveness and efficiency of interacting the users with e-government's developers. Colesca (2009), argued that major problem facing the Kuwaiti e-government is the security problem which allows unauthorized people to access personal data. Syamsuddin and Hwang (2010), advised to use different programs and software to solve technical problems facing e-government web applications users. Both of Scarfone and Mell (2010), indicating that the vulnerability issues can be created from the software designer himself, which means that the software designer can cheat the trust of the managers of e-governments by announcing these codes to unauthorized people.Muthanna (2009), in his study for Bahrain e-government demonstrated that the Bahrain government data network managers should gain a full understanding of any potential risks by noticing the output of information security risk management process; where this process can assess and scan the external and internal environment of Bahrain government data network. AL-Qaisoum (2009) in his study for measuring Saudi Arabia e-government readiness, he found that the main obstacles of the e-government are the network security, legal, and IT skills in the field of computer network security.Therefore the importance of this paper rise from the necessary of assessing the weak points of the computer network from the perspective of the IT developers, the questionnaire and the hypotheses of this paper were build with the help of the researches such as; Kurose and Ross (2005), Schneier (2005), Panda et al (2010).
5. Research Significance
- E-government is one of very important applications implemented on the Internet. The users in all countries gain the usefulness of the e-government application, but on the other side the important point appear here, is how to safe users data from any attack, therefore the significant of this paper comes from the following;• Provide an appropriate level of security to the personal information and data to the users by avoiding the vulnerability issues that might be happened through accessing unauthorized people to the databases.• Avoid vulnerability issues that the systems of e-government are clear from any intrusion so that users can do their transactions through e-governmental applications without having any problems as well as having no fear resulted from the feeling of giving the unauthorized people an access to the system which let them steal users’ personal information and data.• Increase the users’ engagements with the e-governmental applications because, it provides enough security level to keep the users’ data from any misuse.
6. Research Model and Methodology (Instrument Design and Measurements)
- Table (1) shows the supported literature used in designing the factors of the research model. The research model that guides this study is depicted in Figure 1; the model examines the effect of Web Effectiveness (WE), Services Security (SS), Information Technology Use (ITU), Information Technology Security (ITS), Vulnerability Reduction (VR) on e-government weak points.
|
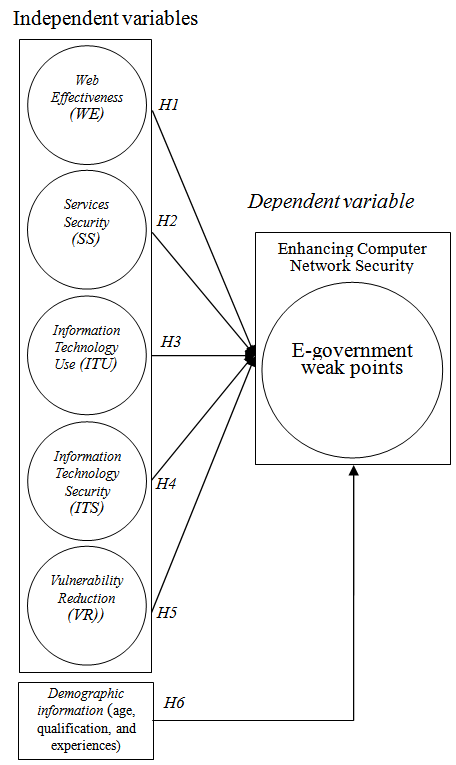 | Figure 1. The research model |
7. Data Analysis
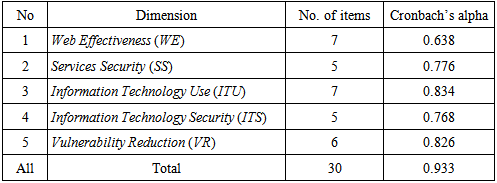
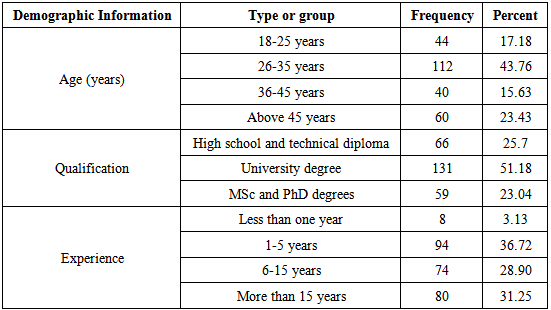
- Descriptive StatisticsThe designed questionnaire was divided into five dimensions of 30 statements. The number of respondents is 356 from the total population 580 IT developer employees.The reliability test was carried out using Cronbach’s alpha, which measured the internal consistency of a construct. The recommended minimum acceptable limit of reliability (alpha) for this measure is 0.60 (Hair et al., 1998). Table (2) shows the Cronbach’s alpha values to the dimension of the questionnaire.
|
|
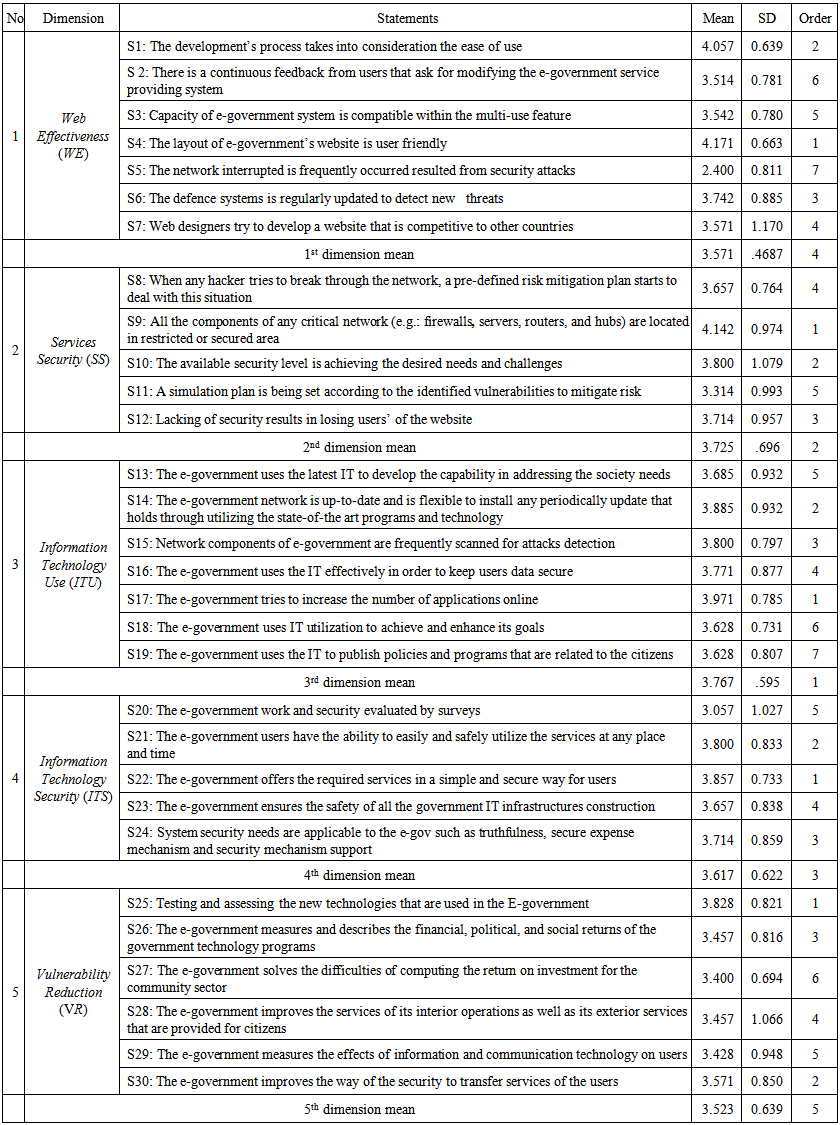 | Table 4. Mean and standard deviation of the questionnaire statements |
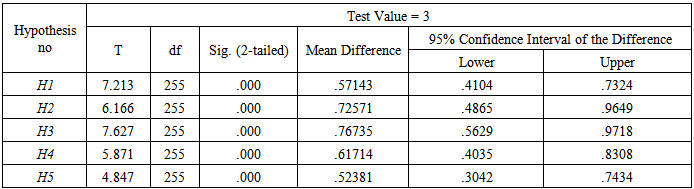 | Table 5. One sample T-test of hypotheses |
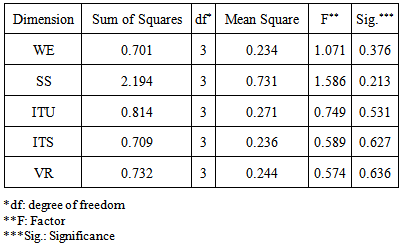 | Table 6. One way ANOVA test for age effect |
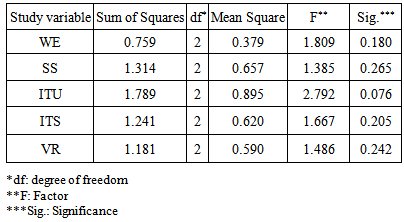 | Table 7. One way ANOVA test for qualification effect |
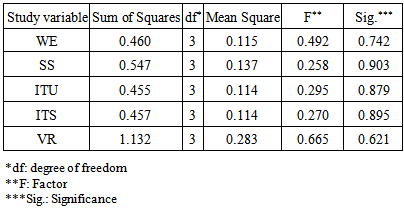 | Table 8. One way ANOVA test for experiences effect |
8. Discussion and Conclusions
- E-governments realized the concept and significance of security and weak points in their applications. Thus, the security and weak points issue in e-governments are controlling the trust of the users, who do their different transactions through Internet. This paper aims to assess the computer network system weak points at the Kuwaiti e-government computer network system. For this aim a questionnaire for IT- developers’ was designed. The results showed the IT-developers agree on the significant effect of Web Effectiveness (WE), Services Security (SS), Information Technology Use (ITU), Information Technology Security (ITS), and Vulnerability Reduction (VR) on e-government weak points to enhance computer network security. Their demographic information; age, qualification and experience have no significant effect on their responds for the five dimensions of the questionnaire, and this indicate the importance of these factors on assessing weak points regardless to their background. This concludes that these factors are important and influence the performance of e-government network.The main contribution of this study is the security must be the first priority of any application or service introduced to users’. In order to eliminate the weak points that may occur in the network, and it will be a risk in using any application, therefore IT developers in any e-government must be continuously monitored the number of users’ and compare these numbers statistically with the previous number of users’ because the number of users’ for each application or service reflect the degree of users satisfaction, which is depended on the users’ confidence for the computer network security.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML