-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
International Journal of Finance and Accounting
p-ISSN: 2168-4812 e-ISSN: 2168-4820
2013; 2(1): 19-23
doi:10.5923/j.ijfa.20130201.03
Implementing the Use of Auditing Skills to Identify and Avert Situations which could Lead to Frauds being Perpetrated
Jones Orumwense
Senior Lecturer, Kampala International University, Uganda
Correspondence to: Jones Orumwense , Senior Lecturer, Kampala International University, Uganda.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
The study dwelt, on the effectiveness of forensic auditing in identifying and averting situations which could lead to frauds being perpetrated. The study sought find out to what level the forensic auditors are able to fulfill this mandate and investigate problems that hinder forensic auditors to make progress in their operations in developing countries with special reference with Nigeria. It also established the role of forensic auditing in banking operations. The internationally recognized audit procedures used in detecting and investigating these frauds were discussed. In conclusion, forensic auditors must be capacitated materially and technically to improve their effectiveness. In addition, the forensic auditors should create a constituted body that serves their - interests and regulate the activities just like any other profession.
Keywords: Use of Auditing skills, Identify, Advertising Frauds
Cite this paper: Jones Orumwense , Implementing the Use of Auditing Skills to Identify and Avert Situations which could Lead to Frauds being Perpetrated, International Journal of Finance and Accounting, Vol. 2 No. 1, 2013, pp. 19-23. doi: 10.5923/j.ijfa.20130201.03.
Article Outline
1. Introduction
- Financial statements compiled represent the following:• Actual receipts and payments(cash basis)• Recognition of certain hems of expenditure or income on accrual basis, in accordance with the applicable statements. For example, recognition of sale may on appropriation of goods for delivery or on actual delivery, both thin accordance with standards but as suited to the needs of the entity• Estimates of provisions and bad! Irrecoverable debts, or write back of creditors and provisions no longer required, etc.• Provisions for various intangible items, like foreign currency fluctuations, retirement benefits based on actuarial valuation or any other basis• Adjustments on account of prior period transactions.The financial statements cannot be said to present exactly the position of financial affairs. The true and fair presentation is an attribute to the methods adopted in compiling such financial statements. However, the basic tenets of the principles of double entry accounting are to be adhered to in maintenance of books of accounts.Accounting standards are only guiding tools in preparation of financial statements. Accounting standards are epitome of various conventions, concepts, principles andpractices to be followed in presentation of financial affairs to reflect a true and fair view. Most of the accounting standards are mandatory. These may broadly be classified into:• Accounting specific: for example inventory valuation, revenue recognition, provision for employees retirement benefits, valuation of investments etc• Reporting and disclosure specific: for example related party transactions, contingents and events occurring after balance sheet date, amalgamation and mergers (mainly basis of valuation) or the treatment of assets acquired out of grant in aid, etc.
1.1. Financial Reporting and Frauds
- Accounts may be falsified to conceal:• Absolute theft of money or money’s value(mainly relating to employees frauds)• True results of operations, or financial position of the entity with a view to prevent timely detection of corporate frauds• Fraud refers to an intentional act by one or more individuals among management, those charged with governance, employees, or third parties, involving the use of deception to obtain an unjust or illegal advantage. Fraudulent financial reporting involves intentional misstatements, in any one or more ways as stated below:• Deception such as manipulation, falsification or alteration of accounting records or supporting documents• Misrepresentation in, or intentional omission from the financial statements, significant events, transactions or other information• Intentional, misapplication of accounting principles relating to measurement, recognition, classification, presentation, or disclosure of material transactions
1.2. Motives For Fraudulent Financial Reporting By Management
- 1). Management is under pressure from sources outside or inside the entity, to achieve (perhaps unrealistic) target, where consequences of failure are significant2). To increase the entity’s stock price or earnings trend3). To keep the results attuned to knowingly unrealistic! non achievable forecasts/commitment made to creditors and lenders4). Tax motivated reasons5). To raise capital either by thither issue of shares at a premium and! or through borrowingsCorporate frauds are results of manipulation of accounts and accounting jugglery designed to deceive others for wrongthl gains
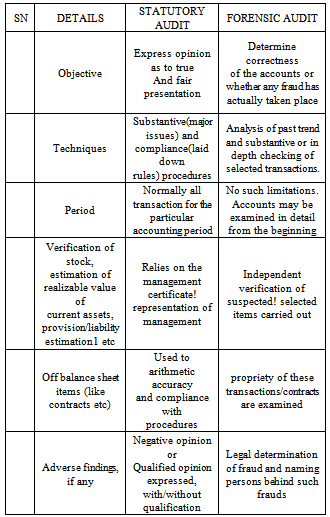
2. Distinction between Statutory Audit and Forensic Audit
|
2.1. Conceptual Framework
- Forensic auditing is an activity that consists of gathering, verit3Jing, processing, analyzing of, and reporting on data in order to obtain facts and evidence in a predefined context in the area of legal Financial disputes and/or irregularities and giving preventive advice (Institute of Forensic Auditors, Belgium, 2004). Albrecht and Albrecht[12] described forensic investigations as the utilization of information in such a manner that the outome will have, application to the court of law. Specialized investigative skills in carrying out an enquiry conducted. From a legal point of view in line with Association of Fraud Examiners (1999), identifies fraud as the fraudulent conversion and obtaining of money or property by false pretences.Attempts to categorize fraud have been a daunting task to fraud specialists. One school of thought differentiates fraud according to occupation and non-occupation, while another school serialized it on the basis of whether it is public or private sector fraud. However, another school accorded fraud in terms of industry in which the fraud was committed, such as bank fraud and insurance fraud. But I found it plausible to categorize fraud in terms of whether it is corporate or non corporate, such as management fraud, insider dealing, investment fraud, and other related frauds. This interactive seminar focused on the Government and the banking services industry.With the phenomenal increase in Government’sexpenditure and revenue budget, the operations of Government have become much more complicated and cumbersome. There has been a paradigm shift in the state’s focus so far as governance and administration issues are concerned. The priority of Government is to uplift the overall socio- economic conditions of the citizens of the country. Though, this has been the priority since independence, but this has become more significant in the recent times as the Government’s exchequer (treasury in Nigeria) has sufficient resources to support these developmental initiatives. In this scenario it has become an absolute necessity for the Government to ensure that the actual benefit reaches to the intended beneficiaries and there are no leakages arid malpractices in the channel and so there is an urgent need to utilize these resources properly and to ensure that the benefits reaches to the poor and needy citizens of the country. In this context, the role of auditing in general and forensic auditing in particular assumes significance.For any Government, the biggest challenge is to prevent leakages and fraudulent activities present in the system. Many of the schemes in the public sector have not been able to deliver the intended results as they were not having proper implementation strategies. Placing the internal controls in place, having proper internal and forensic auditing strategies should form a significant part of the scheme implementation guidelines. There is a need for an expert group who would carefully plan these strategies, right at the scheme design level and put them in place in operational manual as well, so that they become integrated in the scheme itself.The objective of forensic audit is to find whether or not a fraud has taken place. Forensic auditor shall have to examine voluminous records and witnesses, if permitted by law, proper documentation is vital in substantiating the findings. The auditors need to have a fair knowledge of entity’s business and legal environment. They should also have awareness of computer assisted audit procedure for carrying out proper forensic audit. The forensic audit also requires an innovative approach from the auditors so that they arc able to outsmart the fraudster.Internal control framework and internal audit is carried out and reported within d framework which assumes that the top executives of the ministry are responsive to the need for good governance and accountability and would therefore act upon the audit findings. But, at some places there is even a clear will at the top to misuse the Government resources and give mala Me orders and directions to the subordinates. In Nigeria, there are agencies which are responsible for the investigating fraud and corruption. To make their effectiveness better, there is a need to integrate forensic auditing with the role of these investigating agencies. The forensic auditing can provide preliminary data upon which these investigating agencies can base their investigations. The formal wedding between forensic auditing and investigating agencies can go a long way in preventing frauds and ensuring that the Government’s resources are utilized properly.Bank frauds have developed in nature and complexity from the traditional system of simple cheque fraud, where fraudster would just forge his name on a simple cheque by using an ordinary pen to more sophisticated techniques, such as the advance fee fraud which utilizes the Internet and computer highways[9]. Skalah et al[10] managed to identify two species of fraud, those that ate committed by insiders and those committed by other fraud felons outside. Among the bank frauds emanating from within are: rogue traders, fraudulent loans, wire fraud, forged documents, theft of identity, and demand draft fraud. On the other hand, fraud committed by outsiders include: forgery and altered cheques, stolen cheques, cheque kitting, payment card fraud, booster cheque duplication and skimming of card information prime bank fraud, fictitious bank “inspector” fraudulent loans applications, impersonation and theft of identity fraud and advance fee fraud, money laundering, arid missing in the post’ fraud. According to Skalah et al, a rogue trader is a highly placed trader to invest sizeable funds on behalf of the bank This trader makes risky investments using the bank’s money, which when an investment goes bad, the trader engages in further market speculation in the hope of a quick profit which would hide or cover losses. Currency dealers usually commit some of the largest bank frauds, fraudulent loans are one way to remove money from a bank with practice bankers more than willing to encourage if they know that money will be repaid with interest. The borrower may even be nonexistent and the loan merely an artificial thing to conceal a theft of large sums bf money from the bank[13]. Wire fraud makes use of wire transfer network, such as SWIFT, Real Time Gross Settlement (RTGS), and interbank find transfer systems. While several banks have put some checks and balances in place, there is a real risk that insiders may attempt to use fraudulently or forged documents, which claim to request a depositor’s money, wired to another bank, often an offshore account in some distant foreign country [10].A discounting fraud is a confidence trick, where fraudsters use a company at their disposal to gain confidence with the bank, by appearing to be a genuine, profitab[e customer (Levi, 2001). After sometime, the bank is happy with the company and the company may now request that the bank settle its balance with the company before billing the customer. Levi argues that only when the outstanding balance between the bank and the company is sufficiently large, the company takes the payment from the bank, and the company and its customer disappear, leaving no one to pay the bill issued by the bank.Accounting fraud involves hiding serious financial problems, using fraudulent bookkeeping to overstate income, inflate the worth of the company assets or state a profit when the company is operating at a loss. This could be used to conceal theft in a company, as in the United States, the collapse of Enron and Tyco are cases in point. Application, or skimming of information, is a fraud that takes a number of form, ranging from dishonest merchant copying client card number for latter use to the tampered credit or debit card readers to copy the magnetic storage from a payment card while a hidden camera captures the number on the face of the card. The fraudulent equipment would then be removed and the data used to produce duplicate cards that could be used to make Automated Teller Machine withdrawal from tr’ victim’s account[13].Cheque kitting involves the opening of accounts at two or more institutions and using float time of available hinds to create fraudulent balances. Some perpetrators have swapped cheques between various banks on a daily basis, using each to cover the shortfall for the previous cheque. Fraudulent RTGS involves criminals who create counterfeit transfers purporting to be from a particular bank. They conduct business transactions with unsuspecting victims whom they engage as if genuine customers and pay the goods and services by use of these fraudulent RTGS. Trickers can use ATM taking advantage of victims who are not able to operate an ATM.Advance fee fraud involves an upfront payment by a victim to the fraudster, to allow the victims to take part in a much larger financial transaction, which he believes will bring him either profit or result in credit advanced to him[14]. This fraud, because of its prevalence in West Africa, is also known as 4l9scam, being a derivation from section 419 of the Nigerian criminal Code (chapter 777 of 1990) which prohibits Advance Fee Fraud; Interpol, in the same vein, calls it “west Africa Fraud”
3. Detection Techniques
- Forensic auditing should focus on significant transactions both as reflected in financial statements and off balance sheet items. The techniques mainly are critical point auditing and propriety auditing.
3.1. Critical Point Auditing
- Critical point auditing techniques aims at filtering out the symptoms of fraud from regular and normal transactions in which they are mixed or concealed. For this purpose, financial statements, books, records, etc are analyzed mainly to find out:1). Trend analysis by tabulating significant financial transactions2). Unusual debits/credits in accounts normally closing to credit/debit balances respectively3). Discrepancies in receivable or payablebalances/inventory as evidenced from the non reconciliation between financial records and corresponding subsidiary records (like physical verification statement, priced stores ledgers, personal ledgers, etc).4). Accumulation of debit balances in loosely controlled accounts (like deferred revenue expenditure accounts, mandatory spares accountcapitalized as addition to respective machinery items, etc)5). False credits to boost sales with corresponding debits to non-existent(dummy) personal accounts6). Cross debits and credits and inter account transfers7). Weaknesses/inadequacies in internal control/check systems, like delayed/non preparation of bank reconciliation statements, etc.
3.2. Propriety Audit
- Propriety audit is conducted by supreme audit institutions (SA]) to report on whether Government accounts, i.e., all expenditures sanctioned and incurred are need based and all revenues due to Government have been realized in time and credited to the Government account. In conducting the propriety audit, value for money audit technique aims at lending assurance that economy, efficiency and efficacy have been achieved in the transactions for which expenditure has been incurred or revenue collected is usually applied. The same analogy, with modifications to the principles of propriety of public finance, applies in forensic audit to establish fraudulent intentions if any, on the part the management. Financial frauds are results of wasteful, unwarranted and unfruitful expenditure or diversion of finds by the investigated entity to another entity.
4. Averting Frauds
4.1. Tests of Reasonableness
- • Check weaknesses in internal controls• Identify questionable transactions- indicating wide fluctuations from the normal ones and not, in general, related to main objectives• Review questionable transaction documents for peculiarities, like improper account, classifications, pricing, invoicing, or claims etc.
4.2. Historical Comparisons
- • Develop a profile of the entity under investigation, its personnel and beneficiaries, using available information• identify questionable accounts, account balances, and relationships between accounts, for finding out variances from current expectations and past relationships• Gather and preserve evidence corroborating asset tosses, fraudulent transactions, and financial misstatements.
5. Conclusions
- In Conclusion, forensic auditing is a comprehensive undertaking. Once it is completed, the organization’s key stakeholders should capitalize on the work by implementing controls to reduce the risk associated with the event identified as having material and significant ratings and being most likely to occur, The strength of current controls in place and whether they are preventive controls or detective controls are taken into consideration. Can the current controls be overridden or circumvented? Future audit programs should include test on the design and implementation of these controls. If an event has been identified as inconsequential, forensic auditors may decide to take no action: even so, at least it would be documented, and management would be aware of its existence. The forensic risk assessment is not the end of the process. Circumstances change constantly and some changes may trigger the need to revise the assessment. A fraud risk assessment process should be on going, dynamic and reflect the organization’s current business conditions.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML