-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Electrical and Electronic Engineering
p-ISSN: 2162-9455 e-ISSN: 2162-8459
2015; 5(1): 6-12
doi:10.5923/j.eee.20150501.02
Intruder Recognition System
Nagaraj Shet Sdmit Ujire1, Shreesha C. Mit Manipal2, Abdullah Gubbi Pace Ujire3
1Shree Dharmasthala Manjunatheshwara Institute of Technology
2Manipal Institute of Technology
3P.A.College of Engineering
Correspondence to: Nagaraj Shet Sdmit Ujire, Shree Dharmasthala Manjunatheshwara Institute of Technology.
| Email: |  |
Copyright © 2015 Scientific & Academic Publishing. All Rights Reserved.
In present days security of office and home has become an issue of utmost importance. A lot of methods can be used to prevent the intrusion to any place. A full-fledged mechanism known as the Intruder Recognition System is used to detect, capture and send the facial part of the intruder to the authorized owner for taking action against the intrusion. PIR sensors are used to sense the presence of any person in the vicinity of the concerned area. The PIR signals generated are sent to the ARDUINO UNO which is interfaced with the computer. The webcam is used for capturing the image. The fuzzy logic and Local Binary Pattern (LBP) is used to extract face features. The system is programmed to detect, capture and send the image. Finally the intrusion is acknowledged to the concerned authority via e-mail. Note to practitioners-Many Home automation products in market are functionally dependent and require many devices to do even a single job. To automate all the functionalities of home, lot of cost is involved. But for users of such security system, there is no feeling of immediate benefits. Recognition of intruder is foremost function which is incomplete without finding friendly faces in the video image. In the home automation and security domain integration of all functionalities will give a commercially viable product.
Keywords: Security system, Intruder Recognition system, Local Binary Pattern, Fuzzy Logic, Information Set
Cite this paper: Nagaraj Shet Sdmit Ujire, Shreesha C. Mit Manipal, Abdullah Gubbi Pace Ujire, Intruder Recognition System, Electrical and Electronic Engineering, Vol. 5 No. 1, 2015, pp. 6-12. doi: 10.5923/j.eee.20150501.02.
Article Outline
1. Introduction
- The People at home and its contents are highly susceptible to encounter problem or theft, whether it’s equipment, ornaments, or pets. With wide range of approved Home Security Alarm Systems, people can protect their home and it will be notified instantly if there is an intruder. Human deaths and injuries, although less common than damage to valuables are the most severe manifestations of human conflict. The human conflict was long considered to be responsible for more deaths than any other thing in Indian rural region. Large cases of burglary are involved in human deaths every year. Deaths occur while people are protecting their belongings against raiding theives usually at night when people are sleeping. Any Intruder recognition system [1] is incomplete without Face Recognition. Here in this paper we are aiming to keep the home secured from the unexpected attack by intruders. By using the image processing technique the system will recognize whether the person is an intruder or authorized. The face recognition technology has grown for almost four decades. The first automatic face recognition was done in the year 1970. Later many algorithms were presented and the results are continuosly improving. An attempt is made in this work to extract the face features, that effectively represent face. The face features are higly discramble when it is inter class and these features should show less variance within the class. For this reason we have chosen the Local Binary Pattern (LBP) and Fuzzy logic as feature extraction tools and Support Vector Machine (SVM) and K-Nearest Neighbour (K-NN) classifier is used to validate the results. The test face image is checked and verified with database, and if the match is not found then the captured image is mailed to the owner of the house.
2. Background
- Presently available security systems are much more costly, not user friendly and much bulkier in size. Throughout history, humans have sought to protect their life, property and possessions. But with the harnessing of electrical and computer device, protection scheme could be expected to provide consistent peace of mind. At a crude level it started with the simple video capturing and today it includes capturing images, notifying suspicious activities etc. Commercially available Security systems are too expensive to be used by common population. We are trying to present a security system that provides all the facilities needed for security like activation of a webcam, capturing an image of an intruder, along with an email notification at a very low cost. Security has been defined, as safety from harm. The need for Security systems have rapidly grown from being specialized in high-risk areas (like banks, companies, governmental institutions), to be available and demanded rapidly by the average public. Some of the common characteristics of a home security system are 24 hour monitoring, ease of use, difficulty to hack, reliability, heat and motion sensors, ability to control doors, gates, etc. Systems that monitor burglary by capturing an image has efficient, fast and precise notification system. Passive Infrared (PIR) based technology, electronic access control systems, or Video Surveillance System (VSS) cameras, security systems using email notification, SMS through GSM technology etc. are being designed. A system which is both efficient and cost effective then it will perfectly be within the budget of the user. This is the main objective of our work, i.e., to design a system that senses human movement. Along with this captures an image of the intruder which is further compared with the images of owner and if it is not matched, the system automatically sends the captured image to the desired email address in his absence.
3. Methodology
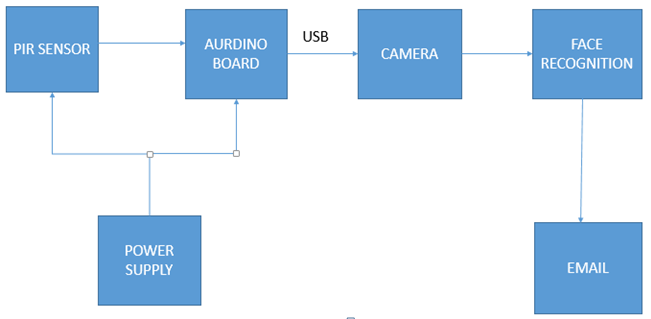
- The work was started with face recognition using Fuzzy Local Binary Pattern. After that we have used the arduino board. The board is used to Interfacing of devices like PIR sensor and camera. PCB design was done using LtSpice. PC Hardware interfacing was learnt for sending Email of captured images. Hardware designThe system block diagram of home security system is shown below which the camera will sense continues video. Camera is switched on arduino in response to PIR sensor output. In the image processing, software unit will recognize the motion in the video by converting the video images into gray scale image. The image processing is done on the processor by using the mat lab. The processed result will compare with given conditions and criterion. If the detected face is not in data base then the alarm will be raised with email to the owner. FBLP Image processing technique is used.
4. Block Diagram
4.1. PIR Sensor
- A passive infrared sensor (PIR sensor) is an electronic sensor that measures infrared (IR) light radiating from temperature variations caused by the movement of people or animals in an enclosed space. The radiant heat energy occupies the electromagnetic spectrum between light and radio waves, i.e. 0.74…. 300µm, which is usually called the infrared region. The pyroelectric infrared sensor (PIR) detects infrared radiation on the basis of the characteristics that the polarization of pyroelectric material changes with temperature. The PIR sensor has the properties to sense ambient temperature, temperature of a moving target, target distance of the Fresnel lens, ambient humidity, amplifier gain and comparison voltage that detects human movement to an extent. A warm body like a human or animal passes by, it first intercepts one half of the PIR sensor, which causes a positive differential change between the two halves. When the warm body leaves the sensing area, the reverse happens, whereby the sensor generates a negative differential change. These changes in the pulses are detected.
4.2. Arduino Uno
- An Arduino is connected to computer via USB cable. The USB connection these purposes:● Upload new software to the board.● Communicate with the Arduino board and your computer.● Supply the Arduino board with power.The Arduino Uno has a resettable poly fuse that protects our computer's USB ports from shorts and over current. Although most computers provide their own internal protection, the fuse provides an extra layer of protection. If more than 500 mA is applied to the USB port, the fuse will automatically break the connection until the short or overload is removed.
 | Figure 1. Overall Block Diagram |
 | Figure 2. Arduino Uno board |
4.3. Communication
- The Arduino Uno has a number of facilities for communicating with a computer, another Arduino, or other microcontrollers. The ATmega328 provides UART TTL (5V) serial communication, which is available on digital pins 0 (RX) and 1 (TX). An ATmega16U2 on the board channels this serial communication over USB and appears as a virtual com port to software on the computer. The ATmega16U2 firmware uses the standard USB COM drivers, and no external driver is needed. However, on Windows, a .inf file is required. The Arduino software includes a serial monitor which allows simple textual data to be sent to and from the Arduino board. The RX and TX LEDs on the board will flash when data is being transmitted via the USB-to-serial chip and USB connection to the computer (but not for serial communication on pins 0 and 1). A Software Serial library allows for serial communication on any of the Uno's digital pins.
4.4. ATmega328 Microcontroller
- The Arduino Uno USB board [2] is based on an AVR ATmega328 microcontroller operating at 5V/16MHz.Today the ATmega328 is commonly used in autonomous systems where a simple, low-powered, low-cost micro-controller is needed. Perhaps the most common implementation of this chip is on the ever popular Arduino development platform, namely the Arduino Uno and Arduino Uno models. A common alternative to the ATmega328 is the ATmega328P.
4.5. Face Recognition
- Face Recognition [3] comes under biometric systems. There are many Biometric systems has many methods. Based on iris, palm, giant, finger prints, etc. all these methods, either requires the contact with the sensor or the user needs to cooperate in capturing the image. Face recognition (FR) is one among the biometric system, that is simple to implement, and produces the good results. FR [4] over the decades has developed many algorithms. The algorithms in FR [5] are classified as (1) Holistic (2) Local features (3) Hybrid methods or Mixture of Holistic and Local features. (4) Local Patterns. The popular algorithms in Holistic approach are Principle Component Analysis (PCA) [6] Linear Discreminant Analysis (LDA) [7] and Independent Component Analysis (ICA) [8]. The Local features makes use of three dimensional information and face Fudicial points for recognition. Hybrid method makes use of above two methods, however Hybrid methods gives good results. The Local patterns are gaining much importance, as the computation is simple and produce good results in the presence of noise and other constraints. The Local Pattern examples are Binary Local Pattern (LBP) [9], Local Directional Pattern (LDP) [10], and Local Directional Number (LDN) [11] etc. In our implementation we have used the modified version of the Binary Local Pattern in the modified form using Fuzzy logic.
4.5.1. Fuzzy Logic
- Fuzzy Logic theory is the extension of conventional (crisp) set theory and fuzzy logic (FL) deals with the fuzzy sets having imprecise and uncertain data. It handles the concept of partial truth (truth values between 1 (completely true) and 0 (completely false)). It was introduced by Zadeh to model the vagueness and ambiguity in complex systems for which there is no mathematical model. The applications of FL encompass several fields; to name few, we have Computer Vision, Control Engineering, and Medical Imaging, Document processing, Signal Processing and Image processing.
4.5.2. Local Binary Pattern
- The Local Binary Pattern method (LBP) [9] is one of the most popular feature extraction method in pattern recognition. This extracts a set of binary code from a patch of 3x3 in the standard form. The LBP operator labels the pixels of an image by thresholding with the centre value of a 3x3 neighbourhood of each pixel and considering the results as a binary number, of which the corresponding decimal number is used for labelling. The derived binary numbers are called local binary patterns or LBP codes. While the LBP operator uses the information of intensity changes around pixels. An example, LBP code generation is as shown below. The threshold value of the patch is 150, and the neighbouring value greater than 150 will be binary ‘1’ and neighbouring value less than 150 will be binary ‘0’.
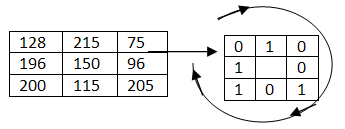 | Figure 3. The basic Local Binary Pattern (LBP) operator |
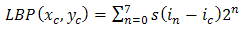 | (1) |
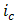 corresponds to the gray value of the centre pixel
corresponds to the gray value of the centre pixel 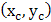 ,
, 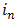 to the gray values of the 8 surrounding pixels and function
to the gray values of the 8 surrounding pixels and function 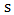 is defined as,
is defined as,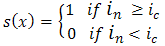 | (2) |
4.5.3. Proposed Method on Fuzzy Binary Local Pattern
- The images are divided by maximum in the image so as to have the Values between 0 to 1.These normalised values are referred as information source values
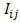 . Next partition the image into a 3X3 window and compute the
. Next partition the image into a 3X3 window and compute the 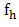 using equation 3 Our objective is to convert fuzzy sets into information sets. The Fuzzifier given in [12] gives the spread of attribute values with respect to the chosen reference (symbolized as ref). It is defined as
using equation 3 Our objective is to convert fuzzy sets into information sets. The Fuzzifier given in [12] gives the spread of attribute values with respect to the chosen reference (symbolized as ref). It is defined as 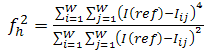 | (3) |
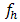 is the fuzzifier and I (ref) can be taken as average (Iavg ) or maximum ( Imax ) or minimum (Imin) from the values in a window, and
is the fuzzifier and I (ref) can be taken as average (Iavg ) or maximum ( Imax ) or minimum (Imin) from the values in a window, and 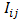 represents Normalized Intensity value also referred as Information source value. It may be noted that the above fuzzifier gives more spread than possible with variance which is used in the standard Gaussian function. The features are computed based on binary to decimal value computed from 3x3 window, fuzzifier and central pixel from same window. We call these features as Root Mean Square features (RMS). The equation is as given below;
represents Normalized Intensity value also referred as Information source value. It may be noted that the above fuzzifier gives more spread than possible with variance which is used in the standard Gaussian function. The features are computed based on binary to decimal value computed from 3x3 window, fuzzifier and central pixel from same window. We call these features as Root Mean Square features (RMS). The equation is as given below; 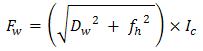 | (4) |
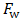 is the feature computed with 3x3 window,
is the feature computed with 3x3 window, 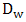 represents the LBP code computed from 3x3 window, and
represents the LBP code computed from 3x3 window, and 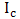 represents the central pixel value of 3x3 window. The procedure is repeated for next 3x3 window and for complete image. These features are stored as a vector. The procedure is repeated for complete database.Classifiers:K-Nearest Neighbor (K-NN) classifier is one of the simplest classifier. It is a non parametric classifier. Since it is non parametric one does not have to worry about the underlying structure. K-NN is the slow classifier. The classification is done based on voting. If K=1 the test pattern is assigned to the neighbor. K-NN is simple to implement.The classification is performed by using a Support Vector Machine (SVM) to evaluate the performance of the proposed method. SVM is a supervised (presence of a teacher) machine learning technique that inevitably maps the data into a higher dimensional feature space. Then SVM finds a linear hyperplane, with a maximum margin, to separate the data points in different classes in the higher dimensional feature space. The SVM classifier with polynomial Kernel with Degree 1 and 2 are used for the evaluation of features.
represents the central pixel value of 3x3 window. The procedure is repeated for next 3x3 window and for complete image. These features are stored as a vector. The procedure is repeated for complete database.Classifiers:K-Nearest Neighbor (K-NN) classifier is one of the simplest classifier. It is a non parametric classifier. Since it is non parametric one does not have to worry about the underlying structure. K-NN is the slow classifier. The classification is done based on voting. If K=1 the test pattern is assigned to the neighbor. K-NN is simple to implement.The classification is performed by using a Support Vector Machine (SVM) to evaluate the performance of the proposed method. SVM is a supervised (presence of a teacher) machine learning technique that inevitably maps the data into a higher dimensional feature space. Then SVM finds a linear hyperplane, with a maximum margin, to separate the data points in different classes in the higher dimensional feature space. The SVM classifier with polynomial Kernel with Degree 1 and 2 are used for the evaluation of features.4.5.4. Results with FLBP
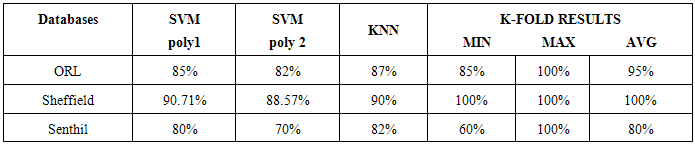
- The experiment is carried out on three databases namely ORL, Sheffield and Senthil databases. The ORL face database contains 40 subjects and each subject has 10 different facial views representing various expressions, small occlusion by glasses, different scale and orientations. All the images were taken against a dark homogeneous background with the persons in an upright, frontal position for some subjects; the images were taken at different times. Sheffield Database; The Sheffield (previously UMIST) Face Database consists of 564 images of 20 individuals (mixed race/gender/appearance). Each individual is shown in a range of poses from profile to frontal views - each subject in a separate directory labelled 1a, 1b, ... 1t and images are numbered consecutively as they were taken. Senthil Database: This database has 5 subjects and each subject has 16 images. The images were taken under different lighting condition and head orientation with expression change.To extract the features we have used equation 3 and 4 for every 3x3 window. We call these features as Root Mean Square features (RMS). To evaluate the features we have used first 50% of the images for training and remaining 50% for testing.ORL database: To conduct the experiment the image in database is divided by its maximum so as to have the values from 0 to 1.Table 1 shows the recognition on ORL database. The recognition rate of 87% is reported from K-NN. K-fold cross validation (CV); The K-fold validation technique randomly divide the dataset into k chunks (folds). The classifier is selected in our implementation we have chosen SVM classifier. for each fold train SVM classifier with all training samples except the test fold test the classifier’s accuracy on the fold. K-fold Cross Validation accuracy is the average of all k-folds.
|
 | Figure 4. Gray scale face images of some of the subject in ORL database |
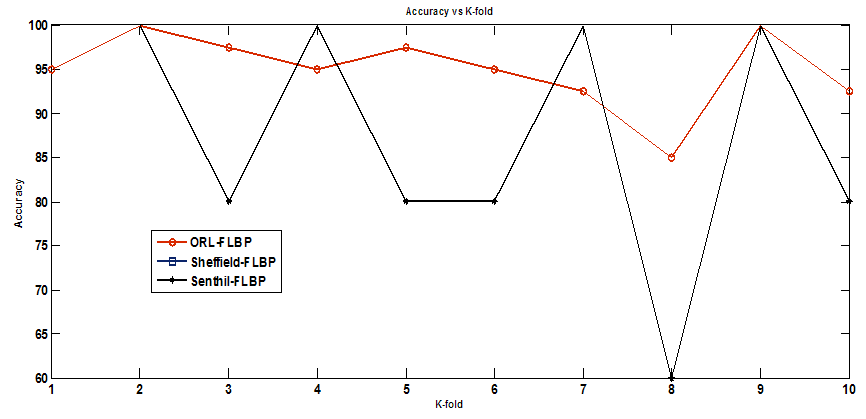 | Figure 5. K-fold results on ORL, Sheffield and Senthil face database on FLBP |
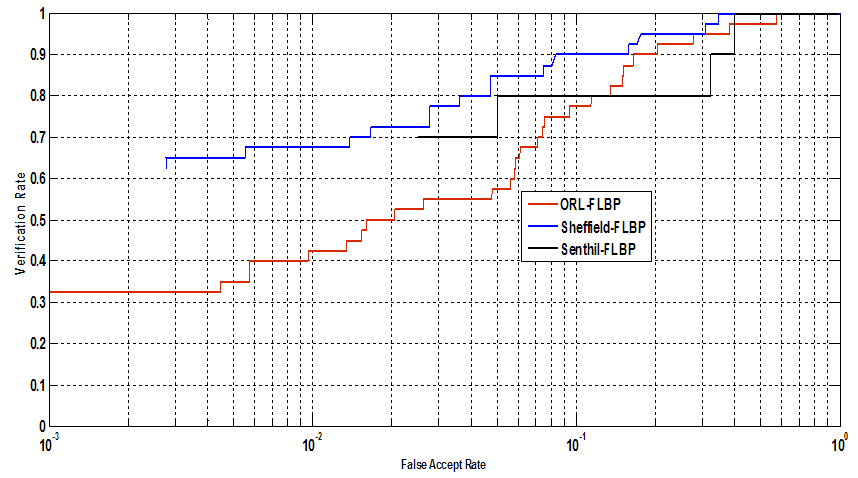 | Figure 6. ROC curves for Fuzzy Local Binary Patterns on ORL, Sheffield and Senthil database with FLBP |
4.5.5. Programming Arduino Board
- The Arduino Uno can be programmed with the Arduino software. Select Arduino Uno from the Tools > Board menu (according to the microcontroller on the board). The ATmega328 on the Arduino Uno comes pre burned with a bootloader that allows to upload new code to it without the use of an external hardware programmer. It communicates using the original STK500 protocol. It is also possible to bypass the bootloader and program the microcontroller through the ICSP (In-Circuit Serial Programming) header.
5. Conclusions
- This work presents a possible solution to the real-time problem of protecting valuables in our absence. This system senses the presence of any unknown person and notifies this to the owner of house in his absence through email. More over work is fulfilling the most important motto of making a low cost security system. High quality PIR motion sensors can be used to detect very precise moments. Video of the intruder can be stored so that we can refer it at latter stage and find the intruder. Upgrading can be done so that owner can receive a call and SMS also. Modifications can be done to have wireless communication between control and sensor units. Output of PIR detector can activate loud alarm to panic the intruder.
ACKNOWLEDGEMENTS
- I acknowledge work of project students for implementing the part of Intruder Recognition hardware.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML