-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Computer Science and Engineering
p-ISSN: 2163-1484 e-ISSN: 2163-1492
2024; 14(4): 75-77
doi:10.5923/j.computer.20241404.01
Received: Jul. 27, 2024; Accepted: Aug. 16, 2024; Published: Aug. 28, 2024

Safeguarding Your Backups: Ensuring the Security and Integrity of Your Data
Taresh Mehra
Previous Organization: Veritas Technologies (Resigned in December 2023), Pune, Maharashtra, India
Correspondence to: Taresh Mehra, Previous Organization: Veritas Technologies (Resigned in December 2023), Pune, Maharashtra, India.
| Email: |  |
Copyright © 2024 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

In the digital age, safeguarding backups is crucial for ensuring data integrity and business continuity. This blog explores the importance of protecting backups against data loss, ransomware attacks, and compliance issues. It provides best practices such as encryption, access control, and offsite storage to secure backups effectively. By implementing these strategies, organizations can mitigate risks and ensure data resilience.
Keywords: Ensuring the Security and Integrity of Your Data
Cite this paper: Taresh Mehra, Safeguarding Your Backups: Ensuring the Security and Integrity of Your Data, Computer Science and Engineering, Vol. 14 No. 4, 2024, pp. 75-77. doi: 10.5923/j.computer.20241404.01.
Article Outline
1. Introduction
- In today’s digital world, data is a critical asset for individuals and businesses alike. With increasing cyber threats and regulatory requirements, securing data backups is essential to protect against data loss and ensure business continuity. This blog examines the significance of backup security, outlines key risks, and presents best practices to enhance data protection. Our goal is to equip readers with actionable strategies to safeguard their backups effectively.
2. Methodology
- Why Safeguard Your Backups?Protection Against Data Loss:Imagine the devastating impact of losing all your critical business records, customer data, or personal files due to an unexpected cyberattack, hardware failure, or natural disaster. Backups act as a crucial safety net, providing a way to recover your information with minimal disruption. Regularly updated backups ensure that you have the most recent version of your data available, which is essential for quick recovery. Without this protection, the process of data recovery can be time-consuming and costly, leading to operational delays and potential financial loss. Effective backup strategies help mitigate these risks by ensuring data availability even in the worst scenarios. By safeguarding backups, you protect against the unexpected and preserve the continuity of your operations.Ransomware Defense:Ransomware attacks are increasingly prevalent, with cybercriminals encrypting your data and demanding a ransom for its release. Secure backups provide a critical defense mechanism against such attacks. By maintaining up-to-date and encrypted backup copies, you can restore your data to its pre-attack state without succumbing to the attackers' demands. This not only saves you from financial loss but also disrupts the attackers' plans. Moreover, incorporating advanced ransomware protection features into your backup solutions can enhance your defense against evolving threats. A well-implemented backup strategy ensures that you have viable alternatives to paying ransoms, protecting your data and organizational integrity.Business Continuity:Downtime can have significant financial repercussions for businesses, affecting operations, customer trust, and revenue. Safeguarded backups play a crucial role in minimizing downtime and ensuring business continuity. In the event of a system failure or data corruption, having reliable backups allows for quick restoration of data and systems, enabling operations to resume with minimal interruption. Effective backup solutions are integrated into disaster recovery plans to provide a seamless recovery process. This proactive approach helps prevent extensive operational disruptions and maintains business efficiency, thereby safeguarding your company’s reputation and financial health.Compliance and Legal Requirements:Many industries are subject to strict regulatory requirements regarding data protection and retention, such as GDPR, HIPAA, or SOX. Safeguarding backups is vital for meeting these compliance standards and avoiding legal consequences. Secure backups ensure that you can meet data retention requirements and provide evidence of compliance during audits or legal proceedings. Implementing robust backup and recovery processes helps in adhering to industry regulations and protecting sensitive information. Failure to comply with these regulations can result in substantial fines and legal liabilities, making effective backup management an integral part of regulatory compliance.
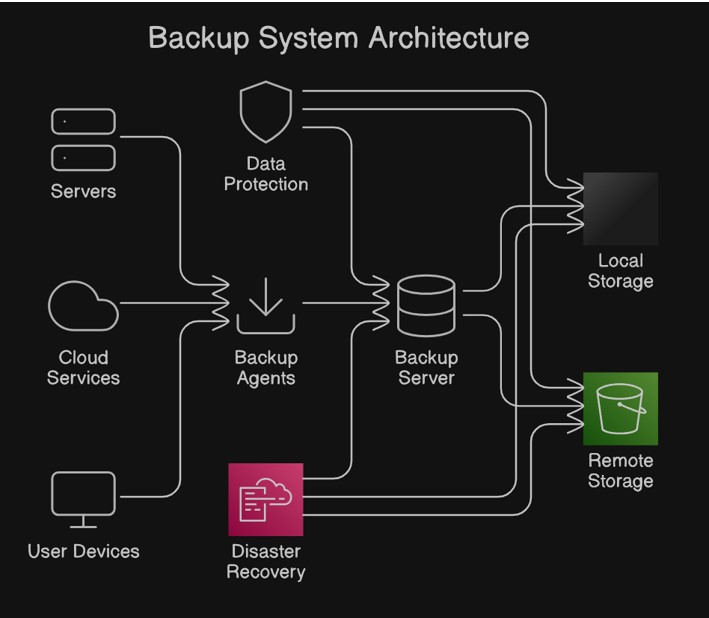 | Figure 1. Backup System Architecture Diagram" |
3. Impact of Emerging Technologies
- AI and Machine Learning in Backup SecurityEnhanced Threat Detection:Artificial Intelligence (AI) and Machine Learning (ML) are transforming backup security by enhancing threat detection capabilities. AI-powered systems can analyze vast amounts of data to identify unusual patterns or anomalies that might indicate a security threat. For instance, AI can detect subtle changes in data access patterns or usage that may signal an impending ransomware attack or unauthorized access. These early warnings enable organizations to take proactive measures to protect their backups and mitigate potential risks.Automated Backup Management:AI and ML technologies streamline backup management processes by automating routine tasks. For example, AI can optimize backup schedules based on data usage patterns, automatically adjusting the frequency of backups to ensure data is captured at the right intervals. This automation reduces the risk of human error and ensures that backups are consistently updated and reliable. Additionally, ML algorithms can predict and prevent potential issues by analyzing historical backup data and identifying trends that may indicate future problems.Intelligent Data Classification:Machine learning algorithms can assist in classifying data based on its sensitivity and importance. By categorizing data more accurately, organizations can apply appropriate security measures and backup strategies tailored to the value of the information. For example, highly sensitive data might be backed up more frequently and stored in more secure locations, while less critical data can have less stringent backup requirements. This targeted approach enhances overall backup security and efficiency.Advanced Encryption Techniques:Emerging technologies are also driving advancements in encryption methods used for protecting backups. AI can enhance encryption algorithms by optimizing key management practices and detecting potential vulnerabilities in encryption protocols. For instance, AI-driven encryption tools can automatically generate and rotate encryption keys, reducing the risk of key compromise and ensuring that backup data remains secure.Predictive Analytics for Backup Integrity:Machine learning models can predict potential backup failures or integrity issues before they occur. By analyzing historical backup data and system performance metrics, ML algorithms can forecast when a backup might become unreliable or fail. This predictive capability allows organizations to address potential issues proactively, reducing the risk of data loss and ensuring that backups remain intact and functional.
4. Best Practices for Safeguarding Backups
- 1. Use Encryption:Encrypt backups both in transit and at rest to protect against unauthorized access. Strong encryption algorithms such as AES (Advanced Encryption Standard) should be used.2. Implement Access Controls:Restrict access to backups based on the principle of least privilege. Only authorized personnel should have access to backup data and systems.3. Regularly Test Backups:Ensure that backups are reliable and can be restored successfully. Regular testing verifies the integrity of backups and identifies any potential issues before they become critical.4. Store Backups Offsite:Maintain copies of backups in secure offsite locations to protect against physical threats like fire, theft, or natural disasters that could impact your primary data center.5. Monitor and Audit:Implement monitoring and auditing mechanisms to detect unauthorized access attempts or anomalies in backup activities. Promptly investigate any suspicious activity.
5. Key Components
- Encryption Layer: Encrypt data during transmission and storage.Access Control: Implement strict access controls and authentication mechanisms.Offsite Storage: Maintain backups in geographically diverse locations.Monitoring: Monitor backup activities for anomalies and unauthorized access attempts.Testing and Validation: Regularly test backups to ensure recoverability.
6. Conclusions
- In conclusion, safeguarding backups is not merely a best practice but a critical necessity in today's digital landscape. Whether you're safeguarding business-critical data or personal information, the principles of encryption, access control, offsite storage, monitoring, and testing are essential for ensuring the security, availability, and integrity of your backups. By incorporating emerging technologies like AI and machine learning into your backup strategies, you can further enhance your ability to protect data and respond to evolving threats. Implementing these practices diligently mitigates risks, protects against data loss, and maintains continuity in the face of unforeseen events. Remember, the value of your data lies not just in its existence but in its accessibility and security.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML