Mayank Hindka
Computer Information Systems, Texas A&M University-Central Texas, United States
Correspondence to: Mayank Hindka , Computer Information Systems, Texas A&M University-Central Texas, United States.
| Email: |  |
Copyright © 2024 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Abstract
In today's digital landscape, Application Programming Interfaces (APIs) are the backbone of modern software architecture, enabling seamless communication and interaction between diverse systems and applications. However, the widespread adoption of APIs has also heightened concerns regarding security vulnerabilities and potential threats. This paper aims to provide a comprehensive guide to API security patterns, offering insights into various techniques and best practices for securing APIs in different contexts. By understanding and implementing these security patterns, developers and organizations can bolster their API ecosystems' integrity, confidentiality, and availability, mitigating risks and safeguarding sensitive data.
Keywords:
Application Programming Interface (API), Digital Transformation, Internet of Things (IoT), API Attacks, API Security, Cyber-Security, Authentication, Authorization, Encryption, Best practices, Patterns, and threat mitigation
Cite this paper: Mayank Hindka , Securing the Digital Backbone: An In-depth Insights into API Security Patterns and Practices, Computer Science and Engineering, Vol. 14 No. 2, 2024, pp. 35-41. doi: 10.5923/j.computer.20241402.02.
1. Introduction
Application Programming Interfaces (APIs) [1] have revolutionized the landscape of modern software development, offering a standardized mechanism for building interoperable, scalable, and extensible applications. APIs serve as the bridge between different software components, enabling seamless communication, data exchange, and functionality integration across diverse systems and platforms. REST has significantly developed and expanded, with numerous authors offering guidance on crafting and constructing practical REST APIs [2], [3], [4], [5], [6]. From web applications and mobile apps to Internet of Things (IoT) devices and cloud services, APIs have a crucial role in enabling the interaction among software entities, driving innovation, and enhancing user experiences. The growing importance of API security in light of increasing cyber-attacks [14] and data breaches, and there are several factors contribute to the heightened emphasis on API security in today's digital landscape; some of the significant factors are as follows-1. The proliferation of APIs: With the rise of microservices architecture, cloud computing, and digital transformation initiatives, the number of APIs exposed to the internet has multiplied exponentially.2. Complexity of API Ecosystems: Modern applications often comprise a complex ecosystem of interconnected APIs, spanning multiple services, platforms, and third-party integrations. Managing the security posture of interconnected APIs requires a comprehensive understanding of data flows.3. Increased Attack Surface: APIs expose endpoints and data interfaces that can be targeted by various cyber threats, including injection attacks, broken authentication, sensitive data exposure, XML External Entity (XXE) attacks, and API endpoint enumeration. Attackers exploit these vulnerabilities to bypass security controls, escalate privileges, and compromise sensitive data.4. Data Privacy & Compliance Regulations: Organizations must adhere to stringent data privacy regulations and regulatory obligations, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Payment Card Industry Data Security Standard (PCI DSS).5. Sophisticated Threat Landscape: Cyber adversaries employ sophisticated techniques, tools, and tactics to exploit vulnerabilities in APIs and perpetrate attacks, including credential stuffing, API scraping, Man-in-the-Middle (MitM) attacks, and distributed denial-of-service (DDoS) attacks.
2. Shift-Left Security Practices
Adopting DevSecOps principles and "shift-left" security practices emphasizes integrating security into the software development lifecycle from the earliest design and development stages. By embedding security controls, automated testing, and vulnerability scanning into CI/CD pipelines, organizations can identify and remediate security flaws in APIs before they are deployed into production environments. In response to these challenges, organizations must prioritize API security as an integral component of their cybersecurity strategy, adopting a holistic approach that encompasses the following fundamental principles:1. Authentication and Access Control: Implement robust authentication mechanisms, access controls, and session management policies to verify the identity of users, applications, and devices accessing APIs.2. Encryption and Data Protection: Utilize robust encryption algorithms, Transport Layer Security (TLS), and data masking techniques to encrypt sensitive data while it's being transmitted and stored, mitigating the risk of data interception and tampering.3. API Security Testing and Auditing: Conduct comprehensive security testing, code reviews, and penetration testing to identify vulnerabilities, security misconfigurations, and compliance gaps in APIs. Regular security audits and vulnerability assessments help organizations maintain the integrity and resilience of their API ecosystems.4. Threat Intelligence and Monitoring: Leverage threat intelligence feeds, anomaly detection algorithms, and security information and event management (SIEM) solutions to monitor API traffic, detect suspicious activities, and promptly address security incidents as they occur.
3. Fundamentals of API Security
As APIs become increasingly integral to modern software architecture and digital ecosystems, they attract the attention of malicious actors seeking to exploit vulnerabilities and bypass security controls. The following are some of the most prevalent threats and attack vectors targeting APIs:1. Injection Attacks: Injection attacks, such as SQL injection (SQLi) and NoSQL injection, occur when malicious input is injected into API parameters, query strings, or data payloads to manipulate database queries, run unauthorized code, or obtain access to sensitive information without authorization. Attackers exploit poorly sanitized input to bypass input validation and execute malicious commands, compromising the data's integrity and confidentiality preserved during storage or processing of the API. 2. Broken Authentication: Broken authentication vulnerabilities arise when APIs fail to enforce robust authentication mechanisms, session management controls, or credential protection measures. Attackers exploit weak or predictable passwords, session tokens, and authentication tokens to impersonate legitimate users, hijack sessions, and gain unauthorized access to protected resources or privileged functionality. 3. Sensitive Data Exposure: Sensitive data exposure occurs when APIs inadvertently disclose confidential information, such as personally identifiable information (PII), financial data, or authentication credentials, in response to unauthenticated or unauthorized requests. Inadequate encryption, improper data masking, and insecure transmission protocols may expose sensitive data to eavesdropping, interception, or unauthorized access by attackers.4. XML External Entity (XXE) Attacks: XML External Entity (XXE) attacks target APIs that parse XML-based input without proper validation and sanitization. Attackers craft malicious XML documents containing external entity references and exploit XML processors to read sensitive files, perform server-side request forgery (SSRF) attacks, or exfiltrate sensitive data from the server environment. 5. Broken Access Controls: Broken access controls occur when APIs fail to enforce proper authorization mechanisms, access controls, and least privilege principles, allowing unauthorized users or malicious actors to escalate privileges, access restricted resources, or perform unauthorized actions. Insufficient validation of user permissions, insecure direct object references (IDOR), and lack of input validation may result in unauthorized data access or API operations. 6. Cross-Site Scripting (XSS): Cross-site scripting (XSS) vulnerabilities occur when APIs return untrusted data in web responses without proper encoding or escaping, enabling attackers to inject harmful scripts into web pages accessed by other users. Stored XSS, reflected XSS and DOM-based XSS attacks exploit client-side vulnerabilities to steal session cookies, perform client-side attacks, or deface web applications.7. Cross-Site Request Forgery (CSRF): Cross-Site Request Forgery (CSRF) attacks exploit trust relationships between authenticated users and web applications to trick users into unknowingly executing unauthorized actions on behalf of the attacker. Attackers craft malicious requests, embed them in specially crafted web pages or emails, and lure victims into being directed to malicious links or submitting counterfeit requests, resulting in unintended actions and unauthorized transactions.
4. API Security Patterns
API security patterns are best practices and solutions to protect APIs from various security threats. They ensure that the data transmitted to and from the API is safeguarded and that only authorized users can access it. Key security patterns include using tokens for authentication, such as JWT (JSON Web Tokens), implementing OAuth for secure delegated access, employing HTTPS to encrypt data in transit, and applying throttling and rate limiting to prevent abuse. Input validation, consistent logging, and regular security audits are also integral to maintaining the integrity and confidentiality of API endpoints. These patterns are crucial for preserving trust in an API ecosystem, especially considering the widespread reliance on APIs for web services, cloud technology, and microservices architectures.1. Authentication Patterns: Authentication patterns comprise OAuth 2.0, Open ID Connect, and API-Key. The steps in Figure 1 are the OAuth 2.0 [7] Authentication process sequence.A. The first and most used authentication pattern, OAuth 2.0, has been popular in securing most APIs. OAuth 2.0 is a widely adopted authorization framework that allows applications to secure access to server resources on behalf of a user. It streamlines user authentication and authorization by employing tokens rather than credentials, facilitating a more secure and flexible access control mechanism across web, mobile, and desktop applications.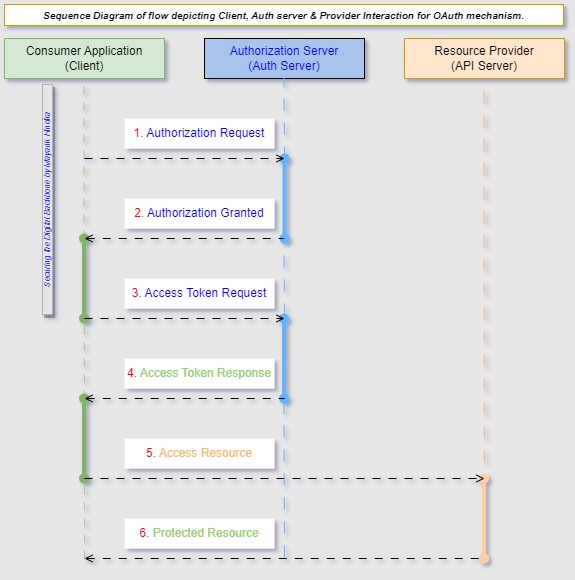 | Figure 1. Sequence Diagram for OAuth 2.0 Authentication |
The OAuth 2.0 sequence in Figure 1 has been detailed and explained as (i) Authorization Request: The consumer application initiates the OAuth sequence by dispatching an authorization request to the authorization server. This request generally comprises information like the client ID, scope of access, and redirect URI. (ii) Authorization Grant: The authorization server authenticates the user and asks for consent if needed. Once the user grants authorization, the authorization server issues an authorization grant (e.g., an authorization code). (iii) Access Token Request: The consumer application presents the client with an authorization grant to the authorization server and solicits an access token. (iv) Access Token: The authorization server validates the grant and issues an access token to the consumer application. (v) Access Resource: The consumer application uses the access token to authenticate itself to the resource server and requests access to the protected resources. (vi) Protected Resource: The resource server verifies the access token. If the token is valid and has the necessary permissions, it provides the requested resources to the consumer application. In summary, OAuth 2.0 enables secure API access by allowing consumer applications to obtain access tokens from an authorization server. These tokens are then used to authenticate and authorize requests to access protected resources from the resource server.B. Another very effective authentication pattern is API-Key [8]. API key-based authentication is a straightforward method for controlling access to APIs, but it lacks some features found in more advanced authentication mechanisms like OAuth 2.0 or OpenID Connect. For instance, API keys do not provide identity information about the client application or user or support fine-grained access control or token expiration management. The API-Key [8] authentication steps are detailed in Figure 2 as follows.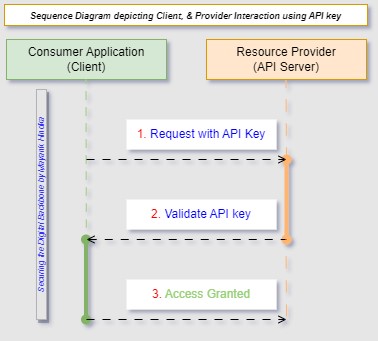 | Figure 2. Sequence Diagram for API-Key Authentication |
As outlined in Figure 2, the API-Key-based authentication is explained as (i) Request with API Key: The client application includes its API key with the request it sends to the API server. The API key is typically included in the request header, query parameters, or as part of the request body. (ii) Validate API Key: Upon receiving the request, the API server validates the API key included in the request. This validation process typically involves checking the API key against a list of valid keys stored by the API server. If the key is valid, the Server proceeds with processing the request; otherwise, it rejects the request. (iii) Access Granted: If the API key is valid, the API server grants access to the requested resource or performs the requested operation. It sends the response back to the client application, allowing it to consume the API's functionality.2. Authorization Patterns: Authorization patterns like Role-Based Access Control (RBAC) [11], [12], Attribute-Based Access Control (ABAC) [13], and JSON Web Tokens (JWT) [10] play crucial roles in securing applications. RBAC assigns permissions based on roles, ABAC uses attributes for fine-grained access, and JWT securely transfers claims for authentication and authorization. A. Role-based Access Control (RBAC) [11], [12] is a security mechanism restricting system access to authorized users based on their organizational roles. It simplifies management and enforcement of enterprise-wide access policies by assigning permissions to roles rather than individual users, enhancing security and operational efficiency. The Sequence in Figure 3 outlines the RBAC pattern.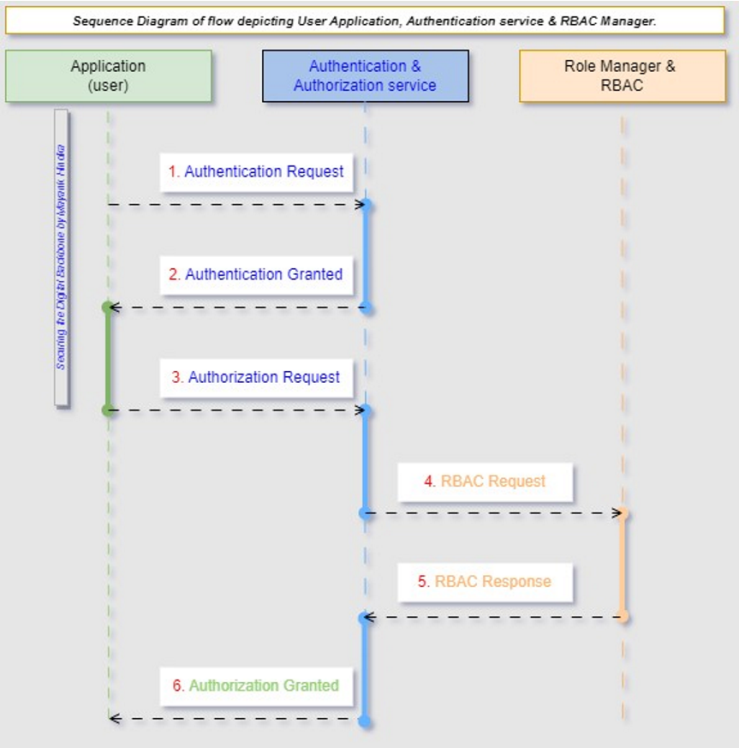 | Figure 3. Sequence Diagram for RBAC Authorization |
The Role-Based Access Control (RBAC) sequence, as outlined in Figure 3, is explained as follows. (i) Application: This represents the software system or application where role-based authorization is implemented. (ii) Authentication: Authentication ensures that users are who they claim to be. It verifies the identity of users through credentials such as usernames and passwords. (iii) Authorization: Once users are authenticated, authorization determines what actions or resources they can access based on their roles and permissions. (iv) Role Manager: The Role Manager manages roles within the system. It handles tasks such as creating roles, assigning permissions to roles, and associating roles with users or user groups. (v) Role-Based Access Control (RBAC): RBAC is the mechanism that enforces access control policies based on the roles assigned to users. It guarantees that users can solely execute actions or reach resources authorized for their roles.B. The second authorization pattern detailed and explored here is the Attribute-Based Access Control (ABAC) [13]. The Sequence diagram below outlines the flow of attribute-based access control within an application, from authentication and authorization to policy evaluation and enforcement.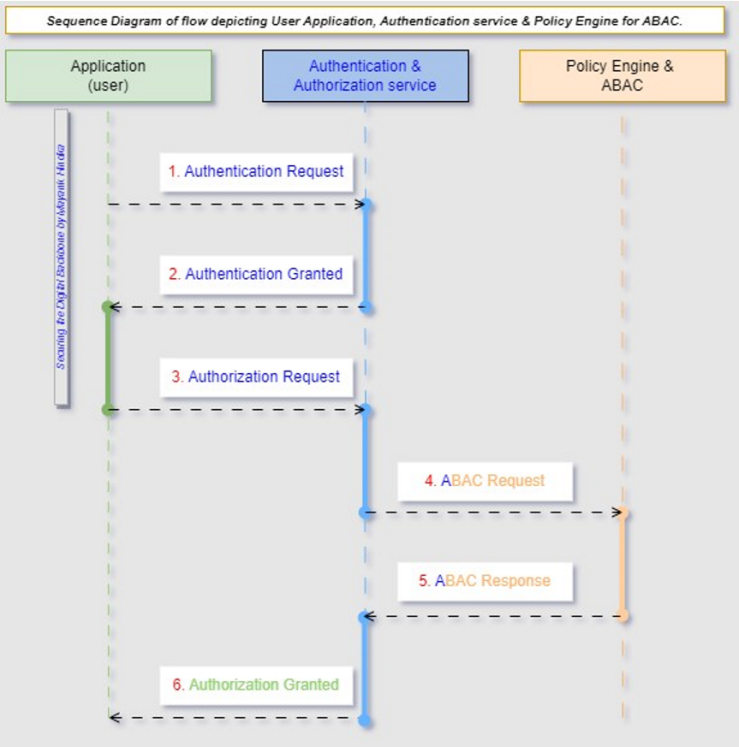 | Figure 4. Sequence Diagram for ABAC Authorization |
The Attribute-Based Access Control (ABAC) sequence, as outlined in Figure 3, is explained as follows. (i) Application: This represents the software system or application where attribute-based access control is implemented. (ii) Authentication: Authentication verifies the identity of users through credentials such as usernames and passwords. (iii) Authorization: Authorization determines what actions or resources users can access based on policies defined in the policy engine. (iv) Policy Engine: The Policy Engine evaluates policies that define access control rules based on attributes of users, resources, and environmental conditions. It handles policy decision-making and enforcement. (v) Attribute-Based Access Control (ABAC): ABAC is a model that uses attributes of users, resources, and environmental conditions to make access control decisions. Attributes can include user roles, user attributes, resource attributes, environmental attributes, and relationships between these attributes.C. The Third authorization pattern is JSON Web Token (JWT) [10]. JSON Web Tokens (JWT) [10] are a compact, URL-safe means of representing claims to be transferred between two parties. They facilitate the secure transmission of information as a JSON object, efficiently encoded and optionally signed or encrypted. JWTs are commonly used in token-based authentication systems to manage user sessions. The flow sequence in Figure 5, has been drawn to explain this pattern in detail. 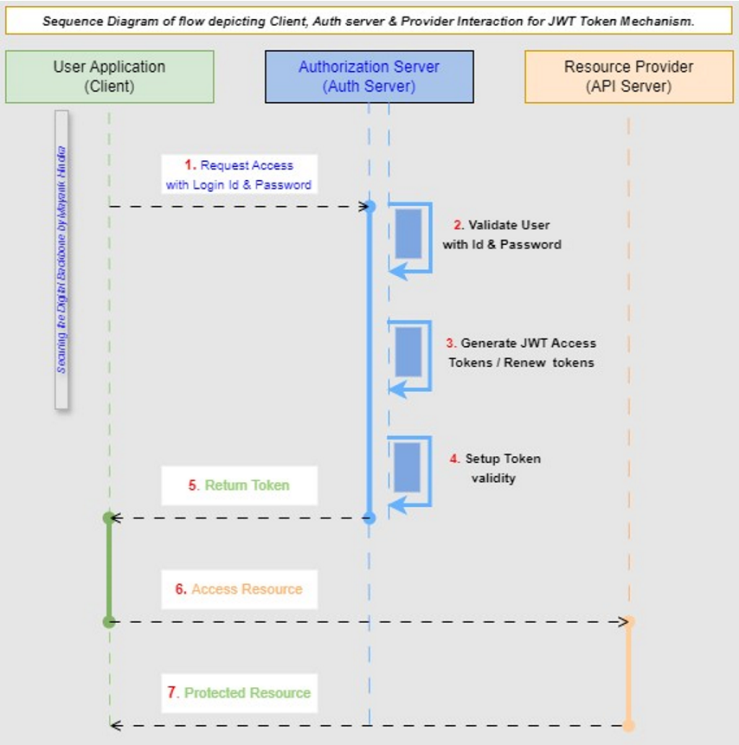 | Figure 5. Sequence Diagram for JWT Authorization |
The JSON Web token (JWT) approach, as shown in Figure 5, is explained in detail. (i) User Application: The user seeks access to a safeguarded resource from the Resource Server. (ii) Authorization Server: The Resource Server forwards the request to the Authorization Server. (iii) Generate JWT: The Authorization Server authenticates the user and generates a JWT containing the user's claims (such as user ID, roles, and other relevant information). (iv) JWT Token Validity: The Authorization Server returns the JWT to the user. (v) Return Token: The user includes the JWT in subsequent requests to reach protected resources hosted on the Resource Server. (vi) Access Resource: The Resource Server validates the JWT to ensure its integrity and authenticity. The Resource Server grants access to the requested resource if the JWT is valid and contains the necessary claims. (vii) Protected Resource: The Resource Server returns the requested resource to the user.3. Encryption and Data Protection Patterns: Transport Layer Security (TLS) is a protocol that provides privacy and data integrity between two communicating computer applications. It's the most widely deployed security protocol today. It is used for web browsers and other applications that require data to be securely exchanged over a network, such as file transfers, VPN connections, instant messaging, and voice-over IP. The sequence of flow in TLS is shown below in Diagram 6. In general, TLS flow involves 7 steps, as listed below-• Starting the TLS Handshake• Server Authentication and Pre-Master Secret• Key Generation• Client and Server Finished Messages• Data Transmission• Continuous Data Protection• Session ClosureFigure 6 outlines a detailed data flow sequence for all the above steps. These steps ensure that data transmission is secure, authenticated, and reliable. Message-level encryption within TLS ensures that even if individual messages are intercepted, they cannot be read without the encryption keys. Key management and rotation are crucial for maintaining the security of the TLS session throughout its duration.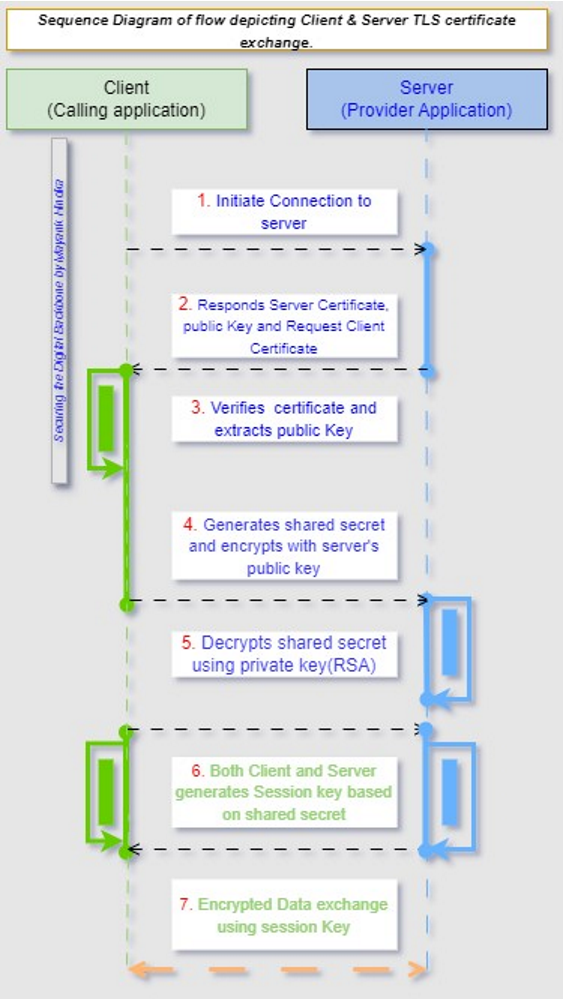 | Figure 6. Data Flow Sequence Diagram for TLS |
The Transport layer security (TLS) approach is explained in detail, as shown in Figure 6. (i) Initiate Connection to Server: The client begins a connection request to the server. (ii) Server Responds: The server responds by transmitting its digital certificate, which contains its public key, and it also Server Certificate: The client verifies the Server's certificate using a trusted Certification Authority (CA). It checks the signature, validity, and other details to ensure the certificate is legitimate. (iv) Client Generates Shared Secret: The client generates a shared secret, and the server replies by sending its digital certificate, which holds its public key. (v) Server Decrypts and transmission starts: The Server decrypts the shared secret using its private key. (vi) Session key generated at Client & Server: The client and Server generate session keys based on the shared secret. (vii) Session Closure: Encrypted data exchange occurs between the client and Server using the session keys.Example 1. Implementing TLS encryption and data protection using client and server code in Python. In this example, I tried to depict a client and server sample implementation that can be used to establish a TLS connection. The Python module of “.ssl” provides the functionality and class to implement. • Here is the Server-side class code in Python-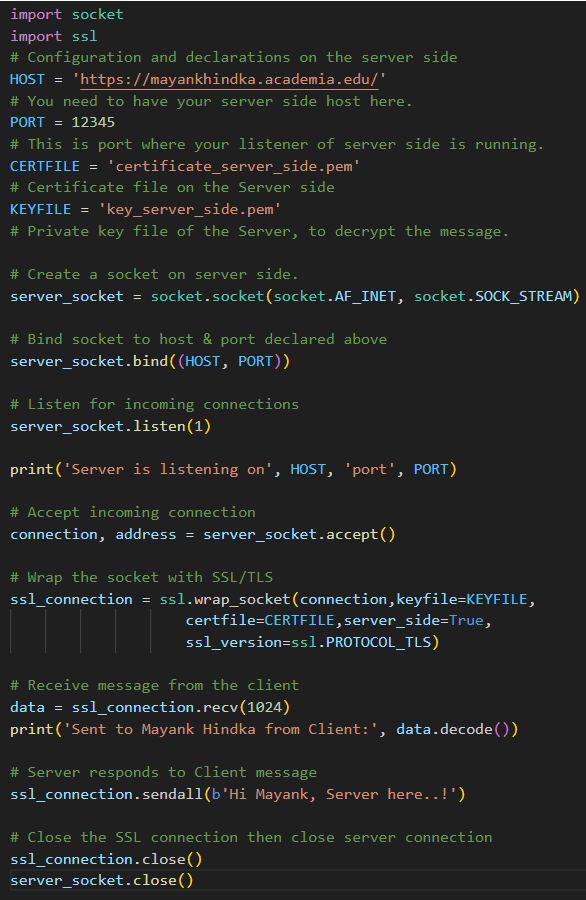 | Figure 7. Server-side code in Python |
• The Client-side code is depicted below.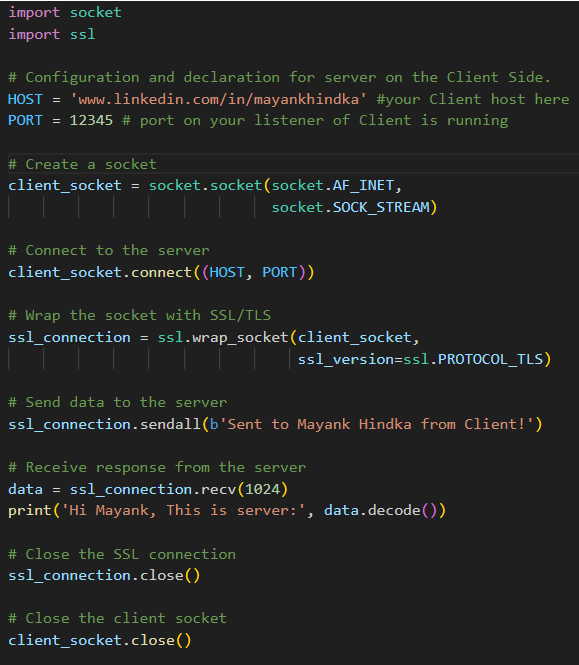 | Figure 8. Client-side code in Python |
As the code on the server side in (Figure 7) and the client side in (Figure 8) depicted above shows, specific points must be considered before using the code. • The server code binds to a specific host and port, listens for incoming connections, and accepts one connection simultaneously.• The client code establishes a connection with the server and sends data to it.• The Server and client use the ssl.wrap_socket() function to wrap their sockets with SSL/TLS.• The Server requires a certificate file (certificate_server_side.pem) and a private key file (key_server_side.pem) for secure communication.• Replace the certificate and private key file paths with your actual certificate and critical file paths.• The client does not require certificates in this example, but in a real-world scenario, it did need. 4. Rate Limiting [9] and Throttling Implementing rate limiting and throttling in APIs is crucial for managing server resources effectively and ensuring equitable access for all users. Rate limiting controls how many requests a user can make to an API within a specific timeframe, while throttling adjusts the speed of responses based on server load or user quota. These mechanisms prevent server overload by capping the number of requests, which is particularly important for high-traffic APIs where demand can exceed server capacity. To implement these, developers can use algorithms like the Token Bucket or Leaky Bucket, allowing flexibility in handling burst traffic and steady request rates. Additionally, setting clear policies and communicating limits through HTTP headers or documentation helps users understand their usage constraints. By strategically applying rate limiting and throttling, API providers can enhance service reliability, optimize resource utilization, and improve user experience, balancing accessibility with the imperative of maintaining robust and responsive services.Implementing rate limiting to prevent API abuse and DDoS attacks involves the following steps: (i) Set Reasonable Rate Limits: Define rate limits that balance accommodating legitimate usage and preventing abuse. Consider factors such as the nature of your API, expected traffic volume, and the needs of your users when setting rate limits. (ii) Apply Granular Rate Limiting: Implement granular rate limiting depending on criteria like client IP address, user identity, API endpoint, or HTTP method. Granular rate limiting allows you to apply different rate limits to various user groups or types of requests. (iii) Choose an Appropriate Rate-Limiting Algorithm: Select a rate-limiting algorithm that suits your specific use case and performance requirements. Standard algorithms include Token Bucket, Leaky Bucket, and Fixed Window. When choosing an algorithm, consider factors like accuracy, scalability, and ease of implementation. (iv) Consider Burst Rate Limits: Implement burst rate limits to allow short-term bursts of traffic while enforcing overall rate limits over extended periods. Burst rate limits can help accommodate sudden spikes in traffic without compromising the stability of your API.
5. Conclusions
In concluding recommendations on API security, it's imperative to consolidate the critical insights and recommendations that form the bedrock of a robust security posture. First and foremost, the security of APIs is not a one-time event but an ongoing process that involves constant vigilance and adaptation to emerging threats. Organizations must recognize the dynamic nature of the threat landscape and that adversaries continually evolve their tactics. Thus, staying ahead requires continuously monitoring, assessing, and improving security controls.It has been emphasized that proactive measures are the cornerstone of adequate API security. This encompasses adopting best practices such as strong authentication, implementing rate limiting, securing sensitive data, and employing encryption both in transit and at rest. Regular security audits and vulnerability assessments are non-negotiable in identifying and remediating potential weaknesses before they are exploited.API security is not merely a technical challenge but a strategic imperative that requires a cultural shift within the organization. Developers, security professionals, and organizational leaders must work collaboratively to ingrain security into the very fabric of the development lifecycle. Security considerations must be integrated from the design phase to deployment and beyond under a "security by design" philosophy.The threat environment constantly changes, with new vulnerabilities being discovered and exploited. In response, the security community must remain vigilant and share information about threats and breaches, thus fostering a collective defense approach. Investing in threat intelligence and being part of broader security communities can significantly enhance an organization's awareness and responsiveness to new risks.Finally, this is a call to action for all stakeholders creating and managing APIs. Developers must embrace secure coding practices, organizations should allocate sufficient resources for security initiatives, and security professionals must remain abreast of the latest developments in cybersecurity. It's crucial to prioritize API security as an integral component of the software infrastructure, recognizing that the cost of prevention exceeds the potential losses from a security breach. By taking these steps, we can aim not just to defend but to set new standards of security excellence in our interconnected digital ecosystem.
References
| [1] | Reddy, M. (2011). API Design for C++. Elsevier Science. |
| [2] | M. Mass´e, REST API Design Rulebook. O’Reilly, 2011. |
| [3] | H. Subramanian and P. Raj, Hands-On RESTful API Design Patterns and Best Practices: Design, develop, and deploy highly adaptable, scalable, and secure RESTful web APIs. Packt Publishing Ltd, 2019. |
| [4] | M. Biehl, “RESTful API design: Best practices in api design with rest,” 2016. |
| [5] | Microsoft. (2022) RESTful web API design. [Online]. Available: https://docs.microsoft.com/en-us/azure/architecture/best-practices/api-design. |
| [6] | J. Au-Yeung and R. Donovan. (2020) Best practices for rest Api design: https://stackoverflow.blog/2020/03/02/best-practices-for-rest-api-design/. |
| [7] | Fett, D., Küsters, R., & Schmitz, G. (2016, October). A comprehensive formal security analysis of OAuth 2.0. In Proceedings of the 2016 ACM SIGSAC conference on computer and communications security (pp. 1204-1215). |
| [8] | Walsh, K., & Manferdelli, J. (2017, June). Intra-cloud and inter-cloud authentication. In 2017 IEEE 10th International Conference on Cloud Computing (CLOUD) (pp. 318-325). IEEE. |
| [9] | Sharieh, S., & Ferworn, A. (2021, October). Securing apis and chaos engineering. In 2021 IEEE Conference on Communications and Network Security (CNS) (pp. 290-294). IEEE. |
| [10] | Jones, M. B., Bradley, B., & Sakimura, S. (May 2015). JSON Web Token (JWT). IETF. https://doi.org/10.17487/RFC7519. ISSN 2070-1721. RFC 7519. |
| [11] | Ferraiolo, D. F., & Kuhn, D. R. (October 1992). Role-Based Access Control. In 15th National Computer Security Conference (pp. 554–563). |
| [12] | Sandhu, R., Coyne, E. J., Feinstein, H. L., & Youman, C. E. (August 1996). Role-Based Access Control Models. IEEE Computer, 29(2), 38–47. https://doi.org/10.1109/2.485845. S2CID 1958270. |
| [13] | Computer Security Division, Information Technology Laboratory (2016-05-24). "Attribute Based Access Control | CSRC | CSRC". CSRC | NIST. Retrieved 2021-11-25. |
| [14] | Hindka, M. (March 2024). DESIGN AND ANALYSIS OF CYBER SECURITY CAPABILITY MATURITY MODEL. https://www.doi.org/10.56726/IRJMETS50400. |










 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML