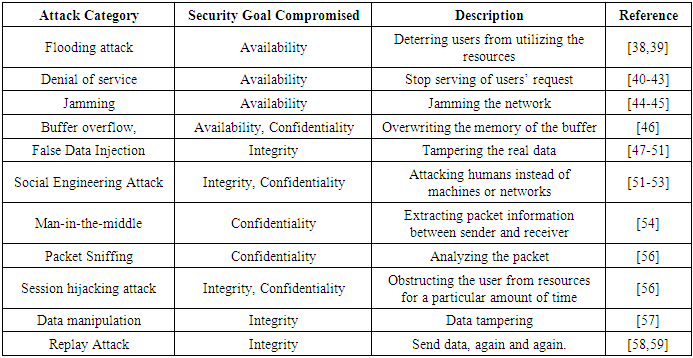
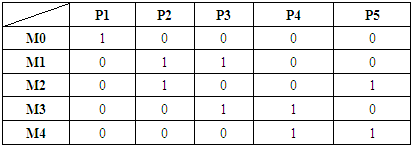
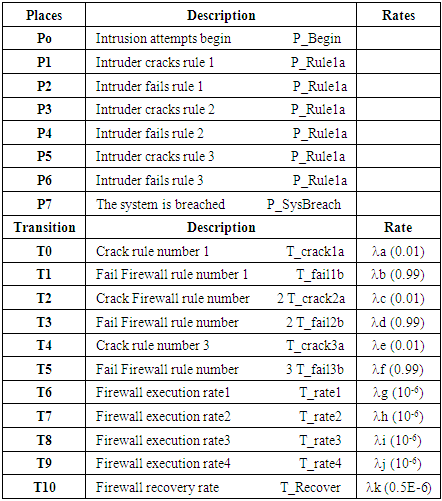
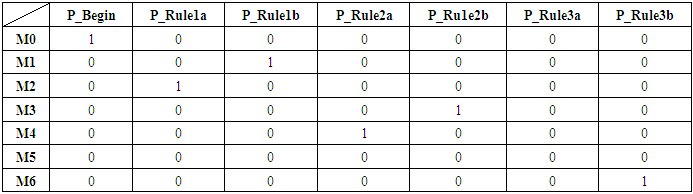
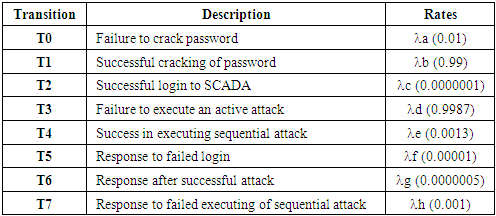
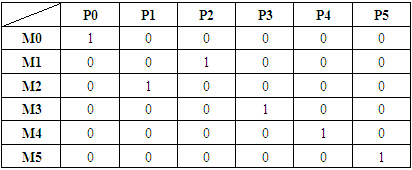
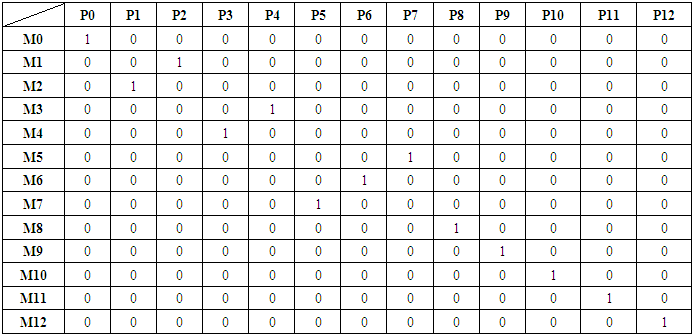
| [1] | Awad, A.; Bazan, P.; German, R. SGsim: A simulation framework for smart grid applications. In Proceedings of the 2014 IEEE International Energy Conference (ENERGYCON), Cavtat, Croatia, 13–16 May 2014; pp. 730–736. |
| [2] | Al Ghazo, Alaa, "A framework for Cybersecurity of Supervisory Control and Data Acquisition (SCADA) Systems and Industrial Control Systems (ICS)" (2020). Graduate Theses and Dissertations. 17834. |
| [3] | Davis, K. R., Davis, C. M., Zonouz, S. A., Bobba, R. B., Berthier, R., Garcia, L., et al. (2015). A cyber-physical modeling and assessment framework for power grid infrastructures. IEEE Trans. Smart Grid 6, 2464–2475. doi:10.1109/tsg.2015.2424155. |
| [4] | Handa, A., Sharma, A., and Shukla, S. K. (2019). Machine learning in cybersecurity: a review. WIREs Data Mining Knowl Discov. 9, e1306. doi:10.1002/widm.1306. |
| [5] | Johnson, J., Onunkwo, I., Cordeiro, P., Wright, B.J., Jacobs, N. and Lai, C. (2020), Assessing DER network cybersecurity defenses in a power-communication co-simulation environment. IET Cyber-Physical Systems: Theory & Applications, 5: 274-282. https://doi.org/10.1049/iet-cps.2019.0084. |
| [6] | Li, Beibei & Xiao, Gaoxi & Lu, Rongxing & Deng, Ruilong & Bao, Haiyong. (2019). On Feasibility and Limitations of Detecting False Data Injection Attacks on Power Grid State Estimation Using D-FACTS Devices. IEEE Transactions on Industrial Informatics. PP. 10.1109/TII.2019.2922215. |
| [7] | Hans de Bruijn, Marijn Janssen. Building Cybersecurity Awareness: The need for evidence-based framing strategies, Government Information Quarterly, Volume 34, Issue 1, 2017, Pages 1-7. |
| [8] | Coffey K. et al. (2018) Vulnerability Assessment of Cyber Security for SCADA Systems. In: Parkinson S., Crampton A., Hill R. (eds) Guide to Vulnerability Analysis for Computer Networks and Systems. Computer Communications and Networks. Springer, Cham. https://doi.org/10.1007/978-3-319-92624-7_3. |
| [9] | Hong, Jin & Enoch, Simon & Kim, Dan & Nhlabatsi, Armstrong & Fetais, Noora & Khan, Khaled. (2018). Dynamic Security Metrics for Measuring the Effectiveness of Moving Target Defense Techniques. Computers & Security. 79. 10.1016/j.cose.2018.08.003. |
| [10] | Häckel, Björn & Niesel, Oliver & Bogenreuther, Maximilian & Berger, Stephan. (2019). Modeling Availability Risks of IT Threats in Smart Factory Networks - A Modular Petri Net Approach. |
| [11] | Razzaq M, Ahmad J (2015) Petri Net and Probabilistic Model Checking Based Approach for the Modelling, Simulation, and Verification of Internet Worm Propagation. PLoS ONE 10(12): e0145690. https://doi.org/10.1371/journal.pone.0145690. |
| [12] | T. M. Chen, J. C. Sanchez-Aarnoutse and J. Buford, "Petri Net Modeling of Cyber-Physical Attacks on Smart Grid," in IEEE Transactions on Smart Grid, vol. 2, no. 4, pp. 741-749, Dec. 2011, doi: 10.1109/TSG.2011.2160000. |
| [13] | K. Labadi, A.-M. Darcherif, I. El Abbassi and S. Hamaci (2020) Petri Net-Based Approach for “Cyber” Risks Modelling and Analysis for Industrial Systems E3S Web Conf., 170 02001 DOI: https://doi.org/10.1051/e3sconf/202017002001. |
| [14] | Beibei Li, Rongxing Lu, Kim-Kwang Raymond Choo, WeiWang, and Sheng Luo (2018) On Reliability Analysis of Smart Grids under Topology Attacks: A Stochastic Petri Net Approach. |
| [15] | Mahmoudi-Nasr, Payam. (2018). Petri Net Model of Insider Attacks in SCADA System. |
| [16] | Markiewicz, Michał & Gniewek, Lesław. (2017). A Program Model of Fuzzy Interpreted Petri Net to Control Discrete Event Systems. Applied Sciences (Switzerland). 7. 10.3390/app7040422. |
| [17] | Radoglou Grammatikis, Panagiotis & Sarigiannidis, Panagiotis & Giannoulakis, Ioannis & Kafetzakis, Emmanouil & Panaousis, Emmanouil. (2019). Attacking IEC-60870-5-104 SCADA Systems. 10.1109/SERVICES.2019.00022. |
| [18] | Jasiul, B.; Szpyrka, M.; Śliwa, J. Detection and Modeling of Cyber Attacks with Petri Nets. Entropy 2014, 16, 6602-6623. https://doi.org/10.3390/e16126602. |
| [19] | K. Yamashita, C.-W. Ten, Y. Rho, L. Wang, W. Wei, and A. F. Ginter, (2020) Measuring systemic risk of switching attacks based on cybersecurity technologies in substations,” IEEE Trans. Power Syst., vol. 35, no. 6, pp. 4206–4219, Nov. 2020. [Online]. Available: https://ieeexplore.ieee.org/document/9078877. |
| [20] | C.-S. Cho, W.-H. Chung, and S.-Y. Kuo, Cyber-physical security and dependability analysis of digital control systems in nuclear power plants,” IEEE Trans. Syst., Man, Cybern., vol. 46, no. 3, pp. 356–369, 2016. [Online]. Available: https://ieeexplore.ieee.org/document/7192645. |
| [21] | Henry, M.H., Layer, R.M., Snow, K.Z., & Zaret, D.R. (2009). Evaluating the risk of cyber attacks on SCADA systems via Petri net analysis with application to hazardous liquid loading operations. 2009 IEEE Conference on Technologies for Homeland Security, 607-614. |
| [22] | Zeng, R., Jiang, Y., Lin, C., & Shen, X. (2012). Dependability Analysis of Control Center Networks in Smart Grid Using Stochastic Petri Nets. IEEE Transactions on Parallel and Distributed Systems, 23, 1721-1730. |
| [23] | Kundur, Deepa & Feng, Xianyong & Liu, Shan & Zourntos, Takis & Butler-Purry, K.L.. (2010). Towards a Framework for Cyber Attack Impact Analysis of the Electric Smart Grid. 244 - 249. 10.1109/SMARTGRID.2010.5622049. |
| [24] | Liu, S., Mashayekh, S., Kundur, D., Zourntos, T., & Butler-Purry, K.L. (2012). A smart grid vulnerability analysis framework for coordinated variable structure switching attacks. 2012 IEEE Power and Energy Society General Meeting, 1-6., |
| [25] | E. E. Miciolino, G. Bernieri, F. Pascucci, and R. Setola, "Communications network analysis in a SCADA system testbed under cyber-attacks," 2015 23rd Telecommunications Forum Telfor (TELFOR), 2015, pp. 341-344, doi: 10.1109/TELFOR.2015.7377479. |
| [26] | Liberati, Francesco, Emanuele Garone, and Alessandro Di Giorgio. 2021. "Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective" Electronics 10, no. 10: 1153. https://doi.org/10.3390/electronics10101153 |
| [27] | Geeta Yadav, Kolin Paul, Architecture and security of SCADA systems: A review, International Journal of Critical Infrastructure Protection, Volume 34, 2021, 100433, ISSN 1874 5482, https://doi.org/10.1016/j.ijcip.2021.100433. (https://www.sciencedirect.com/science/article/pii/S1874548221000251). |
| [28] | Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A Survey on Cybersecurity Challenges, Detection, and Mitigation Techniques for the Smart Grid. Energies 2021, 14, 5894. https://doi.org/10.3390/en14185894. |
| [29] | Pillitteri, V.; Brewer, T. Guidelines for Smart Grid Cybersecurity, 2014-09-25; NIST Interagency/Internal Report (NISTIR); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014. |
| [30] | Yi, P.; Zhu, T.; Zhang, Q.; Wu, Y.; Li, J. A denial of service attack in advanced metering infrastructure network. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 1029–1034. |
| [31] | Bari, A.; Jiang, J.; Saad,W.; Arunita, J. Challenges in the Smart Grid Applications: An Overview. Int. J. Distrib. Sens. Netw. 2014, 1–11. |
| [32] | Gauci, A.; Michelin, S.; Salles, M. Addressing the challenge of cyber security maintenance through patch management. CIREDOpen Access Proc. J. 2017, 2017, 2599–2601. |
| [33] | Khalid, A.; Sundararajan, A.; Hernandez, A.; Sarwat, A. FACTS Approach to Address Cybersecurity Issues in Electric Vehicle Battery Systems. In Proceedings of the 2019 IEEE Technology & Engineering Management Conference (TEMSCON), Atlanta, GA, USA, 12–14 June 2019. |
| [34] | Agarkar, A.; Agrawal, H. A review and vision on authentication and privacy preservation schemes in the smart grid network. Secur. Priv. 2019, 2, e62. [CrossRef] |
| [35] | Zhang, F.; Mahler, M.; Li, Q. Flooding attacks against secure time-critical communications in the power grid. In Proceedings of the 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm), Dresden, Germany, 23–27 October 2017; pp. 449–454. [CrossRef] |
| [36] | Huseinovic, A.; Mrdovic, S.; Bicakci, K.; Uludag, S. A Taxonomy of the Emerging Denial-of-Service Attacks in the Smart Grid and Countermeasures. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20–21 November 2018; pp. 1–4. |
| [37] | Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-Service (dos) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. |
| [38] | Huseinovi´c, A.; Mrdovi´c, S.; Bicakci, K.; Uludag, S. A Survey of Denial-of-Service Attacks and Solutions in the Smart Grid. IEEE Access 2020, 8, 177447–177470. |
| [39] | Cameron, C.; Patsios, C.; Taylor, P.C.; Pourmirza, Z. Using Self-Organizing Architectures to Mitigate the Impacts of Denial-of- Service Attacks on Voltage Control Schemes. IEEE Trans. Smart Grid 2019, 10, 3010–3019. |
| [40] | Kurt, M.N.; Yilmaz, Y.; Wang, X. Real-Time Detection of Hybrid and Stealthy Cyber-Attacks in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2019, 14, 498–513. |
| [41] | Chatfield, B.; Haddad, R.J.; Chen, L. Low-Computational Complexity Intrusion Detection System for Jamming Attacks in Smart Grids. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 367–371. |
| [42] | Gai, K.; Qiu, M.; Ming, Z.; Zhao, H.; Qiu, L. Spoofing-Jamming Attack Strategy Using Optimal Power Distributions in Wireless Smart Grid Networks. IEEE Trans. Smart Grid 2017, 8, 2431–2439. |
| [43] | Ying, H.; Zhang, Y.; Han, L.; Cheng, Y.; Li, J.; Ji, X.; Xu, W. Detecting Buffer-Overflow Vulnerabilities in Smart Grid Devices via Automatic Static Analysis. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 813–817. |
| [44] | He, Y.; Mendis, G.J.; Wei, J. Real-Time Detection of False Data Injection Attacks in Smart Grid: A Deep Learning-Based Intelligent Mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. |
| [45] | Cui, L.; Qu, Y.; Gao, L.; Xie, G.; Yu, S. Detecting false data attacks using machine learning techniques in smart grid: A survey. J. Netw. Comput. Appl. 2020, 170, 102808. |
| [46] | Deng, R.; Liang, H. False Data Injection Attacks With Limited Susceptance Information and New Countermeasures in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 1619–1628. |
| [47] | Riggs, H.; Tufail, S.; Khan, M.; Parvez, I.; Sarwat, A.I. Detection of False Data Injection of PV Production. In Proceedings of the 2021 IEEE Green Technologies Conference (GreenTech), Denver, CO, USA, 7–9 April 2021; pp. 7–12. |
| [48] | Singh, V.K.; Ebrahem, H.; Govindarasu, M. Security Evaluation of Two Intrusion Detection Systems in Smart Grid SCADA Environment. In Proceedings of the 2018 North American Power Symposium (NAPS), Fargo, ND, USA, 9–11 September 2018; pp. 1–6. |
| [49] | Green, B.; Prince, D.; Busby, J.; Hutchison, D. The Impact of Social Engineering on Industrial Control System Security. In Proceedings of the First ACMWorkshop on Cyber-Physical Systems-Security and/or PrivaCy, CPS-SPC ’15, Denver, CO, USA, 16 October 2015; Association for Computing Machinery: New York, NY, USA, 2015; pp. 23–29. |
| [50] | Mrabet, Z.E.; Kaabouch, N.; Ghazi, H.E.; Ghazi, H.E. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. |
| [51] | Pour, M.M.; Anzalchi, A.; Sarwat, A. A review on cyber security issues and mitigation methods in smart grid systems. In Proceedings of the SoutheastCon 2017, Concord, NC, USA, 30 March–2 April 2017; pp. 1–4. |
| [52] | Rajendran, G.; Sathyabalu, H.V.; Sachi, M.; Devarajan, V. Cyber Security in Smart Grid: Challenges and Solutions. In Proceedings of the 2019 2nd International Conference on Power and Embedded Drive Control (ICPEDC), Chennai, India, 21–23 August 2019; pp. 546–551. |
| [53] | Shitharth, S.; Winston, D.P. A novel IDS technique to detect DDoS and sniffers in smart grid. In Proceedings of the 2016 World Conference on Futuristic Trends in Research and Innovation for Social Welfare (Startup Conclave), Coimbatore, India, 29 February–1 March 2016; pp. 1–6. |
| [54] | Pandey, R.K.; Misra, M. Cyber security threats—Smart grid infrastructure. In Proceedings of the 2016 National Power Systems Conference (NPSC), Bhubaneswar, India, 19–21 December 2016; pp. 1–6. |
| [55] | Wang, X.; Shi, D.; Wang, J.; Yu, Z.; Wang, Z. Online Identification and Data Recovery for PMU Data Manipulation Attack. IEEE Trans. Smart Grid 2019, 10, 5889–5898. |
| [56] | Wang, J.; Shi, D.; Li, Y.; Chen, J.; Ding, H.; Duan, X. Distributed Framework for Detecting PMU Data Manipulation Attacks With Deep Autoencoders. IEEE Trans. Smart Grid 2019, 10, 4401–4410. |
| [57] | Irita, T.; Namerikawa, T. Detection of replay attack on smart grid with code signal and bargaining game. In Proceedings of the 2017 American Control Conference (ACC), Seattle, WA, USA, 24–26 May 2017; pp. 2112–2117. |
| [58] | Alohali, B.; Kifayat, K.; Shi, Q.; Hurst, W. Replay Attack Impact on Advanced Metering Infrastructure (AMI). In Smart Grid Inspired Future Technologies; Hu, J., Leung, V.C.M., Yang, K., Zhang, Y., Gao, J., Yang, S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 52–59. |
| [59] | The Essential Role of Cyber Security in the Smart Grid. Available online: https://electricenergyonline.com/energy/magazine/312/article/The-Essential-Role-of-Cyber-Security-in-the-Smart-Grid-.htm (accessed on 30 July 2021). |
| [60] | Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. |
| [61] | https://github.com/sarahtattersall/PIPE |
| [62] | http://www.di.unito.it/~greatspn/index.html |
| [63] | F. Bause and P. S. Kritzinger, Stochastic Petri Nets: An Introduction to the Theory, 2nd ed. Braunschweig, Germany: Vieweg, 2002. |
| [64] | K. Yamashita, C.-W. Ten, Y. Rho, L. Wang, W. Wei, and A. F. Ginter, “Measuring systemic risk of switching attacks based on cybersecurity technologies in substations,” IEEE Trans. Power Syst., vol. 35, no. 6, pp. 4206–4219, Nov. 2020. [Online]. Available: https://ieeexplore.ieee.org/document/9078877. |


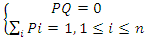
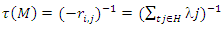
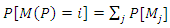
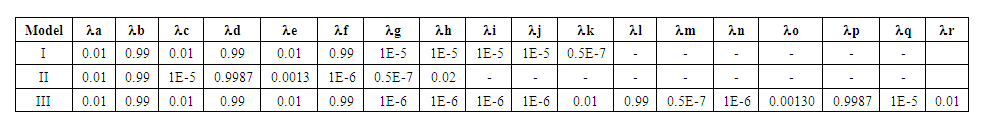
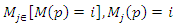 (3) Average number of tokens on a place:
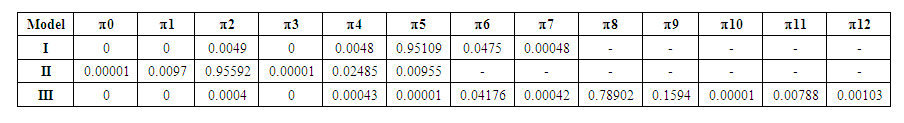
(3) Average number of tokens on a place: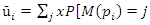
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML