-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Computer Science and Engineering
p-ISSN: 2163-1484 e-ISSN: 2163-1492
2021; 11(3): 41-48
doi:10.5923/j.computer.20211103.01
Received: Oct. 19, 2021; Accepted: Oct. 30, 2021; Published: Dec. 24, 2021

Enhanced Error Correcting Code on Information Extraction of Message from Digital Image Using Parity Error Correction
Tebepah T.1, Onuodu F. E.2, Okolai D. B.3
1Department of Computer Science, Ignatius Ajuru University, Port Harcourt, Nigeria
2Department of Computer Science, University of Port Harcourt, Port Harcourt, Postcode, Nigeria
3Department Computer Science, Niger Delta University, Nigeria
Correspondence to: Tebepah T., Department of Computer Science, Ignatius Ajuru University, Port Harcourt, Nigeria.
| Email: |  |
Copyright © 2021 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Sending hidden messages through images has a problem of delivering error messages to the recipients. One of the ways that has been used to correct these error messages is by a process called iterating embedding and extraction. In this work, an enhanced error correction code on information extraction from images using parity test has been developed and implemented. The proposed system was built on the existing iterating embedding error correction by adding an additional error check called the Parity correction code. The Object Oriented System development methodology (OOSDM) approach was used for in this project. The system was implemented using C++ and hypertext preprocessor (PHP) for the interactive interfaces. The proposed system had an error free message delivered to the recipient at a more optimal time when compared to the system that used the iterating embedding and extraction process. This system will be of relevance to Enterprises and individuals that use cloud computing for storing information.
Keywords: Parity test, Iterating embedding, Extraction
Cite this paper: Tebepah T., Onuodu F. E., Okolai D. B., Enhanced Error Correcting Code on Information Extraction of Message from Digital Image Using Parity Error Correction, Computer Science and Engineering, Vol. 11 No. 3, 2021, pp. 41-48. doi: 10.5923/j.computer.20211103.01.
Article Outline
1. Introduction
- Storing information on the cloud is a technology that has been around for decades. Large companies and individuals have got over their skepticism of storing information on the cloud. The ease of storing information on the cloud or the absence of a better alternative to cloud computing has influenced the decisions of Companies and Individuals. When companies release their information to the cloud, it is beyond them to safely guide their information [15]. The insecurity that arises adding an error check, called: the Parity correction code. The Object-Oriented System development methodology (OOSDM) approach was adopted in this project. The system utilized the C++ and hypertext preprocessor (PHP) for the interactive interfaces. The proposed system had an error-free message delivered to the recipient at a more optimal time when compared to the system that used the iterating embedding and extraction process. This system will be of relevance to Enterprises and individuals that use cloud computing for storing information. from saving information on the cloud has become a massive problem, especially in this era of cyber attacks. To cub cyber attacks, sensitive information is hidden in an image and sent over the cloud. More so, additional problems come with the extraction of the hidden message from the image. This literature proposes a system that enhances the correction of secret messages extracted from a host image using the parity correction code. There is already existing literature that dealt with a distorted extracted message using the iterating embedding procedure [2]. This article builds on this procedure by adding an error-correcting code (ECC) called parity ECC to the already existing iterating embedding and extraction procedure.
2. Literature Review
- Evsutin et al., [2] in their paper: "Algorithm of error-free information embedding into the DCT domain of digital images base on the QIM method using adaptive masking of distortion", tried to address the problem that came with error occupancies that appeared in secret messages extracted from a digital image using a cosine based algorithm. In addition, this paper showed that errors were corrected with the iterative embedding procedure. While their algorithm attempted to extract error-free secret messages from a digital image, it could not do it efficiently. Arunkumar et al. [15] proposed a robust steganographic method to secure medical images. Although the method was robust and able to give a better level of imperceptibility using SVD and DCT, They could not cover the embedding of secret messages on the medical image block based on the contrast and correlation measure.Evsutin & Kokurina [14], in their paper "embedding into digital images based on the discrete Fourier transformation", proposed a new algorithm for embedding messages into digital images using discrete Fourier transformation. Although their work addressed the distortion problem with extracted messages and gave a high-quality steno-image, they could not improve the embedding quality by including other optimisation methods.A JPEG picture that has undergone compression twice will be nonaligned, and estimating the first quantisation matrix is a problem. Yao et al. [5] attempted to address this problem in their article: “improved first quantisation matrix estimation for nonaligned double compressed JPEG images". Although they were able to achieve this in two phases: by estimating the parameters that were misaligned and estimating the quantisation step, they, however, used numerous empirical, theoretical thresholds which were of a distinct theoretical basis.Forgers can re-encode high definition (HD) videos to a lower quality video by decreasing the quantisation parameter (QP) or increasing the bit rate of the video. "Detection of fake high definition for HEVC videos based on prediction mode feature" addressed this problem [16]. The authors proposed a method to detect fake videos over highly efficient video coding (HEVC) by Prediction Mode Feature (PMF). They claimed that their method was better than the already existing method. On the other hand, their work did not cover detecting fake videos on social networks or video websites.Li et al., [6], in their paper: “Extracting Spread-Spectrum Hidden Data from Digital Media", Proposed a multicarrier iterative generalised least square algorithm (M-IGLS) that gave an error probability that was similar to techniques used to solve the extraction problem. On the other hand, their algorithm was not able to give an error-free extraction process. It was more like reinventing the wheel.Yao et al., [1], in their article "High-fidelity dual-image reversible data hiding via prediction-error shift", enhanced an already existing dual-image reversible data hiding (RDH) technology. Their experiment came out with a method they claimed was highly reliable and efficient. Although they claimed that their experiment was successful, it did not meet the requirements of a high-fidelity situation as it should.Chen et al. [3] addressed the tradeoff problem that arose from embedding a signal within a host to form a compound signal with their classes of new methods. Although their method was sustainable against attacks on copyright applications, their Quantisation Index Method (QIM) was termed “close to optimal” by the authors. Porat [7], in their article "Streaming k-mismatch with error correcting and application", presented an efficient design streaming algorithm for series of problems that required an approximate pattern matching Although they were able to achieve an efficient design for pattern matching, more efficient research on K-match with error-correcting was being made concurrently. Lugosch [8] Their thesis titled “Learning Algorithms for Error Correction” attempted to address the complexity that came with short block codes by proposing a recast of the short block code using machine learning language. They claimed that the modification proposed by the thesis improved the neural belief propagation algorithm in performance and reduced its implementation complexity.Dziech & Wassermann [9], in their paper "Application of Enhanced Hadamard Error Correcting Code in Video-Watermaking and his comparison to Reed-Solomon Code", introduced an enhanced variant of the Hadamard Error Correcting Code (EHC). The Enhanced Hadamard Error-correcting Code (EHC) was applied to video watermarking. Watermarking could not survive high video compressing. However, with the use of EHC, the watermarking was salvage after the compression process. Wootters [10], In her seminar titled “Plus Group Testing", established that repetition of the message is expensive; it cost time, power. She proffered other ways of error correction instead of message repetition. Furthermore, the seminar talk defined error-correcting codes, what they are, and how they can solve problems in communication. Although the speaker spoke extensively on error-correcting codes, she laid more emphasis on Reed Solomon's code.Ashura [11], In his article "Error Minimization in BCH Codes," proposed a coding scheme he claimed reduces complexity and increases efficient error performance compared to the frequently used scheme. The researcher used BCH to encode and decode a text message. Their suggestion for future research was to apply optimisation to the speed and device by parallel methodology.Sun et al., [12], In their review "A secure and robust approach to scalable video authentication," presented a content authentication scheme with three video transcoding methods that the authors felt can manipulate the contents of a video. The methods are used when the bit rate of the streaming is to be reduced. The methods are frame resizing, frame dropping and multi-cycle coding. They said the error-correcting codes (ECC) could handle the random errors. More so, despite the distortions and transcoding infrastructure, they claimed that their scheme ensured end-to-authentication.Jiang et al., [13], In their paper "Enhanced Error Correction via Language Processing", talked about two basic approaches for error correction. One of the approaches was the use of redundancy inside data after compression. The other approach was to add external redundancy to the data. Their article focused on the second approach and how it can enhance error correction performance. They argued that using ECC and internal redundancy are compatible because data losing redundancy due to ECC does not affect the data integrity. Jin et al., [4], in their paper "Feature extraction optimisation of JPEG steganalysis based on residual Images", proposed a novel scale adaptive algorithm for the feature extraction filter according to the JPEG factor for optimal performance. Although they got their required result, their proposed algorithm dealt with JPEG images because other picture formats exist.
3. Analysis and Materials
- This section aims to analyze the existing system and the concept design of this article. This analysis will serve as a yardstick for evaluating the proposed system.
3.1. Discrete Cosine Transform (DCT) Procedure
- The Images to be embedded are partitioned into eight by eight distinct blocks of the exact sizes, as shown in figure 3.1. Each of the eight by eight blocks is encoded with its discrete cosine transform. Before applying the DCT on the block, the values in each block are shifted by -128 to surround zero. The DCT procedure calculates the wave coefficient.
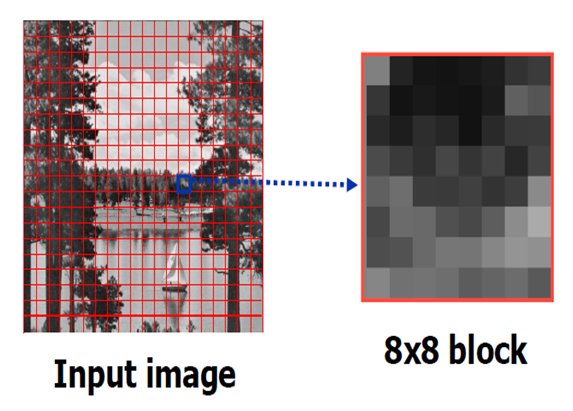 | Figure 3.1. Input image (Source: Khana, 2009) |
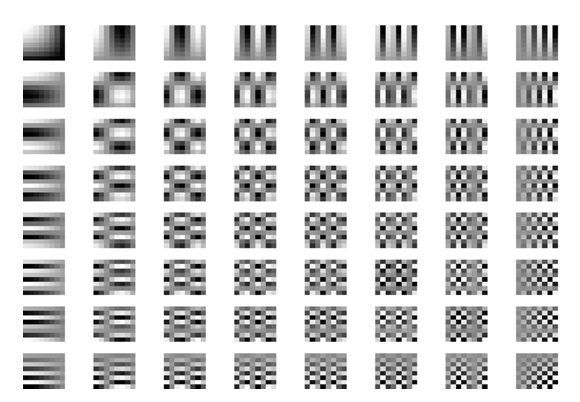 | Figure 3.2. Cosine wave (Source: http://en.wikipedia.org/wiki/JPEG) |
 | Figure 3.3. Image Shifted by -128 (Source: http://en.wikipedia.org/wiki/JPEG) |
 | Figure 3.4. DCT block (Source: http://en.wikipedia.org/wiki/JPEG) |
3.2. The Quantisation Stage
- Removing the high-frequency data is called quantisation. There is a standard Jpeg quantisation table that represents 50 per cent picture quality. The process involves dividing each coefficient from the DCT table by the corresponding value on the quantisation table and round the value to the nearest integer.
3.3. The Embedding Stage
- The message to be sent through the picture is disintegrated into workable lengths, and they are in bits. Likewise, the image is broken down into precise sizes. These broken image sizes are subjected to a frequency transform; at this point, it is ready to receive the hidden message. Note that the number of message fragments to be sent is equal to the number of broken images or blocks. The blocks are processed one after the other by adding the message into the block. An inverse frequency is applied to the processed block, and the resultant image is a stego-image pixel.The embedded phase is summarised as follows:Step 1: the picture image is decomposed into non-overlapping blocks of 8x8 pixels.Step 2: it is assumed that the message embedded in the picture is already in its bit state for simplicity.Step 3: the message is embedded into the first non-empty box of the image.The area on the block being considered for embedding is converted into bits and added to the message. Given that n = embedded area and m = message. The embedding starts at the non zero blocks of the picture. This equation that shows how m is added to n is shown below:M=m1m2….mn-1n1mn+1……m2n-2n2…..m4n-3m4n-2……..mlInput: Picture image (JPEG) with a size of 512 x 512Output: Stego Image with a size 512 x 512
4. Current System Assessment
- The Stego-image from the embedding phase passes through a data extraction test and an error checking test. There are cases where embedding does not take place. Situations like this will require that the embedding process repeatedly occurs. In addition, the extracted message may come with errors at this point. A situation like this will warrant the re-embedding process again. The message block passes through a frequency transform, and a new stego-image is produced again. The embedding process repeatedly occurs until an error-free message is obtained or not. The re-embedding process done to obtain error-free messages is called the Iterative embedding procedure. Another case might be that of a message that continuously gives an error-free extraction. This message block in this category will be termed an empty message block, and its final interpretation will be a message block that had no bits embedded in it.
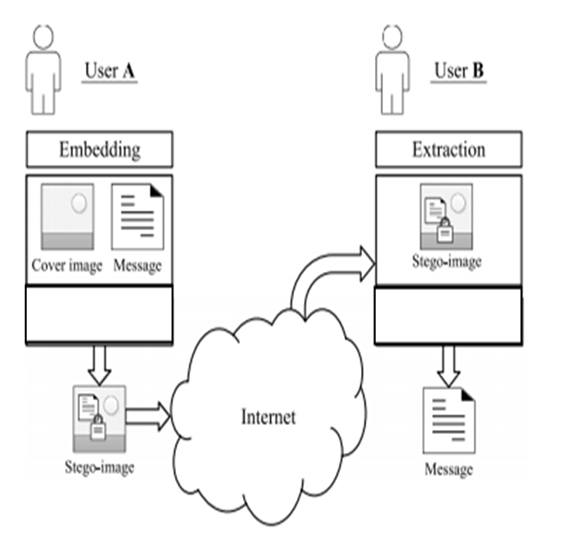 | Figure 4.1. Existing model of the extraction process of a message from a Stego-image (Source: Evsutin et al., 2021) |
4.1. Existing Algorithm
- Input: non-compressed grayscale image I; embedding area ρ; coefficient-flag coordinates in DCT block (u, v).

4.2. Advantages of Existing System
- 1) Extraction of messages from images is a comprehensive and detailed process. 2) Images devoid of messages are identified and adequately processed so as not mistakenly interpreted as images that need to be re-embedded and re-extracted.
4.3. Advantages of Existing System
- The disadvantage of the existing system are as follows:1) Excessive time delay in getting an error-free extracted message from the image through several iterating processes.2) There are instances when blocks of images delivered for further processing are without any embedded message.
5. Proposed System
- An extra bit of '0' or '1' is attached to the binary message before embedding in parity error correction. We have two kinds of parity: even parity and odd parity. If the recipient is expecting a message encoded with even parity but gets an odd number of '1s', it is an error indicator. However, if the recipient expects an error encoded in odd parity but received an even number of '1s', this is another error indicator.Assuming we have a '10011010’ message to be sent through an image. The number of ‘1s’ in this code is 4. If the message is modified using even parity, a '0' is added at the end of the coded message making it 100110100. Conversely, when the message is delivered using the odd parity, a '1' is added at the end of the code, increasing the number of '1s' to 5.The algorithm aims to embed the message in a bit into the eight by 8 DCT block into selected sub-blocks represented by coordinates x and y. Even parity is used on the message bit so that the recipient will expect a message even after extraction. The iterative process and the parity error-correcting code does the error checking. The iterative process
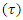 repeats itself a maximum of three times to get three different outputs which the parity error-correcting code would correct. The‘s’ variable is a counter for the message being embedded, ‘p’ is a counter for extracted error messages, it is the counter for the iteration. Its default setting is 0 whenever the algorithm starts up with another block. The D' and D'' is used to check the transition states of the process DCT block. Another essential variable is the 'α' variable which monitors the present result of the present DCT block processing. The α variable can exist in three different states: 0, 1, and 2.1) When α = 0, it means the DCT block processing has commenced.2) When α = 1, it means there are errors on the embedded message fragment. One such error is the inversion of one or more of the bits.3) When α = 2, it means an error-free image has been extracted.
repeats itself a maximum of three times to get three different outputs which the parity error-correcting code would correct. The‘s’ variable is a counter for the message being embedded, ‘p’ is a counter for extracted error messages, it is the counter for the iteration. Its default setting is 0 whenever the algorithm starts up with another block. The D' and D'' is used to check the transition states of the process DCT block. Another essential variable is the 'α' variable which monitors the present result of the present DCT block processing. The α variable can exist in three different states: 0, 1, and 2.1) When α = 0, it means the DCT block processing has commenced.2) When α = 1, it means there are errors on the embedded message fragment. One such error is the inversion of one or more of the bits.3) When α = 2, it means an error-free image has been extracted.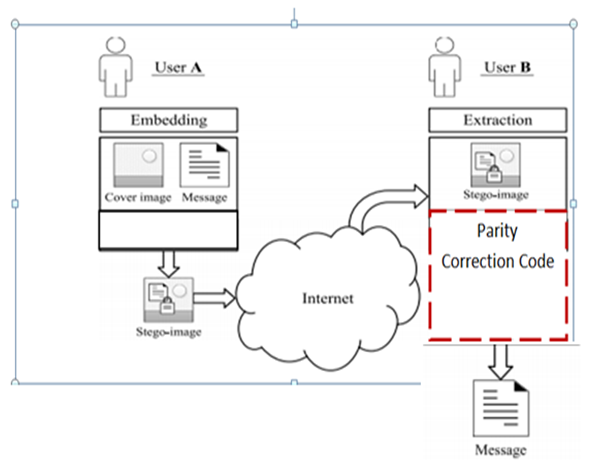 | Figure 5.1. Proposed Model for Error Correction for Extracted Message using Parity Correction Code |
5.1. Proposed Algorithm
- Input: non-compressed grayscale image I; embedding area ρ; coefficient-flag coordinates in DCT block (u, v).

5.2. Methodology
- The Object-Oriented System Development Methodology (OOSDM) was adopted to implement the steganography extraction procedure. OOSDM is robust and was used to produce the analysis model and the design model. There were four major classes: the Image class, Message class. Embed class and the Extract class. Their objects were made to interact with each other through their methods and functions. The image and the message instances were implemented in the embed class. At the point of extraction, the Image and Message instances were implemented in the extraction class. The parity correction code was implemented as a function in the Message class, where the message could pick between an even parity or an odd parity. In addition, the scope of the parity function was extended to the extraction process because it was required to check if the extracted messages complied with the chosen parity type. The rationale behind choosing OOSDM was because it supported the interactions of objects to form another composite object. Most applications presently use OOSDM. For this article, the OOSDM was applied in-network and cybersecurity. The stego-image has been through the internet to the recipient. The recipient had expected a code that can extract the message from the image. It is a bit similar to sending a zip file through the internet and the recipient unzipping the zip file.
5.3. Advantages of the Proposed System
- 1) There is a greater likelihood to get a more accurate message after extraction.2) The iteration embedding process is limited to three iterations because an additional error checking system has been included in the overall process.3) The time taken for the extraction process is reduced since the number of embedding iteration is being controlled.
6. Output and Discussion
- Figure 6.1 shows three authorised users having access to the secure stego images while the fourth person is denied access. Each authorised user can send messages in the images to the sender, and they can also retrieve the senders' hidden message through the download and extract button in figure 6.3. The proposed interface will have an additional button called Parity Check. When the message has been retrieved through the download and extract button, an additional error check will be made by clicking the Parity check button. All authorised users will have login details which will be entered into a GUI like Figure 6.2. The interface of all authorised users will look like the image in figure 6.3 after log in. unauthorised users will not be able to access this interface. Each user will have the option of downloading the image from the cloud using the download button, as seen in Figure 6.3. Furthermore, once the image is downloaded from the cloud, the message embedded in it will be extracted, and the hidden message is separated from the image, as seen in figure 6.5. The hidden messages will usually come with errors. The message will be subjected to a parity test where the error in the message is identified and corrected (Figure 6.5-6.8).
 | Figure 6.1. Authorised users and Unauthorised users of the cloud services |
 | Figure 6.2. User Interface for authorised user |
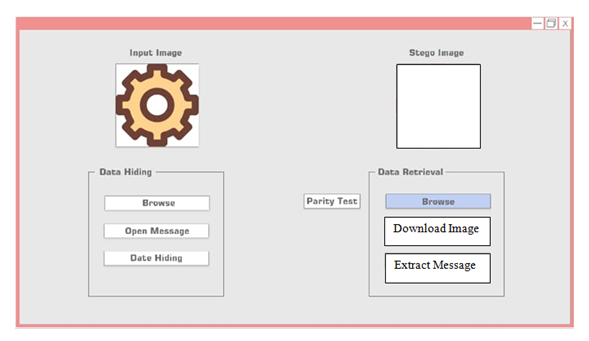 | Figure 6.3. Home Page Interface after login |
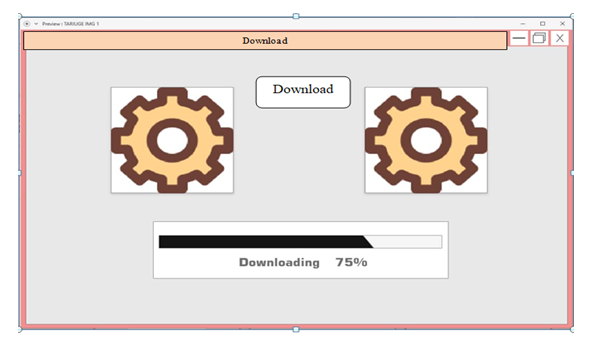 | Figure 6.4. Downloading Image from the cloud |
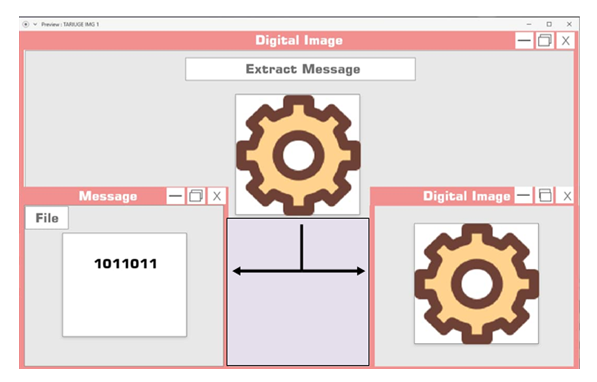 | Figure 6.5. Extract message from the image |
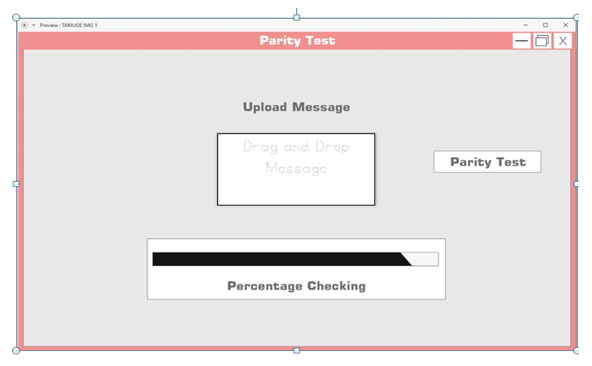 | Figure 6.6. Parity Test |
 | Figure 6.7. Parity Test completed, the corrected message will be accessed through the 'View Message' button |
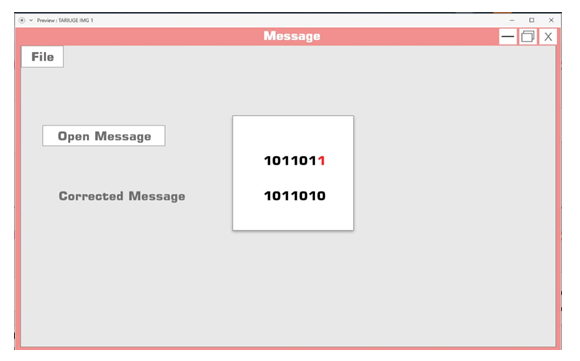 | Figure 6.8. Corrected message |
7. Conclusions
- In this paper, we looked into the entire process of hiding a message in an image using a discrete cosine transform. The embedding procedure was implemented by using the Quantisation index modulation (QIM). The iterating embedding procedure was used to extract the message from the image to achieve an error-free message. The author added an error-correcting measure to the iterating embedding procedure in the form of parity correcting codes. There are tones of error-correcting codes in the literature. Researchers have shown that some of the error-correcting codes are more efficient than the Parity ECC. Futuristically researchers may want to use these available ECC methods to eradicate errors from extracted messages in digital images. In addition, this article did not cover the security needed in transferring hidden messages over the internet.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML