-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Computer Science and Engineering
p-ISSN: 2163-1484 e-ISSN: 2163-1492
2017; 7(1): 1-11
doi:10.5923/j.computer.20170701.01

Access Control of Medical Images using Elliptic Curve Cryptography through Effective Multi-Key Management in a Mobile Multicasting Environment
Tmkk Jinasena1, Rgn Meegama1, Rb Marasinghe2
1Department of Computer Science, University of Sri Jayewardenepura, Sri Lanka
2Department of Medical Education and Health Sciences, University of Sri Jayewardenepura, Sri Lanka
Correspondence to: Tmkk Jinasena, Department of Computer Science, University of Sri Jayewardenepura, Sri Lanka.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Access control is so vital in eHealth, because compromised sensitive medical data often leads to severe consequences for both patients and health workers, resulting in financial losses or even patient death. In this paper, we propose a technique to implement a dynamic and flexible access control mechanism to ensure present access rights of sensitive medical data in a collaborative medical discussion in a mobile environment. Initially, a symmetric and public key encryption using elliptic curve cryptography is used to encrypt a user session. At this stage, the elliptic curve is defined in a prime finite field with the characteristic of p where p is a prime and p > 3. Curve parameters a and b are carefully chosen to avoid vulnerable curves. Subsequently, unique public and private key pairs are generated for all the users in the session. Results show the importance of having optimal elliptic curve implementations for mobile usage.
Keywords: Access Control, Elliptic Curves, Cryptography, Privacy, eHealth
Cite this paper: Tmkk Jinasena, Rgn Meegama, Rb Marasinghe, Access Control of Medical Images using Elliptic Curve Cryptography through Effective Multi-Key Management in a Mobile Multicasting Environment, Computer Science and Engineering, Vol. 7 No. 1, 2017, pp. 1-11. doi: 10.5923/j.computer.20170701.01.
Article Outline
1. Introduction
- Digital content access control is one of the key concerns in computer security today, and it is more important than ever before. A huge amount of digital data is constantly flowing through the internet, mobile networks, and cable and satellite televisions, and electronic medical data exchanged among large groups through public networks, especially in mobile environments, is especially vulnerable. In most cases, it is necessary to protect data from unauthorized and inappropriate access and changes by defining what information users can view and modify. Access criteria are generally associated with roles, groups, locations, or times. However, there are three main types of access control methods: Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Non-Discretionary (Role-Based) Access Control (RBAC) [1]. Furthermore, access control methods are classified as military or commercial based on their usage. MAC is based on Bell-LaPadula’s 1973 multilevel security model, which is more concerned with confidentiality than integrity. In MAC, security policies are defined regardless of user operations. Thus, it is more suitable for military applications. On the other hand, DAC is the most used access control method. It is used in many operating systems, including UNIX, Windows 2000, and FreeBSD. The main disadvantage of DAC is the fact that its three-dimensional access control matrix has O(n2) growth. Finally, RBAC proposed by Ferraiolo and Kuhn in 1992 [1] blends MAC and DAC. It can be customized for individual applications regardless of policies [2-6].In our case, we need to facilitate collaborative medical discussion over mobile devices where sensitive medical data, possibly large content, is shared through public networks while guaranteeing its C-I-A (Confidentiality, Integrity, and Availability) properties [3]. Moreover, we need to have a dynamic and flexible access control method to ensure the right access by the right user at the right time. However, there are no fixed access levels or roles for users. The one who initiates the communication becomes the coordinator of that session. Thus, s/he defines the access levels of the subordinates of the session. In another session, s/he can be a subordinate with low access privileges. Therefore, access control needs to be provided through the content. Moreover, we need to multicast the same content for multiple users with different access levels.
2. Background
- Symmetric key cryptography is faster than asymmetric key cryptography mainly due to its small key sizes. However, it can only guarantee the confidentiality of the data. In a distributive environment, there are many security concerns, such as key distribution, authentication, authorization, integrity, and non-repudiation. To address such concerns, public key cryptography should be used. Therefore, in such scenarios, a combination of both symmetric and asymmetric key cryptography is being used to reap the benefits of both.
2.1. AES Cryptography
- The Advanced Encryption Standard (AES), originally known as Rijndael, was introduced by Joan Daemen and Vincent Rijmen in 1998, and it was recommended by the National Institute of Standards and Technology (NIST) in late 2001 [7]. The AES is a symmetric-key block cipher with a fixed block size of 128 bits, and it uses keys of any multiples of 32 bits between 128 and 256. It is based on both substitution and permutation, and it is fast in both software and hardware implementations. The AES operates on a 4x4 column-major order matrix and has four main operations: AddRoundKey, SubBytes, ShiftRows, and MixColumns [8]. It has 10 to 14 cycles for each block based on its key size [9]. The SubBytes phase is a non-linear phase where it replaces each byte with a value in an 8-bit substitution box (s-box). In order to ensure good linear properties and avoid simple algebraic attacks, the s-box is constructed using the multiplicative inverse over Galois Field GF (28). The time complexity of the Biclique attack, which is faster than the full brute force attack, is O(2n). Thus, given the present computational power, it is virtually unbreakable [10-13].
2.2. RSA Cryptography
- Cryptosystems usually increase their key sizes to obtain higher security, and they can be as big as 300 digits or even bigger. Thus, it has become problematic to store them in small devices safely in public-key cryptography. In 1977, Ron Rivest, Adi Shamir, and Leonard Adleman introduced a public-key encryption method named RSA based on a mathematical problem called factorizing large integers where its time complexity is polynomial [14]. Currently, it is the public-key encryption method recommended by the NIST. However, it is being threatened by the rapid growth in computing power.In 1999, a polynomial time algorithm for integer factorization and computation of discrete logarithms on quantum computers was discovered by Peter Shor [15]. This meant that once the quantum computers reached the 1000 Q-bit range, RSA could easily be broken. Recently, a few alternative approaches have emerged. Among them, Elliptic Curve Cryptography (ECC) has been promising due to its unique capabilities [6, 16-19].
2.3. ECC
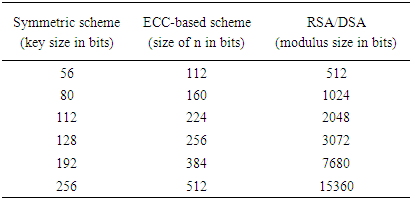
- The new paradigm of public-key encryption using ECC was suggested independently by Neal Koblitz and Victor S. Miller in 1985 [14]. The main advantage of the ECC over RSA is its ability to provide equal security for significantly smaller key sizes. Thus, it provides the most security per bit of any known public-key scheme. Table 1 shows the equivalent security key sizes of ECC, RSA, and symmetric key cryptography. Although the computational overhead of both RSA and ECC grows as O (N3), where N is the key length in bits, ECC is more efficient and stronger than RSA. In fact, it is faster than all the other methods. Furthermore, it needs less computational power and less space. Hence, it is ideal for limited bandwidth communications, wireless devices, and PC cards [20-23].
|
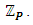 The order of
The order of 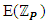 is defined as
is defined as 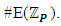 According to Hasse’s theorem,
According to Hasse’s theorem, 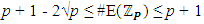
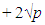 [24]. The best known attack for ECC so far is Pollard’s rho attack, where it runs in exponential time, which is
[24]. The best known attack for ECC so far is Pollard’s rho attack, where it runs in exponential time, which is 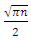 [25]. The time complexity of RSA is sub-exponential, whereas it is exponential for ECC. Figure 1 shows the variation of the time complexities against the key sizes.
[25]. The time complexity of RSA is sub-exponential, whereas it is exponential for ECC. Figure 1 shows the variation of the time complexities against the key sizes. 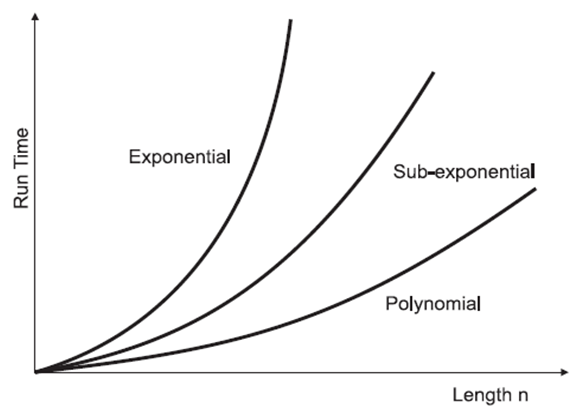 | Figure 1. Time complexity vs key size |
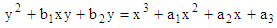 ECs over real numbers use a special class of ECs of the form
ECs over real numbers use a special class of ECs of the form 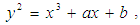 also known as the Weierstrass equation of characteristic [24]. The discriminant of the polynomial
also known as the Weierstrass equation of characteristic [24]. The discriminant of the polynomial 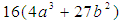 should not be zero in order to possess three distinct roots for a given EC.Furthermore, singular ECs are not suitable for cryptography, since they can be easily cracked due to the fact that they are isomorphic to either addition or multiplication. Super-singular ECs should also be avoided, since they are vulnerable to MOV attack. However, we cannot use real numbers for encryption, since they are prone to round-off error. Thus, we restrict the values of x and y to a prime finite field
should not be zero in order to possess three distinct roots for a given EC.Furthermore, singular ECs are not suitable for cryptography, since they can be easily cracked due to the fact that they are isomorphic to either addition or multiplication. Super-singular ECs should also be avoided, since they are vulnerable to MOV attack. However, we cannot use real numbers for encryption, since they are prone to round-off error. Thus, we restrict the values of x and y to a prime finite field 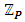 . Such curves are denoted by the form of
. Such curves are denoted by the form of 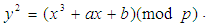 Here, p is a prime, and p > 3. P is also known as the characteristic of the field. Further, the curve parameters
Here, p is a prime, and p > 3. P is also known as the characteristic of the field. Further, the curve parameters 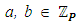 should be carefully chosen to satisfy the condition 4a3 + 27b2 ≠ 0 (mod p) [26]. However, when a finite field is chosen, pretty curves and lines are not applicable, yet the underlying algebra works as usual. When the curve is defined on a finite field
should be carefully chosen to satisfy the condition 4a3 + 27b2 ≠ 0 (mod p) [26]. However, when a finite field is chosen, pretty curves and lines are not applicable, yet the underlying algebra works as usual. When the curve is defined on a finite field 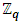 with q elements, the number of points on the curve N, including the additive identity element O, is bounded by
with q elements, the number of points on the curve N, including the additive identity element O, is bounded by 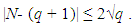
2.3.1. Point Addition
- The point addition in ECs has nothing to do with the conventional arithmetical addition. It is the group operator for the points on an EC. Since it is commutative, EC forms an Abelian group. Let E be an EC over a field K, given by an equation
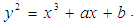 We begin by defining a binary operation + on E(K). For a given P and Q ∈ E(K), the following equations can be used to compute a third point
We begin by defining a binary operation + on E(K). For a given P and Q ∈ E(K), the following equations can be used to compute a third point 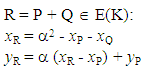 where
where 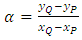 The point addition involves five subtraction operations, one addition, three modular multiplications, and one inversion operation. As shown in Figure 2, the EC has three adding cases. Case (a) shows the addition of two distinct points P and Q on the curve, whereas case (b) shows the adding of the point to itself. Finally, case (c) shows the adding of a point’s mirror or complement to itself in order to obtain the resulting point O at infinity.
The point addition involves five subtraction operations, one addition, three modular multiplications, and one inversion operation. As shown in Figure 2, the EC has three adding cases. Case (a) shows the addition of two distinct points P and Q on the curve, whereas case (b) shows the adding of the point to itself. Finally, case (c) shows the adding of a point’s mirror or complement to itself in order to obtain the resulting point O at infinity.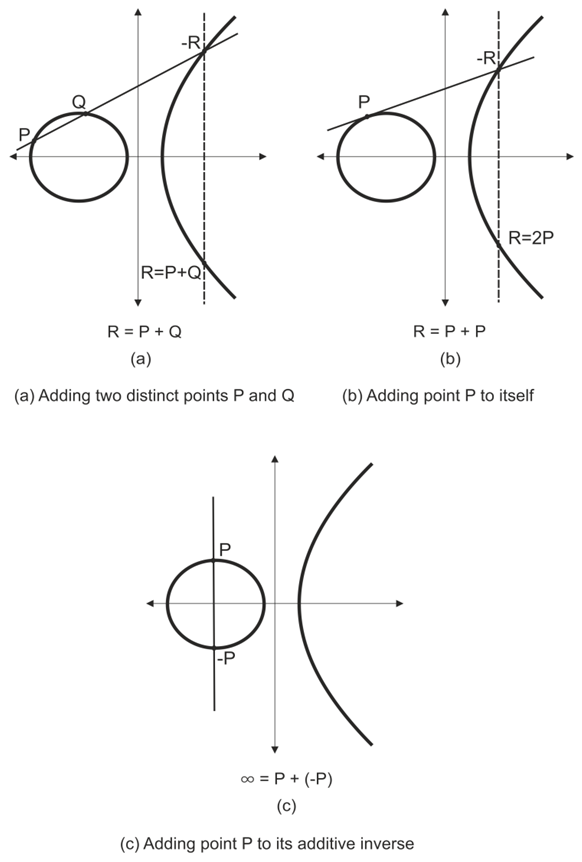 | Figure 2. Three adding cases in an EC |
2.3.2. Point Doubling
- Point doubling or scalar multiplication in ECs also does not represent conventional arithmetical multiplication. As we have seen above, if we extend the point addition to double a point P ∈ E(K), we can obtain a point R ∈ E(K) such that R = P + P = 2P by using the following equations:
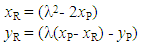 where
where 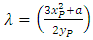 In ECC, scalar multiplication and inversion are very time-consuming operations. However, ECs have properties that enable the efficient implementation of scalar multiplication. For example, rather than computing 126P with 126 additions as follows:126P = P + P . . . + P.It can be calculated by six doublings and five additions as follows: 126P = 2(2(2(2(2(2P + P) + P) + P) + P) + P).Further, the inverse addition or the subtraction of ECs is easy to compute. This can be further reduced to seven doublings and one subtraction as follows: 126P = 2(2(2(2(2(2(2P))))) - P).Figure 3 shows the case of such consecutive point doubling in an EC. However, this scalar multiplication is the key to ECC. If we add point P, n times, a general case can be written as R = n.P ∈ E(K). This operation is elegant, as it is not easy to find the number n even though we know the points P, R, and the curve. Thus, n can be used as a secret or private key, whereas R together with P and the curve becomes its unique public key.
In ECC, scalar multiplication and inversion are very time-consuming operations. However, ECs have properties that enable the efficient implementation of scalar multiplication. For example, rather than computing 126P with 126 additions as follows:126P = P + P . . . + P.It can be calculated by six doublings and five additions as follows: 126P = 2(2(2(2(2(2P + P) + P) + P) + P) + P).Further, the inverse addition or the subtraction of ECs is easy to compute. This can be further reduced to seven doublings and one subtraction as follows: 126P = 2(2(2(2(2(2(2P))))) - P).Figure 3 shows the case of such consecutive point doubling in an EC. However, this scalar multiplication is the key to ECC. If we add point P, n times, a general case can be written as R = n.P ∈ E(K). This operation is elegant, as it is not easy to find the number n even though we know the points P, R, and the curve. Thus, n can be used as a secret or private key, whereas R together with P and the curve becomes its unique public key.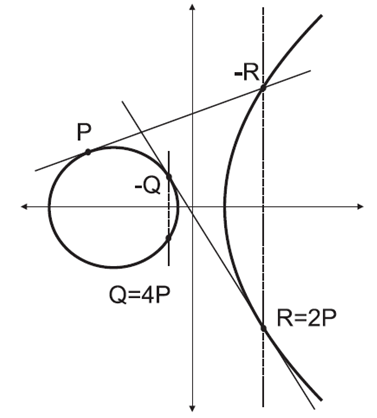 | Figure 3. Doubling point P repeatedly to find 4P |
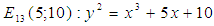 . We obtain quadratic residues
. We obtain quadratic residues 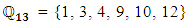 from the reduced set of residues
from the reduced set of residues  This means that the valid points of the EC are as follows:E13(5; 10) = [(0 : 1 : 0); (0 : 6 : 1); (0 : 7 : 1); (1 : 4 : 1); (1 : 9 : 1); (3 : 0 : 1); (4 : 4 : 1); (4 : 9 : 1); (5 : 2 : 1); (5 : 11 : 1); (6 : 3 : 1); (6 : 10 : 1); (8 : 4 : 1); (8 : 9 : 1); (9 : 2 : 1); (9 : 11 : 1); (12 : 2 : 1); (12 : 11 : 1)]The following commands can be used in SAGE to generate the valid points of
This means that the valid points of the EC are as follows:E13(5; 10) = [(0 : 1 : 0); (0 : 6 : 1); (0 : 7 : 1); (1 : 4 : 1); (1 : 9 : 1); (3 : 0 : 1); (4 : 4 : 1); (4 : 9 : 1); (5 : 2 : 1); (5 : 11 : 1); (6 : 3 : 1); (6 : 10 : 1); (8 : 4 : 1); (8 : 9 : 1); (9 : 2 : 1); (9 : 11 : 1); (12 : 2 : 1); (12 : 11 : 1)]The following commands can be used in SAGE to generate the valid points of 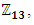 as shown in Figure 4:
as shown in Figure 4: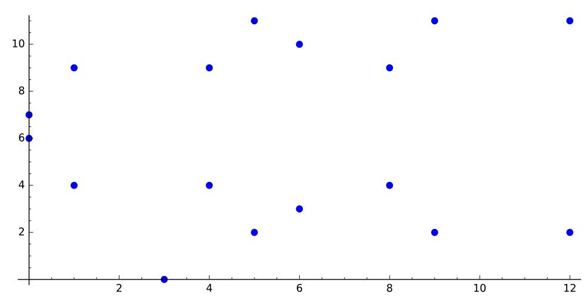 | Figure 4. Valid points of Z13 |
2.3.3. Elliptic Curve Diffie-Hellman (ECDH) Key Exchange
- The DH key-agreement scheme was proposed by Whitfield Diffie and Martin Hellman in 1976 [27]. The DH scheme is used to exchange secret keys between two or more parties. However, it is an interactive way of exchanging keys where the sender and the receiver need to be in the process at the same time. ECDH is the EC version of the DH scheme. If (PA, SA) and (PB, SB) are public and private keys of users UA and UB, respectively, where PA and PB are points on an EC, UA and UB can compute a secret key K as KA = SA × PB by UA and KB = SB × PA by UB [28, 29, 30]. According to the properties of ECDH,
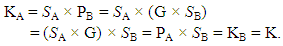
2.3.4. ElGamal Encryption using ECC
- ElGamal encryption was proposed by Taher ElGamal in 1984 [31]. He was the first person to propose the idea of using a DLP for public-key cryptography. However, ElGamal encryption is a passive way of exchanging keys. In other words, the sender can encrypt the data off-line, and the receiver can decrypt it later. Assume that user UB wants to send a secret key to user UA; UA chooses a random point α∈EC(a, b) and multiplies it by a random number SA where 1≤SA≤n-1 to find β such that β=α × SA. S/he lets α and β be publicly known to everybody and secretly keeps SA as his/her private key. UB chooses a random point γ∈EC(a, b) and calculates C1 such that C1 = γ × α and C2 such that C2 = K + γ × β where K is the secret key s/he wants to share with UA. UB sends the message (C1, C2) to UA, and UA decrypts the message and gets the key K as follows [32, 33, 34].K = C2 – SA × C1.
2.3.5. Elliptic Curve Digital Signature Algorithm (ECDSA)
- ECDSA is a variation of the digital signature algorithm that consists of two parts of the signature: sign1 and sign2. Let H be the hash value of the message, which is an integer, and k is a random number, sign1 = (k × G)x mod p. That means sign1 only keeps the x-coordinate modulo p of k × G. If sign1 = 0, then try another k. Now, sign2 = k-1(H + SA. sign1) mod p where k-1 is the multiplicative inverse of k modulo p, which is obtained by the extended Euclidean algorithm, and SA is the private key of user A. When user B receives (sign1, sign2) along with the original document, s/he can compute the w = sign2-1 mod p, u1 = H.w mod p, u2 = sign1.w mod p, and a point on the curve (x, y) = u1 × G + u2 × PA where PA is the public-key of user A. Now, s/he can verify the integrity of the message as well as the sender by comparing sign1 ≡ x mod p. This method has been used by Bitcoin to verify whether the digital coins are spent by the right users. However, it is necessary to use a different k for each signature. For example, if the same k is used for two signs (sign1, sign2) and (sign1’, sign2’), k can be computed as sign2 – sign2’ = k-1(H–H’). Finally, the secret key SA can be computed by using the equation sign2 = k-1(H – SA.sign1). This technique was used to crack the Sony PlayStation 3 (PS3) in 2010 [35]. Moreover, it was used in an incident where the users of Android Bitcoin Wallet lost money due to faulty random number generators in August 2013 [36, 37, 38, 39].
2.3.6. Elliptic Curve Integrated Encryption Scheme (ECIES)
- ECs cannot be directly used for encryption. Thus, in practice, they are combined with symmetric key algorithms and used as a hybrid scheme. In such cases, the EC is only used to encrypt the symmetric key that was used to encrypt the original data. ECIES is a combination of the Key Encapsulation Mechanism (KEM) and the Data Encapsulation Mechanism (DEM). The KEM is responsible for mapping a symmetric key to a point in the EC. The task of the DEM is to encrypt the plain text using the above symmetric key and authenticate the ciphertext [8, 23, 40].
2.3.7. Windows Media Digital Rights Management (WM-DRM)
- Digital Rights Management (DRM) is associated with technologies and algorithms that help a content provider to enforce limitations, such as who can use the media content provided by them and in what way. ECC has been used for DRM for a while.The Windows Media framework is a DRM that allows third-party vendors to create and distribute revenue-generating content. In WM-DRM, they use an EC-based encryption method to protect the access rights of their content, such as audio and video. It was a proprietary algorithm, and from 1999 to 2003, they released three versions of it. However, all three versions were compromised long ago. Other providers, such as Apple and Sony, have their own methods as well. According to Kerckhoffs’s principle, the secrecy of a cryptosystem should only depend on the key [41]. However, all these systems have been implementing security by hiding their algorithms [42, 43, 44, 45, 46].
2.3.8. Sony PlayStation
- Sony’s PS3 console does not allow users to run codes that are not signed by one of its trusted parties. In other words, the developer first has to give his source code to some trusted party and get his signature on the binary. The Sony bootloader checks the signature before it executes the code. Sony has used ECC to implement its security mechanism where a secret key pair within the system is used to communicate with the license server. As we have explained above, the weakness of not avoiding the same random number twice enabled hackers to break it easily and pass their keys to others [35, 47].
3. Methodology
3.1. Symmetric Key Encryption
- Although symmetric key encryption is faster, it requires a large number of keys in a multi-user environment. In particular, when the same content needs to be transferred to multiple users with different accessibility levels, payloads have to be encrypted for each user separately, which is very inefficient and time consuming. Therefore, in our proposed method, we first encrypt the content using a symmetric key and then encrypt the header separately for each user. The symmetric key encryption method is defined as ∏(E, D) where c←Eki(p) and p←Dki(c). Here, p represents the plain text, c represents the ciphertext, and ki represents the symmetric session key of the ith session. Further, Eki and Dki are the encryption and decryption algorithms, respectively, under the symmetric key ki such that Dki (Eki (M)) = M. The AES is a well-tested, robust, and relatively efficient algorithm. As a result, we have selected it as our symmetric key algorithm. However, under the present hardware capabilities, its efficiency is insufficient for encrypting real-time video, even for videos of Phase Alternating Line (PAL) quality [13, 48].
3.2. Public-key Encryption
- In this research, apart from ensuring confidentiality, we need to provide different access levels for each user separately. That is, for the same content, one user can edit it, whereas another can only read it. On the other hand, regarding another content, rights can be the opposite. Because of this dynamic nature, traditional role-based access control would not be an effective method.In our approach, we define a public-key encryption method as follows:
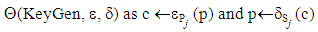 Where ε and δ are the encryption and decryption algorithms, respectively, such that δSi (εPi (M)) = M and δPi (εSi (M)) = M to encrypt the secret symmetric key of the content.ECC over a prime finite field has been chosen as the public-key encryption method. First, we define a prime finite field
Where ε and δ are the encryption and decryption algorithms, respectively, such that δSi (εPi (M)) = M and δPi (εSi (M)) = M to encrypt the secret symmetric key of the content.ECC over a prime finite field has been chosen as the public-key encryption method. First, we define a prime finite field 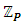 to generate unique public and private key pairs (Pi, Si) for all the users Us = U1, U2, . . Ui. . . Un in the system. Next, we define a base point or the generator G of the field, such that n × G = O for a large n. The EC, prime finite fields
to generate unique public and private key pairs (Pi, Si) for all the users Us = U1, U2, . . Ui. . . Un in the system. Next, we define a base point or the generator G of the field, such that n × G = O for a large n. The EC, prime finite fields 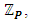 and the base point G are publicly known to everybody in the system. Thus, each user Ui can choose a random number 1< k <(n-1) and multiply G, k times to get another point R in the curve such that R = k × G. This k becomes his/her private key Si, whereas R, together with G, and EC become his public key Pi.There are some vulnerable curves. Thus, the curve parameters p, a, and b should be chosen to define a suitable EC with higher robustness. If so, according to the properties of ECC, it would be difficult for an attacker to compute a user’s private key even s/he knows all the other information. However, in our first approach, we define different public and private key pairs {(Pi1, Si1), . . (Pij, Sij)} for the same user Ui for his/her different accessibility levels Li = { L i1, L i2, . . , L ij }. In other words, if user UA wants to send read-only content to user UB, UA uses UB’s read-only public key PBread-only to encrypt the header of the document or the symmetric key. Hence, user UB has to use his read-only private key SBread-only to get the symmetric key in order to open the document. Because we use our own application to view the content, decryption happens within the application. Therefore, user UB will not be able to see the decrypted symmetric key.However, managing a large number of key pairs for a single user is the biggest problem in this approach. Thus, we move to our second approach, which is defining the access-level key pairs associated to the master key pair. That means the application itself can generate a relevant access-level key pair once the user gives his/her master key. For example, in a public network, UB can compute UA’s read-only private key using UA’s master key as PAread-only = PAmaster× Lread-only where Lread-only is a constant for all users. On the other hand, UA can compute his/her read-only private key as SAread-only= SAmaster + Lread-only.As a result, it is sufficient for a user to worry about managing a single key pair. In both approaches above, another issue is overlapping a user’s accessibility key with another’s master or access-level keys. To avoid such scenarios, two methods have been applied. One is to use a large key space with a high-order n to reduce the possibility of overlapping keys. The other is to use two key spaces ψ and
and the base point G are publicly known to everybody in the system. Thus, each user Ui can choose a random number 1< k <(n-1) and multiply G, k times to get another point R in the curve such that R = k × G. This k becomes his/her private key Si, whereas R, together with G, and EC become his public key Pi.There are some vulnerable curves. Thus, the curve parameters p, a, and b should be chosen to define a suitable EC with higher robustness. If so, according to the properties of ECC, it would be difficult for an attacker to compute a user’s private key even s/he knows all the other information. However, in our first approach, we define different public and private key pairs {(Pi1, Si1), . . (Pij, Sij)} for the same user Ui for his/her different accessibility levels Li = { L i1, L i2, . . , L ij }. In other words, if user UA wants to send read-only content to user UB, UA uses UB’s read-only public key PBread-only to encrypt the header of the document or the symmetric key. Hence, user UB has to use his read-only private key SBread-only to get the symmetric key in order to open the document. Because we use our own application to view the content, decryption happens within the application. Therefore, user UB will not be able to see the decrypted symmetric key.However, managing a large number of key pairs for a single user is the biggest problem in this approach. Thus, we move to our second approach, which is defining the access-level key pairs associated to the master key pair. That means the application itself can generate a relevant access-level key pair once the user gives his/her master key. For example, in a public network, UB can compute UA’s read-only private key using UA’s master key as PAread-only = PAmaster× Lread-only where Lread-only is a constant for all users. On the other hand, UA can compute his/her read-only private key as SAread-only= SAmaster + Lread-only.As a result, it is sufficient for a user to worry about managing a single key pair. In both approaches above, another issue is overlapping a user’s accessibility key with another’s master or access-level keys. To avoid such scenarios, two methods have been applied. One is to use a large key space with a high-order n to reduce the possibility of overlapping keys. The other is to use two key spaces ψ and 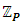 for master keys and access-level keys separately. Because we need to use the same master key to compute access-level keys, the master key space ψ is defined in a subfield of the original field
for master keys and access-level keys separately. Because we need to use the same master key to compute access-level keys, the master key space ψ is defined in a subfield of the original field 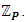 However, in our second approach, there is a fixed relationship between a user’s master keys and his/her access-level keys. This gives more opportunities for an attacker to find one of his/her keys, which would thus compromise all of his/her keys.In our third approach, we compute access-level keys in a random manner rather than a fixed association. This results in a different access-level key even for the same access level of the same user. For this, we used an extended version of the ElGamal encryption algorithm over the EC. UA uses UB’s public key to send a secret message X to UB where X is another point on the curve. For example, if UA wants to send a read-only key to UB, UA selects a random number k and computes C1 = G × k. Then, UA computes C2 = Xread-only + (k + Lread-only) × PBMaster. Subsequently, s/he sends (C1, C2) to UB where UB finds the secret point Xread-only as in equation 1.
However, in our second approach, there is a fixed relationship between a user’s master keys and his/her access-level keys. This gives more opportunities for an attacker to find one of his/her keys, which would thus compromise all of his/her keys.In our third approach, we compute access-level keys in a random manner rather than a fixed association. This results in a different access-level key even for the same access level of the same user. For this, we used an extended version of the ElGamal encryption algorithm over the EC. UA uses UB’s public key to send a secret message X to UB where X is another point on the curve. For example, if UA wants to send a read-only key to UB, UA selects a random number k and computes C1 = G × k. Then, UA computes C2 = Xread-only + (k + Lread-only) × PBMaster. Subsequently, s/he sends (C1, C2) to UB where UB finds the secret point Xread-only as in equation 1.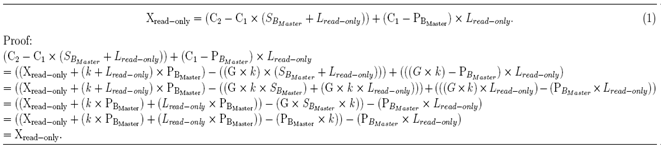 Though we still use that fixed-number Lread-only, Xread-only becomes a one-time key due to the random number k.Assume that UA wants to send the symmetric key X to UB under read-only permission. Consider the above E13(5, 10) as our EC and take G = (5, 2) ∈ E13(5, 10). Further, take the private keys of UA and UB as SA = 5 and SB = 10, respectively, by making their public keys PAMaster= (8, 9) ∈ E13(5, 10) and PBMaster = (6,10) ∈ E13(5, 10). Moreover, let Lread-only = 3 and the symmetric key X maps to the point Xread-only = (4, 4) ∈ E13(5, 10).Now, take 7 as the random number k between 1 and 17 and compute C1 = G × k = (5, 2) × 7 = (1, 9) ∈ E13(5, 10).Then compute C2 = (4, 4) + (7 + 3) × (6, 10) = (12, 11) ∈ E13(5, 10). Once UB receives (C1, C2) and Lread-only, s/he finds Xread-only = ((12, 11) – (1, 9) + (10 + 3)) + ((1, 9) – (6, 10)) × 3 = (4, 4) ∈ E13(5, 10). However, this is only for a single user pair. Our fourth attempt is to extend this to a multicasting environment to avoid separate transmission for its users. Therefore, if the same content is shared with multiple users under different access rights, a single multi-casting can be used. However, this is simply done by concatenating multiple secret key encryptions to the header. Each encrypted field in the header can have a specific access right Li regarding a specific user Ui. Finally, the application is responsible for implementing the required access control corresponding to the Li where i represents the access rights, such as read-only, save, edit, etc. In other words, if the UA wants to send an image for UB with read-only permissions, UC with save permissions, and UD with edit permissions, UA first needs to encrypt the image using AES symmetric key encryption. Then UA needs to encrypt they AES key and IV using each receivers public key Pi and his/her access level Li. For example, PB with Lread-only, PC with Lsave, and PD with Ledit. Structure of one such encrypted header is shown in the bottom diagram of the Figure 5. Next, these individual headers will concatenate as shown in the above diagram of the Figure 5. Finally find the digest of the whole message and sign using UA’s private key. Once UA multicast this to all the users, each user can verify the sender and the integrity of the message using message signature and the digest. Moreover, each can get their header and decrypt it. Because, the header has encrypted using the respective user’s public key, only that user will be able to decrypt it. Finally, the mobile application’s responsibility is to execute the received access rights for that user. For example, UA’s app does not allow UA to edit or save this image, whereas UB can save the same image. Neither users nor apps have fixed access roles in the system. Access permission comes with the content and app dynamically adjusts to it.
Though we still use that fixed-number Lread-only, Xread-only becomes a one-time key due to the random number k.Assume that UA wants to send the symmetric key X to UB under read-only permission. Consider the above E13(5, 10) as our EC and take G = (5, 2) ∈ E13(5, 10). Further, take the private keys of UA and UB as SA = 5 and SB = 10, respectively, by making their public keys PAMaster= (8, 9) ∈ E13(5, 10) and PBMaster = (6,10) ∈ E13(5, 10). Moreover, let Lread-only = 3 and the symmetric key X maps to the point Xread-only = (4, 4) ∈ E13(5, 10).Now, take 7 as the random number k between 1 and 17 and compute C1 = G × k = (5, 2) × 7 = (1, 9) ∈ E13(5, 10).Then compute C2 = (4, 4) + (7 + 3) × (6, 10) = (12, 11) ∈ E13(5, 10). Once UB receives (C1, C2) and Lread-only, s/he finds Xread-only = ((12, 11) – (1, 9) + (10 + 3)) + ((1, 9) – (6, 10)) × 3 = (4, 4) ∈ E13(5, 10). However, this is only for a single user pair. Our fourth attempt is to extend this to a multicasting environment to avoid separate transmission for its users. Therefore, if the same content is shared with multiple users under different access rights, a single multi-casting can be used. However, this is simply done by concatenating multiple secret key encryptions to the header. Each encrypted field in the header can have a specific access right Li regarding a specific user Ui. Finally, the application is responsible for implementing the required access control corresponding to the Li where i represents the access rights, such as read-only, save, edit, etc. In other words, if the UA wants to send an image for UB with read-only permissions, UC with save permissions, and UD with edit permissions, UA first needs to encrypt the image using AES symmetric key encryption. Then UA needs to encrypt they AES key and IV using each receivers public key Pi and his/her access level Li. For example, PB with Lread-only, PC with Lsave, and PD with Ledit. Structure of one such encrypted header is shown in the bottom diagram of the Figure 5. Next, these individual headers will concatenate as shown in the above diagram of the Figure 5. Finally find the digest of the whole message and sign using UA’s private key. Once UA multicast this to all the users, each user can verify the sender and the integrity of the message using message signature and the digest. Moreover, each can get their header and decrypt it. Because, the header has encrypted using the respective user’s public key, only that user will be able to decrypt it. Finally, the mobile application’s responsibility is to execute the received access rights for that user. For example, UA’s app does not allow UA to edit or save this image, whereas UB can save the same image. Neither users nor apps have fixed access roles in the system. Access permission comes with the content and app dynamically adjusts to it. 3.3. File Structure
- As shown in Figure 5, the file starts with the 1-byte field, which shows the sign size. Next, it contains the signature of the remaining part that is signed using the server’s private key. By verifying the signature, the application can confirm the integrity of the content as well as the sender. Because it is multicasting to several users with different access rights, there is a separate header for each user. The client application can find its header by checking the User ID. Then, it uses its private key together with access rights field Li, C1, and C2 to decrypt the AES key.
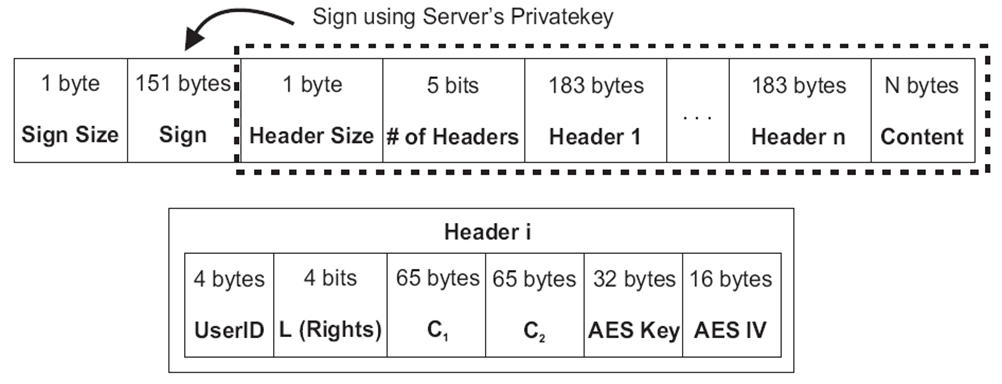 | Figure 5. File structure |
3.4. Algorithms
- Algorithm 1 shows the creation of the final encrypted file with access rights for multicasting. Algorithm 1: File EncryptionInput: data file, sender’s public and private keys, receivers’ public keys, rights list Li Output: Encrypted file1. Read file and compress the data 2. Randomly generate AES key and IV 3. Encrypt the data using AES key and IV 4. for i=1 to no of users do5. Encrypt AES key and IV using receiver publickey[i] and rights L[i] and append to the encrypted file 6. Sign header and data using server’s private key and append to the encrypted file7. end for 8. return: encrypted_file Algorithm 2 shows the process of decryption for a given recipient.Algorithm 2: File DecryptionInput: Encrypted file, receiver’s ID, receiver’s private keyOutput: Decrypted file1. Read the sign and verify the integrity. 2. Get the respective user’s header. 3. Decrypt the header using receiver’s private key and get the AES key and IV 4. Decrypt the data using AES key and IV 5. Decrypt the data file and create the decrypt_file. 6. return: decrypt_file
4. Results and Discussion
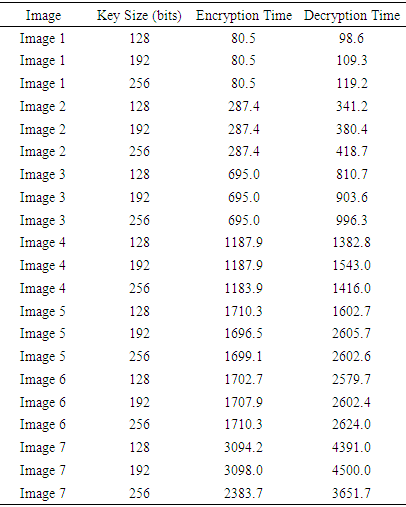
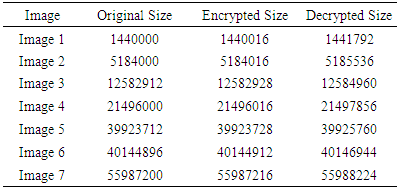
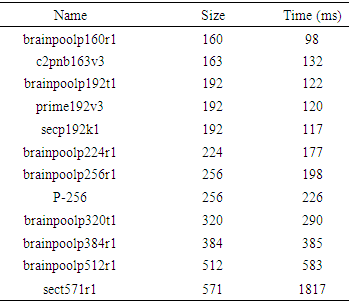
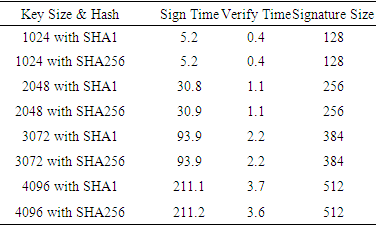
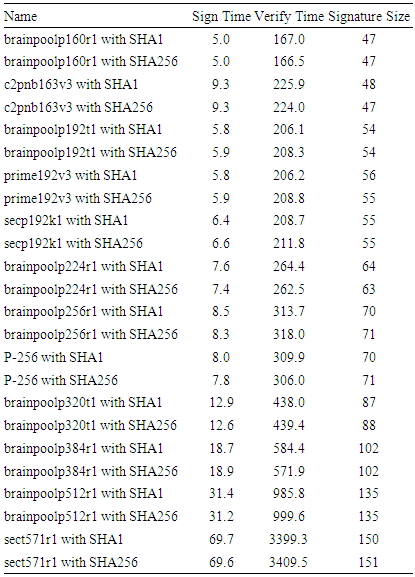
- In order to identify efficient algorithms as well as bottlenecks, several algorithms were tested thoroughly. When the encryption of large medical images happens at the server side, it can be easily empowered by a high-performance server to increase its efficiency. However, the real bottleneck happens at the mobile device due to its limited resources. The mobile application was tested using Android 5.1 and a Samsung Galaxy Core Prime phone with 1.2 GHz Quad-core Cortex-A53 CPU, Adreno 306 GPU, and 1GB RAM.As shown in Table 2, AES symmetric key encryption and decryption times are measured against the different image sizes and different key sizes. Because most of the processes running in the background are Worker Threads or AsyncTask, run times are significantly different from one run to another. Thus, each process is repeated 50 times, and the minimum time is taken as its best run time. The results show that it is almost the same in the long run for any key size. However, the IV generation time is significantly longer than the key generation time.
|
|
|
|
|
|
|
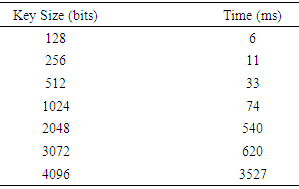
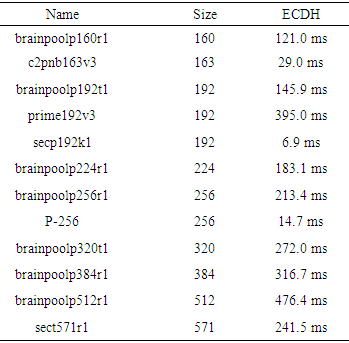
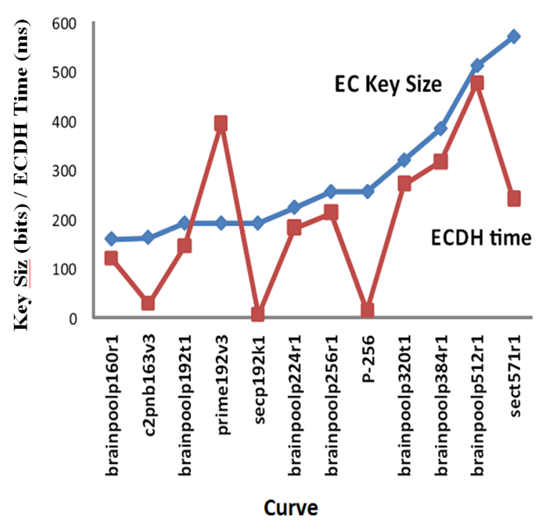 | Figure 6. ECDH time and key size |
5. Conclusions
- In the present work, a combination of two robust cryptography methods has been used to implement a dynamic and flexible access control method that can ensure the access rights of sensitive medical data without compromising the strength of any. The method can be used to enforce different access rights for different users over the same content in a multicasting environment. It uses multiple keys effectively to enforce different access rights without making any extra key storage problem. The method is well suited to mobile devices, since ECC requires fewer computations and less space compared to other public-key methods.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML