-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Computer Science and Engineering
p-ISSN: 2163-1484 e-ISSN: 2163-1492
2015; 5(1): 8-13
doi:10.5923/j.computer.20150501.02
Generation of a Reliable Online Poll Using the Personals Informations from the Social Networks
Mohcine Kodad1, El Miloud Jaara1, Mohammed Erramdani2
1Computer Science Research Laboratory (LARI), University Mohammed First, Oujda, Morocco
2High School of Technology Team (ESTO), University Mohammed First, Oujda, Morocco
Correspondence to: Mohcine Kodad, Computer Science Research Laboratory (LARI), University Mohammed First, Oujda, Morocco.
| Email: |  |
Copyright © 2015 Scientific & Academic Publishing. All Rights Reserved.
This paper analyzes the integrated poll in the social networks such as Facebook poll and discusses the lack of transparency and credibility in some survey. We Introduce MKO E-voting tool as a new system which aims to establish a reliable tool to generate an online poll based on personal information of users extracted from the social networks. Our contribution is also to make a new strategy to add some new options to control and to count the votes in order to have a reliable survey.
Keywords: Social Networks, Poll, Facebook Group, Facebook App, MKO E-voting tool
Cite this paper: Mohcine Kodad, El Miloud Jaara, Mohammed Erramdani, Generation of a Reliable Online Poll Using the Personals Informations from the Social Networks, Computer Science and Engineering, Vol. 5 No. 1, 2015, pp. 8-13. doi: 10.5923/j.computer.20150501.02.
Article Outline
1. Introduction
- The technology leap brought by the arrival of the Internet, including all mediums of communication such as e-mail changed the approach of sampling methods. One very attractive factor for poll experts is that the cost is cheaper online than by phone or mail.The social networks are also a rich wealth of easily accessible information for researchers and pollsters opinions. Moreover, they are a free way to get in touch with a customer, since it is enough to create an account to be on a social network.According to some researcher in this field, several benefits are directly related to the use of social networks by marketers such as: the ability to target and to select easily qualified samples and with large size, it is easy to have the answer of any user without having his contact information, the permanent availability of respondents thanks to the expansion of the use of mobile devices and social networking applications, or also it is easy to follow the returns and the developments to adjust the survey approach.In [1] voting system contracts restrict copying, duplication, decompilation, reverse engineering, and preparing derivative works as well as other actions. Con-tracts consider it a breach of confidentiality if anyone else than the customer’s “employees, agents or contractors” engage in these kinds of activities. And, complicating matters, confidentiality obligations can extend to information re-corded in tangible forms (hardware, software, manuals, etc.) as well as oral communications and “know-how” obtained while interacting with the system.Several articles have also pointed out technical and security vulnerabilities in e-voting systems. Security was not found to be a part of the design of two e-voting systems and security features were just added in an ad-hoc manner resulting in numerous vulnerabilities in the systems [2]. Similarly, security gaps in technology were found in online voting pilots in the UK [3]. Other technical and security factors that hinder e-voting systems include lack of transparency [4], potential for accidental or intentional errors in the recording of votes [5], programming errors, potential for tampering, and inability to recover [6].The purpose of this paper is to establish a reliable tool to generate an online survey which is based on the personal information of users collected from social networks to calculate the votes, it is all about to set up a new strategy to add new options in order to control and to count the votes to have a reliable survey, it is to store the email and/or the identifier of each social network user (in this document, we will call it from now "RS Identifier"), we will take in consideration the relationship between the email account and the RS Identifier.The rest of this paper is structured as follows: In the second section the paper discusses the online surveys, its advantages and his role in the social network, the third section presents the methods and data analysis of MKO E-voting tool, the fourth section talks about setting up our tool, and we end up with a conclusion in the fifth section.
2. Online Surveys
2.1. Online Surveys: What is the Context?
- There are two main contexts for using an online survey, a larger public survey and a targeted survey.Larger public survey: This one is about to get different people answers for any subject in order to take the most representative one among this population.Targeted survey: Some surveys have to go to a targeted public or costumers; For example, to know the most preferred colors of flat screens for computer buyers.The improvement of customer service is another example. It is easy for an organization to conduct an online survey to find out what customers like or not with the company behaviors. By asking questions like “What factors motivated your choice for our product?” Or, “What elements in our company do you value the most?” Many Organizations can improve the service they offer to their customers. This type of online survey is easily achievable by e-mail.There are also two main methods of online survey, like:- Establishing an online survey directly on internet.- Sending the survey by e-mail, this type of online survey is much more personalized and effective because we must firstly select the participants.The main advantages of an online survey are: Low costs, quick responses, quality of responses and effectiveness of their Analysis. However, we must be very careful with the use of online survey, because the customer can be harassed, irritation of visitors to our site, or the representativeness of respondents.Finally, another area where online surveys are highly used by some organizations is to take the opinion of their employees. In general these online surveys take place prominently on the company intranet and are therefore easily accessible by all employees.
2.2. The Poll in Social Networks
- In general, online surveys on social networks give some freedom to users; it is not required for them to submit their responses in the presence of an investigator, which can influence or judge the quality and the authenticity of the answers. The polls can be found in many social networks like Facebook that offered the notion of "groups" from September 2004 as one of the major characteristic. These groups include a survey also known as the "Ask Question".This survey allows for group members to create polls in a simple click on the "Ask Question" tab and they put a title and the options they want and also give the ability for other members to add options they want (see Figure 1).
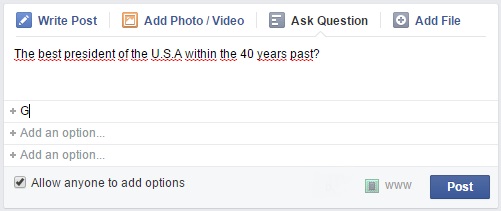 | Figure 1. Facebook poll example |
2.3. Problems
- Currently some social networks offer online surveys such as ones in Facebook that effectively provide a survey for its users like what we mentioned in the previous paragraph (2.2), but it contains some problems of reliability regarding the credibility and the transparency like the ability to change the location of a vote and for which one a member voted, without forgetting that this poll is restricted and limited to only member of the group, not for all Facebook users or for the public.Also for websites that offer online surveys [7], the strategy to control and to count the votes is often based on the options that follow: - "None": there is no voting control that means that the user can vote multiple times, and all that will be counted by the counter.- "Cookie": the vote is controlled with cookie and when it is saved on the machine the user cannot repeat the action.- "IP Address": the vote is controlled with the IP address, so when the IP address is saved in the database the user cannot vote for the second time.- "IP + Cookie": It is the most efficient technique for voting; once the cookie and IP address are saved the owner of these information, can’t vote for the second time.As explained above, the options before can have many reliability problems with the calculation of votes and therefore automatically affect the results of a survey.
3. MKO-Evoting Tool: Methods & Data Analysis
- Our contribution is to provide a new tool to solve the problem of reliability described in the previous paragraph and it is of course an extension of the work done in [7], which is based in its context, the calculation of votes is only for people with an email account. MKO-eVoting tool whose name came from (Mohcine Kodad Electronic Voting tool) is a new system which is based on the IDs of the social networks users to ensure non-duplication of votes.
3.1. Votes Counting Strategies
- As seen in (2.3), the online surveys are often based on 4 options "None", "Cookie", "IP Address" and "IP + Cookie".So our contribution is to implement a new strategy by adding some options to control and to count the votes in order to make it a more reliable survey, so we have to add email and RS identifier as a necessary option for this operation:- "E-mail": The vote is counted after verification that the current e-mail doesn’t exist in the database and after the confirmation of the e-mail by the user.- "RS Identifier": The vote is counted automatically after verification that the e-mail correspondent to the current identifier doesn’t exist in the database.MKO E-voting tool system takes into consideration that every RS identifier is associated with one and only one e-mail, the fact that you cannot find an RS Identifier account without an e-mail. Therefore, the system before it has an RS identifier it will first check the email associated with that ID if it does not exist in the database (see Figure 2).
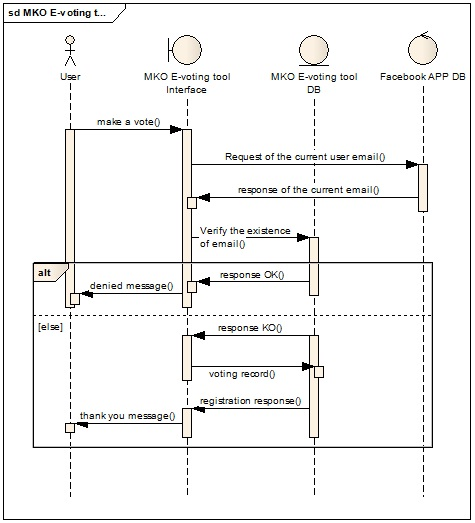 | Figure 2. Sequence diagram to verify the existence of the e-mail based on the RS Identifier |
- If the e-mail exist in database the message “denied message” is sent to the user, if the vote is saved in the database a “thank you message” is returned to the user.
3.2. MKO-Evoting Tool: Architectures
- We present in this section two architectures about the behavior of our system, starting with the generated survey and ending with the operation of our system at its deployment.For the generated survey from our system MKO E-voting tool, the web master want to create a survey, must first register in our system database, and after validation of his identity provides via his e-mail, he can access to the menu, and then he configures his survey (i.e. The title of the survey, security options, and picture for each option). In addition, he can customize the survey (i.e. "color", "police style" and "the count type of votes' that was mentioned in paragraph 3.1). Once the configuration is finished, the system generates the source code of the survey in order to help the web master to integrate it into his website and also returns him a link to his survey to use it directly from our system (see Figure 3).
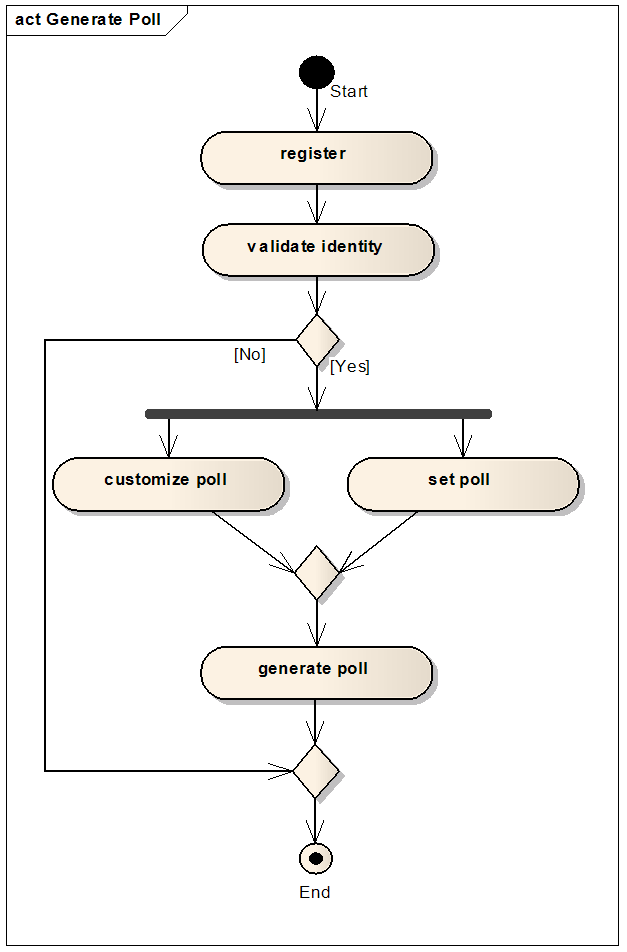 | Figure 3. Activity diagram of the process of generating poll from MKO E-voting tool |
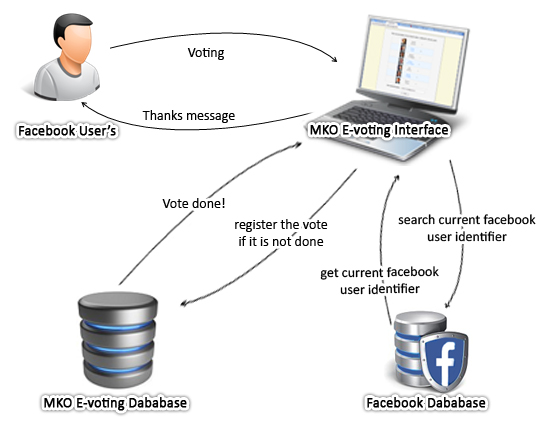 | Figure 4. Operating process architecture of MKO E-voting tool |
4. Setting up of MKO-Evoting tool
4.1. Social Network Application
- To retrieve the information of users from social networks account, and in general to bring some processing and developments from social networks such as Facebook. This one offers module named "Facebook App" in the "Facebook developers'” section [8]. That Facebook application aims to provide more abilities to users in order to participate and develop on Facebook using the personal information of other users wishing to contribute, all this in order to enhance the experience of users on Facebook. The information found in these apps is stored on developer servers that aren't hosted by Facebook. The developers are responsible for their servers, and Facebook cannot remove information from them.Keep in mind when you install an app, you give it permission to access your public profile, which includes your name, profile pictures, username, user ID (account number), networks and any information you choose to make publicly available. You also give the app other information to personalize your experience, including your friends list, gender, age range and locale [9].The application can provide additional information such as personal email address or birthday, but it always asks user for confirmation before gathering these information, even if it may limit the functionality of the application when they refuse. To create an application you can simply go to the "Facebook Developers" section, fill in the information about your application, and personalize some settings see Figure 5.
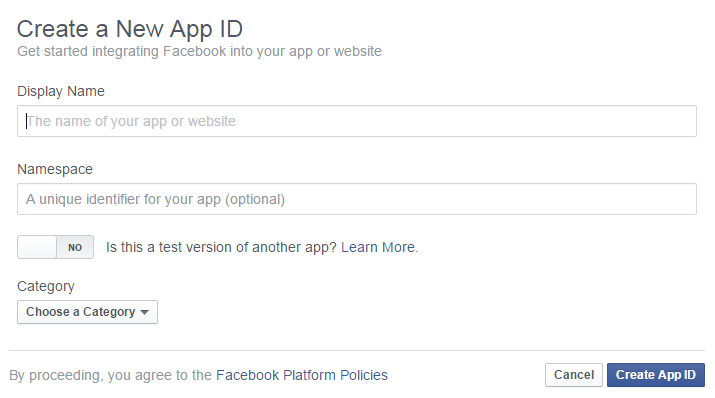 | Figure 5. Create a new app ID for “Facebook App” |
4.2. Setting up MKO-Evoting Tool
- To develop the MKO E-voting tool, we used PHP as a web page programming language with HTML5 and CSS3 for data formatting. In addition, after we created our "App ID" as mentioned in (3.3 Social Network Application). We will have to integrate the information provided such as the "App ID" and the "App Secret".These codes are generated when "Facebook App" is created, these two keys (App ID and App Secret) are needed to identify the Facebook application that belongs to us and will be used in the PHP code in order to help us to reuse and access to Facebook users who agreed that our application use their information.Thus, we developed our application to give everyone a specific role (see Figure 6 that represents a use case of our work).
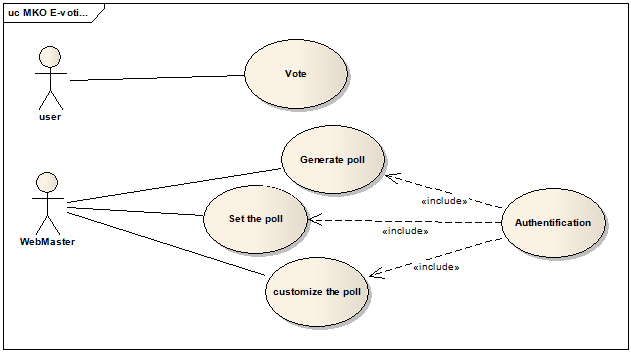 | Figure 6. Use case of MKO E-voting tool |
5. Conclusions
- We have seen in this article the different types of survey, the different types of options that controls the votes, we also showed our contribution by proposing a new strategy to prevent the duplication of votes, such as validation by e-mail or by social network identifier in order to establish a new system to generate a reliable poll also known as MKO E-voting tool.We have also put in this paper some diagrams and illustrations to help explain the functioning process of our system and also its architecture during the establishment of the survey from our system.Regarding our perspective, we expect to deploy MKO E-voting tool in a remote server for public access to validate its effectiveness and receive all remarks of users.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML