-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Bioinformatics Research
p-ISSN: 2167-6992 e-ISSN: 2167-6976
2021; 11(1): 1-31
doi:10.5923/j.bioinformatics.20211101.01
Received: Jan. 16, 2021; Accepted: Feb. 20, 2021; Published: Mar. 3, 2021

Effect of Coronavirus Worldwide through Misusing of Wireless Sensor Networks
Md. Rahimullah Miah1, AAM Shazzadur Rahman2, Md. Shahariar Khan3, Mohammad Abdul Hannan4, Md. Sabbir Hossain5, Chowdhury Shadman Shahriar6, S. A. M. Imran Hossain7, Mohammad Taimur Hossain Talukdar8, Alamgir Adil Samdany9, Mohammad Shamsul Alam10, Mohammad Basir Uddin11, Alexander Kiew Sayok12, Shahriar Hussain Chowdhury13
1Department of Information Technology in Health and Research Associate, Northeast Medical Pvt. Limited, Sylhet, Bangladesh and Former PhD Student, IBEC, Universiti Malaysia Sarawak (UNIMAS), Kota Samarahan, Sarawak, Malaysia
2Department of Medicine, Northeast Medical College, Sylhet, Bangladesh
3Department of Paediatrics, Northeast Medical College & Hospital, Sylhet, Bangladesh
4Department of Endocrinology, Northeast Medical College & Hospital, Sylhet, Bangladesh
5Department of Pathology, North East Medical College and Hospital, Sylhet, Bangladesh
6USMLE Student, USA and Ex-student of North East Medical College, Sylhet, Bangladesh
7Department of Oral and Maxillofacial Surgery, North East Medical College and Hospital, Sylhet
8Department of Clinical Oncology, North East Medical College and Hospital, Sylhet, Bangladesh
9Department of Orthopedics, Northeast Medical College, Sylhet, Bangladesh
10Department of Forensic Medicine, Northeast Medical College and Hospital, Sylhet
11Department of Paediatrics, Northeast Medical College and Hospital, Sylhet, Bangladesh
12IBEC, Universiti Malaysia Sarawak, Kota Samarahan, Sarawak, Malaysia
13Department of Dermatology, Northeast Medical College, Sylhet, Bangladesh
Correspondence to: Md. Rahimullah Miah, Department of Information Technology in Health and Research Associate, Northeast Medical Pvt. Limited, Sylhet, Bangladesh and Former PhD Student, IBEC, Universiti Malaysia Sarawak (UNIMAS), Kota Samarahan, Sarawak, Malaysia.
| Email: |  |
Copyright © 2021 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Corona is a non-communicable sensor disease spreading worldwide through misusing of processed radio frequency. So far higher authorities of health services are facing the undesirable escalating causes of coronavirus towards human beings as a very scientific puzzle comprehensive issue. The study aims to evaluate the maltreating of wireless sensor networks that affect individuals within the body boundary area. Wireless sensor data were collected from individual’s profile, diagnosis and sensor node records at laboratory experiments. The study shows the effect of processed sensor nodes among individual’s body organs to compare with the existing environments. The study illustrates all individuals suffer from sensor disease due to reflecting of wavered sensors at open eyes sights with high speed electromagnetic-radio tracking systems. The overweight and obesity patients are sick from corona disease at less sensor time in a dark environment than that of light conditions. These findings replicate the severe global one health security that the expert provides in active eyes within geographic locations. Systematic healthcare awareness is essential for treatment with medical technological devices but such consciousness is poorly recognized and medication supports are still below par. The study suggests upcoming healthcare paths of a new dynamic alternative approach to promote global public health security concerning Sensor Health Policy and Sustainable Development Goals 2030.
Keywords: Corona virus, Sensor node, Obese, Dark environment, Health security
Cite this paper: Md. Rahimullah Miah, AAM Shazzadur Rahman, Md. Shahariar Khan, Mohammad Abdul Hannan, Md. Sabbir Hossain, Chowdhury Shadman Shahriar, S. A. M. Imran Hossain, Mohammad Taimur Hossain Talukdar, Alamgir Adil Samdany, Mohammad Shamsul Alam, Mohammad Basir Uddin, Alexander Kiew Sayok, Shahriar Hussain Chowdhury, Effect of Coronavirus Worldwide through Misusing of Wireless Sensor Networks, American Journal of Bioinformatics Research, Vol. 11 No. 1, 2021, pp. 1-31. doi: 10.5923/j.bioinformatics.20211101.01.
Article Outline
1. Introduction
- Coronavirus is the most pressing scientific puzzle, which is tarnished in the history of the world [1,2,3,4,5]. The virus infected several people at Wuhan Province in China on December 29, 2019 [6]. Then the number of people infected with the virus increased day by day and spread all over the world, and almost 2 million deaths from the COVID-19 virus [7,85]. This new virus and disease were unknown before the outbreak began at Wuhan last year but till to date total confirmed total cases 92022539, total deaths 1970394 (3%) and recovered 65865510 (97%) [8]. In this unwanted situation, all the countries and the whole world are worried, anxious and scared. There is stagnation in all spheres including social, economic and communication due to unwanted conditions of coronavirus [9]. The World Health Organization provides information and guidance online on the spread of the virus, as well as regular virtual conferences, meetings, press briefings and exchange of information [7]. Corona virus is known as COVID-19 or Coronavirus disease 2019, which is spreading in geographic locations, which is affecting 219 countries and territories around the world [8]. The most recently discovered coronavirus causes a disease formed COVID-19 [10]. Most countries in the world are inclined to such outbreaks due to the presence of interconnected markets, complex emergencies, barrier to religious mass gatherings, variation in emergency healthcare systems performance within and between geographic landscape, seascape and skyscape [11,12,13].Now a day’s medical sensor technology is essential in every step of healthcare. Wireless Sensor Network is an integrated infrastructure comprising sensing, computing, detecting, tracking, observing and reacting the individuals within geographic positioning systems (GPS) locations [14]. This network deploys the indoor and outdoors in large sensor fields using the object's light and radio signal [13,15,16,17,18,19,20,21,22,23]. Current and customary medical systems cannot meet the requirements of patient needs in a timely fashion. Applications of sensor technology have unlocked up new scenarios in healthcare systems [24]. This technology is actually valuable in some healthcare applications, which can be inserted into the human body for treatment services [25,26,27]. The cutting-edge sensor technology misuses in different services including healthcare activities, which have triggered a collective capacity of scarcities and securities. Wireless sensor networks are premeditated to achieve the scarcities like dimension, tracking, detection and cataloging, simulation particularly the field of health monitoring [14]. A harmonized amount of medical technologies has been organized for patients’ monitoring who suffer from severe diseases or have urgent prerequisites [27]. Wearable health-monitoring provides a revolutionary sensor technology, which serves as an alternative to traditional diagnosis, putting healthcare data on a path that is more remote, portable, and timely [28,29,30,31]. Physicians and health researchers use these healthcare data to evaluate body conditions with a sensor technology like internet of everything, artificial intelligence, deep-learning algorithm [32,33,34]. Moreover, sensor technology has a great advantage on non-communicable diseases to identify the classical symptoms [14]. Wireless sensor networks are a huge endeavor of digital health technology, including technology dependence, which has led to frustration due to lack of proper security. Smartphones can do a lot of lucrative things with at least 12 functions with digital health sensor systems [35,36]. Cyber hackers misuse the radio frequency through smartphones, telematics and high frequency sensor devices for spreading this corona remote sensing VIRUS (Vital Information Resource Under Siege) among animals and human beings, mostly coronavirus [15]. Wireless sensor networks are a huge endeavor of digital healthcare including digital health data, technology dependence, which has led to frustration due to misusing of advanced technology [14]. The rationalized generations involve in good or harm activities to any human in the world through wireless sensor networks through hidden codes [14]. The present world is being one-sidedly mistreated sensor networks one after another from cyber hackers [15]. The heartbreaking phenomena of this frustration are the foremost consequence of today’s COVID-19 outbreaks in human beings [37].The study is to observe the impact of wireless sensor networks towards individuals through spreading corona disease at body boundary. The aim of the study is to find out the new innovations with interdisciplinary approaches to solve the core challenges in global health security to recover corona disease in order to provide the justifiable policy options by the use of sensor technology.
1.1. Historical Background of Coronavirus
- The history of coronavirus is long. Most people do not know its exact history, although some speak of China's Wuhan Province to infect people with novel coronavirus [95,96]. World Health Organization (WHO) leading Scientists searching the historical background of the coronavirus are wrapping up a protracted investigation in Wuhan, China [97,98,99]. Again, someone is saying "zoonotic cause" [100]. Different individuals and organizations have pointed out its wrong source in different ways. No one was fully aware of its exact source. Again, many are saying out of superstition and bigotry that corona is "the wrath or torment of Allah (SWT)." It is informed from my research that their ideas are wrong. Corona virus is not a wrath of God (Allah). Its man-made sensor programming virus, which can make people and animals sick by tracking them at specific GPS distances by adjusting the retina of human and animal eyes through sensor devices. This was revealed in 2018 through the ISNAH test in PhD research at UNIMAS (Universiti Malaysia Sarawak) in Malaysia. The PhD thesis was approved by the Senate of UNIMAS on May 20, 2018. Since then, the study has been trying to inform the people of the world about the findings of the PhD research from 2018 to date, but cyber hackers are creating obstacles in various ways. This is because, “some people (through the misuse of technology) are wreaking havoc on water and land all over the world” [87]. In 2018, the name of the study on sensor technology test was "ISNA-Impact of Sensor Networks towards Animals", and in 2019 it was called "Corona" at Wuhan, then WHO declared as COVID-19. The symptoms that appeared during research on dogs and cats are exactly the same in people infected with the coronavirus. Some scientists and researchers around the world have misunderstood the history of the coronavirus, which has already infected 105 million people and killed 2.3 million of them [85]. Again, many more are getting sick, some of them may die or be healed by being aware of its effects. Many in the world have tried to know its history, but many have failed, many have fallen ill and eventually died. It is an education for all of us, so that it can be realized the misusing of sensor networks in the future. Many have read my research and learned its basic history. In order to stay healthy, the study has presented the findings in various ways in the media, webinars, seminars, conferences and publications to create awareness. But some of them did not listen to me but called me a crazy-goat, also called me a liar, separated me from my family, fired me and many more tragic things happened - because of my research. So, corona is not spread by bats, humans or any other animals, it was not made in any scientific lab like the Wuhan Institute of Virology [101], but cyber hackers spread corona disease in humans and animals’ body through cloud sensing devices due to misusing of wireless sensor networks at certain GPS distances [15]. Mask, handwash, social and physical distance and vaccines are not completely recovery pathways, but cyber hackers send messages with false interfacing to the higher authority [Appendix A].
2. Research Materials and Methods
2.1. Study Site
- This research method was conducted as PhD research work from October 2014 to May 2018 at the Universiti Malaysia Sarawak (UNIMAS), Malaysia. The materials and methods were connected with different parameters to enhance data collection, ISNAH Experiment, Specimens Tracking Process, Data Analysis and interpretation [38] as below:
2.2. Sample Size and Study Design
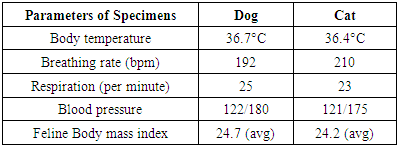
- All specimens were housed in a room with controlled temperature 36.4°C in cat and 36.7°C in dog with breathing rates, respiration, blood pressure and feline body mass index [39]. The experimental design was randomly divided into three experimental groups with Body Mass Indexes including obese, normal and underweight (Table 1), and observed the impact of wireless sensor networks towards tracheas among them in the light and dark environments. The test samples in this study were dogs and cats.
|
|
 | Figure 1. Study design of Processed Wireless Sensor Networks |
2.3. ISNAH Experiment
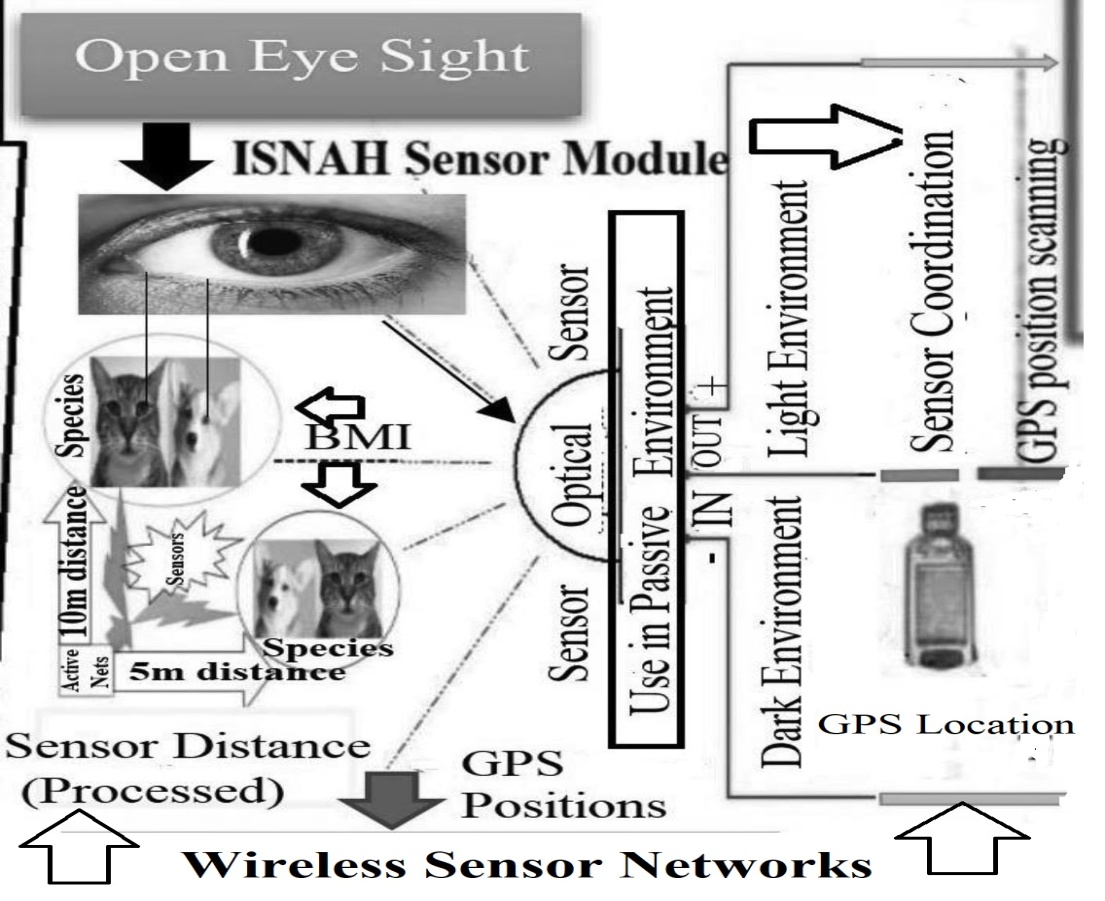
- The study necessitates an integration of methods used in wireless sensor networks towards animals’ bodies and identified its implication. This envisaged the research taking in matter-of-fact research elements to investigate issues hoisted in the study, primarily targeted at SMART devices like telematics’ users towards specimens. Telematics is a smart device, consisting of a scanner, recognizer, detector, global positioning systems (GPS) and global navigation satellite systems (GNSS). The fieldwork conducted in the studied area within January 2015 to January, 2017. ISNAH Experiment is the novel and uniqueness experiment which includes the Impact of Sensor Networks towards Animals [40]. The ISNAH process showed the necessary components in Figure 2. This is a multi-diversified experiment in connection with sensor technology to augment non-communicable diseases among animals and the human body [41].
 | Figure 2. ISNAH Process [15] |
2.4. Study Process
- The study examined two specimens, one is dog and another one is cat among 14 individuals for identification of this misuse application. These animals are available in the study area and suitable for experiment. The study selected sound health two species (14 individuals) with Feline Body Mass Index (FBMI), body temperature, breathing rate, respiration and blood pressure [42]. The experiment took at dark and light conditions. The specimens stayed in specific geographic locations and put the individual inside the iron case (size: 3.5′x 2′x2.5′). Then measurement of an individual's coordinates location includes longitude, latitude and ellipsoid height with GPS and GNSS identifiers. From the field observation, the Automated Radio Telemetry System is more effective in dark than light environments. For this purpose, the study examined the system on smart cell phones, telematics devices, iron cage and individual species separately. The experiment continued at five locations, viz. (i) Location A with light environments but no WiFi, (ii) Location B with dark and light environments including WiFi, (iii) Location C with dark and light environments including WiFi, (iv) Location D with light environments but no WiFi, (v) Location E dark and light environments including WiFi.
2.5. Sensor Disease Spreading Process
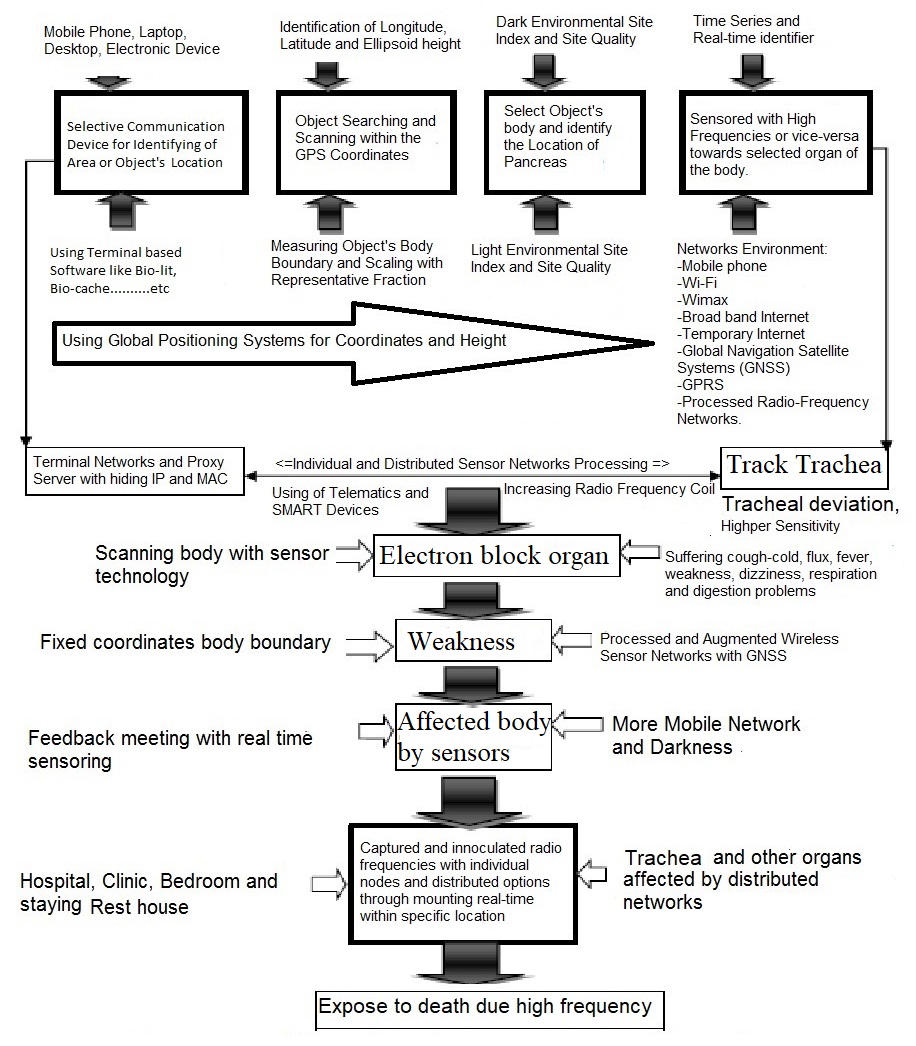
- Common Acute Sensor Infections and Disorders (CASID) is the new term, which indicates the sensor diseases produce and spread through processed radio frequency of advances in sensor technology. When this processed radio frequency is tracked in GPS positions towards living cells, particularly human beings and animals’ bodies. The sensed living cells block electron movement and produce different types of disorders or diseases in the affected organ of the body. The CASID implies a formula as,
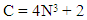
 (i)Where, N= the number of sensor network generation processed response signals.C= the producing sensor diseases including CASID.The cyber hackers are misusing the wireless sensor technology due to expanding processed radio frequency coil at longitude, latitude and ellipsoid heights. These processed radio frequencies are disseminating to a human body’s GPS coordinates points through a clouding system around the world. The cyber hackers are staying at geographic locations and produce different types of diseases, particularly Coronavirus disease in the human body. The hackers select the specific organ of the body as a fixed GPS location, including (i) Office room, (ii) dining room, (iii) Bed room, (iv) Wash room, (v) Meeting and conference room, (vi) Media / communication room, (vii) Computer / Network Server room, (viii) Mobile / Telephone room, (ix) TV / Theatre room, (x) kitchen, (xi) Dressing room, (xii) Healthcare room, and (xiii) Other GPS location. The sensor disease can produce through the following steps, which as shown in Figure 3.
(i)Where, N= the number of sensor network generation processed response signals.C= the producing sensor diseases including CASID.The cyber hackers are misusing the wireless sensor technology due to expanding processed radio frequency coil at longitude, latitude and ellipsoid heights. These processed radio frequencies are disseminating to a human body’s GPS coordinates points through a clouding system around the world. The cyber hackers are staying at geographic locations and produce different types of diseases, particularly Coronavirus disease in the human body. The hackers select the specific organ of the body as a fixed GPS location, including (i) Office room, (ii) dining room, (iii) Bed room, (iv) Wash room, (v) Meeting and conference room, (vi) Media / communication room, (vii) Computer / Network Server room, (viii) Mobile / Telephone room, (ix) TV / Theatre room, (x) kitchen, (xi) Dressing room, (xii) Healthcare room, and (xiii) Other GPS location. The sensor disease can produce through the following steps, which as shown in Figure 3.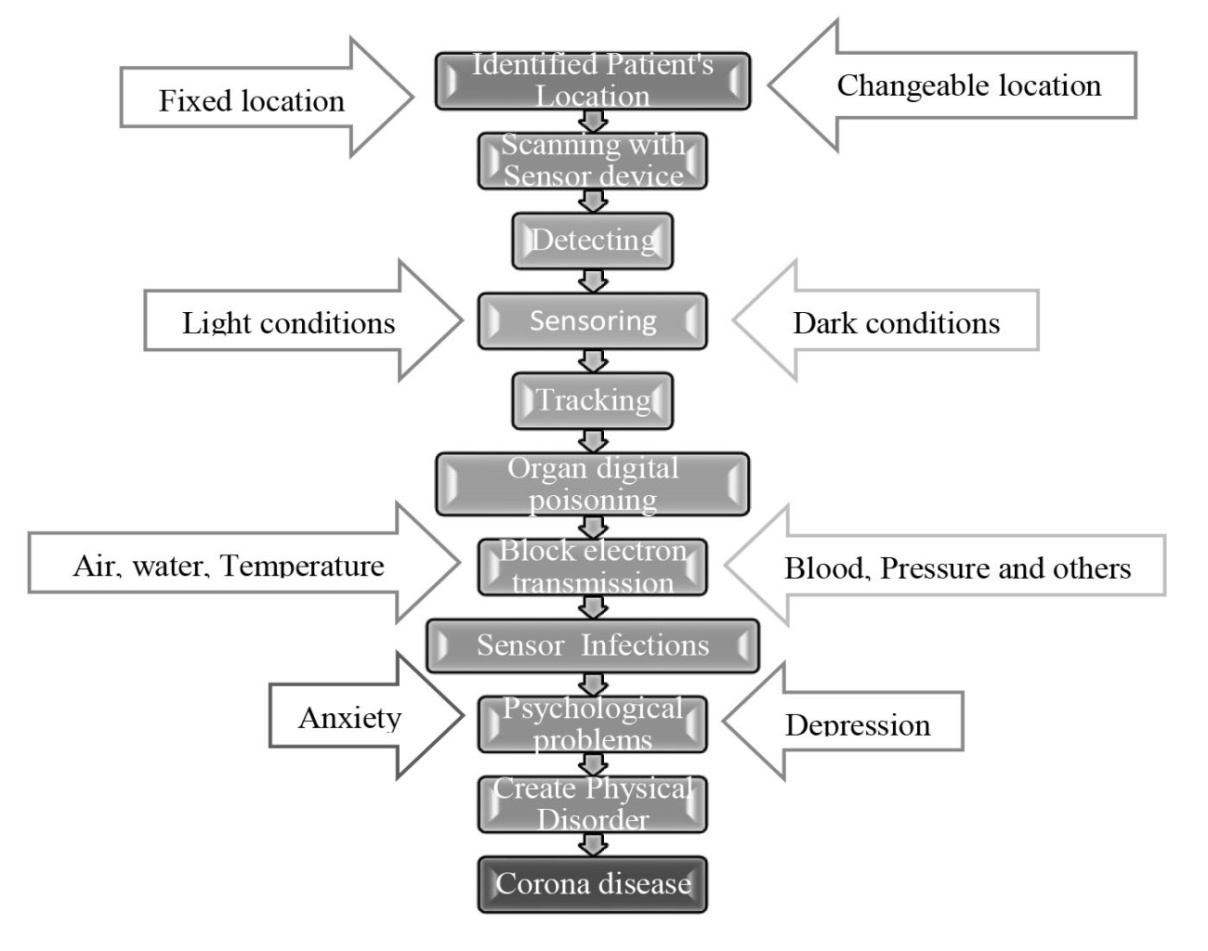 | Figure 3. Sensor Disease spreading process |
2.6. CASID Recovery Process
- CASID implies the common acute sensor infections and disorders. The CASID recovery process is simple and easy, which includes different components as shown in Figure 4. These are (i) disease recovery components, (ii) Sensor health quality services, (iii) Improvement of wireless health sensor trained-up options, and (iv) Sensor health community networks.
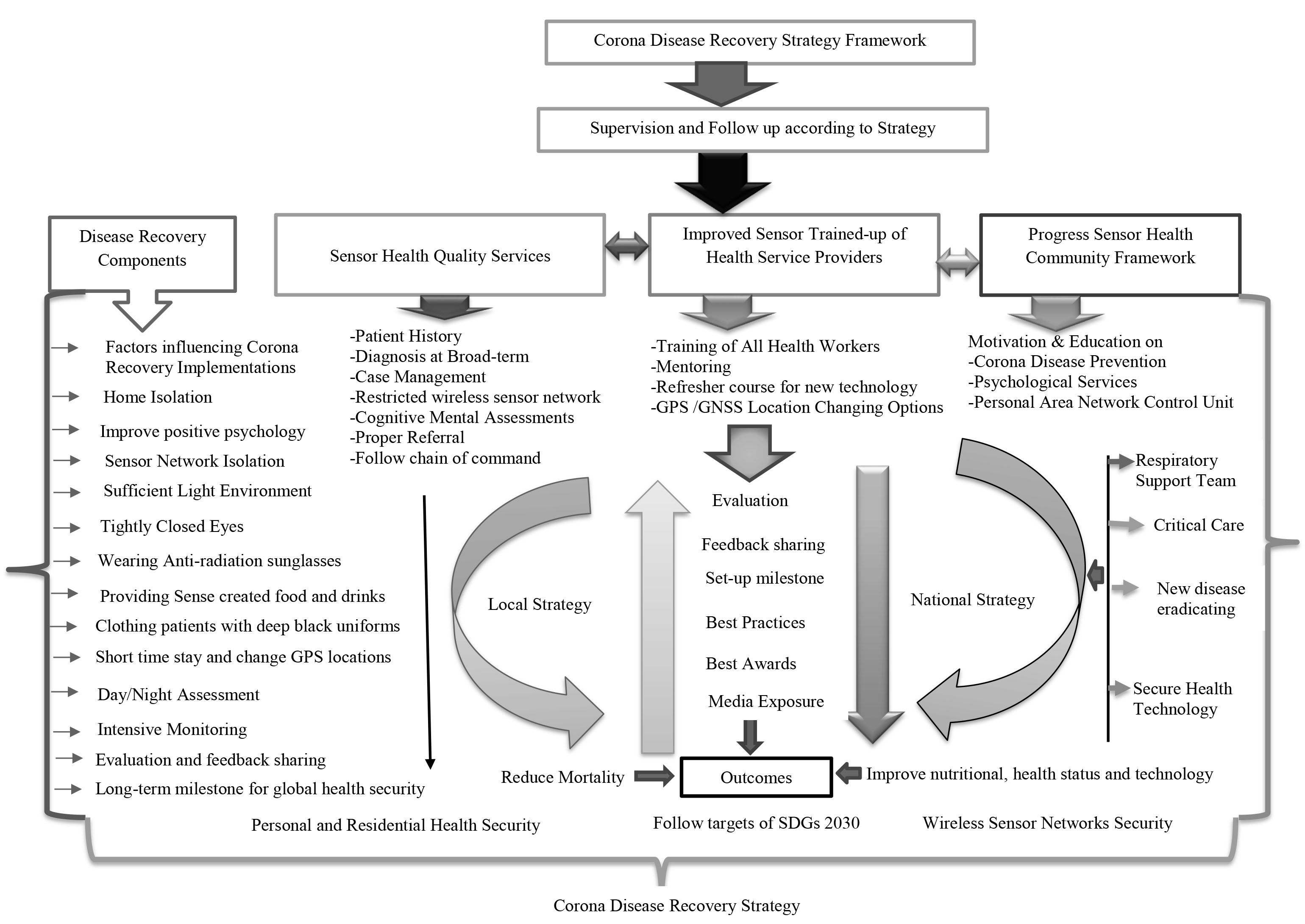 | Figure 4. Corona disease recovery system |
2.7. Ethical Consideration
- The study is a part of PhD research work at UNIMAS, Malaysia, which was approved by the Senate and Graduate Study Committee. Every ethical issue was discussed with the COVID patients including underweight, normal and overweight, regarding the study and informed written consent were obtained.
2.8. Data Compilation
- Quantitative and qualitative related bio-sensor data were obtained through ISNAH experiment while secondary data were obtained from diverse sources. All collected data were compiled for analysis according to findings.
2.9. Data Analysis and Interpretation
- All general information regarding the occurrence of specimens, status and affected condition were checked for accuracy from the different sources and sources of information were also verified. The compiled and processed data were involved in the preparation of the data master sheet and assimilated into suitable systems used in the results and other segments consecutively. The data were compiled and analyzed for presentation and interpretation using standard data analysis software like MS Office Suite 2016 and SPSS version 26.
3. Results
3.1. Identified of Individuals’ Location and Tracking Time
- The study identified species location from sensor devices at light and dark environment conditions. Individual’s location is recognized with body reflection through sensor technology within GPS locations. Using optical distance through processed radio frequency, the sensor device scanned the individual's location at least 30 ways for tracking. such as: (1) Individual’s active open eyes, (2) Active mobile phone, (3) active computer or laptop within eyesight (even if it is off, if there is an electrical connection), (4) staying at TV, fridge and Air Conditioning boundary, (5) opening sensor electronic devices, if there has electrical connection, (6) active individual’s retina or sense site index, (7) speaking words softly or loudly, (8) Sneezing, (9) Breathing more or less, (10) Sudden cough softly or loudly, (11) hiccups, (12) urination/ micturition sudden, (13) Sudden flatulence, (14) Bowel movements, (15) Suddenly itching in body and other organs such as ears, head, hands and feet, (16) Teeth grinding sudden, (17) Face suddenly fades /cyanosis, (18) Suddenly running nose, (19) Feet suddenly ache, (20) Hands suddenly grind, (21). Backside / sciatica suddenly itches, (22) Fingers suddenly tingling, (23) Suddenly get angry, (24) Suddenly feel very hot or very cold at instant location, (25) Suddenly feel very hungry or thirsty, (26) Making suddenly noise, (27) Suddenly feel sick, (28) Suddenly screaming, (29) Suddenly stomach ache, (30) Crying at instant location, (31) Ecstasy or happiness suddenly, (32). Suddenly move at undulation place/stair, (33). Gossip with others nearby.
3.2. Sensor Reflection at Dark Environment
- Processed wireless sensor networks reflect the dark environment among the body mass index patients. The study continued tracking towards cat and dog species at dark conditions. These processed sensors are more sensitive towards obese dog within 5 minutes and obese cat within 7 minutes affected to the whole body, particularly tracheal organ, which as shown in Figure 5. From the ISNAH experiment, the study represents human body transmission with sensor disease, particularly coronavirus disease or COVID-19.
 | Figure 5. Impact of processed wireless sensor networks at dark environment |
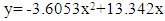
 (i)
(i)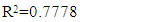
 (ii)Where, y is the affected time on censored dog and x is the affected time on censored cat, with underweight, normal and overweight species in coronavirus at dark environments. Equation (i) has adjusted with the equation (ii) R2 (coefficient of multiple determinant of 0.7778 with standard error of estimate on observed mean. The value of R2 is equivalent to 1, which indicated censored time was affected towards the animal's body, particularly at trachea. So, the stated equation is accepted. The developed equation was then employed to stimulate human’s sensor disease consciousness regarding wireless sensor networks with processed radio frequencies in BMI status. If the value of R2 is negative, then the approaches between observed censored time and simulated values estimated effects on human trachea to augment the causes of coronavirus disease. The fluctuated radio frequency affected sensor disease on animals and human beings positively.
(ii)Where, y is the affected time on censored dog and x is the affected time on censored cat, with underweight, normal and overweight species in coronavirus at dark environments. Equation (i) has adjusted with the equation (ii) R2 (coefficient of multiple determinant of 0.7778 with standard error of estimate on observed mean. The value of R2 is equivalent to 1, which indicated censored time was affected towards the animal's body, particularly at trachea. So, the stated equation is accepted. The developed equation was then employed to stimulate human’s sensor disease consciousness regarding wireless sensor networks with processed radio frequencies in BMI status. If the value of R2 is negative, then the approaches between observed censored time and simulated values estimated effects on human trachea to augment the causes of coronavirus disease. The fluctuated radio frequency affected sensor disease on animals and human beings positively.3.3. Impact of Processed Radio Frequency at Light Condition
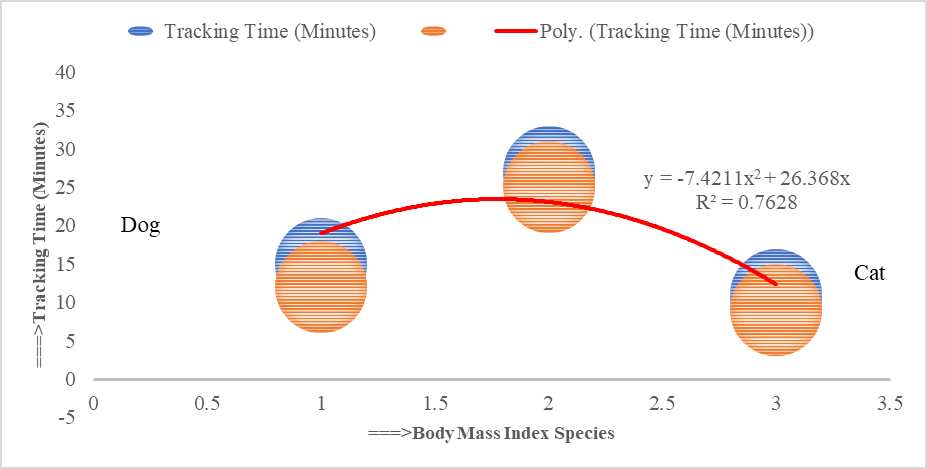
- Impact of processed and fluctuated radio frequencies are also positive in animals and human beings for sensor disease, particularly coronavirus disease. The study has gone tracking towards dog and cat species at light environmental conditions. These processed sensors are less effective, including underweight dogs taking 15 minutes and underweight cats within 12 minutes, which is shown in Figure 6. From the ISNAH experiment, the study represents human body transmission with sensor disease, particularly coronavirus disease or COVID-19 in a light environment.
 | Figure 6. Impact of processed wireless sensor networks at light environment |
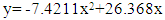
 (i)
(i)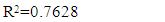
 (ii)Where, y is the affected time on censored dog and x is the affected time on censored cat, with BMI species effect in coronavirus disease at light environment. Equation (i) has adjusted with the equation (ii) R2 (coefficient of multiple determinant of 0.7628 with standard error of estimate on observed mean. The value of R2 is equivalent to 1, which indicated censored time was affected towards the body, particularly at trachea. So, the defined equation is also recognized. The established equation was then active to stimulate human’s sensor disease awareness concerning processed wireless sensor networks. If the value of R2 is fluctuated, then the approaches between observed censored time and simulated values estimated effects on human trachea to augment the causes of coronavirus disease. The light environment is suitable for sensor disease in animals or human beings negatively.
(ii)Where, y is the affected time on censored dog and x is the affected time on censored cat, with BMI species effect in coronavirus disease at light environment. Equation (i) has adjusted with the equation (ii) R2 (coefficient of multiple determinant of 0.7628 with standard error of estimate on observed mean. The value of R2 is equivalent to 1, which indicated censored time was affected towards the body, particularly at trachea. So, the defined equation is also recognized. The established equation was then active to stimulate human’s sensor disease awareness concerning processed wireless sensor networks. If the value of R2 is fluctuated, then the approaches between observed censored time and simulated values estimated effects on human trachea to augment the causes of coronavirus disease. The light environment is suitable for sensor disease in animals or human beings negatively.3.4. Integrated Impact of Sensor Networks
- From the study of misuse of telematics, it observed that the examined species- cat and dog felt uneasy and after a few moments, they sensed laryngitis with fever in body. Immediately the cell phone removed and disconnected the wireless sensor network from the body area and changed the existing location. During medication time, the study also observed that both animals are weak and felt pain at trachea. The study identified that the animals were suffering from tracheal infection and fluctuated body temperature. The radio frequency also impacts on tracking effective time to animals, which is shown in Figure 7.
 | Figure 7. Tracking time towards species at dark and light environments |
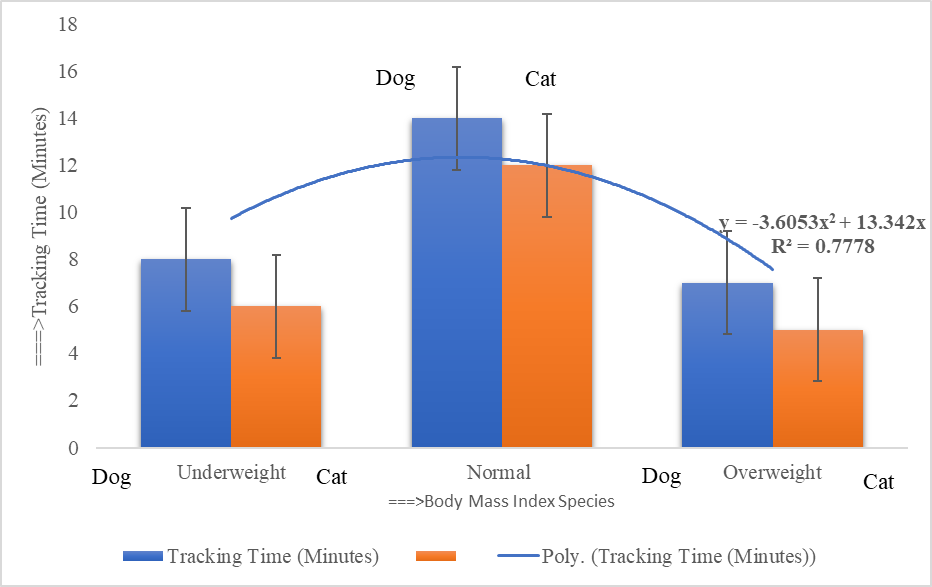
3.5. BMI and Processed Radio Frequency
- COVID patients with BMI types including underweight, normal, overweight are affected in processed wireless sensor networks at GPS location in the optical distance due to active open eyes. The underweight patients were affected by coronavirus within medium time (12 minutes) tracking in a dark environment, but overweight and obesity COVID patients were affected sick in less time (7 minutes) than the underweight, which is shown in Figure 8. Overall, all people are affected in a short time by the processed wireless sensor network at GPS position in a dark environment than that of light environmental conditions.
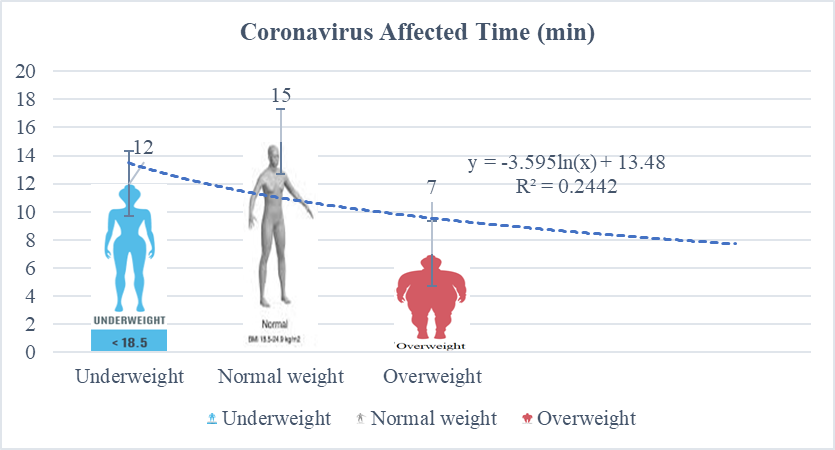 | Figure 8. Coronavirus affected times among BMI category patients |
3.6. Occurrence of Coronavirus Infection with Sensors
- For coronavirus infection, Cyber hackers first scan the sensor via GPS to confirm the current location of the person, animal or object and create symptoms of the corona. Cyber hackers can then censor certain parts of your body to make you sick, depending on the distance of the frequency, or to stop your breathing through the misuse of sensor technology. And if you stop breathing, your death is certain. Thus, by misusing node frequency, a person or an animal can be made sick or killed in corona and by misusing distributed frequency, people, animals, cows, goats, poultry, birds, fish or other animals can be made sick in corona together. Or can be killed. Cyber hackers block the movement of electrons in the clouding process through telematics devices between humans, animals and objects. Due to processed sensor networks, the wireless sensor first generation device produced 6 diseases according to application of stated formula, 4N3 + 2. But it depends on the user’s potentiality between country to country's network security. According to fourth generations, 258 sensor diseases produced, but physically observed that 362 sensor diseases have already produced from options, which as shown in Figure 9. Here, the CASID implies common acute sensor infections and disorders. According to ISNAH study, due to fixed GPS locations, these CASID converts into diseases, but changeable GPS positions with demand requirements, the patients recover these sensor diseases. It is also alarming that without dynamic sensor security networks, the CASID will be dangerous in future for living cells, as for example 4002 types of infections and disorders in tenth generation.
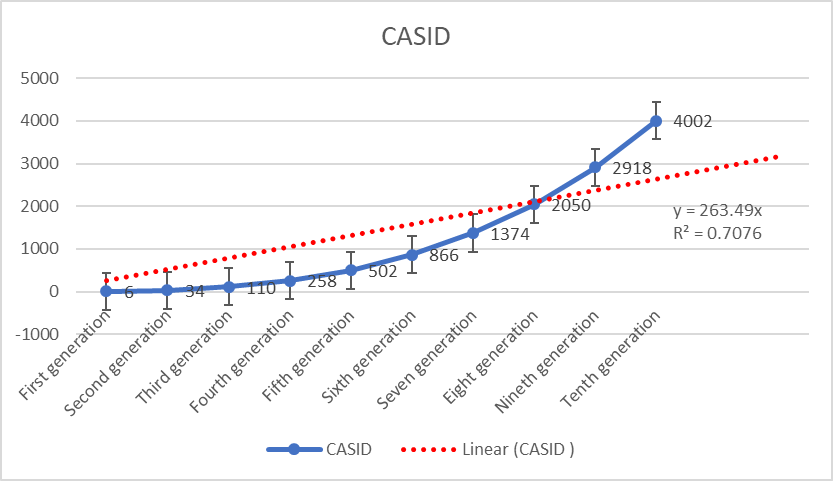 | Figure 9. Worldwide sensor infections and disorders |
3.7. Coronavirus Disease Spread through Wireless Sensor Technology
- Telematics is a type of sensor light made with sensor technology, which works in combination with atmospheric waves. Cyber hackers are scanning the retina of the human eye to know the current location and monitor every moment. As a result, your location will be known immediately wherever individuals open their eyes at the country or international border and their activities will go to the sensor server with the picture. Because the sensor network is adjusted to your vision in the atmosphere. In addition, individuals are sitting / lying in the office or at home, working, eating, sleeping, etc. on a daily basis. At this time, even if you have a mobile phone or sensor device around you, your location is easily known. Moreover, even if you do not have a mobile phone, your location can be known through words, laughter, tears, high-cough or open eyes. Cyber hackers find out the distance of different parts of your body from your surroundings through telematics devices, then digital scanning is done from the neck to the head of your body with software like CT (Computed Tomography) scan or MRI (Magnetic Resonance Imagery). Then the low frequency electromagnetic sensor force is applied to the voice box and trachea of the place through smart remote sensing with the help of telematics. For a while, the person feels a tingling sensation, body temperature rises, sneezing-coughing, or high-hiccups and body fades, runny nose, loss of appetite, and dryness in the airways. After the SMART mobile sensor contracts, the airway becomes constricted and the tracheal cartilage becomes more constricted and the air stops moving from the lungs, causing the person to have difficulty breathing and die within minutes. And Cyber hackers spread the word in the media that he died after being attacked by Corona. When a person realizes that he has or is likely to be infected with corona, he should immediately go to a place without a network, without going to a hospital or health center. He will stay in that place in silence, without any words or words, will only communicate with gestures. No electronic device or mobile phone can be used at that time until the condition of the body is normal. Again, if a person goes to a hospital or clinic by mistake, he is more likely to die, because in those places, Cyber hackers come in secret and will ensure death by tracking with wireless sensor technology from hiding beside him. Mainly three organs of the patients are affected in coronavirus including lung, larynx and trachea (Figure 10).
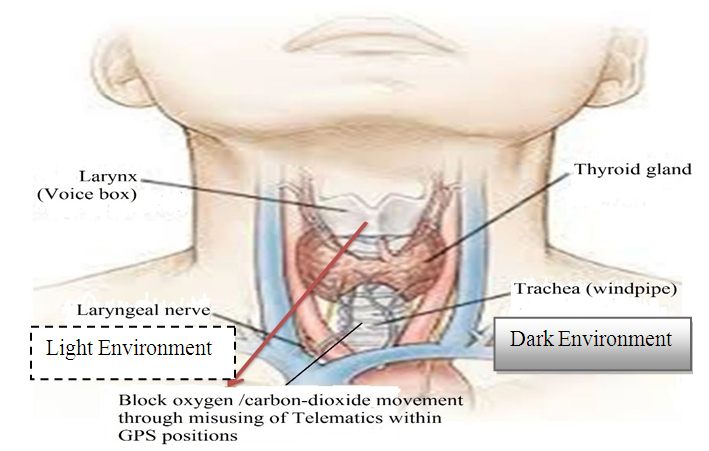 | Figure 10. Block air movement through misusing of sensor technology within GPS location |
3.8. Body Attack with Processed Wireless Sensor Technology
- Corona is a wireless-sensing technological virus that blocks electron movement at trachea. These block activities were occurred in different steps from smart devices like mobile phones, remote mobile phones, telematics or satellite phones with disseminating of fluctuated or same characteristics frequencies to infect individual’s organ at GPS positions including longitude, latitude and ellipsoid height, which as shown in Figure 11. It obstructs the movement of oxygen / carbon dioxide in various parts of the body, especially in the throat or trachea, impedes the movement of electrons in the body, and it also hampers the flow of blood in the aorta. Thus, individuals were infected with different diseases, like corona, laryngitis, fever, cough-cold, flux, dizziness, tracheal cancer, and tracheal deviation. In this way, individuals fall ill,eventually exposed to die due to swayed frequencies. From the ISNAH experiment, overweight obese animals were sickened by the sensor in the dark and died in 7 minutes, and in 12 minutes in the light, whereas light and normal animals became sick in the dark in 12 minutes and in the light in 25 minutes. That is, the animals were sick twice as often in the light. Sensor technology, however, is more sensitive to dark environments than light to make these animals sick. If the time and frequency of the experiment could be increased or doubled, it would have a negative effect on the animals.
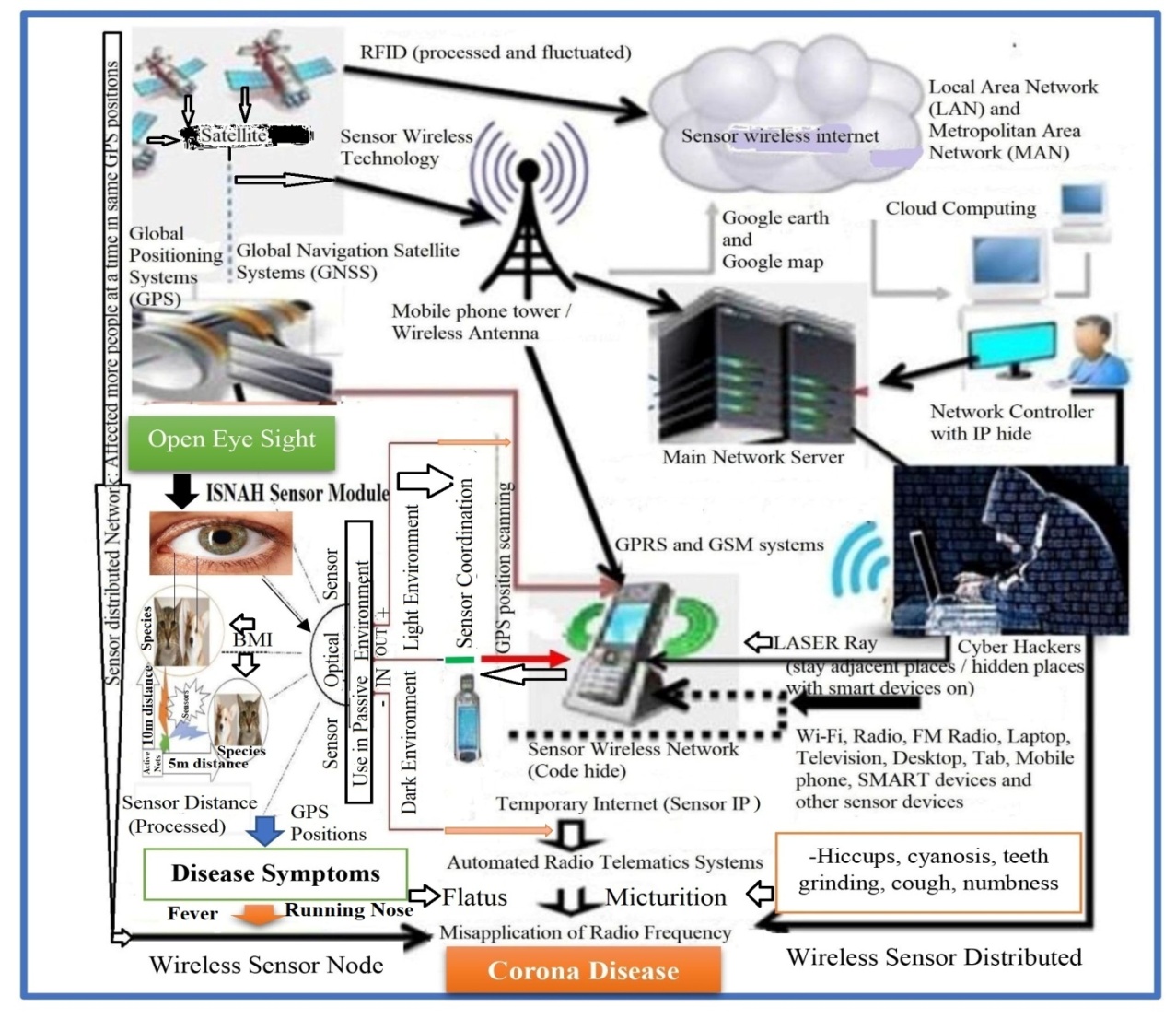 | Figure 11. Corona attack with processed radio frequencies through wireless sensor technology |
3.9. Coronavirus Recovery Rate
- The Coronavirus disease recovery rate varied in different situations including underweight, overweight and obesity patients, light and dark conditions, active GPS sensors and locations, wireless sensor networks and active open eyes. The recovery rate of coronavirus was 93.10% in February 2020, but in March 2020, it decreased at 80.71%. On the other hand, due to recovery awareness among COVID patients, it was increased to 97.10% in January 2021, which is shown in Figure 12. All coronavirus diseases are produced by cyber hackers at GPS positions through misusing of wireless sensor networks. From the higher study, only 3% of respondents are known to have processed sensor networks.
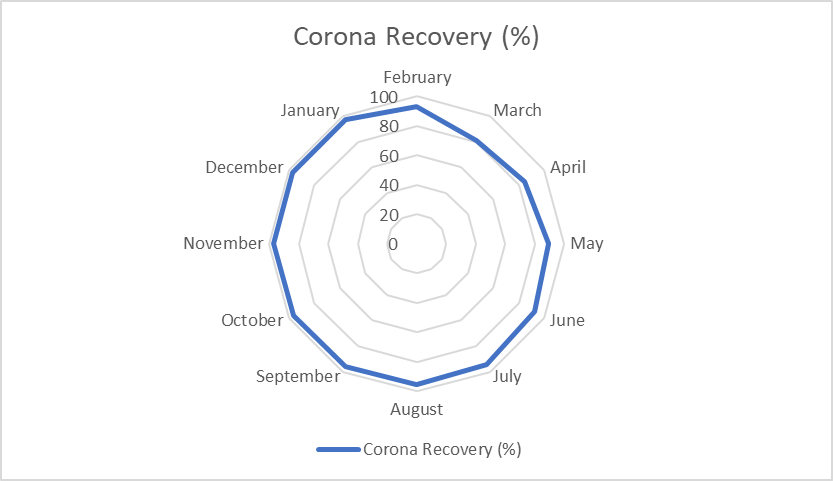 | Figure 12. Corona recovery worldwide from February 2020 to January 2021 |
3.10. Case Study on Patients with Corona
- Patients with Coronavirus were testified as a case study at Sylhet division in Bangladesh. About 150 COVID patients were sampled from North East Medical College at Sylhet. The distribution of these patients is from Sylhet, Sunamganj, Moulvibazar and Habiganj districts. Out of them, most patients were 65 between the age limit on 30-39 including male 48 and female 17. Other aged patients were 48 at age 20-29, 22 at age 40-49 and only 15 at age 50-59, which is shown in Figure 13. The maximum ages patients are downwards, which is shown as a logarithmic trendline. From the case study, the recovery rate from COVID-19 was 100% and no deaths in this study.
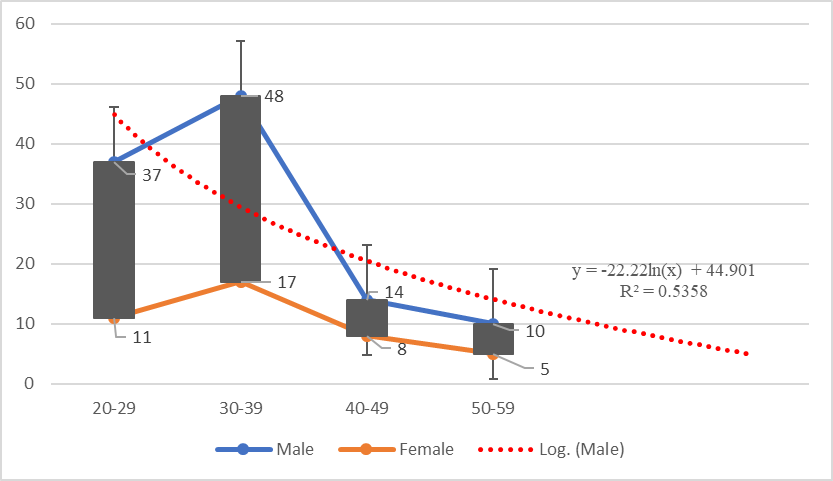 | Figure 13. Case Study on Corona patients in different ages |
3.11. ISNAH Effect on Living Cells
- The ISNAH test is the impact of the sensor network towards animals and human beings, i.e. the effect of the sensor network on humans and animals. From the study developed a formula on the ISNAH effect, which is known as the ISNAH effect. The formula is: “Due to the active sensor technology, every human, animal or object is affected by the fluctuated frequencies of its movement through electromagnetic transmission within the boundaries of the body located in the GPS position, and this effect is proportional to its weight and disproportionate to its GPS positions. As a result, the person, animal or object is damaged by the changing waves and for recovery systems, the object should change existing location instantly”. That is, the ISNAH effect is the weight / GPS position of the object.Overall findings include, (i) Processed wireless sensor networks produce coronavirus disease within GPS positions due to active open eyes. (ii) Humans locations are identified with wireless GPS sensor cameras due to creating hiccups, yawning and flatus in light and dark environments.
4. Discussion
- The finding of the study is on the effect of sensor networks towards an individual's origins of corona through misusing sensor technology. The study also represents the oxygen flow speed fluctuates with infection due to misuse of wireless sensor networks. The findings reflect the importance in corona management through prevention and treatment that the physicians provide, which fails to recover due to access abusing the sensor network’s environments. The study demonstrated the signs of individual’s location augmenting causes of corona in the dark and light environment within BMI status. In the dark environment, the obese people are more vulnerable than normal and thin individuals and vice versa in the light environment. The study illustrates to test the radio frequency of patients’ coordinates by RFID (Radio Frequency Identification) detectors with GPS (Global Positioning Systems) locations, whether the actual radio frequency pressure was abnormal in the body of those suffering from corona due to abuse of radio frequency. Each sensory system has transformed tissue containing an array of fixated neurons to sense and transduce specific physical stimuli in optical sights [43]. Human eyes are the powerful natural close circuit camera, which focuses optical sight within a GPS position. Through assimilating adaptive optics micro-stimulation with high-speed eye tracking, the retinal function can be explored at the level of the individual cone photoreceptor in active eyes [43]. The eye offers one exception to this situation, with the cornea and lens affording a view of the retina that is only obscured by imperfections in the optics. Recent advances in ocular imaging now make it possible to overcome these imperfections and image individual photoreceptors in the living retina [44]. Besides, the strength and directions of temperature and orbital vibration signals can be monitored with sensor devices [103].
4.1. Corona as a Sensor Technological Virus
- Corona is a sensory technical virus to spread as a non-communicable disease in animals and human beings. This virus is not biological,it is spread by technological programming and remote sensing. But somebody and institutions demonstrated that coronaviruses were found in bats [134]. Actually, these viruses were produced by cyber hackers through processed wireless sensor networks and receptors from individual’s retina. That's why after the introduction of corona in China, it spreads directly to Italy and later to other countries without spreading to neighboring countries. This is because a group of cyber hackers were directly abusing technology through the Clouding Sensor Network. Moreover, the symptoms of diseases like Corona, SARS, MERS and Ebola are almost the same, only the names are different. Wherever a person or animal is in the state of consciousness with open eyes, the movement of electrons according to the position of the organ in that person's body can be obstructed by telematics in the GPS position, resulting in the above symptoms. That's why Corona is a technological virus. When cyber hackers misuse homogeneous or procedural frequencies to a specific person or animal at a given geographical distance through sensor technology, the person soon develops the following symptoms and becomes ill, such as: (i) sudden yawning, (ii) sneezing, (iii) cold, (iv) Fatigue, (v) Cough, (vi) Fever, (vii) Hiccups, (viii) Discoloration, (ix) Sore throat, (x) Increases asthma, (xi) Anorexia, and (xii) sudden difficulty in breathing. This effect disseminates from smart mobile phone, where two thirds of the global populations are unique digital phone subscribers [36]. Moreover, no death in corona disease at some countries and territories due to technological awareness, such as, (i) Cambodia, (ii) Laos, (iii) Vanuatu, (iv) Dominica, (v) Macao, (vi) Micronesia, (vii) Samoa, (viii) Wallis and Futuna, (ix) Marshall Islands, (x) Anguilla, (xi) Saint Pierre Miquelon, (xii) Solomon Islands, (xiii) Vatican City, (xiv) Greenland, (xv) Falkland Islands, (xvi) Saint Kitts and Nevis, (xvii) New Caledonia, (xviii) Timor-Leste and (xix) St. Vincent Grenadines [8]. On the other hand, maximum deaths in some countries due to lack of dynamic sensor security, (a) The 389,621deaths from COVID-19 in USA, which is the highest in the world, (b) The 204,726 deaths in Brazil, which is the second ranking in the world, (c) The 151,564 deaths in India at third position in the world, and (d) The 135,682 deaths in Mexico at fourth ranking in the world [8].
4.2. Who is Creating the Corona Virus?
- A team of Cyber hackers has created 362 diseases till to December 31, 2020 [Appendix C] including coronavirus disease through misusing of advanced sensor technology in humans, animals and plants worldwide, and is creating more new diseases through cutting edge nano-sensor technology. Cyber hackers have a four-member of management team. Three of them are involved in the operation and one is a sheltered for them. The pseudonyms of these four are: (i) Tangal Pharaoh Bari Hatem, (ii) Narsi Nimrud Jasim, (iii) Chichang Karun Nizam, and (iv) Mohakhali Candle Taj [135]. Each of them has four sub-groups. Each subdivision has a separate division of responsibilities based on area or country. They use sensor technology from time to time to create new names in human or animal bodies for specific frequencies with telematics, spreading them in different ways. Again, they spread in the media that the person concerned had died of such a disease. In this case, you have to be very careful. The research has shown from the ISNAH (Impact of Sensor Networks towards Animals and Human beings) effect that the GPS position of humans and animals can be determined by coding the retina light rays of their eyes. Digital poisoning at the GPS location interferes with the movement of electrons in the body of humans and animals, i.e. oxygen in the trachea and blood flow to the heart. Cyber hackers create this barrier through misusing of sensor technology within GPS location. Educational institutions were closed due to pandemic coronavirus. According to policy, vaccines are limited for school students. From my study, all animals and human beings are affected in processed wireless sensor networks. So, the vaccine policy is also bouncing message, if it is verified its authentication.
4.3. How to Detect Cyber Hackers
- For effective measure, the higher authority takes necessary action against the misusers of sensor technology. But the authorities are not aware the global cyber crime due to lack of trained-up officials on advances in nano-sensor technology. For this reason, there is a combination between general public and administration for detecting the cyber hackers at local, national, regional and global levels. By co-operating with the police and the public, cyber hackers can be detected and appropriate and dynamic measures can be taken to remove corona disease through law and administration [135]. However, no words, sounds, mobile phones, wireless / networks can be used while searching for cyber hackers. For their own safety of the security team, the police can use weapons and the public can use sticks or defensive measures. All countries must have all kinds of networks and electricity off during special operations at the same time. And when meeting all the acquaintances / strangers, the higher authorities have to make sure that the smartphone or electronic device of the person concerned is off or 6 feet away, so there is no need to be worried or frustrated. Allah said (interpretation of the meaning): “And do not be anxious nor grieved” [80]. Telematics is a type of sensor light made with sensor technology, which works in combination with atmospheric waves. Cyber hackers scan the retina of the human eye with sensor technology to find out its current location and monitor every moment. The advantage of using decision support interlinks with wireless sensor network [47]. Recent progress in the use of bio-metric identifiers and simplified electronic medical record systems will mean that this is possible [48]. As a result, your location will be known immediately wherever you open your eyes at the country or international border and your activity will go to the sensor server along with the image. The sensor network has to adjust to your vision in the atmosphere. Moreover, you are sitting / lying in the office or at home, working, eating, sleeping, etc. on a daily basis. At this time, even if you have a mobile phone or sensor device around you, your location is easily known. Moreover, even if you do not have a mobile phone, your location can be known through words, laughter, tears, and high-cough or open eyes. Cyber hackers find out the distance of different parts of your body from your surroundings through telematics devices, and then digital scanning is done from the neck to the head of your body with software like computed tomography (CT) scan or Magnetic Resonance Imagery (MRI). Then the low frequency electromagnetic sensor force is applied to the voice box and trachea of the place through smart remote sensing with the help of telematics. For a while, the person feels a tingling sensation, the body temperature rises, sneezing-coughing, or yawning, hiccups and the body fades, hypnosis, runny nose, loss of appetite and dryness in the airways. After the smart mobile sensor is contracted, the airway becomes constricted and the tracheal cartilage becomes more constricted and the air stops moving from the lungs, then the person suffers from shortness of breath and dies within a few minutes. And cyber hackers spread the fake word in the media that he died after being attacked by Corona. Allah (The Creator) said in the Noble Quran as [87]: Evil (sins and disobedience of Allah, etc.) has appeared on land and sea because of what the hands of men have earned (by oppression and evil deeds, etc.), that Allah may make them taste a part of that which they have done, in order that they may return (by repenting to Allah, and begging His Pardon).
4.4. Treatment
- If the corona virus was biological, its treatment would be very quick. But because it is a sensor technological virus, it is very difficult to get proper treatment. Although various companies and organizations are talking about the discovery of anti-corona, how effective it will be in curing the disease is a matter of dynamic research. The research has shown that 80% of the disease needs to be treated through psychological and 20% through physical therapy and medicine. Controlling seven places for sustainable non-communicable disease management, this is to prevent the state-of-the-art of various aspects of wireless body area sensor network [54]. Moreover, the advice of a doctor experienced in medical sensors can be taken in this regard to advance the field of disease care [55]. If a person lives in a remote area where there is no regular registered doctor. Then he has to think of alternative arrangements. For example: as soon as any symptoms of corona disease appear, you need to move quickly. There will be no mobile phone or Wi-Fi of any kind with any person moving to a new place, and no words or words will be spoken, all kinds of gestures will be communicated until normal. Individuals stay 2-6 feet away in each case for at least 2 to 6 minutes. The network control unit or jammer machine or network isolator must be set up where the sick person will be located. Whenever a person feels sneezing, coughing, yawning chills and headache or discomfort, his current condition must change immediately. The sick person should wear sunglasses over his eyes, never sleep or stand in the dark, and drink regular lemon-ginger tea until he recovers. In addition, a teaspoon of lemon juice, a paracetamol (800 mg) and a glass of oral saline should be taken together. Regularly the person eat garlic, black cumin, neem leaf powder and honey together and change his/her bed position from time to time for good health and be very careful in using smartphone. Anti-radiation bed and mosquito net must be used in bedroom and facility-based care when it is needed [56]. The obese patients are risk in COVID-19 due to respiratory syndrome [88,89,90,91,92,93,94].The treatment of coronavirus disease is simple. It includes three steps, which as shown in Figure 14, such as: (a) Pre-treatment, (b) Treatment, and (c) Post-treatment and follow up.
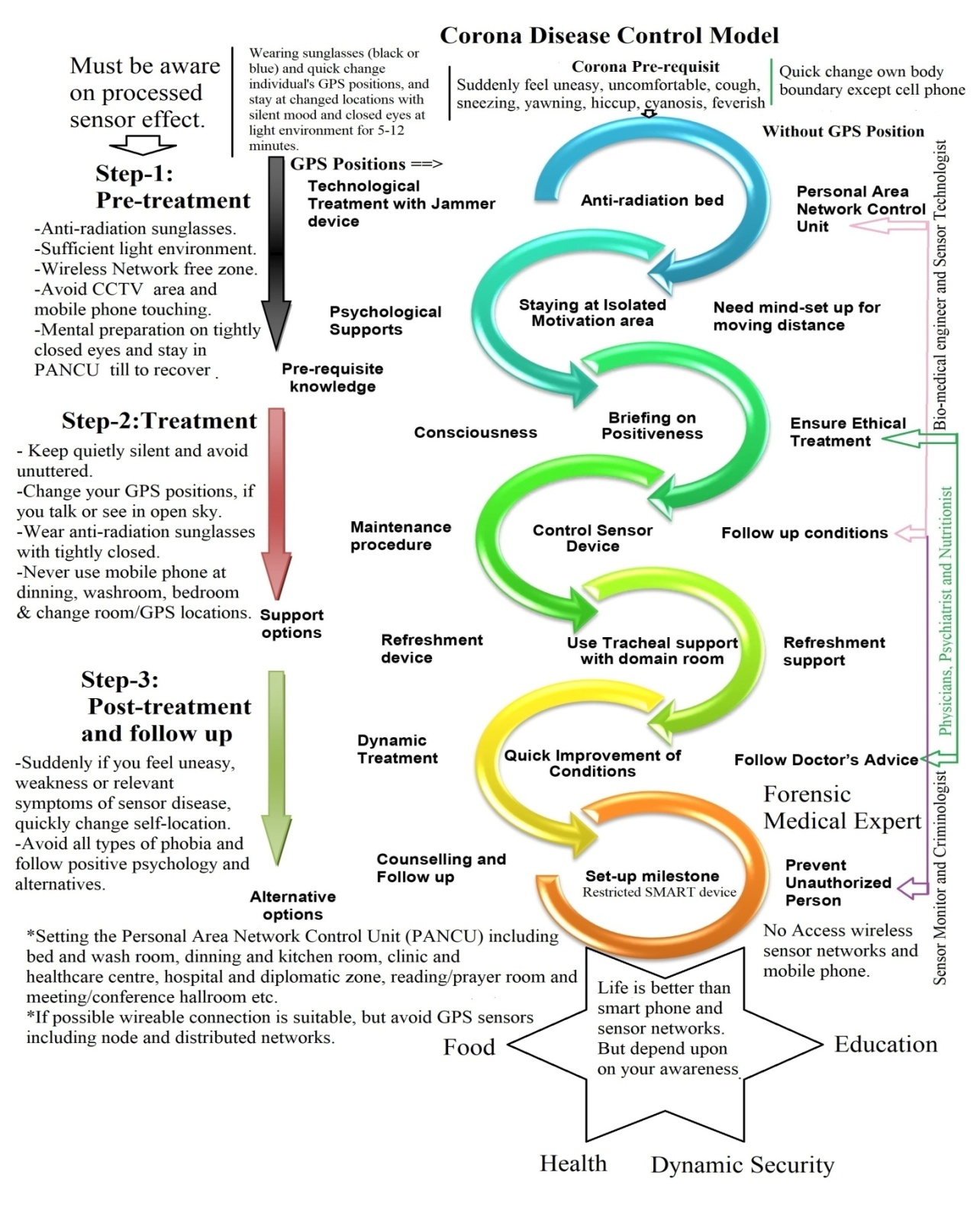 | Figure 14. COVID-19 Treatment Steps [15] |
4.5. COVID Care Pathway
- The COVID patients are being focused with regular follow-up to instigate their recovery phase after home isolation. They take in terms of sensor technological and nutritional direction in their home-setting is frequently inadequate. The right information these COVID patients take in terms of nutritional support at their home-setting is accommodated suitably. The scientific experts and dietitians are being anticipated to support them with effective guidelines and a care pathway for healthcare setting at wireless network free place or personal network control area [106]. The area is always effective light condition, anti-radiation sunglass and nutritional supports for them till to fully recover.
4.6. Global Corona Disease Recovery Systems
- COVAX is a global solution for COVID-19 treatment providing vaccines for controlling with effective testing and preventives measures [82]. Treatments give these tools to help patients to treat COVID-19 [83]. Furthermost people who suffer corona disease caused by SARS-CoV-2 will have only mild illness. Mild corona disease cases still can make individual feel crummy. But he/she should be able to rest at home with positive psychological mind and recover fully without a trip to the clinic or hospital. He/she should follow the personal body boundary network control unit or stay free Wi-Fi or Mobile Sensor Network till to sound health. Scientists, physicians and researchers are continually tracking contagions and recovery system. As a scientist, my findings for recovery is simple. During staying at home/office, he/she must be showed accepted signs or symbol except words/speeches to communicate with others and wears sunglasses for minimizing own’s optical sight. Mask use is not recovered from corona disease. Again, there is no relation between application of mask and corona recovery. But cyber hackers send messages to the main health administration for development of policy on mask applicability. Most health administrators have no idea on bouncing message and voice coding. As a result, they circulate policy to the security force. According to the rules and regulations, the security force monitors the general people. Public suffers in disease and punishment from cyber hackers and police respectively.
4.7. Sensor Disease Management
- According to Isaac Newton’s 3rd Law of Motion illustrated as for each and every action, there is an equal and opposite reaction. Modern wireless Sensor Technology has the same condition as for advantage and disadvantage in the application of processed and fluctuated radio frequencies. Due to processed radio frequencies, a lot of sensor infections and negative effects produce within positions of longitude, latitude and ellipsoid height. These infections and disorders convert into sensor diseases in living cells of human beings and animals’ body. Every sensor disease is dangerous due to blocking of electron transmission in GPS positions. This GPS coordinates points block the transfer of oxygen, carbon dioxide, water, blood and other fluid materials through misusing of processed and fluctuated wireless sensor networks. If individual is affected by this type of WSN, he/she must change his/her existing GPS location quickly for safety nets. Otherwise tends to being dead indeed within few minutes due to misapplication of overlapped and homogenous radio frequencies. The cyber hackers are misused these radio frequencies for spreading sensor diseases from January 1, 2000 to till date due to lack of effective sensor security. They produced 362 common acute sensor infections and disorders (CASID) till to December 31, 2020. They disseminate unwanted types of radio frequencies in human beings and animals’ body to spread CASID. Some diseases like COVID-19, heart attack, diabetes and cancer etc. are major sensor diseases from CASID. Someone can puzzle on my research or none can believe due to diverse causes, such as: (i) Habituated in Personalism, (ii) Lack of perfect sensor technological awareness, (iii) Superstition, (iv) Infodemic, (v) Nepotism with cyber hackers, (vi) Cyber hackers oneself, (vii) Obsolete person, (viii) Phobia person in sensor disease, (ix) The person, who kidnapped and threatened by cyber hackers, and (x) Cybercriminal. The CASID can result in significant morbidity, if not appropriately diagnosed and treated in real time and GPS location. There are some sensor parameters like fluctuated radio frequency, GPS location, optical sight, existing environment and body boundary areas of the spreading infections and disorders etc. are important guides to initial treatment strategies. When CASID is augmenting in living cell due to passive processed radio frequencies at optical sight within GPS location, it must treat as soon as possible. The CASID recovery management team consists of the following teams for rebuilding a CASID core team (Figure 15), such as (i) Real-time Anti-radiation processed intelligence device (RAPID) team, (ii) Spatial monitoring and reporting tools (SMRT) team, (iii) Patients’ antiradiation bed-room-zone team, (iv) Wireless sensor networks access control unit team, (v) Medical police and security team, (vi) Hospital co-management team, (vii) Team for management of patients, (viii) Emergency hospital petrol group, (ix) Clinical management team, (x) Laboratory technicians and experts, (xi) Corona disease/ sensor disease identification team, (xii) Intensive support and reporting team, (xiii) CASID case management team, (xiv) Corona disease/ sensor disease treatment, recovery and follow up team, (xv) Regular nurse’s forum, (xvi) Proactive doctor’s forum, (xvii) Personal Area Network control Unit (PANCU) and interface identifier team, (xviii) Intensive assessment and evaluation team, and (xix) Dynamic CASID Core Team.
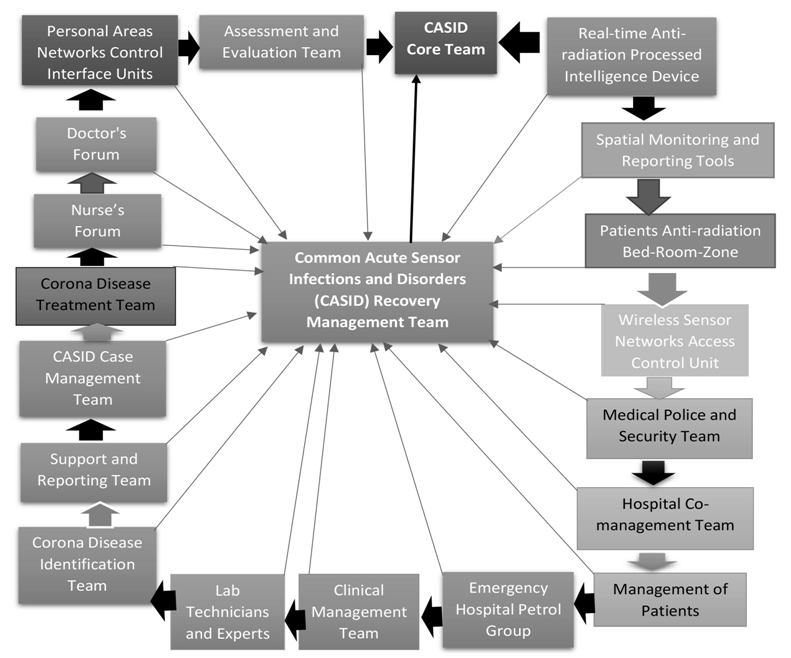 | Figure 15. Common Acute Sensor Infections and Disorders Recovery Management Team |
4.8. Global Uniqueness Research
- Optical sensors are integrated with a radio transmitter/transceiver in a GPS position [115,116,117]. The wireless processed sensor network is a uniqueness research in relation with biology and sensor technology in advances. So, it advances in bio-sensor research to improve the capacity of healthy life. This is rare and limited awareness in the modern world due to integrated study for all generations. It opens the research door with scientific access to multidiscipline. There are some uniqueness in this research as (a) Quick sensor network affected towards man, animals, plants and landscapes, (b) Disseminate the distributed sensor network to the whole network areas through individual or group wise, (c) Large animals are more prone to be negatively affected by sensor telematics network because of peripheral congested environment and splitting high frequency, (d) The radio frequencies of telematics (500 to 999 mHz) were detected using Automated Radio Telemetry System within the 5 and 10 meter distances, and (e) Exposure high RFID detects to die.
4.9. Worldwide Potentiality
- Ambiguous on the magnitude of pandemic impact, coronavirus could rapidly alter a geopolitical event. This virus tarnished global history due to lack of secure sensor technology with changing economic, technical, social and health impacts [114]. This learning has the potential to change the global direction for looking ahead. It can enhance security systems for teacher, medical doctors, nurse, officer, scientists, researchers, patient and other stakeholders. Experts have tried to implement ways of reducing this impact by encouraging pertinent institution to go competitive market with medical through alternative potentiality. Large potential on RFID technology uses including learning, research, servicing and access benefit sharing to achieve specific goals related to national health policy in connection with Sustainable Development Goals 2030.
4.10. Safety Geo-health-politics
- The world is facing an unparalleled health crisis through misusing of cyber hacker’s activity [107]. Due to the spreading coronavirus, the geopolitical tensions are escalating, which hampers in global healthcare policies [108]. This pandemic is a tactical shock as the extreme threat to the global order and political leaders, which are interrupted the global economy, political relations and health policies through challenging the strength of humanities and social relations [109,110]. Sometimes political leader behaves an insane suddenly to the mass people due to tracking at his/her brain by the cyber hackers within GPS locations. Again, national political instability, mutiny among soldiers and army illegal empower etc. are occurred by cyber hackers through misusing of sensor technology like interfacing, voice coding and bouncing messages [15]. The world of geopolitics is shifting speedily exciting from a phase of virtual solidity to one. The disconcerting and insecure sensor network link to social, technical, and personal uncertainty is also conveying about cutting-edge technology and political changes. These are more inward looking not only nationalist but also individualist, protectionist and dogmatic shape due to undesirable situations [113]. Presently the integrated decision necessitates the reconsidering state policy approach and target-oriented achievements. So, it is urgently necessary the safety geo-health sensor technology for all civilians and the eminent political leaders.
4.11. Message of Sensor Technological War
- COVID-19 is a message of third world war. The coronavirus has exaggerated the entire world, which escaped the horrors of the previous World War I and II. These coronaviruses were spreading unambiguously everywhere in all countries. People are already aware that it will take months if not years to end the COVID-19 conflict, which became painfully obvious that the conflicts during world war I and II would go on and on for months and years. Both these wars were also misnomers. The World War I ended with roughly 20 million people dying, which is comparison with COVID-19 deaths [136]. The coronavirus pandemic has confirmed the disturbing potential of viruses as a weapon of mass destruction, reduction of social rapport building, distancing in religious activities, which have transformed the concentration, dimension and trajectory of an undeclared third world war and, in its aftermath, could conceivably transmit about a revolution in the global order [137]. The world is in turmoil from racial injustice to rising inequalities due to pandemic COVID-19 [138]. These World Wars were named with retrospective effect to all generations. From the higher study, it is informed that COVID-19, suddenly earthquake, tsunami, cyclone, rainfall, forest fire, building burning, load shedding, soldiers’ mutiny, plane demolish, family clash, vehicles’ accident, political instability, landslide, winter storm, building fallen down etc. have been occurred by cyber hackers due to misusing of wireless sensor networks.
4.12. Looking Ahead Research
- As new technologies continue to emerge, human beings, animals and plant’s roles will continue to evolve, with each advance, bringing a safer and healthier future for both researchers and the students’ motto in their domains. As researchers, scientists, engineers and network specialists continue to make leaps forward with these innovations, more lives will be saved and more research will receive assistance. But there is general question, “who is secured in the world at the insecure wireless sensor technology, which as shown as Figure 16. Every life is better than smart phone and wireless sensor networks to depend upon in awareness. Risk of reinfection depends on the likelihood of re-exposure to infectious cases of coronavirus, who are mild to moderate the replication-competent virus has not been recovered after 10 days [118-132]. So, the present world is in risks to live insecure life. The chief executive of State of United Nations is also insecure, if he/she has rapid action batalian (RAB), army, special force, police and other security team due to misusing with nano-sensor technology and open active individual’s eyes. The study mentions for effective future research directions for global public health security.
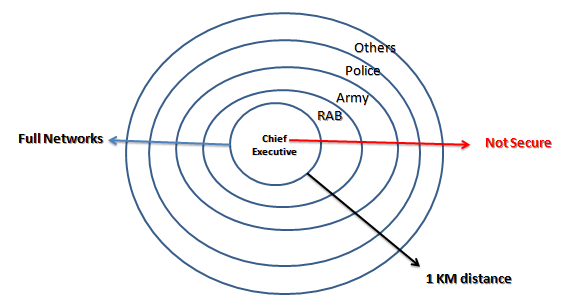 | Figure 16. Who is secured by wireless sensor networks within GPS location |
4.13. Risks in Research
- The major challenge is the stimulation of individual neurons is difficult when individuals sit within an array of similar receptors, with the array itself hidden inside a sensory organ [48]. False interface, bouncing message [Appendix B] and voice coding [Appendix A] are increasing through sensor technology due to lack of effective security [16]. Because, sensor nodes are capable of transferring data without physical medium [102,104]. Cyber hackers spread the fake information in the media that he died after being attacked by Corona [16]. Despite the spread of information technology, it is very difficult to find the right antidote to cure corona disease [57]. Many mobile phone users are not aware to overcome the health security measures of sensor technology [58,59]. Cyber hackers are scattered among different groups of society and are arbitrarily abusing it [60]. Many people are not aware of the police and other security forces due to using GPS data from the environment [60,105]. Moreover, many people are using smartphones without control of the waves, without following any rules and regulations [60]. As a result, various non-communicable diseases including corona are increasing abnormally [15,61]. Therefore, corona is a huge challenge for the World Health Organization, including the national governments, organizations and communities [7]. There are huge misuse of sensor technology and cost of update technology in health management [53]. The research organization develops a set of recommendations for all countries to recover [54] corona with its challenges. The use of low-cost digital sensor devices can measure vital signs in risks [55]. At present, few low-income countries have reliable sensor data despite substantial investments in health information systems [56,62] but sensor security system is weak. The crowdsourcing data about providers, facilities, and health systems is likely to grow as more people with sensor in risks [63]. Violence against healthcare technology providers has increased worldwide in the context of COVID-19 for challenging treatment with insecure technology [64,65,66]. Some people believe to reduce spread and deaths due to using facemasks, social distancing, and avoid handshaking [67]. But these are bouncing messages from cyber hackers sending to the higher authority, which are almost fake. Cyber hackers highlight scamming mails, voice calls and electronic news for media exposure as an infodemic with phobia formula accelerating negative psychology towards mass people [68 -79,86] during the management of disease outbreaks as a global problem [81]. Moreover, COVID-19 treatment situation has not improved yet due to discriminatory nature of the existing health system [84].
4.14. Recommendations
- The study commends to be very vigilant to stay healthy from the misuse of sensor technology. That is why there are some recommendations in the field of awareness, which we can all benefit from following, such as:(a) Individual should close eyes with wearing sunglasses and quick-change body boundary without uttering 5-10 minutes.(b) When meeting all acquaintances / strangers, including office assistants and housekeepers, make sure that the smartphone or electronic device of the person concerned is turned off or 6 feet away. You can't meet with your own or someone else's mobile phone.(c) Avoid audio-video, talking and use of all kinds with smart mobile phones in and around the bed in open eyes.(d) The sleeping room must be without network and sensor free, no person or animal in that room can ever use the wireless network, only to be damaged.(e) The patient’s bed and mosquito net should be anti-radiation category at home and hospital.(f) To have peace of mind and not to stay in one place or bed, to move regularly and to keep occasional body movements.(g) If the effects of corona disease are widespread in a geographical area, the local, regional and international mobile and sensor networks in that areas should be disconnected for 5 to 10 minutes or suitable time.(h) The higher health authority should formulate the dynamic global health policy on the priority of cutting-edge sensor technology.
5. Conclusions
- To conclude, the World Health Organization is monitoring the spread of the virus and the viral situation in order to rapidly expand scientific knowledge about the new virus. And the agency is cooperating in consultations and intensive investigations to take necessary action on a number of issues to protect the health of neighboring countries and individuals and prevent its spread. Due to the corona virus, the doors of the world such as business, trade, education, initiation, movement and daily life are being closed. This should be monitored the illegal activities of Cyber hackers under the law with the joint cooperation of doctors, nurses, general public, police and concerned organizations. As a result, the security of the sensor technology will ensure that there will be no more corona in the area. However, no words, sounds, mobile phones, wireless / networks can be used while searching for Cyber hackers. For their own safety, the police can use weapons with sunglasses and the public can take sticks or defensive measures. In all countries, all types of networks, including mobile networks, CCTV and electricity must be turned off during special operations. However, the instructions for a special operation cannot be typed or exchanged on a computer or mobile phone, the operation guideline must be handwritten before the operation, otherwise the operation will not be successful. Therefore, as long as Cyber hackers are not caught through the law, above 362 diseases including coronavirus disease will not be free from the world [Appendix C].
6. Declarations
- FundingThis research work is a part of PhD Thesis, which was funded by the Zamalah Postgraduate Scholarship of UNIMAS, Malaysia and also sponsored by the Information and Communication Technology Division, Ministry of Posts, Telecommunication and Information Technology, Government of People’s Republic of Bangladesh. The funders had no role in the design of the research, in data collection, analyses or final interpretation of data, in the writings of the manuscript, or in the decision to publish the findings.Data AvailabilityThe data are being used to support the findings of this research work are available from the corresponding author upon request. Competing InterestsThe authors declare no potential conflict of interests in this research work.
ACKNOWLEDGEMENTS
- The authors acknowledged the authority of Universiti of Malaysia Sarawak (UNIMAS), Malaysia for providing the Zamalah Postgraduate Scholarship for the completion of PhD degree. The authors are also grateful to the authority of the Information and Communication Technology Division, Ministry of Posts, Telecommunication and Information Technology, Government of People’s Republic of Bangladesh, for PhD Fellowship during the higher study in Malaysia. The authors acknowledged the authority of Northeast Medical College & Hospital (NEMCH) Pvt. Limited, Sylhet, Bangladesh for kind supports.
Appendix A: (i) False Interface and Voice Coding
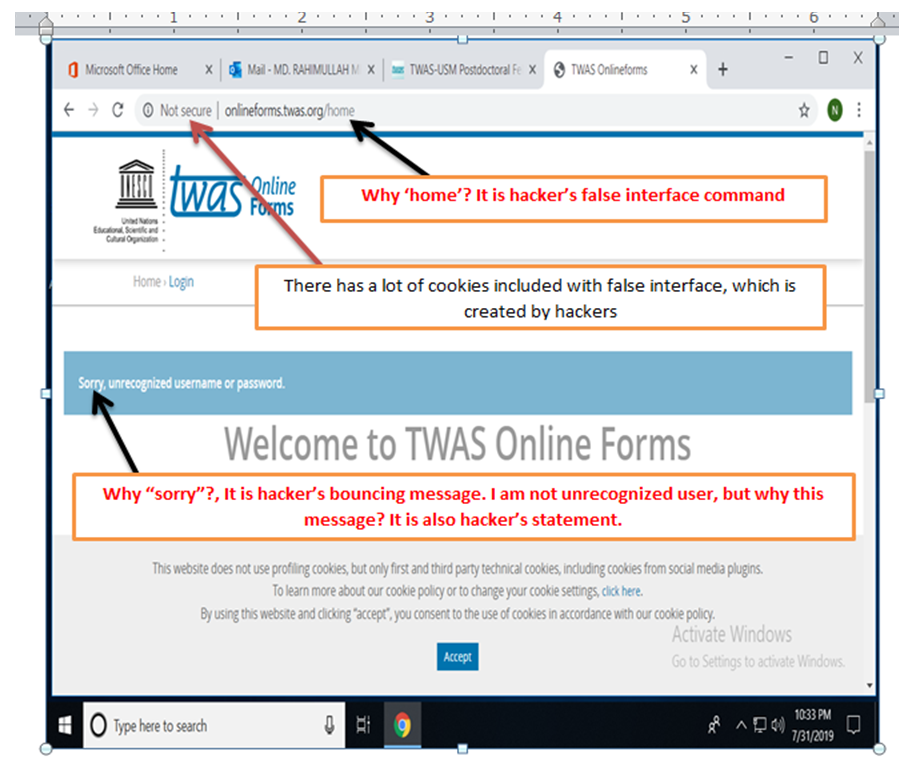 | Same event at RT-PCR, display positive, actually he/she was negative. |
Appendix B: Bouncing Message
 | Appendix B |
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML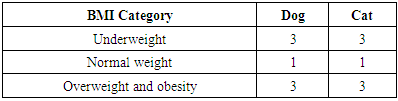

 (Accessed Time on January 11, 2021 at 7:00 am).
(Accessed Time on January 11, 2021 at 7:00 am). (Accessed time on January 16, 2021 at 8:00 am).
(Accessed time on January 16, 2021 at 8:00 am).