-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Algorithms Research
2012; 1(2): 5-11
doi: 10.5923/j.algorithms.20120102.01
Algorithm Re-Ordering: a Solution for Abating Internet Bypass
Awoleye O. M, Atoyebi M. K, Abang I. S, Siyanbola W. O
National Centre for Technology Management, an Agency of the Federal Ministry of Science & Technology, Obafemi Awolowo University, Ile-Ife, Nigeria
Correspondence to: Awoleye O. M, National Centre for Technology Management, an Agency of the Federal Ministry of Science & Technology, Obafemi Awolowo University, Ile-Ife, Nigeria.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
The use of mobile data services as a means of communication came into existence through the introduction of 3rd Generation (3G) Technology, it is expected that this technology will continue to increase opportunities for improved revenues and enable new services & tariff generation. Research have shown that the use of third party application like Tor browser, Indian proxy, Your-freedom (http://www.your-freedom.net), Privoxy etc are used to bypass the data services offered by the network providers. This is carried out by leveraging on virtual private network (VPN) technology, distributed network of relays and available free ports. This has limited the revenue derived by the providers in a country where such proliferation is thriving. In Nigeria for example Government on its part have taken some steps to finding solutions to end this menace and related increasing cyber crime activities, but the challenge still remain with us. This work thus postulates an innovative way of abating this activity which has lead to huge loss of revenue in the sector. The approach is a theoretical method in solving the industry-related problem. It narrowed down the problem of the current algorithm to improper algorithm order and thereby proposing an appropriate model to reducing the menace.
Keywords: Algorithm, flowchart, policy, internet, data services
Article Outline
1. Introduction
- History reveals that the mobile/wireless telecommunication could be traced back to the laboratory research carried out in United State in the 1920’s by means of radio telephony technology[1]. This has been suggested to be the most important device of the mobile telecommunication and as the key element to enable mobile and wireless access[5,7].The initial design of the mobile telephone was based on analogue which was characterised as the first generation (1G) of mobile phones. It was designed to carry voice only, which was then the primary function[17]. The mobile telephone has gone through a number of developmental cycles up to the advent of migration from 2G to 3G technology that have increased the market base of the network operators worldwide. There have been considerable increases in the investment on infrastructure expansion in the telecommunication industry over the years due to continuous growth and increased market demand[3.5]. Technological innovations in the transmission and switching technologies have also been reported to aid cost reduction, as well as improve accessibility of existing telecommunication services[1].In addition, deregulation of the telecommunication industry has made the market more competitive, this combined with technological advances that have resulted in a diversity of new services, most especially data transmission and video applications[2,3]. The extensive use of these services and its adoption, especially the wireless data service cannot be overemphasised. This has presented an avenue for the providers to tap into new opportunities of revenue generation in the industry. Surprisingly, despite the huge benefits of providing these services coupled with the exorbitant amount of such investments from the provider’s side, saboteurs are beginning to ravage some of the revenue that could accrue to the providers. Beyond gainsay, it has been established by the evidences around that some prepaid data service subscribers still have access to the internet even when their credit is below the threshold set by the providers to gain access to the service. This thus set us thinking about the future of this industry and some research questions are raised which this work will attempt to answer. It is expedient to raise an issue of sustainability in an arena of looming uncertainty. These questions are: (i) Will the wireless data service providers be willing to continue in the near future when the investment/overhead is no longer commensurate to revenue? (ii) Will the futility of the struggle of the providers to abate Internet by-pass kick them out of business without a reasonable solution? (iii) Is there any alternative solution (technical and non-technical) to abate this menace? This has been carefully attended to by employing algorithm and using policy suggestions as a veritable instrument of control to safe the situation. This is a theoretical approach of solving an industry related problem in Nigeria.It is worth noting to state that a number of third party software are used in carrying out this nefarious activities. Example of which are: freedom server, tor browser, ultra surf to mention a few, have been used extensively among the perpetrators. Freedom server for example has specifically listed the service providers in Nigeria with their corresponding by-pass proxy configurations and port numbers to enable data services on the third party provided network. Riding on the platform provided by the local service provider in Nigeria to access another remote system for service provisioning contrary to terms of use is viewed as a major algorithm order loophole. This is blamed on the local service providers who could not secure their network appropriately. Security has proved to be an essential aspect of telecommunication as exemplified by the inclusion of authentication of mobile terminal by the network which stopped the massive fraud that was occurring in the previous generation of analogue mobile system[14]. Attempts have been made by some of the service providers to stop this menace but it seems to be of no avail. The approach adopted mostly is to change the Internet Protocol (IP) addresses of their web proxy and related servers. This study thus employed the use of algorithm to illustrate the steps that must be taken to mitigate data service by-pass. It therefore set three objectives to achieve a main goal of preventing by-pass of data services provisioning. These are to: (i) examine the current procedure for mobile call service on how the service providers carry out this primary function; (ii) review the data service procedure with a view to present an alternative; and (iii) to advance some useful policy directions to prevent future occurrence(s) in the industry.
2. Methodology
- The approach adopted in this research is the use of flowchart to elicit the loop-holes of the telecoms operators’ activities in Nigeria with a view to proffer a suitable measure to overcome the limitations. To achieve this, a framework (flowchart and pseudo-code) were designed following an extensive literature search on the procedure employed by network operators for their voice call and data services. The research thus redirected the procedure to censor the infiltration of proxy browser users. This is to create a secure mode for data communication and tackle the concern of revenue loss.
3. GSM to GSM Call Initiation
- Mobile technology’s original function was to perform voice service only[15]. Fig.1 depicts the process of making a GSM to GSM call. This starts from the Mobile Station (MS) initiating a call by sending a request on the Request Access Channel of the Base Station Subsystem (BSS). The BSS responds with Base Transceiver (BTS) to the MS using the Assignment Channel (present in the antenna). The process is carried out so as to allocate a specific voice channel to MS. The BSS then send a request to the Mobile Service Switching Centre (MSC), thus this initiates a call. The MSC perform the necessary authentication with the aid of the Home Locator Register/Visitor Locator Register, Authentication Centre and the Equipment Identity Register. The Home Locator Register (HLR) holds the Subscriber Identity Module (SIM) information and its associated location. The Authentication Centre (AUC) verifies the SIM to identity, the Equipment Identity Register perform the verification of the Mobile Equipment (mobile Phone). After the authentication, the MSC check the threshold value of the callers SIM to ensure the value is at least a minimum value to initiate the call. The MSC thereafter sends a message to the BSS of the called party. The BSS verifies the called party to ensure it is within the coverage area, otherwise it checks whether or not the called party has a voice mailbox activated. If it is not activated it terminates the call, but if voice mailbox is activated it prompts the caller to drop a message for the called party, but if the user is within the network coverage area, a signal is sent to the caller that his destination has been reached. In some instances the user might be on a call and the incoming call would be terminated unless he activates the call waiting service, which function is present on the network operator’s end and also on the mobile equipment, the caller gets a call waiting request on the screen of his phone[8]. At the end of the conversation either of the party can terminate the call; in fig. 1 the called party end the call. The called mobile send a disconnect message to the BTS using the Fast Associated Control Channel. (FACCH), the FACCH is present in the antenna. The BSS then forward this message to the MSC, which then channel the request for termination to the callers BTS[5]. The BTS respond by sending release message down to the MS, the MS then respond by sending a message back to the BSS, which then send a release complete message to the MSC. The MSC then control the BSC to free that channel for any available user or release the BTS from the traffic channel (TCH) which is also present in the BTS[14,15].
3.1. The Procedure for Mobile Wireless Data Service
- The advent of 3rd generation technology gives rise to Data service which comes either in circuit data or packet data[4]. This process is initiated when the user clicks on the connect button to request for a network connection through the modem which is connected to a computer. The modem then sends the user request to BSS through the BTS. The BTS directs the modem to dial the Internet service provider’s (ISP’s) phone number which is answered by another modem at the receiving end. The modem sends a control signal back and forth harmonizing connection between the user and the ISP’s modem to determine the connection speed. Once the connection(speed) is established the mobile service switching centre (MSC) which consist of Authentication Centre (AUC) and the Home Location Register (HLR) send the username and the password to the ISP, using a process called Challenge Handshake Authentication process (CHAP) as shown in fig 2[8]. The GPRS Support Node (GSN) checks the username and password against the database of the active subscriber and check the threshold value of the subscriber’s bundle, once this condition is satisfied then the connection is established. After the connection has been successfully established, the browser then sends the HTTP client request to the server. The server upon receiving the request generates the requested file and begins the transmitting process[4].
 | Figure 1. Initiating a GSM – GSM Call |
 | Figure 2. Current Data Service |
3.2. Description of a Typical Data Service by-pass
- Owing to the various benefits associated with the use of new technologies, there has been increasing demand especially for data services which gives access to surfing the Internet. This had left the service providers with the various challenges of meeting their high rising demand. The focus of these service providers had been prioritized on their ability to meet up with the demand of their subscribers with little or no attention on the security aspect of their network. The procedure to connect to the data service, especially the pre-paid billing plan requires a dial-up via the computer. When the request to connect is made, the system checks all the necessary conditions for authentication, if all the conditions are fulfilled then authentication is granted. It is worth noting to state here that even when the condition for balance on credit request is not met, the system still allow the authentication to be granted though with a limitation to transmit data on the provider’s server. This is where the loophole is, authenticating the modem without having enough credit balance has given the modem the opportunity to ride on this platform to a third-party server. The third party server will thereafter take it over from there and provide the data service to the subscriber. Although the data service provided is at no cost to the local service provider who originally provides the modem, but the overhead to sustain the modem online is borne by the local service provider. Some subscribers have noticed this loophole and have capitalized on it. Some have even commercialized this nefarious activity and are introducing other subscribers to it. If this should continue freely without any check, there is a likelihood that the service providers will be out of business. This is possible when all loyal subscribers are no more subscribing for their service. When the overhead being consumed on their proxy server is not paid for; this will eventually lead to huge revenue loss. This is actualized especially when the subscribers who are suppose to recharge their access refuse to do so and yet are given access to login successfully, although with limitation to surfing the Internet. To reiterate this process, successful login is all that is needed to link up with other remote server which provides access through either a VPN or an external proxy access. For example, ‘your-freedom.net’ provides different price plans as shown in Fig 3.
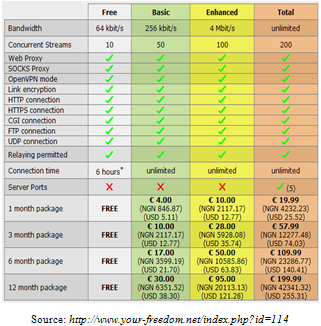 | Figure 3. price plans (packages) for remote data service |
3.3. Framework for re-ordering the Data Service
- Fig. 4&5 presents the pseudocode and flowchart respectively for the new thinking to solving the problem of the by-pass in the data services provisioning. The process is initiated by connecting the modem to the computer, the Base Station Subsystem (BSS) which comprises the Base Station Controller (BSC) and the Base Station Transceiver (BTS) directs the modem to dial the Internet service provider’s (ISP’s) data service dedicated phone number which is answered by another modem at the receiving end. The modem then send a control signal back and forth harmonizing connection between the user and the internet ISP’s modem to determine the connection speed. Once the connection (speed) is established the mobile service switching centre (MSC) which consist of Authentication Centre (AUC) and the Home Location Register (HLR) send the username and the password to the ISP using a process called Challenge Handshake Authentication process (CHAP) as shown in fig 4[6,9].
 | Figure 4. Framework for Re-Ordering Data Service Connection |
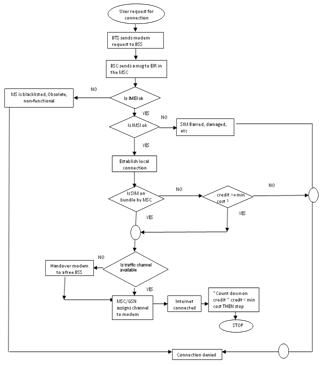 | Figure 5. Framework for re-ordering data service connection |
4. Conclusions
- This study identified a major industry-related loophole in the telecoms industry in Nigeria. This has to do with a flaw in the algorithm order of the pre-paid wireless data service. This gives the opportunity to subscribers to use their network as platform to link to other data service provider, thereby making local service providers to lose revenue to their counterparts out of the shore of the country. The major concern in addition to revenue loss is the question of sustainability and continuity for the local service providers if this practice is not curtailed. This work also studied the existing GSM to GSM call service as well as the data service in order to identify the point of the algorithm error. We thus found that providing data service to the pre-paid subscribers, they are allowed to authenticate even when the remaining credit balance does not meet up to the required value to surf the Internet. Though the system restricts access to the same for data transfer as a second level access check. Investigation thus revealed that the first level access/authentication is all that is needed to connect to a third party service provider to link the subscriber to the Internet. The third party provider thus provided some parameters to the user’s browser to redirect its request to a given proxy server and different port number. Others have also achieved this by providing software that will connect the user’s machine in a virtual private network. This work therefore has presented a new procedure that will re-order the pre-paid billing & connect algorithm. The first level access to authenticate is not granted unless enough or the minimum credit balance is detected before access is granted. This presentation will follow what is at the moment operational with the prepaid call service. With the prepaid call service, once your credit is exhausted you are not allowed to connect. If this procedure is copied to the pre-paid wireless data service then the chance of overcoming the age long menace stands strong.
5. Policy Recommendations
- It is expedient that this anomaly is corrected hence the providers will suffer for it and in return it will impact the countries’ GDP. This is possible when the perpetrators network continue to grow and in return shrinks the number of loyal subscribers to the local service provider. To this end a number of policy recommendations are therefore advanced in this direction, and the ideal role for the key players, i.e the service providers, the government and the citizens (subscribers) are reiterated.The service providers must include a clause to bind the subscribers and users of their products and services to exclusively use it for the purpose and their service alone. Any defiant should be forewarned and threatened with SIM barring and possibility of prosecution. If this already exists in the terms of use then it must be enforced, and reminder should be sent to subscribers at intervals. They can also make the subscribers to occasionally re-affirm their loyalty before access is granted. If this is done, there will be enough evidence tenable in court against any defiant. Once this is put in place then it becomes binding on the users and this will serve as deterrent especially when a few offenders have been punished. In addition, the service providers also should be given incentives to loyal subscribers such that if they have been loyal to their subscription for 11months then the 12th months be given free. This way, subscribers will not exert their energy looking for ways to defraud them or looking for alternative ways of by-passing the payment. They should also at regular interval carry out analysis on the usage i.e. traffic flow on their network relative to income generated within a certain period. This promises to show some hidden pattern especially when data mining principles are employed. Some of which amongst others are possibility of outliers, which ordinary inspection cannot reveal. If any outlier is noticed then it must be thoroughly investigated. A public domain can also be created which will facilitate reporting of any act of indiscipline on a named network. Individual service providers can dedicate a sub-domain for this on their websites.The government too on their part should play a supervisory role by ensuring that the service providers deliver their promises with good quality of service. They must also ensure that the citizens are not extorted with unreasonable cost on the services. Since liberalization of the sector which is over ten years now, it is believed that by now the cost of the services should be relatively affordable and cheap. Then the government in return should further provide enabling environment for the smooth running of their services, such as provision of stable electricity which will go a long way in saving the cost of alternative power generation which the service providers are already incurring. The government also should also cut down on the tariff imposed on the service providers.The subscribers also should be advised to act responsibly and should know that to keep those services available and running smoothly they have to play supportive role by paying correctly for the services.
ABBREVIATION
- GSM: Global System for Mobile communicationBSS: Base Station systemBSC: Base Station ControllerBTS: Base Transceiver StationGPRS: General Packet Radio System 3G: Third Generation2G: Second GenerationPC: Personal ComputerMS: Mobile StationSIM: Subscriber Identity ModuleAUC: Authentication CentreEIR: Equipment Identity RegisterHLR: Home Location RegisterVLR: Visitor Location RegisterUSRP: Universal Software Radio PeripheralFACCH: Fast Associated Control ChannelTCH: Traffic ChannelISP: Internet Service ProviderGSN: GPRS Support NodeHTTP: Hyper Text Transfer ProtocolCHAP: Challenge Handshake Authentication ProcessIP: Internet ProtocolPPP: Point-Point ProtocolMSC: Mobile Service switching CentreIMSI: International Mobile Subscriber IdentityIMEI: International Mobile Equipment Identity
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML