-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Signal Processing
p-ISSN: 2165-9354 e-ISSN: 2165-9362
2011; 1(1): 12-16
doi: 10.5923/j.ajsp.20110101.03
Performance Analysis of Suboptimal Spectrum Sensing Algorithm in Cognitive Networks
D. T. Do
Department of Communications Engineering, School of Electrical and Electronics Engineering, Ton Duc Thang University, Ho Chi Minh City, Vietnam
Correspondence to: D. T. Do , Department of Communications Engineering, School of Electrical and Electronics Engineering, Ton Duc Thang University, Ho Chi Minh City, Vietnam.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Recently, both optimal and suboptimal spectrum sensing approaches have attracted extensive attention in wireless communications field. Thanks to opportunistic spectrum access schemes, different cognitive users can cooperatively search for and exploit instantaneous spectrum availability. In this paper, we address the analysis of spectrum sensing in opportunistic spectrum access models and then determine throughput of the cognitive radio system. Our goal in all designs is reach optimal access policy for each channel with the high cooperative sensing performances.
Keywords: Cognitive Radio, Spectrum Sensing
Cite this paper: D. T. Do , "Performance Analysis of Suboptimal Spectrum Sensing Algorithm in Cognitive Networks", American Journal of Signal Processing, Vol. 1 No. 1, 2011, pp. 12-16. doi: 10.5923/j.ajsp.20110101.03.
Article Outline
1. Introduction
- It is well-known that the current spectrum management policy has resulted in an under-utilized spectrum[1]. In order to enhance limited spectrum resource, cognitive radio (CR) network is proposed. Especially, cognitive radio is considered as a key technology to deal with this increasingly tense situation in spectrum use. It enables public access to those unused spectral range by allowing the unlicensed (cognitive) users to opportunistically access to the licensed spectrum, and therefore the overall spectral efficiency can be economically increased. Basically, the secondary user (SU) to search for and utilize instantaneous spectrum opportunities left by primary user (PU), while limiting its interference to PU. Related to the spectrum opportunities, the SU should first model PU’s behavior. In the previous literature, they proposed two models, namely, discrete-time and continuous-time models. In discrete-time model, both PU and SU are time-slotted. It can be seen that, in[1], an opportunistic MAC protocol with random and negotiation-based sensing for ad-hoc networks is proposed. With the optimal spectrum sensing and access strategies, we often concern that the synchronization issues of all PUs and SUs in discrete-time model is necessary. In fact, it causes more overhead and time offset may be fatal for SU’s MAC strategy. In[2, 3], the optimal sensing period is derived for the simplest single-channel model.Methodology is designed to sense the spectrum in areliable manner becomes one of the major challenges in implementation of the cognitive radio. Due to complex channel fading and shadowing effects, the received signal strength at the cognitive user may be severely degraded, and the sensing performance of the single detector is limited. As a result, cooperative spectrum sensing approaches, which can enhance the sensing performance, have attracted extensive attention. In literature, a number of opportunistic spectrum access strategies have been investigated for cognitive network. Most of them are based on the assumption that each of the cognitive users has the full spectrum sensing ability for wide spectrum band. In real condition, due to hardware limitation, the cost to achieve wide-band spectrum sensing by one single cognitive user is quite high[4, 5]. And it is realistic that a cognitive user is able to sense limited bandwidth of spectrum during a certain amount of time.Medium Access Control has an important role in several cognitive radio functions: spectrum mobility, channel sensing, resource allocation, and spectrum sharing[3]. Spectrum mo- ability allows a secondary user to vacate its channel, when a primary user is detected, and to access an idle band where it can reestablish the communication link. Channel sensing is the ability of a cognitive user to collect information about spectrum usage, and to maintain a dynamic picture of available channels. Resource allocation is employed to opportunistically assign available channels to cognitive users according to QoS requests. Spectrum access deals with contentions between heterogeneous primary and secondary users in order to avoid harmful interference. Multi-channel MAC protocols for ad-hoc wireless networks have represented a first step in the development of MAC protocols for cognitive radio in unlicensed scenarios. These protocols address similar problems; they operate in a multi-channel context, and face the multiple channel hidden terminal problems[4]. A cognitive radio may exploit, however, increased sophisticated sensing functionalities; it distinguishes between primary and secondary users, and provides protection to licensed transmissions. The number of channels available at each user is fixed in a multi-channel network, while it varies with time and space in a cognitive network. Furthermore, the time-scale in which a cognitive radio operates is very different from that of an ad-hoc radio: secondary users must exploit periodical sensing to be aware of the wireless environment evolution, and must rapidly adapt their behaviour to reach QoS.In this paper, we mainly contribute to design of Medium Access Control (MAC) layer which has an important role in several cognitive radio functions: spectrum mobility, channel sensing, spectrum resource allocation, and spectrum sharing[6]. We can analyze these procedures carefully. Firstly, spectrum mobility allows a SU to vacate its channel, when a PU is detected, and to access an idle band where can reestablish the communication link. An then channel sensing procedure help cognitive user to collect information about spectrum usage, and to maintain a dynamic picture of available channels. While resource allocation is employed to opportunistically assign available channels to cognitive users according to QoS requests. Interestingly, spectrum access approaches deals with contentions between heterogeneous primary and secondary users in order to avoid harmful interference.In the cognitive communications, Multi-channel MAC protocols for ad-hoc wireless networks have represented a early development of MAC protocols for cognitive radio in unlicensed scenarios. Unfortunately, these protocols address similar problems; they operate as multichannel systems, and face the multiple channel hidden terminal problems[6-8]. It is true that a cognitive radio may increase sophisticated sensing functionalities; it distinguishes between PUs and SUs, and provides protection to licensed transmissions. The number of channels available at each user is fixed in a multi-channel network, while it varies with time and space in a cognitive network. Furthermore, the time-scale in which a cognitive radio operates is very different from that of an ad-hoc radio: secondary users must exploit periodical sensing to be aware of the wireless environment evolution, and must rapidly adapt their behavior to reach QoS and comply with interference constraints.The rest of the paper is organized as follows. In section II, we introduce the system model for MAC layer design in Opportunistic Spectrum Access requirement. Next, we analyze the optimal spectrum sensing scheme in different scenarios in section III. The numerical results are presented in section IV and the concluding remarks are pointed out in section V.
2. System Model
- We consider a spectrum consisting of M channels in this paper. Each channel has the bandwidth
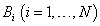 . These N channels are licensed to a primary network whose users operate following the synchronous slot structure. The traffic of all of the PUs are such that the occupancy of these N channels obeys a discrete-time Markov chain with
. These N channels are licensed to a primary network whose users operate following the synchronous slot structure. The traffic of all of the PUs are such that the occupancy of these N channels obeys a discrete-time Markov chain with 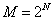 states. The network state in the slot is given by
states. The network state in the slot is given by 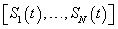 where
where 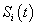 is a set of
is a set of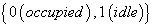 . Assuming that the spectrum usage statistics of the PUs’ network remain unchanged during T slots. In fact, this spectrum is licensed to a primary network, whose users are operated in a synchronous time-slotted fashion. Since the primary network does not use the whole spectrum all the time, it is assumed that the probability of channel being occupied by the primary network in one time slot is
. Assuming that the spectrum usage statistics of the PUs’ network remain unchanged during T slots. In fact, this spectrum is licensed to a primary network, whose users are operated in a synchronous time-slotted fashion. Since the primary network does not use the whole spectrum all the time, it is assumed that the probability of channel being occupied by the primary network in one time slot is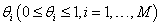 . These values are affected by the channel allocation schemes and traffic statistics of the primary network. Besides, our duties focus on maximizing SU’s total channel utilization while limiting its interference to the PUs. We also model the interference between PU and SU via the average temporal overlap. The formulation describes the interference
. These values are affected by the channel allocation schemes and traffic statistics of the primary network. Besides, our duties focus on maximizing SU’s total channel utilization while limiting its interference to the PUs. We also model the interference between PU and SU via the average temporal overlap. The formulation describes the interference 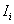 between SU and PUi is
between SU and PUi is 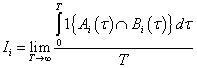 | (1) |
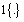 is the indicator function of the event enclosed in the brackets;
is the indicator function of the event enclosed in the brackets; 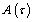 and
and 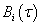 denote the event that PUi and SU access channel
denote the event that PUi and SU access channel 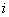 at time
at time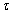 , respectively.The channel utilization is defined as the SU’s temporal utilization ratio (i.e., the transmission time divided by the total time). These SU’s channel utilization
, respectively.The channel utilization is defined as the SU’s temporal utilization ratio (i.e., the transmission time divided by the total time). These SU’s channel utilization 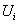 on channel
on channel 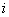 is
is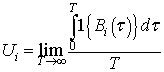 | (2) |
3. The Suboptimal Strategy for Spectrum Sensing
- Spectrum sensing is the functionality enabling cognitive radios to be aware of spectrum usage and to detect spectrum opportunities. When two nodes want to communicate, source and destination are responsible for performing sensing; they select a set of channels to sense, they estimate channel availability, then channel filtering is performed, and a communication link is set up. Both reactive (on-demand) and proactive sensing may be exploited in a cognitive network. During data transmission, periodic in-band sensing is performed to detect incumbent PUs and avoid harmful collisions, while the sensing process dealing with the search of new opportunistic resources is referred to as out-of-band sensing. In this framework, we do not concern about techniques processing observations and detect PUs. There are two kind of the sensing outcome processing and available channel estimation, namely a distributed and centralized fashion. In the centralized approach, a leader fuses all sensing information according to a certain rule (for example, AND, OR, or M-out-of-N rules) and it evaluates spectrum opportunities. In the distributed solution, secondary nodes share observation data and independently take decisions regarding resource availability[4-12].In the cognitive radio technology, the optimal spectrum sensing policy can be computationally prohibilitive. The reason here is that the dimension of the sufficient statistic grows exponentially with the number of channel N. In fact, the optimal algorithm can be computed offline and process prior to the SU want to access the required spectrum. This approach makes it difficult to adapt to changes in the spectrum occupancy statistics. This is motivation for develop suboptimal spectrum sensing schemes. Let
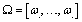 where
where 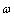 is the probability that channel
is the probability that channel 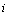 is available at the beginning of a slot. As a result, the dimension of the sufficient statistic reduces from
is available at the beginning of a slot. As a result, the dimension of the sufficient statistic reduces from 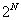 to N. This result points to the possibility of significantly reducing the computational complexity of the optimal Opportunistic Spectrum Access issues. Through the sufficient statistic, we apply the suboptimal scheme based on a greedy approach that maximizes per slot throughput. The analyzed systems have independently channels.
to N. This result points to the possibility of significantly reducing the computational complexity of the optimal Opportunistic Spectrum Access issues. Through the sufficient statistic, we apply the suboptimal scheme based on a greedy approach that maximizes per slot throughput. The analyzed systems have independently channels. 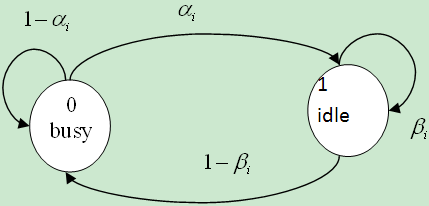 | Figure 1. The Markov chain diagram |
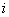 transits from the state 0 to state 1 with the probability
transits from the state 0 to state 1 with the probability 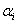 and stays in the state 1 with the probability of
and stays in the state 1 with the probability of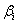 . We gain the expected reward in the slot
. We gain the expected reward in the slot 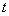 if channel c is selected as follow
if channel c is selected as follow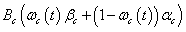 | (3) |
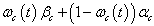 is the probability that channel
is the probability that channel  will be available in the slot
will be available in the slot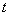 . Applying the greedy approach, the action in slot
. Applying the greedy approach, the action in slot 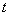 is chosen aiming to maximize the immediate reward below
is chosen aiming to maximize the immediate reward below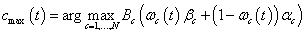 | (4) |
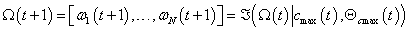 | (5) |
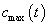 and the observation at the end of the slot
and the observation at the end of the slot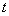 ;
; 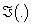 function represents the updated knowledge of the network state after incorporating the action and observation obtained in selected slot[13-18].Note that when the channel is not sensed, the probability of its availability is updated according to the Markov chain. But channel is sensed will be lead to the belief vector records the channel state prior to the state transition at the beginning of each slot.
function represents the updated knowledge of the network state after incorporating the action and observation obtained in selected slot[13-18].Note that when the channel is not sensed, the probability of its availability is updated according to the Markov chain. But channel is sensed will be lead to the belief vector records the channel state prior to the state transition at the beginning of each slot.4. Simulation Results
- In simulations, we present numerical results to evaluate the performance of the suboptimal cognitive MAC schemes. We consider some independent channels with the same bandwidth
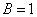 and transition probabilities
and transition probabilities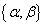 .In the first experiment, we set up 4 independent channel for determining the throughput. If we increase the alpha probability parameter then its throughput degraded seriously.Next, we present the different number of the sensed channels in Figure 3. We can see the more channel based spectrum sensing method has better performance compared to another. Consequently, through this illustration we gain optimal performance together with design of the communication links between the source nodes and destination nodes properly. This result confirms the chosen suboptimal spectrum sensing methodology will be reduced the complexity in computational functions.
.In the first experiment, we set up 4 independent channel for determining the throughput. If we increase the alpha probability parameter then its throughput degraded seriously.Next, we present the different number of the sensed channels in Figure 3. We can see the more channel based spectrum sensing method has better performance compared to another. Consequently, through this illustration we gain optimal performance together with design of the communication links between the source nodes and destination nodes properly. This result confirms the chosen suboptimal spectrum sensing methodology will be reduced the complexity in computational functions.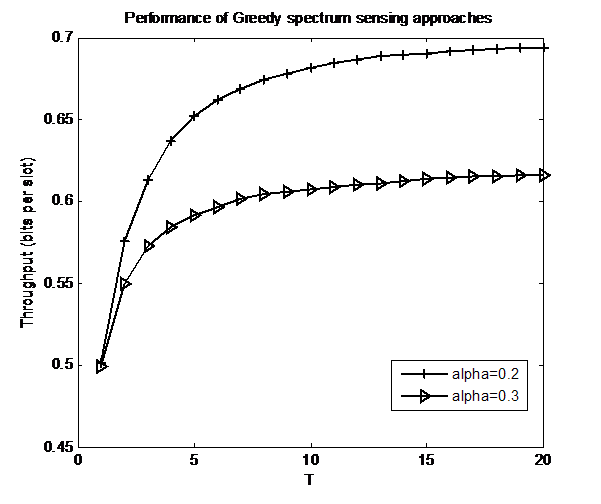 | Figure 2. Throughput analysis of the Greedy approach |
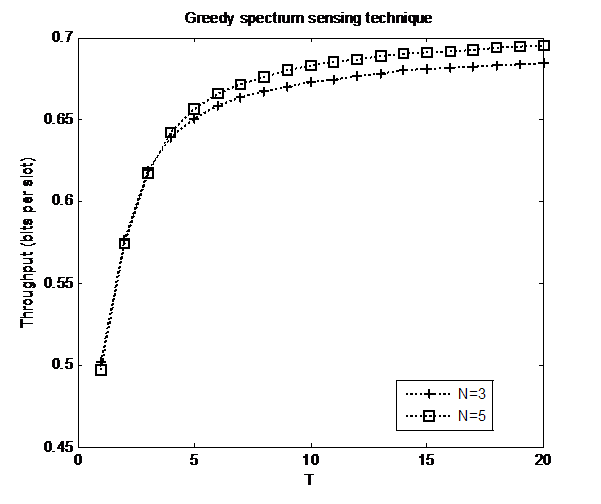 | Figure 3. The performance comparison with different schemes |
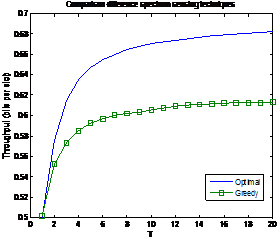 | Figure 4. The optimal and Greedy schemes |
5. Conclusions
- We have presented the performance of throughput of the suboptimal spectrum sensing technique and optimal one as well. Throughout the paper, it can be seen that the selection of alpha parameter of the probability in the selected node at value of 0.2 bring the good performance for cognitive radio. We try to change some determined parameters aiming to prove that the cognitive radio can implementation in reality with proper number of independent channel and the state transition probability. The throughput analyses in the simulations are clear demonstrations providing the improvement work for cognitive networks, especially in opportunistic spectrum access schemes.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML