-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Intelligent Systems
p-ISSN: 2165-8978 e-ISSN: 2165-8994
2015; 5(2): 73-80
doi:10.5923/j.ajis.20150502.04
Data Transmission Using Multi-Factor Authentication over Wireless Communication Channel
Zachaeus K. Adeyemo, Temitope A. Lasisi, Isaac A. Akanbi, Amole A. Olatide
Electronic and Electrical Engineering Department, Ladoke Akintola University of Technology, Ogbomoso, Nigeria
Correspondence to: Zachaeus K. Adeyemo, Electronic and Electrical Engineering Department, Ladoke Akintola University of Technology, Ogbomoso, Nigeria.
| Email: |  |
Copyright © 2015 Scientific & Academic Publishing. All Rights Reserved.
Data transmission through the internet over the worst channel is increasing everyday due to its convenience. However, hackers interrupt the integrity and availability of the data being transmitted. Conventional method used to combat these challenges such as one-factor authentication is prone to hacking because of its weakest in validating the identity of a person. Therefore, this paper investigates the security of the data being transmitted over the wireless communication channel using two-factor authentication. The transmitted data is first encrypted using Advanced Encryption Standard (AES) after which the finger veins of 123 volunteers consisting of 83 males and 40 females are integrated into the encrypted data. This is transmitted using a secret key and finger vein enrollment. The data is then filtered, modulated and transmitted through the wireless channel. The received data is demodulated, decrypted using the same key after the finger vein authentication. The performance of the technique is evaluated using Response Time, False Acceptance Rate (FAR) and False Rejection Rate (FRR). The results show that high level of accuracy and small response time are obtained. The significance of this work is seen in criminal identification, autonomous vending, institutions of learning, hospitals and automated banking.
Keywords: Two-Factor Authentication, Symmetric Cryptography, Finger Vein, Database, Encryption
Cite this paper: Zachaeus K. Adeyemo, Temitope A. Lasisi, Isaac A. Akanbi, Amole A. Olatide, Data Transmission Using Multi-Factor Authentication over Wireless Communication Channel, American Journal of Intelligent Systems, Vol. 5 No. 2, 2015, pp. 73-80. doi: 10.5923/j.ajis.20150502.04.
Article Outline
1. Introduction
- Wireless system is prone to transmission problem and hacking. Many of the unauthorized accesses in wireless transmission are due to low level of security of the network. The level of security in organizations and establishments such as universities, industries which depend on internet should be very high to preserve the data from hacking. This process of using security code, key or password is known as one-factor authentication and is vulnerable to hacking because it is a default one-factor authentication. Authentication is the process of identifying a person who has been registered or enrolled as a true user. Two-factor authentication is a combination of two features of authentication which may be password and biometric technologies such as retina, finger prints, face and palm vein recognitions. The two features of authentication can be encryption and any of biometric features. Encryption is the process of encoding the data in such a way that unauthorized person will not be able to read it, that is, no one will not be able to understand the coded signal being transmitted. The data is decrypted to restore the data. Encryption of data is being analyzed by cryptographic algorithms where there is a known key by the authorized user to decrypt the data. Cryptography is the science of using mathematics to encrypt and decrypt data. It enables storage of sensitive data to be preserved for intended recipient [1-6]. In other word, cryptography is associated with scrambling of plaintext either ordinary text or clear text into ciphertext (encryption) and then back again (decryption). There are two types of cryptographic algorithms namely: secret key cryptography known as symmetric key cryptography where the same key is used for both encryption and decryption and secondly, public key cryptography which is also known as asymmetric cryptography where two different keys are used with one for encryption and the other one for decryption [7].Biometrics is a technology of measuring and statistically analyzing biological or physiological traits. More generally, a biometric is a feature measured from a human that can be used for recognition, user authentication and verification purposes. This is based on the privilege of having features that are unique and exclusive to individual by the human body. Most popular biometric includes fingerprints, iris, retina, face, hand, voice and signature. Biometric techniques for personal identification have been attracting attention because one factor authentication such as keys, passwords, and PIN numbers have problems in terms of theft, loss and on the user’s memory [8-10].Some of the conventional biometric techniques such as the ear, iris, retina and fingerprint recognitions have associated problem like deterioration of the epidermis of the fingers, finger surface particles, human body and surgical operation effects which reduce the recognition accuracy. The finger vein which is the second layer of authentication is considered with cryptography in this paper because of its universality, uniqueness, and no adverse effects on human body.In this paper, two-factor authentication which consists of Advanced Encryption Standard under symmetric cryptography and finger vein is considered to improve the level of security over any one-factor authentication. The investigation is carried out over wireless communication channel. The system model developed consists of a transmitter, wireless channel and the receiver. The transmitter consists of the data to be transmitted, encrypted using symmetric cryptography, after which the finger vein data is binarised, embedded, modulated and properly filtered before sending over the wireless channel to the receiver which also consists of other signal processing techniques for demodulation, filtration, authentication and decryption using the secret key to obtain the original data. The system model is evaluated using False Acceptance Rate (FAR) and False Rejection Rate (FRR) which are functions of match ratio and response time. The system has high level of security due to its high accuracy and small response time.
2. System Model
- The system model consists of a transmitter with many signal processing techniques such as encryptor, finger vein database, Recognition algorithm, modulator and filter, then the wireless channel, and the receiver which has demodulator, filter, finger vein authentication and decryptor to retrieve the original transmitted data. The transmitted data is first encrypted using Advanced Encryption Standard (AES) algorithm. After which the finger veins of 123 volunteers consisting of 83males and 40 females are embedded into the encrypted data. This forms the secured data to be transmitted over wireless channel using a secret key and finger vein enrolment. The secured data is filtered, modulated and transmitted. The received data is demodulated, decrypted with the same key after the finger vein authentication is applied to receive the original transmitted data. Figure 1 shows the system model developed for the investigation. The performance of the system is evaluated using FAR and FRR which are functions of match ratio and response time. Figure 2 depicts the flowchart of the technique used for the process.
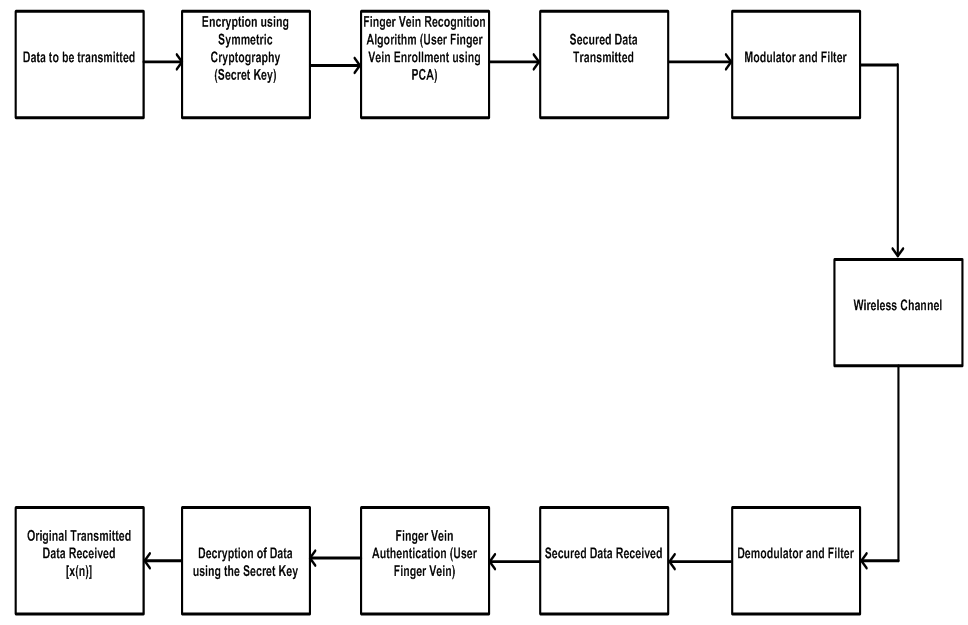 | Figure 1. System Model |
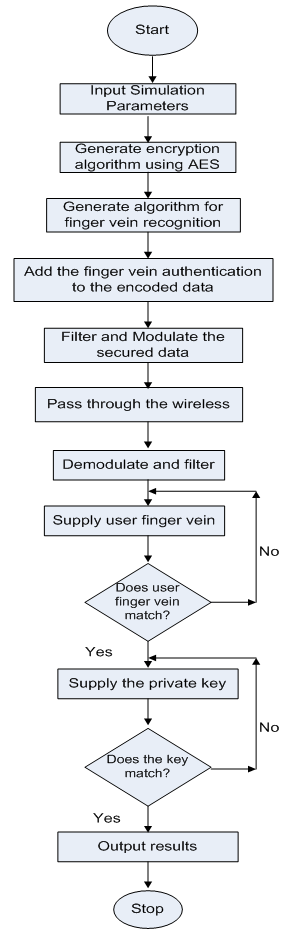 | Figure 2. Flow Chart of the technique |
2.1. Method of Simulation
- The cryptography scheme that is used for the first layer authentication is the Advanced Encryption Standard (AES) while the finger vein recognition is used as the second layer authentication. The two layer authentications are integrated and simulated using MATLAB communication and signal processing toolboxes. The system used for the analysis has 4GB RAM, Windows 8, Core i3 @ 2.4 GHz with MATLAB version of 8.1.0.604 (R2013a).
2.1.1. Advanced Encryption Standard
- In Advanced Encryption Standard (AES), the input consists of 128 bits block for both decryption and encryption to form a matrix. For encryption algorithm, the block is copied into a state array which is modified at each stage of the algorithm and then copied to an output square matrix. The plain text and the key are depicted as 128 bits square metric. This key is then expanded into an array of key scheduled word. The algorithm begins with an ‘add round key stage’ followed by nine rounds of four stages and the tenth round consists of three stages. These four stages are: substitute bytes, shift rows, mix columns and add round key. The decryption algorithm is the inverse of the encryption algorithm. The tenth round simply leaves the mix columns stage. The first nine rounds of the decryption algorithm consist of Inverse Shift rows, Inverse Substitute bytes, Inverse Add Round Key and Inverse Mix Columns. The AES algorithm requires 16 bytes key to serve as the password and expand before using in the encryption and decryption processes [5] [11].
2.1.2. Finger Vein Recognition
- The finger vein recognition is used as the second layer authentication because of its advantages when compared with other biometric technologies due to its universality and uniqueness. Hand and finger vein detection methods do not have any negative effects on human body; the condition of the epidermis has no effect on the vein features detection.
2.1.3. Finger Vein Database Description
- The images in the database are collected from 123 volunteers comprising 83 males and 40 females, who are staff and students of Universiti Sains Malaysia [11]. The age of the subject ranges from 20 to 52 years old. Every subject provides four fingers: left index, left middle, right index and right middle fingers resulting in a total of 492 finger classes. The captured finger images provide two important features: the geometry and the vein pattern. Each finger is captured six times in one session and each individual participated in two sessions, separated by more than two weeks’. In the first session, a total of 2952 (123 x 4 x 6) images are collected. A total of 5904 images from 492 finger classes are obtained from the two sessions. The spatial and depth resolution of the captured finger images are 640 x 480 and 256 grey levels, respectively.
2.2. Integration Mechanism
- The finger vein authentication layer is integrated into the system by following a simple rule of transmitting the finger vein template with the last 94 bytes of the data to be communicated. This is possible because the finger vein feature extraction algorithm extracts 94 bytes of data from the original finger vein image. At the receiver, the last 94 bytes are decrypted first and matched before decrypting the rest of the data.
3. Performance Metrics
- The metrics used to evaluate this technique are false acceptance rate (FAR) and false rejection rate (FRR) which are defined as in (1) and (2):
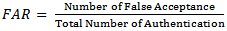 | (1) |
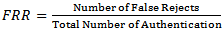 | (2) |
4. Results and Discussion
- The results are obtained by observing the performance of finger vein recognition at the receiving end when matched with the finger vein images in the database. The technique is simulated using MATLAB Version: 8.1.0.604 (R2013a) application package. The output of the encryption sequence is presented as follows:
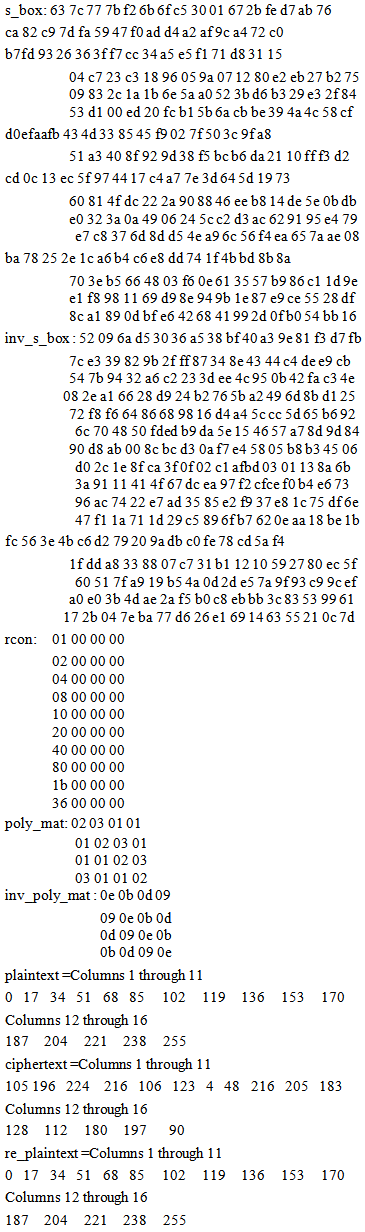 Figure 3 shows the False Acceptance Rate graph. This is the graph of frequency against the match ratio. It is measured by computing the match ratio for different fingers. It verifies how the finger vein recognition algorithm is evaluated with different fingers. Since the database used consists of 123 fingers, thus making the size to be 15006 (123 x 122). The distribution of the match ratio ranges from 0 to 0.25 with the highest frequency at the match ratio of 0.18.
Figure 3 shows the False Acceptance Rate graph. This is the graph of frequency against the match ratio. It is measured by computing the match ratio for different fingers. It verifies how the finger vein recognition algorithm is evaluated with different fingers. Since the database used consists of 123 fingers, thus making the size to be 15006 (123 x 122). The distribution of the match ratio ranges from 0 to 0.25 with the highest frequency at the match ratio of 0.18.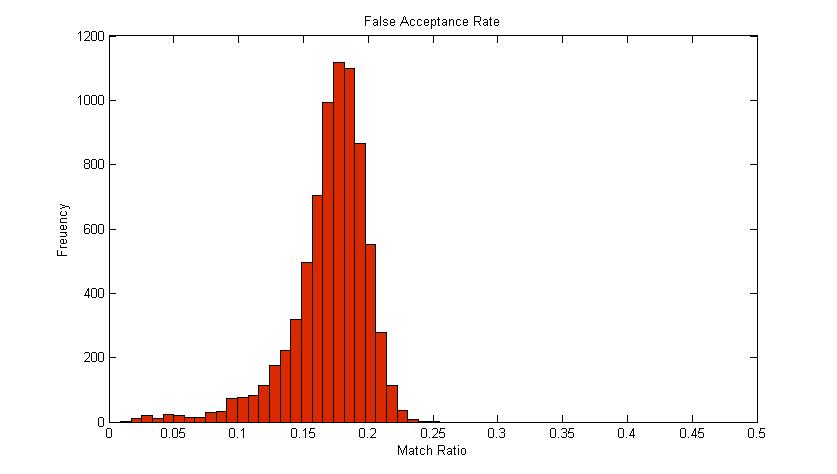 | Figure 3. False Acceptance Rate Graph |
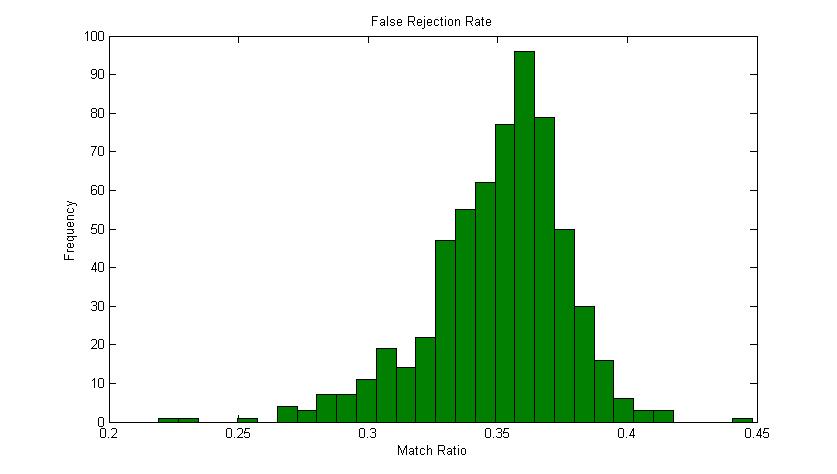 | Figure 4. False Rejection Rate Graph |
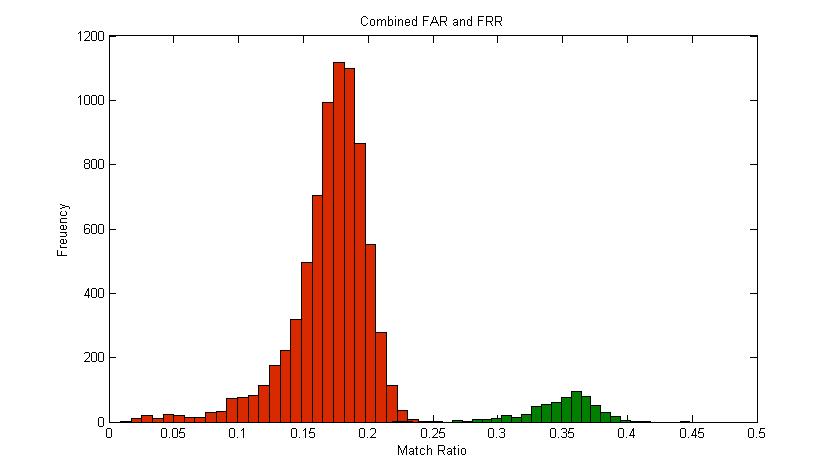 | Figure 5. Combined FAR and FRR Graph |
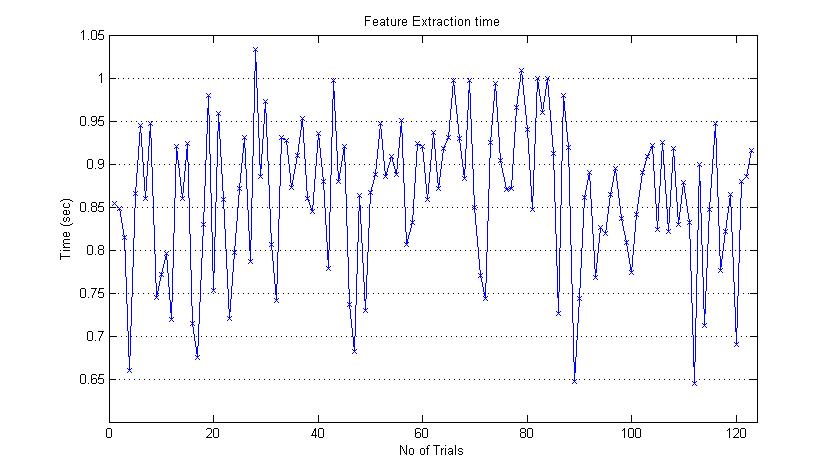 | Figure 6. Feature Extraction Time Graph |
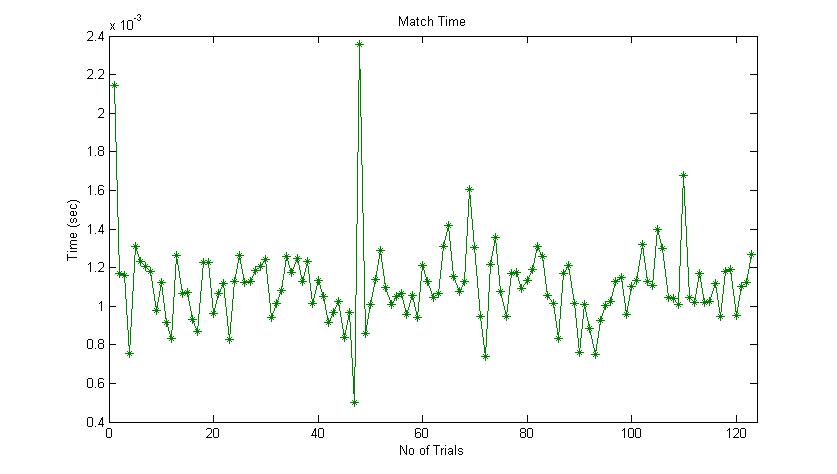 | Figure 7. Match Time Graph |
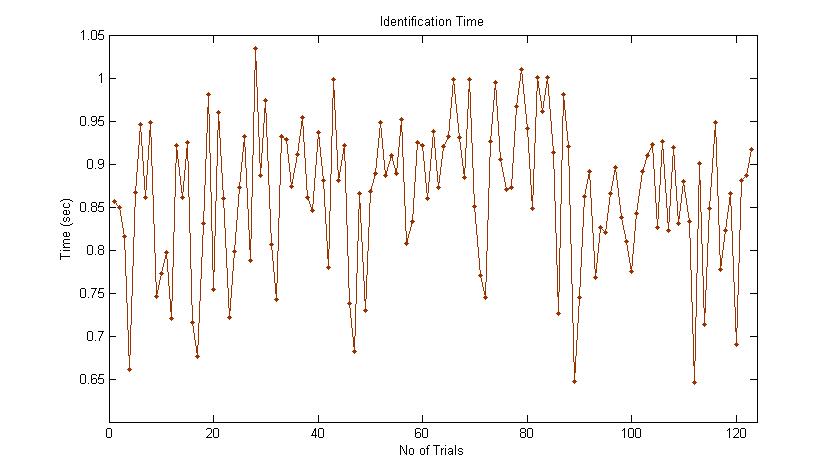 | Figure 8. Identification Time Graph |
5. Conclusions
- In conclusion, a system of two-factor authentication using symmetrically encrypted data and finger vein recognition has been developed over a wireless channel to secure transmission of data. The model is developed around many signal processing techniques at the transmitter to have the secured data that has been transmitted over the wireless channel. The other signal processing techniques at the receiver are developed to retrieve the original data. The performance is evaluated in terms of false acceptance rate, false rejection rate, feature extraction time, match time and identification time. From the results obtained, it can be deduced that this system of two-factor authentication method adopted has been able to show that it is convenient for the user to almost eradicate the various security challenges such as man-in-the-middle forgery thus protecting the confidentiality, integrity and availability of data. Also, this system of 2-factor authentication has proven to be time efficient in terms of authentication.
ACKNOWLEDGEMENTS
- We wish to acknowledge Mohd Shahrimie. Mohd Asaari, Shahrel A. Suandi, Bakhtiar Affendi for making finger vein data base available to us.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML