-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Intelligent Systems
p-ISSN: 2165-8978 e-ISSN: 2165-8994
2015; 5(1): 27-33
doi:10.5923/j.ajis.20150501.03
An Antifraud System for Tourism SMEs in the Context of Electronic Operations with Credit Cards
Fidel Rebón, Iñigo Castander, Jon Argandoña, Jon Kepa Gerrikagoitia, Aurkene Alzua-Sorzabal
CI Ctour GUNE, Donostiako Parke Teknologikoa, Mikeletegi Pasealekua, Donostia, Spain
Correspondence to: Fidel Rebón, CI Ctour GUNE, Donostiako Parke Teknologikoa, Mikeletegi Pasealekua, Donostia, Spain.
| Email: |  |
Copyright © 2015 Scientific & Academic Publishing. All Rights Reserved.
The new paradigm of marketing and communication, in which the “tourism marketer” conducts its strategies by adapting services to the tourists’ interests has enabled an increase in the number of transactions made by tourists, before, during and after the trip. This act, in which both parties, buyer and seller, annul their differences are generally carried out on the internet by means of credit cards. Knowledge Discovery in Databases techniques bring up an optimal solution for discovering fraud conducted in internet transactions before it is executed. This study proposes a novel system of antifraud model in order to improve the analyzed techniques and help in the decision-making process of fraud with credit cards in electronic transactions for the tourism SMEs.
Keywords: Credit Fraud, Credit Fraud Model Process, Knowledge Discovery in Databases
Cite this paper: Fidel Rebón, Iñigo Castander, Jon Argandoña, Jon Kepa Gerrikagoitia, Aurkene Alzua-Sorzabal, An Antifraud System for Tourism SMEs in the Context of Electronic Operations with Credit Cards, American Journal of Intelligent Systems, Vol. 5 No. 1, 2015, pp. 27-33. doi: 10.5923/j.ajis.20150501.03.
Article Outline
1. Introduction
- Traditionally, sociocultural elements of the environment have been embraced by human beings and incorporated into their personality in order to adapt to society’s needs. However, the real world is leading to an attractive digital and virtual realm that, in contrast, is able to rapidly adapt to these requirements. Society has started to respond to the globalization and digitalization phenomena, where Information and Communication Technologies (ICTs) represent one of the pillars in the new knowledge economy [1].In the context of tourism, the new paradigm of marketing and communication, in which the “tourism marketer” conducts its strategies by adapting services to the tourists’ interests [2], has enabled an increase in the number of transactions made by tourists before, during and after the trip [3], [4]. This act, in which both of the parties, buyer and seller annul their differences, is generally carried out through credit cards based on the Internet.The statistics on electronic Commerce (e-commerce) state that between the years 2009 to 2012 the volume of online buyers in the United States has experienced a growth of over 22 million. Forecasts estimate that by 2015 these numbers will be up to around 38 million [5]. Not only the number of users will rise rapidly, but also the business volume will increase. For example, in the first quarter of 2013, the 25 million transactions originated in Spain and directed out of its borders represented an amount of 1.2 billion euros. The largest part of the purchases was directed towards the European Union, adding up to 89% of the total. The transactions directed to the United States stand for a 5%. The value of the foreign transaction directed to Spanish websites reached 463 million euros. The biggest share of the transactions had its origin in the European Union, counting for a total volume of business of around 72% [6].The data provided shows an upward tendency in the number of daily trade transactions that will take place in the market. This fact inevitably leads to the increase of fraud in credit cards operations. This type of fraud has an estimated waste cost of billions of dollars for both consumers and the financial industry [7].These financial and industrial entities are the ones that have put more means for preventing this type of fraud. Nevertheless, small and medium size enterprises (SMEs) have little access to resources, capital and knowledge needed to fight against fraud. Furthermore, a large share of enterprises in the tourism sector pertains to this structural segment [8]. Besides this, the incorporation of ICTs to the cooperative network culture is barely developed, despite it could positively influence in its level of competitiveness [9].Actually, information technology and Business Intelligence provide a novel direction to support enterprise business in the new age [10]. At this moment a confluence of practices is taking place and technologies are leading into smarter computing capacities. This paradigm shift will enable organizations to overtake intelligent actions to address time-sensitive business processes and benefit from analysis [11]. This analysis is developed by applying Knowledge Discovery in Databases (KDD). These techniques bring up an optimal solution for discovering fraud before it is executed in transactions conducted by means of the credit cards. This is a non-trivial process as discovering knowledge and useful information within the data contained in a repository of information is a tedious task [12]. There is a high natural imbalance within the data when significant and critical characteristics regarding fraudulent cases from the non-fraudulent are extracted.In order to make the fraud detection in commercial transactions carried out with credit cards easier and also to be able to detect them before they are executed, the authors of this study will analyze the different existing techniques. After that, an improved solution to help in the detection of fraud with credit cards in electronic transactions for tourism SMEs is presented.
2. Related Work
- A broad variety of fraud forms have been gathered in a taxonomy [13] (See Figure 1).
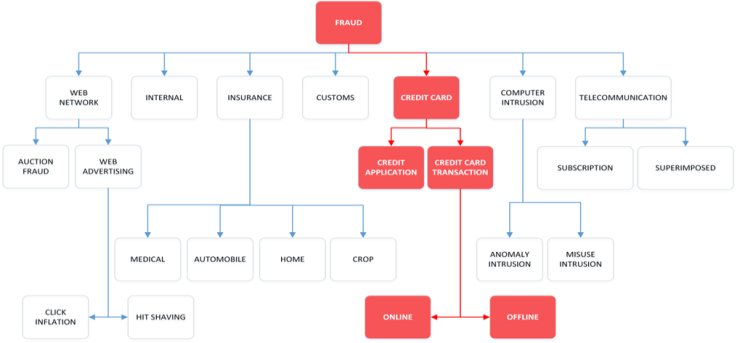 | Figure 1. Taxonomy of fraud types [Laleh & Azgomi, 2009] |
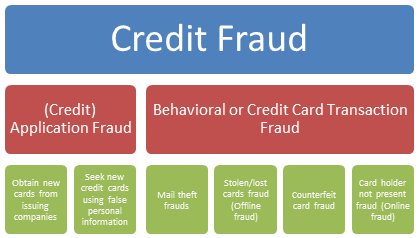 | Figure 2. Credit fraud types |
3. Results and Methodology
- The study has firstly performed an extensive review of the state of the art. Once the current capabilities and deficiencies have been identified, the authors propose a novel system which facilitates an early detection of fraudulent transactions.A comparison among the methods described in the previous section is performed first. It should note that this comparison is extracted by means of the conclusions based on related work. With this aim, a value between zero and one is assigned to each cell. There are two cases in which the value will be zero: a) the comparison is performed on the technique itself; b) the proposed technique on the row has not a behavior as good as the technique offered in the column. Otherwise, the assigned value will be one (See Table 1).
|
3.1. Credit Fraud Model Process
- CFMP is an intelligent and expert system, capable of validating payment operations through a digital media before they have happen.It is considered an intelligent and expert system because it initially learns from an expert and it continues improving through experience as it grows. All the decisions are stored and are re-evaluated in order to anticipate to the new fraud behaviors.In order to be able to discard an operation, CFMP applies KDD techniques. These techniques look for valid, novel and potentially useful and comprehensible patterns through transaction history.
3.1.1. Internal Operation
- The process is modelled in the system by a series of operations made on the initial commercial operation data (See Figure 3 and Figure 4).
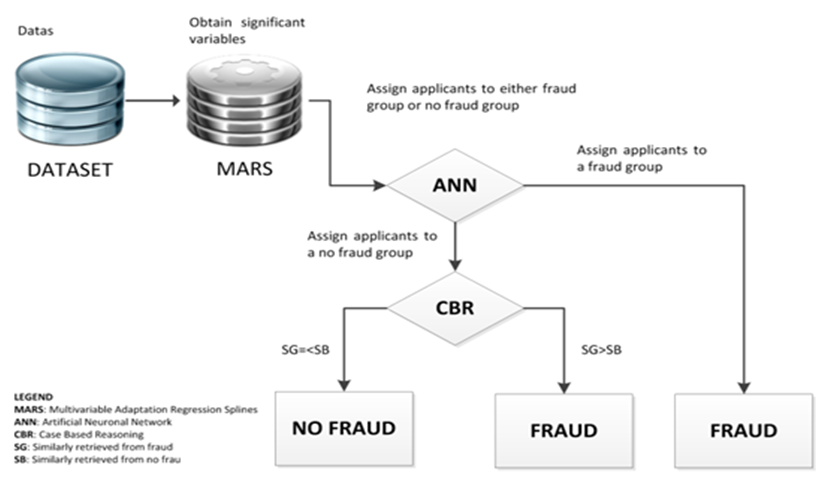 | Figure 3. Internal Operation of CFMP (1/2) |
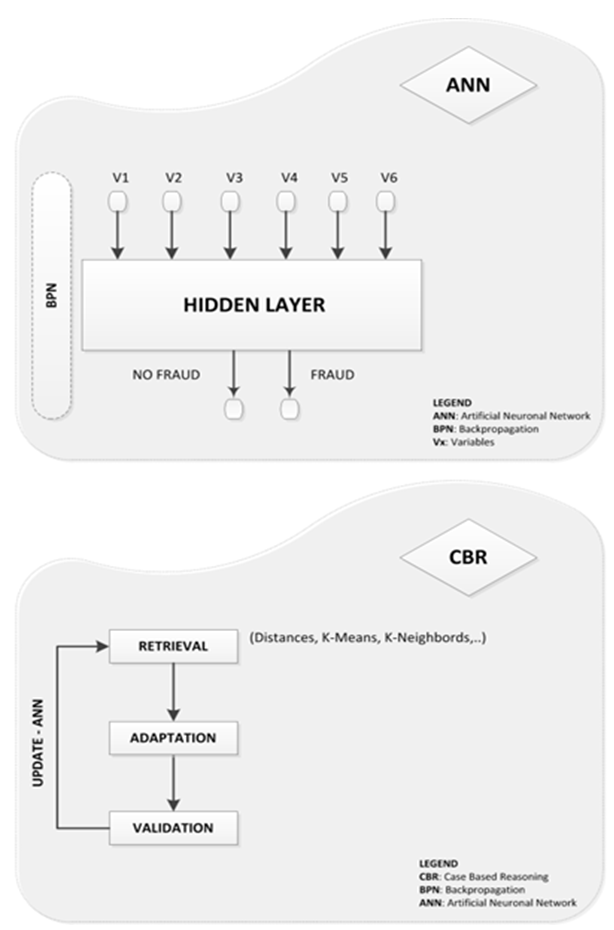 | Figure 4. Internal Operation of CFMP (2/2) |
- The initial data are received by a Multivariable Adaptation Regression Splines (MARS) task; which will reduce the input variables to the most significant. This will facilitate working in a more efficient fashion. After this, the variables are converted in an intake and they are checked by an ANN. These inputs are credit cards’ data and/or the information about the cards’ owner that the MARS consider more significant. The evaluation will indicate if the operation is “fraudulent” or “not fraudulent”. In case of a “not fraudulent” result the input will pass to a Case Based Reasoning (CBR). The CBR has the aim of filtering incorrectly detected fraud cases. The mechanism of the CBR is simple; it looks up the number of previous inputs in the database that are close to the input and show a “fraudulent” result (SG) in front of the previous inputs that are close to the input and hold a “not fraudulent” result (SB). If SG is less or equal to the SB, the CBR will indicate that the operation as “not fraudulent”, however, if the SG is greater than SB, the CBR will show it as “fraudulent”.Once the operation is discarded or accepted, the system will store the result with their respective inputs in order to be able to incorporate this new case to CBR.The system will also evaluate the raid of the new case inside the training data of ANN, seriously considering to add it if the case has been considered “fraudulent”.
3.1.2. Advantages of the CFMP over Other Tools
- When considering fraud detection tools, it is visible that CFMP and, in particular, the CBR component is better than GA and ANN if the features (skills, functional facilities,…) are taken into consideration. However, it is not the case when comparing LR and ANN [37]. This happens because ANN has a higher overall accuracy than LR but it has a lower one than the AR when working with datasets containing several years of data. It is also highlighted, that considering the same sample, AR achieves a better precision than LR. In addition, it should be noted that the system includes all MARS + ANN + CBR techniques and those have a more optimal ratio of accuracy, as a whole, than other techniques utilized in the current context of fraud credit: LDA, LR, CART Y ANNs [22]. Furthermore, the technical level of CBR entitles the usefulness of supplying a similar case based on prior knowledge. This allows reallocating a case that has already been classified. From a business perspective, the combination of the ANN + CBR provides a significant improvement to the decision makers [22].
4. Conclusions and Future Work
- This study has presented a new novel system to prevent fraud based on commercial transactions.CFMP is a system that can improve the current lack of preventive systems by means of KDD techniques.This proposal should be elevated to another testing data environment, where the system and the other techniques will confront again; although the advantages of the CFMP about these KDD methods are clearly demonstrated.In addition, this system must adapt to the users’ behavior changes especially in Internet related purchasing activities performed from mobile apps. Having in account that the mobile commerce revenue is expected to reach 31 billion U.S. dollars in 2016 it will be crucial in the future.
ACKNOWLEDGMENTS
- We would like to thank the participants and partners in European project: “e-COMMERCE Proficient Applications in Security and Sales for SMEs (SME E-COMPASS)”.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML