Irfan Syamsuddin
Department of Computer and Networking Engineering, State Polytechnic of Ujung Pandang, Makassar, 90245, Indonesia
Correspondence to: Irfan Syamsuddin , Department of Computer and Networking Engineering, State Polytechnic of Ujung Pandang, Makassar, 90245, Indonesia.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Abstract
Successful e-government adoption in society depends mostly on trust among citizens who use it. It is vital to ensuring security of e-government applications and infrastructures as a guarantee of security and privacy of stakeholders in storing, processing and exchanging information over the online systems offered by the government. As threats on e-government information security are dynamic and continue to grow, policy makers need to perform evaluation on existing information security strategy to establish a trusted e-government service. This paper intends to propose a new method that can guide decision makers in evaluating strategic government information security. The evaluation framework is based on new Fuzzy Analytic Hierarchy Process that combines tangible and intangible factors as well as has specific capabilites to be used in vague and fuzzy decision environment which is common in information security related issues.
Keywords:
Information Security, Evaluation, Fuzzy Set Theory, Analytic Hierarchy Process
Cite this paper:
Irfan Syamsuddin , "Evaluation of Strategic Information Security with Fuzzy AHP Method", American Journal of Intelligent Systems, Vol. 2 No. 1, 2012, pp. 9-13. doi: 10.5923/j.ajis.20120201.02.
1. Introduction
E-government is about bridging government and citizen communications in more efficient, transparent and reliable ways through effective use of information technology. The Internet has become the main media for e-government from delivering public information to electronic document and financial transactions although it is widely attributed to serious security weaknesses. As a result, security and privacy are the most crucial concerns of any e-government applications[1].Many attempts have been proposed to overcome the issue. Unfortunately, most of the previous solutions tend to focus on technical solutions in various forms details such as firewall, intrusion detection systems, web application security and penetration testing using proprietary or open source technologies. In fact, security is no longer solely a technical concern; it is now becoming complex issues[2, 3].Current evaluation frameworks commonly deals with specific area of concerns mostly related to technical aspects such as firewall security etc. Lack of adequate framework which combines broad perspectives of information security is considered as a gap in recent e-government literature[3, 4] in particular in the case of how to evaluate information security practices of e-government from strategic perspectives.Ensuring security of e-government applications andinfrastructures is crucial to maintain trust among stakeholders to store, process and exchange information over the e-government systems. Due to dynamic and continuous threats on e-government information security, policy makers need to perform regular evaluation on current information security practices and controls. Based on the facts, this paper attempts to propose a holistic approach from managerial decision making perspective by combining all related aspects of security to create a framework used to evaluate e-government security strategy.Since decision making mostly involve multi criteria and alternative to consider altogether, this framework implement multi criteria decision making (MCDM) approach to view e-government security strategy from managerial perspective. Fuzzy set theory is applied to complement the framework in order to capture fuzziness in the form of inconsistencies and vagueness coming from subjective judgments by decision makers.The rest of this paper is organized as follows. Section 2 presents literature review of e-government security. In section 3, basic concept of fuzzy set theory is described. Then, in section 4, the new fuzzy analytic hierarchy process as a decision making framework is clearly explained and justified. Finally, concluding remarks and future research directions are given in last section
2. E-Government Security
E-government is one of key indicator for nations development as formulated by United Nation Public Administration Networks (UNPAN)[6]. Proliferation of e-government strongly relies on trust among citizens to store, process and exchange information over the e-government systems. Trust is maintained through effective security controls to ensure no sensitive information goes to unauthorized person.In some studies[7, 8] security issues are found to affect public services management. Trust on e-government plays a significant role to improve efficiency and effectiveness on transparent information flow between governments business and citizens[9]. On the other hand, lack of security concerns are responsible for unsuccessful e-government initiatives in some developing countries[10].Therefore, security controls is one of key factors for achieving an advanced stage of e-government for national development.Whilst technical considerations have received major concern in improving security controls on e-government systems in the past[11], non-technical issues such management, economic and cultural issues have emerged since the impact of cyber crimes has also become widely affecting many government and business organizations[2,12,13]. Complying with international standards, strong management commitment and regular review of security controls for security updates are examples of management aspects of information security that has received increasing concerns in recent years[13]. E-government security might also be viewed from economic perspectives. Security related spending with adequate investment analysis is believed to bring more success in handling security threats[12] which critically measure risks associated with impacts of security threats on e-government sensitive information.Van Solms[13], on the other hand, argues that success in maintaining information security mainly depends on people. Security awareness as a means of human security can be improved through comprehensive education and implementing reward punishment mechanisms[13]. This at the is supposed to create so called security culture. Gap of security between members and management of the organization about information security should be reduced otherwise it potentially become another source of threats in the future.Therefore in order for e-government to be implemented properly, security culture should be taken into top list of consideration.While the vital role of information security is significantly justified, only limited studies discuss specifically on how to evaluate and to make decisions regarding e-government security strategy.Although different organizations tend to define different security strategies, they generally agree upon the basic security strategy based on the CIA security triangle (confidentiality, integrity, and availability[14].Strategic decision lies on fundamental question of how to allocate security resources within the three security elements. One of a significant contribution to answer this question was proposed by Hwang and Syamsuddin[3] who propose an information security policy decision making based on Analytic Hierarchy Process. This work was expanded and applied to e-banking security to guide policy makers in performing evaluation of e-banking security in Indonesia[5]. However, this approach did not tolerate fuzziness such as inconsistency and vague decisions which commonly presented in many cases. For that reason, in the following sections, we describe how fuzzy set theory is adopted and combined with analytic hierarcy process to develop a new Fuzzy AHP method that able to tackle inconsistencies and vagueness that possible occur in evaluating strategic e-government information security.
3. Fuzzy Set Theory
The fuzzy set theory was introduced by Zadeh[15] to deal with fuzziness issues in many control systems applications. It was oriented to the rationality of uncertainty due to imprecision or vagueness. Its ability in representing vague data is considered as the major contribution of fuzzy set theory to science and technology. In the area of MCDM, fuzzy set theory has given a significant contribution by accepting uncertainty and inconsistent judgment as a nature of human decision making[16,18,19].In fuzzy set theory, triangular fuzzy numbers are represented with a triplet (L, M, U) for Lower, Medium and Upper numbers. Figure 3 shows the membership triangular fuzzy numbers.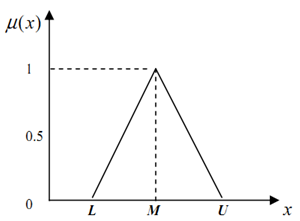 | Figure 1. Example of an image with acceptable resolution |
Let A be a triangular fuzzy number with a triplet (L, M, U). The membership value can be defined as followsVarious arithmetic calculations can be applied to these fuzzy membership values. However, there are few basic operations that widely used for triangular fuzzy numbers as explained below.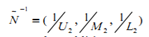 | (1) |
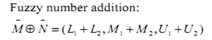 | (2) |
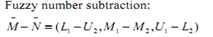 | (3) |
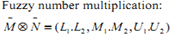 | (4) |
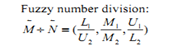 | (5) |
A major contribution of fuzzy set theory is its capability of representing vague data. The theory also allows mathematical operators and programming to apply to the fuzzy domain[15].In this section we introduce the proposed method as the main objective of this study. The new fuzzy multi criteria decision making framework for e-government security strategy is aimed at providing comprehensive decision making solution with ability to deal with inconsistent and vague judgments during decision making processes by the policy makers. Instead of using crisp numbers to represent preference used in classical Analytic Hierarchy Process[17], fuzzy numbers along with its linguistic variables are applied in this framework as shown in the following table.| Table 1. Fuzzy linguistics variables and their scales |
| | Linguistic Variable | Fuzzy Scale(l.m.u) | Reciprocal scale(l.m.u) | | Equally Important | (0.5,0.5,0.55) | (0.45, 0.5, 0.5) | | Slightly Important | (0.55, 0.6, 0.65) | (0.35, 0.4, 0.45) | | Important | (0.65, 0.7, 0.75) | (0.25, 0.3, 0.35) | | Very Important | (0.75, 0.8, 0.85) | (0.15, 0.2, 0.25) | | Absolutely Importanrt | (0.85, 0.9, 0.9) | (0.1, 0.1, 0.15) |
|
|
Comprehensive analysis of the framework is discussed in the following steps:
3.1. Construction of Evaluation Hierarchy
The proposed framework is basically adopted from our previous study[5] which applied the Analytic Hierarchy Process to form the evaluation hierarchy. As shown in figure 2 it consists of four levels, goal, criteria, sub criteria, and alternatives.At the top level, we define the goal as information security policy performance evaluation. Subsequently, four criteria are listed at the second level, namely Management (M), Technology (T), Economy (E) and Culture (C) as the criteria.At the third level, all criteria are divided into sub criteria as follows. Management consists of comply with standard (M1), regular review (M2), and commitment (M3). Technology consists of end point security (T1), network security (T2) and application security (T3). Economy consists of security investment (E1) and cost of attack (E2). Culture consists of reward & punishment (C1) and security education (C2).Finally, at the bottom level, we define three security objectives as the central concern in making any security decisions. They are confidentiality integrity and availability or commonly called CIA Security Triangle[3,5,14].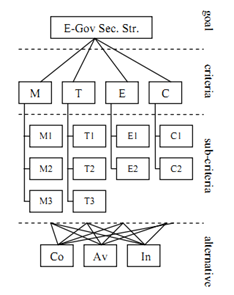 | Figure 2. Four layers of evaluation hierarchy |
3.2. Pairwise Comparison by Decision Makers
Based on the analytic hierarchy process structure[17], a set of questionnaire should be formed based on linguistic variables mentioned in table 1.The decision maker will be headed with a series of pairwise comparison questions in the the general form such as, ‘How important is criterion M to criterion E ?’. There are six possible answers provided in linguistic variables of Just Equal, Slightly Important, Important, Strongly Important, Very Strongly Important, and Absolutely Important (see table 1).Later, all answers are translated into its corresponding fuzzy scale as well the reciprocal numbers.
3.3. Aggregating Fuzzy Weights
In this framework we adopt fuzzy geometric mean method[16, 18] to deal with N numbers of decision makers since it has specific characteristic in shortening the gap effects of very high or low values, which significantly affect in reducing estimation bias.First, geometric mean for “upper” fuzzy numbers is calculated.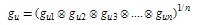 | (6) |
Then weight for upper fuzzy numbers derived from normalizing geometric mean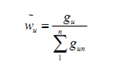 | (7) |
Finally, by using similar procedures we will also obtain weight for other fuzzy numbers for lower and medium.
3.4. Deriving Final Weight
In this step, final weight or often called overall weight is calculated. In this case, the calculation process is similar to technique used by classical AHP method[17]. To do so, all fuzzy numbers derived at each level are constructed in the form of matrix and then multiplying them to derive final weight. This step is conducted onto three fuzzy numbers (l,m,u).
3.5. Combining Group Decision Makers
In case more than one decision makers are involved, addition step is required to combine all decision makers results in the form of group decision making. 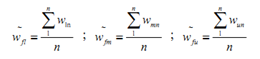 | (8) |
By using aritmethic mean, final results of N number decision makers can be obtained (see equation 8 above). Finally, we obtain three final weights above for lower, medium and upper fuzzy numbers. The three values are used to describe pessimistic, normal, and optimistic modes for further simulation purposes.In the proposed framework, the application of fuzzy set theory on AHP by Buckley[15] is modified and improved to meet the requirement for developing a new fuzzy MCDM framework to evaluate e-government security strategy.
4. Conclusions
This paper introduces a new fuzzy multi criteria decision making framework for e-government security strategy. Its main feature lies in its ability to capture vagueness and inconsistencies coming from subjective human judgments as decision makers. This feature overcomes weaknesses on previous approaches based on classical AHP.In details, comprehensive calculation procedures of the fuzzy AHP framework have been clearly explained and justified which can be implemented in real case. It starts from gathering decision makers’ judgments with fuzzy numbers and finally aggregates their fuzzy judgments into three modes of analysis, pessimistic, normal and optimistic. Furthermore, we plan to extend this study by applying it into empirical case study to assist policy makers in making appropriate decisions under fuzzy situation.
ACKNOWLEDGEMENTs
The author would like to acknowledge DIPA Politeknik Negeri Ujung Pandang for supporting this study.
References
| [1] | Jin-fu Wang, (2009) "E-government Security Management: Key Factors and Countermeasure," IAS, vol. 2, pp.483-486, 2009 Fifth International Conference on Information Assurance and Security |
| [2] | Filipek, R. (2007) “Information security becomes a business priority”, Internal Auditor, vol. 64, no.1, pp.18 |
| [3] | Hwang,J and Syamsuddin,I. (2009) "Information Security Policy Decision Making: An Analytic Hierarchy Process Approach," Proceeding of IEEE Third Asia International Conference on Modelling & Simulation, AMS 2009, pp.158-163 |
| [4] | Ku, C.Y. Chang, Y.W. and Yen, D.C. (2009) “National information security policy and its implementation: A case study in Taiwan”, Telecommunications Policy, vol. 33 , no. 7, pp. 371-384 |
| [5] | Syamsuddin,I and Hwang,J. (2009) "The Application of AHP Model to Guide Decision Makers: A Case Study of E-banking Security," Proceeding of IEEE Fourth International Conference on Computer Sciences and Convergence Information Technology ICCIT 2009, pp.1469-1473 |
| [6] | Hicks, R. (2010) OECD Plans Creation New E-government Indicators, FutureGov, available online athttp://www.futuregov.net/articles/2010/may/18/ / |
| [7] | Backhouse, J. and G. Dhillon (2001) "Current Directions in IS Security Research: Toward Socio OrganizationalPerspect-ives", Information Systems Journal, 11 (2), pp. 127-153 |
| [8] | Dhillon, G. and Torkzadeh, G. (2006) “Value Focused Assessment of Information System Security inOrganiz-ations”. Information Systems Journal. Vol 16. No 3 |
| [9] | Heeks, R (2006), Benchmarking e-Government:Improving the National and International Measurement, Evaluation and Comparison of e-Government, Published Research |
| [10] | Hwang,J and Syamsuddin,I (2008) “Failure of E-Government Implementation: A Case Study of South Sulawesi”, Proceeding of IEEE International Conference on Convergence and Hybrid Information Technology ICCIT2008, pp. 952-960 |
| [11] | Siponen, M.T and Kukkonen, H.O. (2007) “A review of information security issues and respective researchcontribu-tions”. DATA BASE 38(1): 60-80 |
| [12] | Anderson, R.. (2001) “Why Information Security is Hard : An Economic Perspective”, Proceedings of 17th Annual Computer Security Applications Conference, pp.10-14 |
| [13] | von Solms, B. (2001) “Information Security — AMultidimensional Discipline” Computers & Security, Vol. 20, Issue 6, 1, pp. 504-508 |
| [14] | Bishop, M (2004), Introduction to Computer Security, Addison-Wesley |
| [15] | Zadeh LA (1965) “Fuzzy sets”. Information and Control vol 8, pp. 338–53. |
| [16] | Buckley, (1985). “Fuzzy hierarchical analysis”. Fuzzy Sets and Systems. Vol. 17. pp. 233-247 |
| [17] | Saaty, T.L. (1990) The Analytic Hierarchy Process, RWS Publications, Pittsburgh, PA |
| [18] | Chiou H. Tzeng G. and Cheng D. (2005), “Evaluating sustainable fishing development strategies using fuzzy MCDM approach”. Omega, vol. 33, pp 223- 234 |

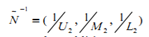
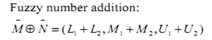
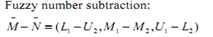
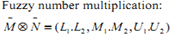
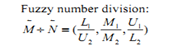

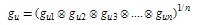
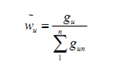
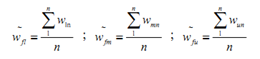
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-Text HTML
Full-Text HTML