-
Paper Information
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Computer Architecture
2023; 10(1): 9-14
doi:10.5923/j.ajca.20231001.02
Received: Apr. 15, 2023; Accepted: Apr. 25, 2023; Published: Apr. 27, 2023

Cybersecurity in the AI Era: Ensuring Your Data Stays Protected
Ashok Kumar Padmaraju
Sr Technical Manager in Leading BioPharma Industries, Raleigh, North Carolina, USA
Correspondence to: Ashok Kumar Padmaraju, Sr Technical Manager in Leading BioPharma Industries, Raleigh, North Carolina, USA.
| Email: |  |
Copyright © 2023 The Author(s). Published by Scientific & Academic Publishing.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Artificial Intelligence (AI) can revolutionize cybersecurity by improving threat detection, response time, and overall security posture. However, implementing AI for cybersecurity requires a comprehensive and iterative approach. It involves identifying use cases, gathering and preparing data, selecting and training AI models, implementing and integrating the models, monitoring and refining the system, evaluating and improving the solution's effectiveness, ensuring Explainability and transparency, and implementing governance frameworks. By following these steps, organizations can build a robust and proactive cybersecurity posture capable of detecting and responding to threats in real-time. This article explores AI's potential benefits and challenges in cybersecurity and provides a detailed outline of the steps in implementing AI for threat detection.
Keywords: Artificial Intelligence, Cybersecurity, Data Breach, Encryption, Machine Learning
Cite this paper: Ashok Kumar Padmaraju, Cybersecurity in the AI Era: Ensuring Your Data Stays Protected, American Journal of Computer Architecture, Vol. 10 No. 1, 2023, pp. 9-14. doi: 10.5923/j.ajca.20231001.02.
Article Outline
1. Introduction
- As technology grows and becomes more integrated into our daily lives, the threat of cyber-attacks and data breaches also increases. Using artificial intelligence (AI) in cybersecurity has become increasingly prevalent to combat these threats. This article explores the role of AI in cybersecurity and the various ways we can use it to safeguard sensitive data. It examines the benefits and challenges of using AI in cybersecurity, such as the potential for false positives or negatives and the need for continuous learning to keep up with evolving threats. The paper also discusses the importance of ethical considerations in using AI in cybersecurity and the need for transparency and accountability.Ultimately, the paper argues that AI can be valuable in ensuring data security in the digital age. Still, it must be used responsibly and in conjunction with human expertise. By leveraging AI and human intelligence, organizations can create a more robust and effective cybersecurity strategy to protect against the growing cyber-attack threat.
2. How Artificial Intelligence is Transforming Cybersecurity
- In today's world, the threat of cyber-attacks has become more severe than ever before, making cybersecurity an essential part of any organization's operations. The traditional methods of securing data are no longer sufficient as cybercriminals constantly evolve their tactics to exploit vulnerabilities in security systems. To combat this, organizations have started implementing Artificial Intelligence (AI) to enhance their cybersecurity. AI has proven to be a game-changer in cybersecurity. It can analyze vast amounts of data, detect patterns and anomalies, and make informed decisions without human intervention.Conventional security systems rely on rule-based systems that can only detect known threats. However, AI doesn’t limit by pre-determined rules and can learn from new data and detect unknown threats. This real-time analysis can provide security teams with actionable insights, allowing them to respond to threats quickly and efficiently. Another advantage of AI in cybersecurity is its ability to automate repetitive and time-consuming tasks. AI can handle routine security tasks such as monitoring and reporting, freeing up security teams to focus on more complex and strategic studies. This automation can significantly reduce the workload of security teams and improve the overall efficiency of cybersecurity operations.AI can also improve the accuracy of threat detection and response. Machine learning algorithms can learn from past incidents and use that knowledge to identify potential threats before they cause harm. This proactive approach to cybersecurity can significantly reduce the impact of a cyber-attack and minimize any damage caused. AI can also enhance vulnerability assessment and penetration testing. Traditional vulnerability assessment and penetration testing methods can be time-consuming and resource intensive. However, AI-powered vulnerability assessment tools can automatically scan an organization's network and identify vulnerabilities. Similarly, AI-powered penetration testing tools can simulate cyber-attacks on an organization's network to identify weaknesses in the security system. This approach is faster, more accurate, and more efficient than traditional methods.AI in cybersecurity is its ability to adapt to new threats continually. Cybersecurity threats constantly evolve, and AI can learn from new data and quickly adapt to new threats. This adaptive capability makes AI a powerful tool for combating cyber-attacks. It can evolve alongside the threat landscape and remain effective over time.
3. The Revolutionary Benefits of Using AI for Cybersecurity
- Artificial Intelligence (AI) has revolutionized cybersecurity, offering a range of advantages that traditional security systems cannot match. Here are some innovative ways that AI is enhancing cybersecurity:Advanced threat detection: AI-powered security systems can detect and respond to threats in real time. ML algorithms can scrutinize vast amounts of data and recognize patterns and irregularities that conventional security systems may overlook. This advanced threat detection capability can significantly reduce the time to identify and respond to cyber-attacks.Automation: AI can automate routine security tasks such as monitoring and reporting, freeing up security teams to focus on more complex and strategic studies. This automation can improve the overall efficiency of cybersecurity operations and reduce the workload of security teams.
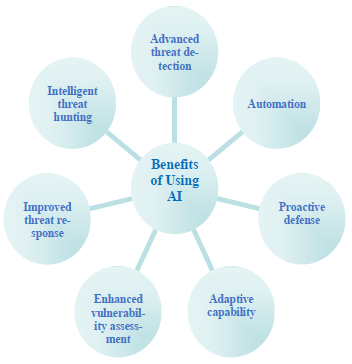 Proactive defense: AI can learn from past incidents and identify potential threats before they cause any harm. This proactive approach to cybersecurity can significantly reduce the impact of a cyber-attack and minimize any damage caused.Adaptive capability: AI can continually adapt to new threats and learn from new data, making it a powerful tool for combating cyber-attacks. This adaptive capability makes AI-powered security systems more effective over time.Enhanced vulnerability assessment: AI-powered vulnerability assessment tools can scan an organization's network and identify vulnerabilities automatically. This approach is faster, more accurate, and more efficient than traditional vulnerability assessment methods.Improved threat response: AI-powered security systems can respond to threats more accurately than traditional security systems. This improved threat response capability can significantly reduce the impact of a cyber-attack and minimize any damage caused.Intelligent threat hunting: AI can analyze vast amounts of data and identify threat indicators that may have gone unnoticed by traditional security systems. This intellectual threat-hunting capability can help security teams proactively identify and mitigate potential threats.
Proactive defense: AI can learn from past incidents and identify potential threats before they cause any harm. This proactive approach to cybersecurity can significantly reduce the impact of a cyber-attack and minimize any damage caused.Adaptive capability: AI can continually adapt to new threats and learn from new data, making it a powerful tool for combating cyber-attacks. This adaptive capability makes AI-powered security systems more effective over time.Enhanced vulnerability assessment: AI-powered vulnerability assessment tools can scan an organization's network and identify vulnerabilities automatically. This approach is faster, more accurate, and more efficient than traditional vulnerability assessment methods.Improved threat response: AI-powered security systems can respond to threats more accurately than traditional security systems. This improved threat response capability can significantly reduce the impact of a cyber-attack and minimize any damage caused.Intelligent threat hunting: AI can analyze vast amounts of data and identify threat indicators that may have gone unnoticed by traditional security systems. This intellectual threat-hunting capability can help security teams proactively identify and mitigate potential threats.4. Navigating the Risks of AI-Powered Cybersecurity Solutions
- While Artificial Intelligence (AI) offers many advantages in cybersecurity, a few potential disadvantages need to consider. Here are some innovative ways that AI could pose challenges for cybersecurity:Limited Understanding of Context: AI systems can only analyze and detect threats based on patterns and data sets that they have trained on. They may need to fully understand the security incident's context, which could lead to false positives or negatives.Complexity: AI-powered security systems often require specialized knowledge to configure and maintain. Organizations may need to invest significant resources in training staff or hiring experts to ensure the system does set correctly.Bias: AI systems are only as effective as the data quality they train on. If inherent biases influence that data, the performance and accuracy of the AI system may be compromised, leading to inaccurate or partial results. It can be particularly problematic in cybersecurity, where limited results could lead to overlooked threats or false positives.Vulnerability to Adversarial Attacks: AI systems can be vulnerable to attacks by hackers who seek to manipulate or deceive the system. Adversarial attacks can lead to false positives, false negatives, or other errors in the design, which could undermine its effectiveness.Lack of Transparency: AI systems can be difficult to understand or interpret, mainly using complex machine learning algorithms. This lack of transparency can make identifying and addressing any issues or errors challenging.Dependence on Data Quality: The effectiveness of AI-powered security systems depends heavily on the data quality used to train them. If the data is complete, accurate, and biased, it can lead to correct or ineffective results.
5. From Challenges to Opportunities: Innovative Uses of AI in Cybersecurity
- There are some potential disadvantages to using Artificial Intelligence (AI) in cybersecurity. However, there are also ways for AI does use to overcome these challenges. Here are some innovative ways that AI can help address the potential drawbacks of AI in cybersecurity:Improving Context Awareness: AI can improve context awareness in cybersecurity by analyzing a more comprehensive range of data sources and considering the broader context of security incidents. It can help reduce false positives and negatives and improve the accuracy and effectiveness of security systems.Enhancing Explainability: AI systems can be made more transparent and explainable by providing visualizations, explanations, or other tools that help users understand how the system works and why it makes specific recommendations. It can build trust in AI-powered security systems and enable users to better interpret and act on the results.Mitigating Bias: AI can minimize bias in cybersecurity by ensuring that the data used to train the system is diverse, representative, and free from discrimination. Additionally, AI monitors and detects bias in the design, allowing organizations to take corrective action when necessary.Defending Against Adversarial Attacks: AI can defend against adversarial attacks by detecting and responding to unusual or anomalous behavior. It can help identify and prevent attacks that manipulate or deceive AI-powered security systems.Ensuring Data Quality: AI can ensure data quality in cybersecurity by automatically identifying and correcting errors or inconsistencies in the data used to train the system. Additionally, AI can monitor the quality of data inputs in real-time, enabling organizations to identify and address any issues quickly.
6. Building a Strong and Proactive Cybersecurity Posture Using AI
- Implementing AI for cybersecurity involves several steps. Here is a detailed outline of these steps:Identify Use Cases: Identify the cybersecurity use cases that can benefit from AI-based solutions. It may involve reviewing incident reports, conducting vulnerability assessments, and analyzing threat intelligence feeds to identify areas where AI can help improve security.Gather and Prepare Data: Collect and prepare relevant data for AI analysis. It may include network traffic, system event logs, threat intelligence feeds, and other security-related data sources. The data does clean, structured, and normalized for analysis.
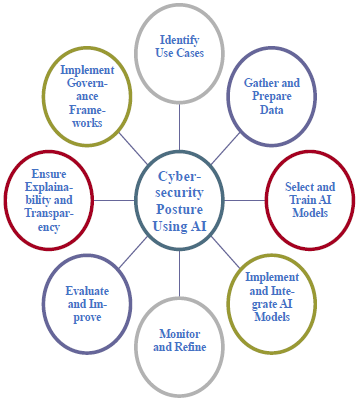 Select and Train AI Models: Choose the appropriate AI models for the specific cybersecurity use cases based on the available data and security needs. It may involve using supervised or unsupervised learning techniques to train the AI models on historical data. The models should be evaluated for accuracy and performance using appropriate metrics.Implement and Integrate AI Models: Deploy the AI models into the security infrastructure, integrating them with existing security tools and systems. It may involve customizing the models to fit the specific environment and adjusting parameters.Monitor and Refine: Continuously monitor the performance of the AI models and refine them over time as needed. It may involve adjusting parameters, retraining the models on new data, and updating them to address emerging threats.Evaluate and Improve: Regularly evaluate the effectiveness of the AI-powered security system and look for opportunities to improve it. It may involve conducting regular penetration testing, identifying gaps in coverage, and analyzing false positives and negatives to refine the models.Ensure Explainability and Transparency: AI models used in cybersecurity should be transparent and explainable. Understanding how the AI model arrived at a particular decision or recommendation is important. Organizations must ensure that AI models used for cybersecurity are transparent, explainable, and aligned with ethical standards.Implement Governance Frameworks: To manage AI models and ensure they are deployed and used ethically, implement governance frameworks. It involves establishing policies, procedures, and processes to ensure that AI models should be responsible and transparent.Implementing AI for cybersecurity requires a comprehensive and iterative approach. It involves identifying use cases, gathering and preparing data, selecting and training AI models, implementing and integrating the models, monitoring and refining the system, evaluating and improving the solution's effectiveness, ensuring Explainability and transparency, and implementing governance frameworks. By following these steps and embracing the potential of AI, organizations can build a robust and proactive cybersecurity posture capable of detecting and responding to threats in real-time.Example of the workflow of Algorithm and Flowchart:Algorithm 1: Intrusion Detection Systema. Collect data from various sources such as firewalls, logs, and network traffic.b. Analyze the data using machine learning algorithms such as decision trees, random forests, or neural networks to identify anomalies or suspicious activity.c. If suspicious activity is detected, alert the security team to investigate.d. Update the machine learning model with new data to improve its accuracy over time.Algorithm 2: Data Encryptiona. Generate a symmetric encryption key for each piece of data to be encrypted.b. Utilize the encryption key to encode the information using a block cipher algorithm like AES.c. Transmit the encrypted data over the network or store it in a database.d. When the data needs to be accessed, use the same key to decrypt the data.Algorithm 3: Access Controla. Authenticate the user by requiring a username and password or other authentication methods such as biometrics.b. Authorize the user by checking their access privileges and permissions.c. Monitor user activity for suspicious behavior or violations of access policies.d. Enforce access policies by revoking privileges or terminating user accounts if necessary.Flow Diagram:[Start] --> [Collect Data] --> [Analyze Data] --> [Detect Suspicious Activity] --> [Generate Alert] --> [Investigate Alert] --> [Update Machine Learning Model] --> [Encrypt Data] --> [Transmit Data] --> [Decrypt Data] --> [Authenticate User] --> [Authorize User] --> [Monitor User Activity] --> [Enforce Access Policies] --> [End]This flow diagram outlines the steps to protect data in the AI era. The process begins by collecting and analyzing data from various sources to detect suspicious activity. If suspicious activity is detected, an alert does generate for the security team to investigate. The machine learning model is updated with new data to improve its accuracy. Data is encrypted when transmitted over the network or stored in a database. Users do authenticate and are authorized to access data based on their privileges and permissions. User activity monitors for suspicious behavior, and access policies are enforced by revoking privileges or terminating user accounts if necessary. Finally, the process ends once all data is protected and secure.
Select and Train AI Models: Choose the appropriate AI models for the specific cybersecurity use cases based on the available data and security needs. It may involve using supervised or unsupervised learning techniques to train the AI models on historical data. The models should be evaluated for accuracy and performance using appropriate metrics.Implement and Integrate AI Models: Deploy the AI models into the security infrastructure, integrating them with existing security tools and systems. It may involve customizing the models to fit the specific environment and adjusting parameters.Monitor and Refine: Continuously monitor the performance of the AI models and refine them over time as needed. It may involve adjusting parameters, retraining the models on new data, and updating them to address emerging threats.Evaluate and Improve: Regularly evaluate the effectiveness of the AI-powered security system and look for opportunities to improve it. It may involve conducting regular penetration testing, identifying gaps in coverage, and analyzing false positives and negatives to refine the models.Ensure Explainability and Transparency: AI models used in cybersecurity should be transparent and explainable. Understanding how the AI model arrived at a particular decision or recommendation is important. Organizations must ensure that AI models used for cybersecurity are transparent, explainable, and aligned with ethical standards.Implement Governance Frameworks: To manage AI models and ensure they are deployed and used ethically, implement governance frameworks. It involves establishing policies, procedures, and processes to ensure that AI models should be responsible and transparent.Implementing AI for cybersecurity requires a comprehensive and iterative approach. It involves identifying use cases, gathering and preparing data, selecting and training AI models, implementing and integrating the models, monitoring and refining the system, evaluating and improving the solution's effectiveness, ensuring Explainability and transparency, and implementing governance frameworks. By following these steps and embracing the potential of AI, organizations can build a robust and proactive cybersecurity posture capable of detecting and responding to threats in real-time.Example of the workflow of Algorithm and Flowchart:Algorithm 1: Intrusion Detection Systema. Collect data from various sources such as firewalls, logs, and network traffic.b. Analyze the data using machine learning algorithms such as decision trees, random forests, or neural networks to identify anomalies or suspicious activity.c. If suspicious activity is detected, alert the security team to investigate.d. Update the machine learning model with new data to improve its accuracy over time.Algorithm 2: Data Encryptiona. Generate a symmetric encryption key for each piece of data to be encrypted.b. Utilize the encryption key to encode the information using a block cipher algorithm like AES.c. Transmit the encrypted data over the network or store it in a database.d. When the data needs to be accessed, use the same key to decrypt the data.Algorithm 3: Access Controla. Authenticate the user by requiring a username and password or other authentication methods such as biometrics.b. Authorize the user by checking their access privileges and permissions.c. Monitor user activity for suspicious behavior or violations of access policies.d. Enforce access policies by revoking privileges or terminating user accounts if necessary.Flow Diagram:[Start] --> [Collect Data] --> [Analyze Data] --> [Detect Suspicious Activity] --> [Generate Alert] --> [Investigate Alert] --> [Update Machine Learning Model] --> [Encrypt Data] --> [Transmit Data] --> [Decrypt Data] --> [Authenticate User] --> [Authorize User] --> [Monitor User Activity] --> [Enforce Access Policies] --> [End]This flow diagram outlines the steps to protect data in the AI era. The process begins by collecting and analyzing data from various sources to detect suspicious activity. If suspicious activity is detected, an alert does generate for the security team to investigate. The machine learning model is updated with new data to improve its accuracy. Data is encrypted when transmitted over the network or stored in a database. Users do authenticate and are authorized to access data based on their privileges and permissions. User activity monitors for suspicious behavior, and access policies are enforced by revoking privileges or terminating user accounts if necessary. Finally, the process ends once all data is protected and secure.7. A Comparative Analysis of Traditional Methods and AI-based Systems
- Compare the implemented AI cybersecurity system with a previous method to highlight their approach and effectiveness differences.Previous Method: Signature-based detection - The last method for cybersecurity was signature-based detection. This method relied on predefined signatures or patterns to detect known threats such as viruses, malware, and other cyberattacks. Signature-based detection was effective against known threats but had limited capabilities in seeing new and unknown threats.Implemented AI Cybersecurity System - The implemented AI cybersecurity system, on the other hand, uses machine learning algorithms such as decision trees, random forests, or neural networks to detect anomalies or suspicious activity. This approach does not rely on predefined signatures or patterns but can identify new and unknown threats. Additionally, the system can learn and adapt to new threats over time, improving its accuracy and effectiveness.The critical difference between the previous signature-based detection method and the implemented AI cybersecurity system is their approach to detecting threats. The last method relied on predefined signatures to identify known threats, whereas the AI system uses machine learning algorithms to see new and unknown threats. The AI system's ability to learn and adapt to new threats makes it more effective in preventing cyberattacks than the previous method.Moreover, the AI cybersecurity system can also automate many processes, such as intrusion detection, data encryption, and access control, which reduces the human workload and minimizes the possibility of human error. In contrast, the previous method required manual updates to the signature database, which could lead to delays in detecting and preventing new threats.Here are a few comparative examples:Malware Detection: Signature-based detection systems use a predefined database of signatures to identify known malware. However, someone should regularly upgrade these databases to account for new threats. This process can be time-consuming, leaving systems vulnerable to new and unknown threats.In contrast, an AI cybersecurity system can use machine learning algorithms to identify behavior patterns indicative of malware. This approach can detect new and unknown malware not included in a signature-based database.Intrusion Detection: Signature-based intrusion detection systems use predefined signatures to identify known attacks. This approach can be effective in detecting attacks identified early. However, it can be less effective in detecting new and unknown attacks.An AI cybersecurity system can use machine learning algorithms to detect anomalous behavior that may indicate an attack. This approach can see new and unknown episodes that must identify.Access Control: Traditional access control systems rely on user authentication and authorization to determine access privileges. However, these systems may not be effective in detecting unauthorized access or account hijacking.An AI cybersecurity system can use machine learning algorithms to monitor user behavior and detect anomalies indicating unauthorized access or account hijacking. This approach can improve the effectiveness of access control systems by detecting and preventing unauthorized access before it occurs.
8. Quantifying the Effectiveness of AI-Based Cybersecurity: Evaluating Parameters for Data Protection in the AI Era
- Indeed, here are some parameters that should use to evaluate and report the outcome of an AI-based cybersecurity system.Detection Rate: The detection rate measures the percentage of known and unknown threats that the AI-based cybersecurity system can identify and block. This parameter provides insight into the system’s effectiveness in detecting and preventing cyber threats.False Positive Rate: The false positive rate measures the number of legitimate activities or data incorrectly flagged as threats by the AI-based system. A high false positive rate can lead to a loss of trust in the design and an increase in unnecessary alerts and workloads.False Negative Rate: The false negative rate measures the number of actual threats the AI-based cybersecurity system does not detect. A high false negative rate can indicate a weak point in the system that cyber attackers can exploit.Response Time: The response time measures the time the AI-based cybersecurity system takes to detect and respond to a threat. A fast response time can help prevent the spread of an attack and minimize the damage caused.Scalability: Scalability measures the ability of the AI-based cybersecurity system to handle a large volume of data and users. The architecture should accommodate increasing users and data while maintaining optimal performance and security levels without compromise.Adaptability: The adaptability of the AI-based cybersecurity system measures its ability to learn and adapt to new threats over time. The design should be able to analyze and incorporate new data and behavior patterns to improve its detection and prevention capabilities.Reporting the outcome of an AI-based cybersecurity system using these parameters can provide valuable insights into the effectiveness and performance of the system and help improve its capabilities for protecting data in the AI era.
9. Conclusions
- Artificial Intelligence (AI) has become an essential component of cybersecurity. AI-powered solutions in cybersecurity have helped organizations identify and respond to attacks more quickly and effectively than ever before. The benefits of AI in cybersecurity include• improved threat detection and response times,• reduced false positives and negatives, and• enhanced scalability and automation.Even so, there are potential drawbacks to employing AI in cybersecurity, including partiality, insufficient transparency and explicability, and vulnerability to adversarial attacks. Despite these challenges, innovative uses of AI can help to mitigate these risks and maximize the benefits of AI-powered security systems.Overall, using AI in cybersecurity is essential for organizations to keep pace with the rapidly evolving threat landscape. As threats become more complex and sophisticated, AI-powered solutions will be critical in safeguarding sensitive data and protecting against cyber-attacks. By embracing the benefits of AI and addressing the potential disadvantages, organizations can build a robust and resilient cybersecurity posture capable of withstanding even the most advanced threats.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML