-
Paper Information
- Next Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
American Journal of Biomedical Engineering
p-ISSN: 2163-1050 e-ISSN: 2163-1077
2013; 3(2): 31-40
doi:10.5923/j.ajbe.20130302.01
A Fingerprint Verification Tool Using Adaptive Resonance Theory Nets
Tirtharaj Dash1, Tanistha Nayak1, Subhagata Chattopadhyay2, Fethi A. Rabhi3
1Dept. of Computer Science and Engineering, Veer Surendra Sai University of Technology Burla, Odisha 768018, India
2Dept. of Computer Science and Engineering, Camellia Institute of Engineering, Kolkata 700129 West Bengal, India
3School of Computer Science, The University of New South Wales, Sydney 2015, Australia
Correspondence to: Subhagata Chattopadhyay, Dept. of Computer Science and Engineering, Camellia Institute of Engineering, Kolkata 700129 West Bengal, India.
| Email: |  |
Copyright © 2012 Scientific & Academic Publishing. All Rights Reserved.
Accurate verification of fingerprints is important to prevent hassles related to one’s identification. The hassle could be at the recognition of one’s own as well as the forged prints of others. The objective of this work is to develop a fingerprint verification tool using JAVA. The algorithms of Adaptive Resonance Theory (ART) net – ART-1 and ART-2 have been used. These algorithms have been implemented with ‘C’ language. Two hundred and twenty two genuine versions of finger prints have been used as training cases and 518 very similar looking but forged fingerprints have been used as test cases. Here, the optimum vigilance parameter (ρ) is obtained through carefully conducted parametric studies. Finally, a flexible error threshold has been selected to accept fingerprints with 95% matching in the pixel patterns and the rest are rejected. The study observes that, ART 1 and 2 are able to identify forged fingerprints with Total Success Rate (TSR) of 95.80% and 97.37%, respectively.
Keywords: Biometrics,Fingerprints, Forgery, Verification, Adaptive Resonance Theory Net, Graphic User Interface
Cite this paper: Tirtharaj Dash, Tanistha Nayak, Subhagata Chattopadhyay, Fethi A. Rabhi, A Fingerprint Verification Tool Using Adaptive Resonance Theory Nets, American Journal of Biomedical Engineering, Vol. 3 No. 2, 2013, pp. 31-40. doi: 10.5923/j.ajbe.20130302.01.
Article Outline
1. Introduction
- Biometrics is the secure, reliable, and convenient methods to verify the identity of a person. It has now largely replaced the traditional paper-based (e.g., signature-based documents), password-protected devices (e.g., computers), and identity card-based systems (e.g., employee authorization). One important advantage of the biometrics is that, they are devoid of any worry of losing the information by losing the identity card or paper or forgetting the passwords[1][2]. Generally, left thumb impression (LTI) is considered to be most commonly used biometry in many cases[3]. The issues with LTI are that these could be distorted (e.g., in heavy duty manual labours) and therefore become inconclusive, when viewed by the naked eyes. As a serious consequence, such issues open the scope for forgeries. Given this practical scenario, this paper focuses on the development of a tool-based detection of an LTI using Adaptive Resonance Theory (ART) Nets – ART-1 and ART-2 those use the concept of Artificial Neural Network (ANN). Neural Networks (NN) learn and adapt exemplary patterns by observations[4] and has been successfully applied to process very complex and large datasets[5][6][7]. There can be of two types of learning modes, such as supervised and unsupervised learning. Adaptive Linear Net (ADALIN), Multiple ADALIN (MADALIN), Perceptron Network, etc. are some examples of supervised learning methods. These types of NNs learn faster and more accurately, but the problem with these is that, new trainings are required each time they learn new input patterns and as a result, the previously learned patterns are lost. On the other hand, networks, such as Counter Propagation Network (CPN), Adaptive Resonance Theory Net (ART), and Kohonen’s Self Organizing Map (SOM) rely on unsupervised learning and can store previously learned patterns well. Among these networks, ARTs in particular, are able to store new patterns without losing the memory of older patterns and thus advantageous over the supervised methods[8]. It is worth noting that Associative Memory Net (AMN) could be another useful technique that retains the patterns, learned in the past[9]. The key focus of this paper is to develop a faster Graphical User Interface (GUI) using ART-1 and 2 algorithms for fingerprint verification, offline. In this GUI-based system, the developed algorithms will be working as the backend of the tool, which were implemented using ‘C’ language. To train the algorithms a large database of genuine fingerprint patterns have been used. The advantage of using ART is its ability to capture the complexity of the fingerprint patterns without losing the previously learned patterns. The verification task is performed offline by computing a mismatch value. The front end of the tool has been developed with JAVA. The concept of native programming has been used to set a communication between ‘C’ and JAVA. As there are two algorithms, such as ART-1 and ART-2, these have been compared according to their performances. Rest of the paper is organized as follows: section 2 studies related literature; proposed methodology is discussed in section 3; results and discussions are given in section 4; and the work is concluded and future scopes are discussed in Section 5.
2. A Brief Overview of Previous Works
- Different techniques are being implemented for fingerprint detection. Below we have showcased few interesting studies in past ten years. Yang and Park, (2008) proposed a fingerprint verification algorithm with tessellated invariant moment features[10]. This method could be applied to poor quality images of the fingerprints also. Authors had used Eigen value-weighted cosine distance for finding similarity between images. The algorithm yielded high detection accuracy. Dash et al., (2012) studied three algorithms, such as Associative Memory Net (AMN), ART-1 and ART-2 in the detection of ‘forged’ handwritten signatures and compared their respective performances[11]. The authors used OpenMP for developing and implementing the algorithms. The study observes that ART-1 and ART-2 were able to detect forged signatures with high accuracy (98.99% and 99.99%) compared to AMN (78.68%). Li et al., (2012) developed a cryptosystem by combining fingerprints with error correction codes and the work showed an improved performance[12]. Global and local structures of a fingerprint could be used by (Mali and Bhattacharya, 2011) for fingerprint verification[13]. However, in this work, simple matching technique had been used for authentication purpose, which might not be successful in the verification of distorted images or fingerprints taken with some angular deviation. A fusion system using biometrics like fingerprints, face, retina etc. was developed by Ross and Jain, (2003)[14]. This method addressed the information fusion in biometrics. This work was similar to work of Prabhakar and Jain, (2002) where the authors addressed decision-level fusion[15]. A fingerprint retrieval system was developed based on level-1 and level-2 features of the sample where level-1 refers to local orientation or frequency and level-2 is minutiae by Cappelli and Ferrara (2012)[16]. The error in the detection was only 1-2%. A mathematical model based fingerprint verification system was proposed by Jin et al., (2004)[17]. The model was developed on Integrated Wavelet and Fourier-Mellin transforms. The equal error rate was 1.01% in this work. A state of art research was conducted by Maio et al., (2002) in Fingerprint verification competition where total four algorithms were tested on a large number of data sets[18]. A fingerprint verification system was developed by Bazen et al., (2000) based on the principle of signal correlation[19]. In this work, template matching was used in the secondary stage of the verification. The equal error rate (EER) in their work was found to be 7.98%[19]. Two algorithms from top ten presented in fingerprint verification competition (FVC) in the year 2004 took an average of 3.5 seconds[20] to check the forgery. So in this case, our algorithms proposed in the next section achieve better result in minimal time consumption. Triangular method of matching of fingerprint pattern could be used by KovaÂcs-Vajna (2000) to develop a verification system[21]. Intermediate phases worked with minutiae extraction and dynamic time wrapping (DTW). The correct verification was found to be 85%.
3. Proposed Methodology
- Methodology includes steps as described below. Fig.1 shows the outline of the proposed methodology, followed by a discussion of each step.
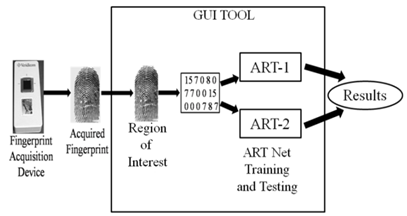 | Figure 1. Outline of Proposed Methodology |
3.1. Acquisition of Fingerprint
- A compact solid state sensing device was used for acquisition of fingerprints from different persons. The device is given in Fig.2(a) below and the acquired fingerprint from the device is shown in Fig.2(b).
 | Figure 2. (a) Fingerprint Acquisition Device, (b) fingerprint by the device |
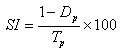 | (1) |
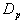 is the number of ‘dissimilar pixels’ and
is the number of ‘dissimilar pixels’ and 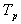 is the total number of pixels.
is the total number of pixels.3.2. Formation of Region of Interest (ROI)
- Region of interest was found out based on change in pixel value of the fingerprint image. A typical figure is given in Fig.3 to demonstrate the methodology of selecting the region of interest.
 | Figure 3. Fingerprint and the corresponding region of interest |
3.3. Feature Extraction from the ROI
- It is wise to mention that this work proposes two algorithms based on which the tool has been developed using JAVA. One algorithm uses the concept of ART net of Type-1 and other one uses the concept of ART net of Type-2. ART-1 uses the binary training and testing database for its operation whereas the later type of net uses continuous decimal values. So, the feature (pixel) extraction followed the formula given in equation-2.
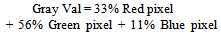 | (2) |
3.4. Proposed Algorithm
- The proposed algorithm for this work is given in a pseudo-code below. It should be noted that, the algorithm was implemented in ‘C’ language whereas the GUI tool was developed using JAVA. Both the program (C and JAVA) were linked using Native programming (JAVA Native Interface)[19]. Reason for such implementation is discussed in later section.STARTInitialize learning rate (α), vigilance parameter (ρ), initial weights (bij(0), tji(0))/*Total number of iteration = Number of training patterns*/WHILE (Stopping condition is FALSE)DOFOR each input training fingerprintsDOGet the pixels of the genuine fingerprintsF1-Layer ProcessingIF (Reset is TRUE)Find the victim unit (F2 unit) to learn the current input PatternCalculate F1(b) unit from F1(a) and F2ELSEPerform weight updationENDENDREPEAT WHILE loop for the tested imposter fingerprintsSTOPUpdation of weights is performed using the following mathematical equations:Equations 3.1 and 3.2 correspond to the bottom-up and top-down weight updation respectively in ART-1.
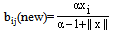 | (3.1) |
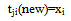 | (3.2) |
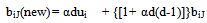 | (4.1) |
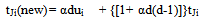 | (4.2) |
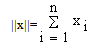 | (5.1) |
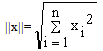 | (5.2) |
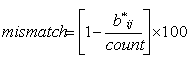 | (6) |
3.5. Developed GUI and running of the tool
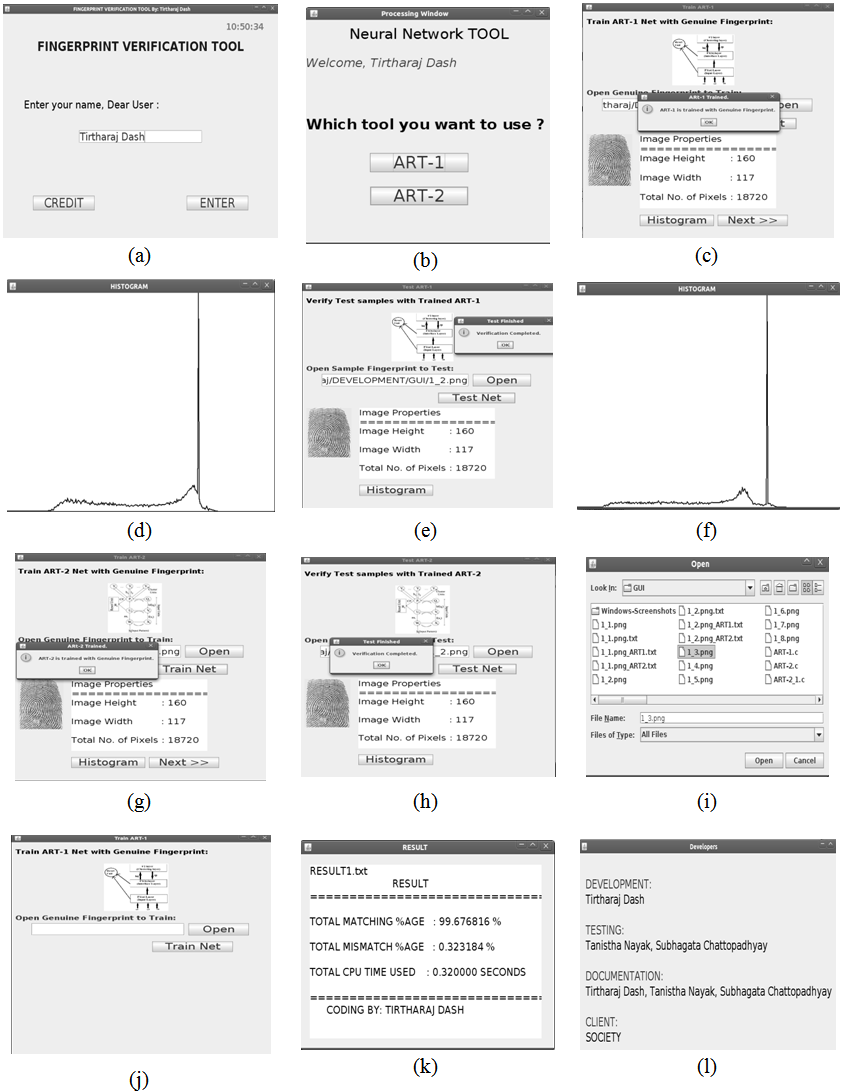
- Below figures/windows (Fig.4a through j) show the GUI developed and its usage in this research work.
3.6. Running of the Tool
- When the JAVA tool is executed in JAVA environment, a welcome window appears and asks the user for name. The purpose of creating this window is to save the result data against the current user’s name for future references and uses. As, this tool has been made for testing purpose only, it ask about the tool choice. That is, whether to choose ART-1 or ART-2 net. After choosing one tool, the user scans its left thumb in the acquisition device and click ‘train network’ button. If the user has already stored its fingerprint image in the computer, then no need to scan again. He/she can directly upload it into the tool using ‘open’ button. The tool then shows the image properties and the corresponding histogram. The next step is to test the network with imposter patterns. For this purpose, the same procedure is followed as stated above. Finally the result window opens and shows the matching percentage and computing time used and the data is appended in the user name file.
4. Experimental Results and Analysis
- The contribution of this work is an applicable GUI tool for fingerprint verification and a detailed parametric study on the vigilance parameter (ρ) using the principles of ART-1 and 2. Then the CPU time has been computed to note the decision making speed by the tool. The study is carried out on the created fingerprint database. This work also compares performances of both ART-1 and ART-2 based algorithms for verification purpose.Basically, performance of a biometric verification algorithm refers to its error rate and accuracy tested under many possible conditions. Four important terms have been used in this section for this purpose. Those are False Acceptance Rate (FAR), False Rejection Rate (FRR), Total Success Rate (TSR) and Equal Error Rate (ERR) and are given in equations 7-10, below.
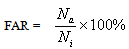 | (7) |
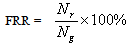 | (8) |
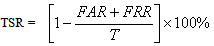 | (9) |
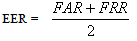 | (10) |
4.1. Results of ART Nets
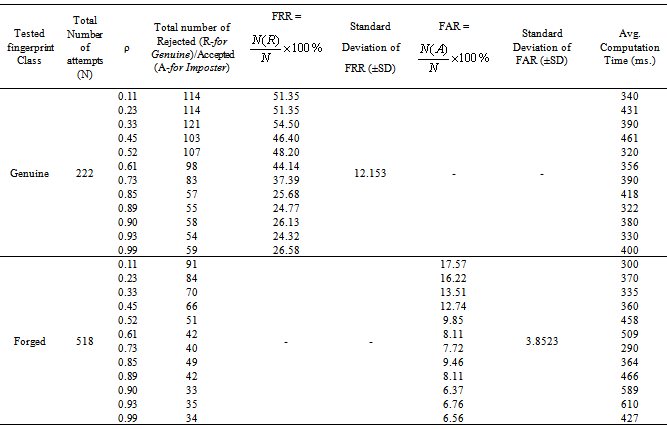
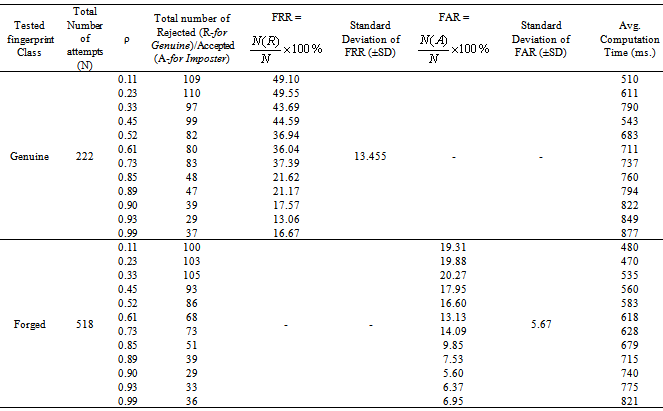
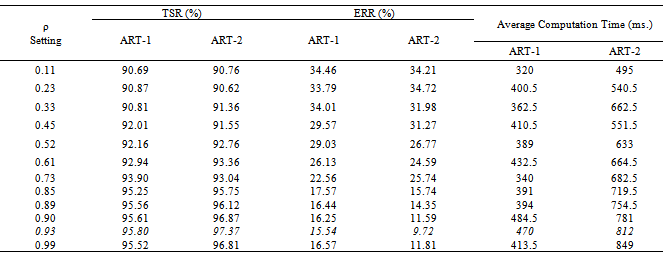
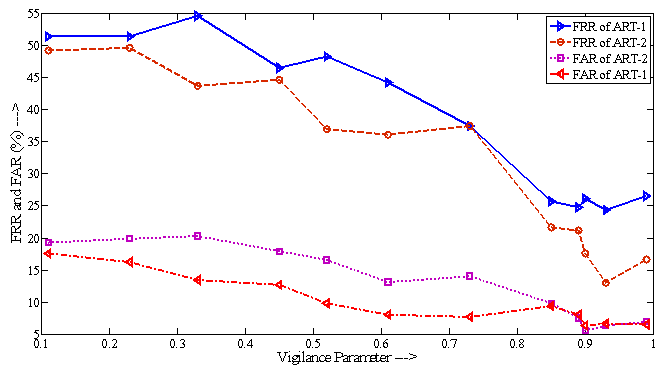
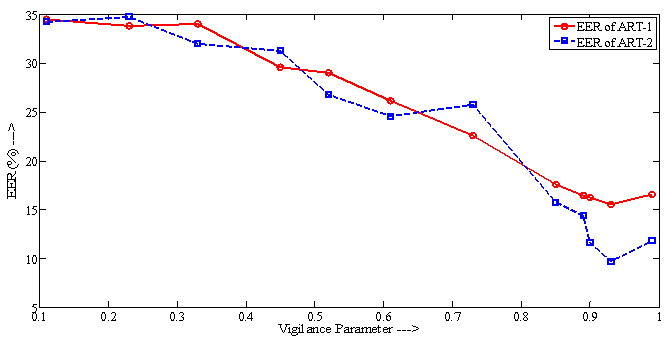
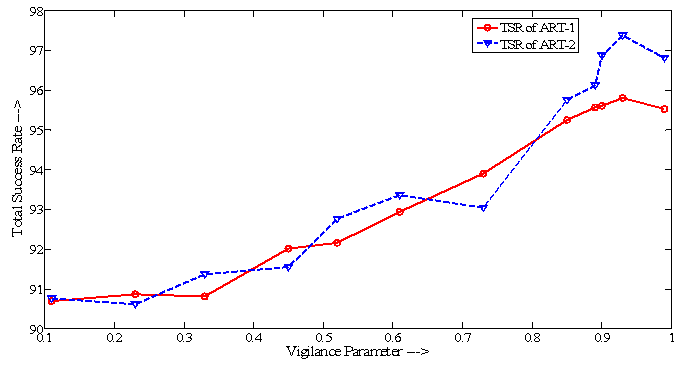
- Table-1 and 2 shows FAR and FRR achieved by the developed ART-1 and 2 algorithms, respectively. The algorithm has been tested with various values of ‘ρ’ ranging from 0.50 to 0.99 as 0<ρ<1. It should be noted that for decision making, we have set the threshold as low as 5% mismatch to count number of accepted or rejected fingerprint patterns from the created database of 740 patterns. Hence, any mismatch threshold <5% is considered as ‘accepted’ and vice versa. By setting a stricter mismatch threshold, such as <1%, these false acceptances could be averted. It is wise to mention that the number of cluster unit (m) in ART nets is set to 20.It should be noted that the average computation time for each vigilance parameter was calculated as the average of ten executions. However, time required to train the network with whole 222 fingerprints was not noted as it was a pre-testing task. The system which was used for development and testing of this tool was having following specification.System architecture:● RAM size : 2 GB● Processor : Intel® Core™ 2 Duo CPU @ 2GHz● Operating System : 32-bit Linux OS (Ubuntu 11.10)● Compiler: gcc compilerIt is mentioned in former section that the developed algorithms are implemented in ‘C’ language and the tool was developed using JAVA language. This is because of the following two reasons: a) Computational speed of ‘C’ language is faster as compared to that of JAVAb) To decrease the computation time to much lower value, a parallel approach can be made in ‘C’ easily using parallel languages like Message Passing Interface (MPI)[22], but this is too difficult in JAVA programming. As, this tool can also be used for palm print verification or recognition, the larger area size of the palm print image will make the tool slower, that’s why a time efficient tool must be developed for the same.Table-2 shows that the average computation time in case of ART-2 net is more than that of ART-1. This is because the complexity of feed-back path between processing layer of neural nodes and the input layer. A detailed analysis on TSR and EER could be crucial to compare the performance of the two algorithms. Table-3 shows this comparison. For calculation of TSR, the total number of attempts is taken as 740 (total number of patterns in the fingerprint database). However, the time will significantly increase if the supplied fingerprint area is larger. Table 3 shows that ART-1 is performing with a TSR of 95.80% and ERR of 15.54% only when the vigilance parameter is tuned to 0.93. The developed ART-1 algorithm outputs the result within 470 milliseconds. Similarly, ART-2 has a TSR of 97.37% and ERR of 9.72% at same vigilance parameter. Various plots are given in Fig. 5-9 below to focus more on the comparison of performances between the two algorithms.In the Fig. 5-7, it can be seen that the tuning vigilance parameter has a major effect on the algorithmic performance. This also accelerates capacity of the tool for detection. With low vigilance parameter, the algorithms are less able to cluster the input patterns and hence are failed to catch skilled imposter pattern. With vigilance parameters tuned between 0.4-0.9, the inputs could be clustered among the set number of cluster units (m=20). Therefore, vigilance parameter near to 0.9 is the optimized value.
|
|
|
 | Figure 5. Vigilance parameter vs. FAR and FRR of ART algorithms |
 | Figure 6. Vigilance Parameter vs. Equal Error Rate |
 | Figure 7. Improvement of Success Rate with vigilance Parameter |
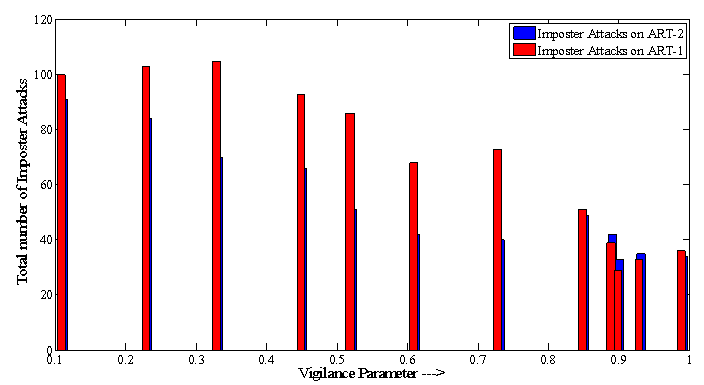 | Figure 8. Imposter attacks on ART algorithms and resolution with different vigilance parameters |
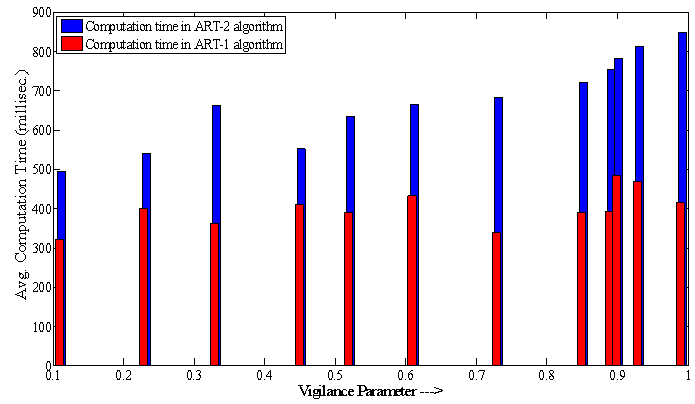 | Figure 9. Decision making time taken by two algorithms |
5. Conclusions and Future Work
- In this paper, two algorithms based on ART were proposed for fingerprint verification process. A complete fingerprint tool has been demonstrated with a GUI for testing of the developed algorithm. We have used ART networks – type 1 and 2 to develop the back end of the tool using ‘C’. The front end is developed in JAVA, which has been connected to back end by the concepts of native programming, so that user inputs could be processed and the decision could be viewed. The tool has been tested with 740 test cases of genuine (222) and forged (518) fingerprints. ART-1 achieved a TSR of 95.80% with EER of 15.54% whereas ART-2 performed best with TSR of 97.37% and EER of 9.72% with mentioned vigilance parameter. From the technical perspective, the paper reveals that tuning of vigilance parameter (ρ) is the key to the successful detection of imposter fingerprints, which has been performed during the training. In this study, ART-1 and ART-2 with ρ = 0.93 detect very similar looking forged patterns with maximum success rates. The study also observes that, in case of ‘n’ number of pixels partitioned into ‘m’ number of clusters (in case of ART-2), the algorithmic time complexity becomes O(n × m). This issue could be handled with the help of parallel computing, so that the said tool could be more time efficient. The authors are currently working on various standardization processes of the tool for its future implementations.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML