-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Advances in Computing
p-ISSN: 2163-2944 e-ISSN: 2163-2979
2017; 7(2): 40-43
doi:10.5923/j.ac.20170702.06

Theft Detector
Rashmi J. Nayak, Numreen, Salma Ahlam, Meera Savaliya, Vijetha U.
Computer Science and Engineering, St Joseph Engineering College, Mangalore, India
Correspondence to: Numreen, Computer Science and Engineering, St Joseph Engineering College, Mangalore, India.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

For over a decade, Surveillance cameras have been the prime option to ensure security at places of interest. The main drawback of this system is that it simply stores video footage and fails to alert the concerned personnel in real-time about the ongoing crime. In this proposed system, Theft Detector, theft can be detected and notified to the user in real time. The system uses pi camera and PIR sensors connected to Raspberry pi to detect the intrusion in real time. On detecting an intrusion, the concerned person (victim) is notified about the theft via mail and SMS. The victim also receives an image of the intruder and has access to the video footage of the theft immediately. This system can prove to be beneficial in jewelry shops, home etc.
Keywords: Frames, Image processing, IoT, PIR sensor, Raspberry Pi
Cite this paper: Rashmi J. Nayak, Numreen, Salma Ahlam, Meera Savaliya, Vijetha U., Theft Detector, Advances in Computing, Vol. 7 No. 2, 2017, pp. 40-43. doi: 10.5923/j.ac.20170702.06.
Article Outline
1. Introduction
- Surveillance system is becoming more and more important for observing places of interest. The existing Surveillance systems merely store video footage. With such systems, the footage will be useful only after the occurrence of the crime is revealed, just to determine the sequence of actions that took place or to identify the intruder. Clearly, it fails to meet the requirements of ensuring total security. What we need is smarter surveillance systems that not only captures video but also alerts the user right away when something unusual takes place. There are many theft detection software available in the market. They provide a lot of features to the user. One of the major drawback of those systems is either their price or the user interface isn’t very user friendly.Our approach to theft detection is to provide the use with an affordable and user friendly interface system. The system continuously captures the image of the place of interest and compares it against a reference image frame of the place of interest. The assumption here is that the surveillance system functions at the time (possibly at night) when there are no human security personnel inside to guard the place. A reference image would be an image of the empty room/shop and therefore presence of any human in the captured video would create a difference in the reference image and captured image and would flag a possible intrusion. A motion sensor is used as a complement to the camera surveillance to add some additional security to the place.
2. Implementation
- Internet of Things (loT) is an on-going development by which all 'things' have communication capabilities thus allowing them to send and receive data. In the proposed system, we provide internet connectivity to camera and sensors that send the gathered data to the processing system for further analysis.
2.1. Control Flow
- The control flow of the system is shown in the figure below.
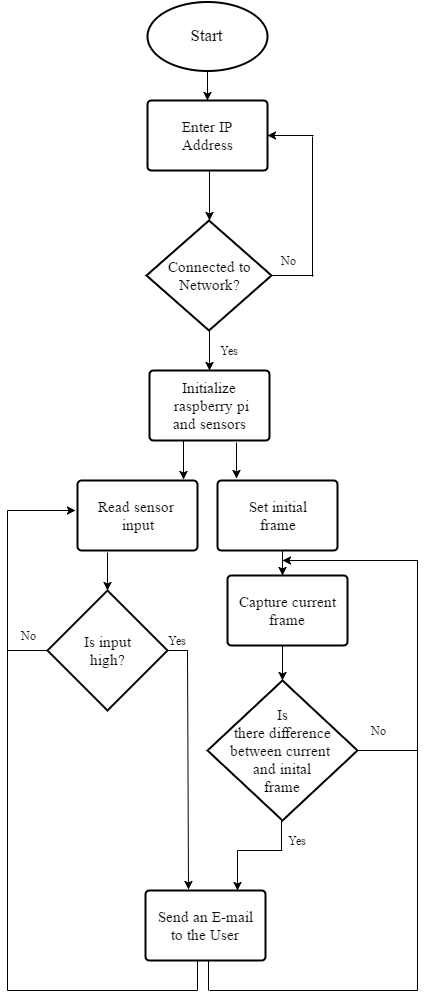 | Figure 1. Control system flow |
2.2. Pseudo Code
- A high level description of our code is given below:

2.3. Result
- With our approach to smart surveillence, the user is allowed to depict a time for monitoring intruders. During the survery time, the system continously polls data from pi camera and PIR sensor. In case of an intrusion, the intruder will have crossed the motion sensor, an image of the room is captured and mailed to the user. The pi camera on the other hand captures images and sends it to raspberry pi for further analysis. If the image processing flags a possible intruder, the user is notified through sms and email. User can also view and download the footage of the intruder to be used as evidence.
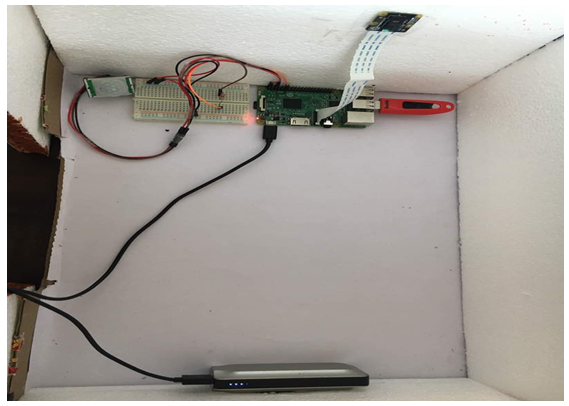 | Figure 2. Setup of empty room |
 | Figure 3. Figure showing movement in the empty room |
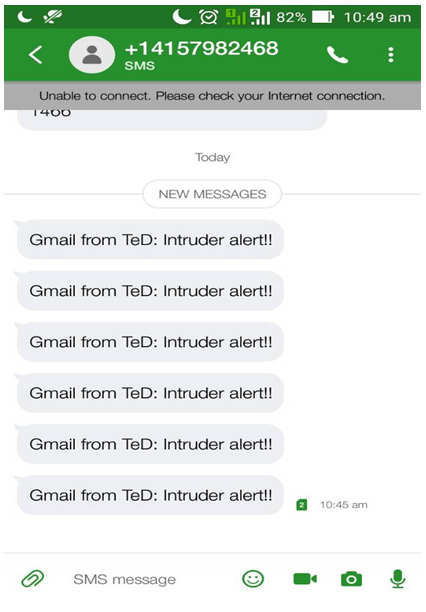 | Figure 4. Notification of intrusion via SMS |
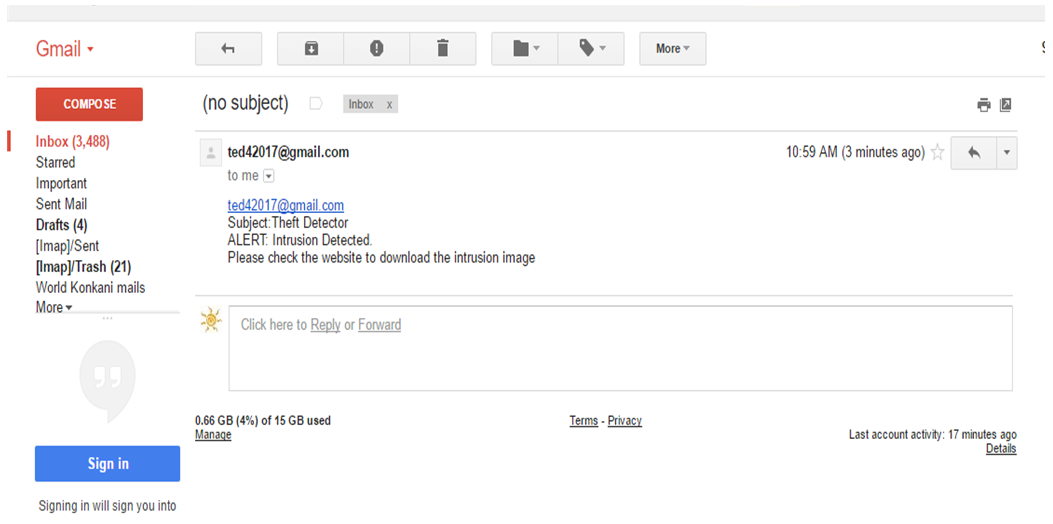 | Figure 5. Notification of intrusion via E-mail |
 | Figure 6. Video of the intrusion |
3. Conclusions
- In this paper, we introduced a tool Theft Detector, developed as a solution to detect and alert about ongoing theft. The proposed system succeeds in detecting intrusion everytime there is movement or person’s presence inside the room. Our system works exceptionally well with negligible or no false alarms. The present setup of the project assumes some minimum lighting in the room. The system may have to be upgraded to contain IR cameras to work equally well in complete darkness.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML