-
Paper Information
- Next Paper
- Previous Paper
- Paper Submission
-
Journal Information
- About This Journal
- Editorial Board
- Current Issue
- Archive
- Author Guidelines
- Contact Us
Advances in Computing
p-ISSN: 2163-2944 e-ISSN: 2163-2979
2017; 7(2): 35-39
doi:10.5923/j.ac.20170702.05

Connectify- A Social Networking Website
Sharyl Cutinha, Sonalia Rodrigues, Sanjay P., Supreetha R.
Department of Computer Science and Engineering, St Joseph Engineering College, Mangaluru, India
Correspondence to: Sonalia Rodrigues, Department of Computer Science and Engineering, St Joseph Engineering College, Mangaluru, India.
| Email: |  |
Copyright © 2017 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/

Social media is more important today than ever before. Staying connected and informed has become the need of the hour for every individual. Social networking sites have become very popular avenues for people to communicate with family, friends and colleagues from around the corner or across the globe. Traditional social networks have all of the user’s contacts muddled into a single list offering everyone the same privileges. Connectify- The Social Network is a social networking website that intends to connect people in a more organized manner by categorizing the user’s connections according to his work, social and familial relations. This paper gives a brief overview of the project which focuses on the social network and its features which are extensively used today by a wide range of people.
Keywords: Social Networks, Activities, Groups, Website, Security
Cite this paper: Sharyl Cutinha, Sonalia Rodrigues, Sanjay P., Supreetha R., Connectify- A Social Networking Website, Advances in Computing, Vol. 7 No. 2, 2017, pp. 35-39. doi: 10.5923/j.ac.20170702.05.
1. Introduction
- Social Networks are used by hundreds of millions of people around the world and have become prevalent forms of communication and interaction on the internet [1]. A Social Network is defined as an internet-based service that allows individuals to construct a public or semi-public profile within a bounded system, articulate a list of other users with whom they share a connection, and view and traverse their list of connections and those made by others within the system [2]. Social Networking sites connect people worldwide through a range of features including fairly static profile information, such as job history and likes/dislikes, and more dynamic content like what people are doing and how people are feeling at various points throughout the day. While this sort of input provides the ultimate flexibility, the requirement for manual input places a barrier between a person’s dynamic status and its representation on a users profile page. What makes social network sites unique is not that they allow individuals to meet strangers, but rather that they enable users to articulate and make visible their social networks. Beyond profile, social networking sites vary greatly in their features and user base. Some have photo sharing or video-sharing capabilities; others have built-in blogging and instant messaging technology [8]. Connectify- The Social Network aims at providing an unambiguous platform where one can separate his/her contacts into any of the three groups- Work, Friends or Family and give individual attention to each. This provides greater convenience and a better networking experience to the user. The attempt of this website is to standardize multiple services to avoid the need of duplicate entries and allow efficient use of social network for convenience of users [3]. It ensures filtered group structure throughout the website for ease of the user communication. Connectify categorizes the user’s connections at their first point of contact and maintains it throughout. Whenever the user receives a request for connection, he/she can add the contact to any of the three groups [6]. A confirmation message is sent to the request sender about the group they are added to. The user can share posts to each group separately according to the context of the post. It also facilitates viewing the updates of each group on different pages. A business related post such as a meeting reminder will be posted and viewed in the Work section of the account. Switching between each group becomes easy. The project offers the users crucial features like two-step verification, location tracking during login and word filter according the user’s discretion. At the same time the user interface is intuitive and avoids extraneous features not related to networking. In a world where time is money, an organized social network can go a long way in providing a hassle free experience to the masses. This project provides a platform to network without the unnecessary clutter that comes with traditional social media. It provides effective environment for personal as well as business oriented needs.
2. Related Work
- During the last few years social networking has evolved into a fundamental daily activity for many individuals and a new frontier for business marketing. Besides traditional social networking, the recent trend is professional and domain-specific networking services focused on interactions and relationships of a business nature around a specific target domain [4]. IT professionals may use social networks to stay updated about the corporate world whereas common users may use it to connect with their friends. So it is necessary to have a social network that will satisfy the needs of different types of users. There are many social networks in the market today with the most popular one around the world being Facebook. Other examples for social networks include MySpace, Sabakuch, LinkedIn, Twitter etc. The conception of MySpace opened the internet users to vast opportunities of self- expression which include wide control over a user’s profile content [5]. Facebook started as a local social network made for the students of Harvard [5]. Facebook was built on the idea that all our information could be shared and the user is allowed to register, and then proceed with the login process to perform specific tasks such as messaging, posting images etc [2]. Sabakuch.com is another social network which is an encompassment of three aspects of popular web browsing needs i.e., Social Networking, Entertainment and Learning with just one login. After registering with Sabakuch.com users can have their own user profile which further gives them an access to three different sections on a single dashboard. These are referred to as zones and used for separate interests such as work, family and friends. They provide with the separate interface for the different groups. On Twitter, online users can post their tweets about what they have in mind [2]. These social networks have shaped the concept of Connectify.
3. Implementation
- The social networks contain various categories which themselves contain forums which contain topics like discussions or which are made up of individual posts where a user writes something [5]. All these categories are arranged in a unique way for the ease of the user. The project “Connectify”, unlike other networking portals is a unique assimilation of three kinds of networking needs shared on one platform [5]. The website gives the users the convenience to deal with their personal and professional contacts on a single portal, which traditionally required them to use different portals for their varied needs.It aims to provide a platform to the people so that they can easily and quickly; think, create, express and share their thoughts, beliefs, and information with friends, family or the business world. This project is totally self contained and works efficiently. The system works on internet server, so it can be operated by any end user. It provides unambiguous database to store user details who have registered to this service. The user has to enter username and password to gain access to his/her account and use the social networking services as per his/her interest. The user friendly Graphical User Interface (GUI) provides menus, icons and hyperlinks to facilitate screen navigation and data entry [5]. Appropriate interfaces are provided for users login, profile and viewing of friends activities. The user can switch between his work, friends and family accounts easily. The user interface for the software shall be compatible with any browser such as Internet Explorer, Mozilla Firefox and Google Chrome. To use the website, a user must first login into system by entering a valid email identification and password. Only registered users can login into the system [6]. The registration process is fairly simple and intuitive; requiring basic information of the user and setting up a password for his/her account. This website provides two-step verification for all its accounts. Two-step verification is one of the best ways to prevent unauthorized access to your accounts [7]. In the most common implementation, after correctly entering your password, an online service will send you a text message with a unique string of numbers that you’ll need to punch in to get access to your account. In this project, along with an OTP (One Time Password) being sent to the mobile number, an OTP is sent to the registered email also to verify the email address provided. Once the user logs in, the account information of the user is displayed which he/she can update it. The home page of the website gives an overview of all the latest updates in the family, friend and work timelines of the user. It enables the users to quickly update themselves on what their contacts in each category are up to. The system is designed to be simple and easy to use without a lot of hassle and does not require searching for certain features. To connect with other users and form associations, the user has to look up for the contact’s profile under the Search Friends tab where friend suggestions appear for the ease of the user. By typing the name of the contact, the user can find the basic profile of that contact along with a Send Request button [6]. Clicking on it allows a request to be sent from the sender’s profile. On the receiving end, these requests can be seen under the Friend Requests tab in the user’s account. Here all requests appear in a grid-like form and can be selected using checkboxes. The requests can be categorized under Friend, Family or Work as per the user’s wish. This categorizing allows users to interact with their personal, social and business contacts discreetly [5]. Once the user adds a contact under any group, a notification is sent to the sender to confirm the association under that particular group. Hence both the users are aware and approve of the relationship they share.The figure 1 depicts the overview of the social networking site. End users are individuals who have registered to use the social networking service. Each user belongs to different groups and each group can be assigned individual permissions [5]. The home page allows the user to navigate to each of his three timelines which is the Friend Timeline, Family Timeline and Work Timeline. Each of these display everything shared by the users contacts in each group, hence enabling smooth browsing through the feed. Suppose the user is time-bound and wants to go through only the activities of his professional contacts, he can easily do so by viewing his Work Timeline only. There is no need to skim through the single timeline as in the case of traditional social networks. To post updates, the user should navigate to the Post Message tab where he/she can post pictures along with a text message for his/her contacts to view. Along with this, another essential piece of information is which timeline the user wants to post the update to. The group is selected depending on the update’s interest. Accordingly the timeline selected will be updated with the new post and the contacts in that group can view it. Posts are contained in threads, where they appear as boxes one after the other [5].
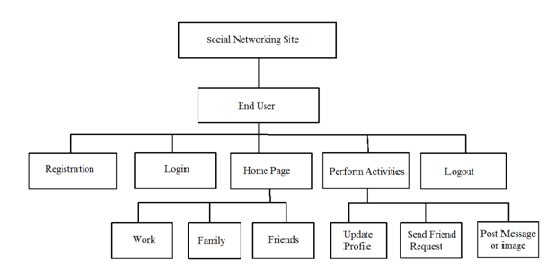 | Figure 1. Block diagram of the Social Networking Site |
4. Security Issues
- In today’s socially connected workplace, information flows freely between employees and their online followers [9]. Users tend to post a variety of information including their personal data or photos which are exposed to the external world. This can pose serious risks to an enterprise’s network, data, reputation and misuse of the data [9]. A security issue occurs when a hacker gains unauthorized access to a site’s protected coding or written language. The more information a person posts, the more information becomes available for a potential compromise by those with malicious intentions [9]. The hacker can use the account and the data present in it for the personal benefits thus harming the reputation and privacy of the user. Therefore it is necessary to ensure security in the social networking sites. This project aims to provide with some features to overcome the security issues involved in the social networking site. The features provided by this project to overcome security issues are Two-step verification and Location Tracking. The descriptions of the features are mentioned below:A. Two-step verification This project incorporates two-step verification to provide the user with extra security. The added layer of security makes it much harder for a hacker to access an account. The extra log-in steps will save the user’s time and helps in securing the account. It prevents anyone else from accessing the user’s account. Initially the user will sign-in by filling the basic details with the password of their choice and next step consists of sending a code to the registered phone number [7]. The code corresponds to the OTP. An OTP is an automatically generated numeric or alphanumeric string of characters that authenticates the user for a single transaction or session. This OTP will be sent to the registered phone number of the user so that the access is granted only to the desired user. OTP is generated randomly and it is different for every user. Once the user enters the valid OTP, the user will be directed to the login page but invalid OTP causes the user to remain in the same page. Once the two-step verification is successful it provides with access to the user to their respective accounts. Thus this project aims at providing the basic level of security to the users to secure their accounts from any external agents. This feature makes sure that only user with valid phone number will gain access to the social network so that the account remains secure. B. Email VerificationWhen it comes to the use of social network, it is very important that the account of the user remains secure since it consists of sensitive information such as pictures, details regarding family or business, contact information etc. So it is very important to know the identity of the users [5]. For this reason email verification is done to check whether the email id entered by the user is genuine or not. This project does not provide access to the user who have entered fake email id during the registration process. An email id can be associated with only one user and cannot be shared by multiple users. This avoids the single user in having multiple accounts in the same social network. An OTP will be sent to the registered email id entered by the user during the registration process [7]. User needs to enter the correct OTP to get login access.C. Location Tracking Online social networks typically deal with large amount of user data, which contains enormous personal information like personal interests, contact details, photos, associations and interactions, once revealed may incur various magnitudes of impact. Therefore location tracking becomes very important in these networks [11]. Location information is sensitive because it enables the possibility of tracing someone in person. It is very necessary to ensure that the access to the social networking account is given only to the authorized user to avoid the potential damage to the user. Use of two-step verification authorizes the users to login to their respective account but it cannot provide security if an unauthorized user hacks the user’s account. Two-step verification is only to verify the user to one who claims to be [7]. Therefore it is necessary to know that every time a user logins in, it is the authorized user who is trying to access the account and not an unauthorized user. This issue can be overcome by using the location tracking technique. Initially location tracking involves in determining the location of the authorized user. The user’s location should be continuously monitored to determine the authorized users and unauthorized users. This is done by fetching the IP (Internet Protocol) address. The idea behind this is when one of the devices is connected to the internet, that device is assigned an IP address by the internet service provider of the network. This IP address is set of numbers that identifies who the internet service provider is as well as from where the user is connecting from [12]. If a user logs-in from a particular city or a place and then if a log-in is made into the same account after a couple of minutes from another city or place, the location tracker will determine whether it is possible for the user to travel from the first location to the second in the specified time interval. This states that the second location corresponds to the unauthorized user and should be blocked immediately to restrain from any further misuse of the account. User has to then contact the admin to recover the account. Since the location tracker continuously monitors the user’s location by fetching IP address, it is possible to determine the user’s location and that of the unauthorized user [12]. This way the project ensures to overcome the security issues involved in the social networking sites and provides with a secure environment for the user to work in.
5. Conclusions
- Social networking has transformed the way the connected masses communicate. In today’s social network, the line between user’s personal and corporate lives is blurred [9]. The Connectify website is developed making use of available tools, technique and resources that would generate a proper online social network. The website is user friendly and also will be acceptable to any user to adequately meet their requirements. The website is hosted on the internet and can be accessed by anyone with a valid email address and phone number. The website includes some new features apart from other social networking site such as location tracking and word filter. The website categorizes friends, family and work connections separately where the user can switch between personal and corporate life [5]. Thus the website aims to meet various needs of the user by providing a filtered social networking environment.Social networking website is a revolutionary idea with a very bright future with further scope for advancements. There are always features that can be added as per the user’s ever increasing needs. Some features which can be included in the future are video and audio upload, voice recording, online chat where the user can chat with friends, online games, uploading multiple files/images, video calling etc. Traditional login can give way to login using face recognition. Security can be further increased using end-to-end encryption for messages. In the near future all the left behind features can be added in this website to make it more advanced.
 Abstract
Abstract Reference
Reference Full-Text PDF
Full-Text PDF Full-text HTML
Full-text HTML